Cryptography in the fight for the bright future of the Internet

The term “cryptographic” means the state of the formal world between states, which at the same time are actively fighting each other in different fields, but without the use of force. The clearest example of crypto is the cold war between the USSR and the USA. However, today this term has a different meaning. Cryptic became known as a conflict of interest, where one side is the population that wants to use strong cryptographic tools, and the other side is the power that doesn’t want to allow it. It would seem, not for the first time in human history, those in power are trying to ban something and restrict something. But such cryptographic ones directly affect the development of all of our beloved Internet. That is, affect everyone.
The first kriptovna
The first cryptographic program began in 1991, when American programmer Philip Zimmerman released the first version of his cryptographic tool PGP (Pretty Good Privacy). The significance of this event is hard to overestimate: perhaps for the first time in history, absolutely anyone had the opportunity to encrypt and exchange messages that no one could intercept and read, except for the addressee.
Naturally, the reaction of the security forces and governments followed immediately. Under the pretext that PGP could take advantage of the criminal element, the United States banned the export of “strong cryptography” tools altogether. As a result, a number of applications, for example, Netscape Navigator , began to appear in two versions: with support for 128-bit encryption for “internal” use, and with support for weak 40-bit for the international market.
')
But the first step has already been taken, and many new features have come to taste. The basis of strong and weak encryption was the same fairly simple mathematical apparatus. The difference was only in the length of the key, and attempts to artificially limit it were ineffective. As a result, by the early 2000s, bans on the use and export of strong crypto tools had become obsolete and were largely abolished. So the first kriptovna ended in victory for the inhabitants of the Internet.
The second crypto
This time, the role of Gavrila Principle was played by a small smiley on a secret document of the US National Security Agency.
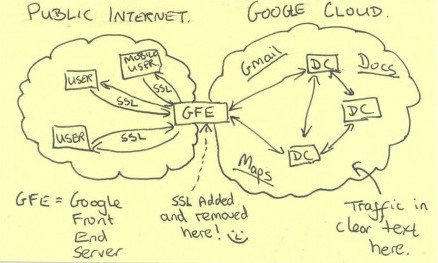
This drawing was published by the Washington Post , which took it from a selection of secret documents merged by Edward Snowden. It schematically depicts how the security service is built into the exchange of information between Google data centers. The notorious smiley emphasized that the NSA had found a cunning way to circumvent the strong cryptographic protection of the Corporation of Good. And the industry came from this excitement.
A new stage in the struggle of the general public for the opportunity to prevent Big Brother from intercepting information circulating in the network has begun. Cryptography began to be embedded wherever possible, including in mobile applications and operating systems. So even those users who had never thought about the struggle between good and evil in the field of applied cryptography were included. Naturally, such mass initiatives rose across the throat of large information control programs implemented by special services of different countries. If earlier large companies that aggregate huge amounts of user information actually served as external databases for any organizations authorized by authority, now cryptography increasingly occurs at different stages of information transfer, allowing legal services to put sticks in wheels.
Obviously, governments are not going to put up with this process. Under the auspices of the fight against world terrorism and other signs, various forms of control over the Internet and other communication channels are being actively promoted. Moreover, the responsibility for developing and embedding interception tools is often assigned to providers and providers of online services who are completely unhappy with these initiatives.
However, the role of cryptography is not limited to keeping the security services from reading our correspondence over the shoulder. Today there is a lot of talk about network neutrality , and encrypted traffic, which the provider is not able to sort, can de facto ensure equal treatment of all online services. In addition, cryptography does not allow embedding advertising cookies into user traffic, which is practiced by a number of large providers.
The implementation of national Internet censorship is also greatly hampered in the context of widespread traffic encryption. True, in many cases, such traffic is now simply blocked by default. But this can continue only as long as most of the information on the Internet remains unencrypted.
Another field of discussion is cryptocurrency circulation. A number of countries have banned their use, believing that cryptocurrencies have a negative impact on the ability of central banks to regulate the movement of finances. However, cryptocurrency algorithms are fairly simple and widely available, so despite the ban, anyone can generate digital money.
It is difficult to say how and when the ongoing struggle between the Internet industry and the authorities will end. Most likely, both those and others will “overcome” each other's virtual territories in which they will establish their own rules of the game. It is unlikely that in the medium term we will come to total control or network anarchy. Time will tell where the cryptography will be fixed, and where it will be pressed in favor of one or another interest.
Source: https://habr.com/ru/post/261371/
All Articles