Vulnerability iOS and OS X, the success of Bethesda, a reward from Google - and other news of the week for a mobile developer

Weekly ios bugs
The last time speech about bugs in iOS and OS X comes so often that it is time to open the heading “Apple's Weekly Bugs”. It is worth noting that in the two previous releases there were reports of blatant, but rather innocuous vulnerabilities: the OS crashes when a certain message is received and it enters an infinite reboot cycle when trying to connect to Wi-Fi. But this time, the Cupertino company surpassed itself , forcing the device owners to think seriously about security.
Apple became aware of a new vulnerability back in October last year, when a group of outside researchers reported about it. Scientists have provided an example of a malicious application, which, without any problems after moderating the App Store and being on the user's device, is able to access Keychain password storage manager. This means that all account data stored on the device is under threat of theft.
')
The company said that it would take half a year to fix the problem - at the moment the vulnerability is not fixed. Google has already removed the integration with Keychain from its Google Chrome browser.
Fallout Shelter overtook Candy Crush Saga

The mobile project from Bethesda ranked third in the top box-office games of the British and American App Store, ahead of Candy Crush. The game reached the first position in the 21st country and in the 38th was in the top five.
The success of the project can really be called impressive, because Candy Crush is the longevity of the top App Stores in many countries. In the top of the grossing of the British side, the candy saga has been in place since December 2012, in the top of the American - since January 2013.
Even more surprisingly, for all that, the developers did not plan a commercially successful project, having released the game rather as a seed before the upcoming Fallout 4. It’s obvious: the monetization in the game is extremely unobtrusive. With this approach, will the application be able to stay in the top for a long time and make a significant profit to its developers, or, having completed the advertising function, will give way to more mercantile competitors - we'll see.
The time spent in applications has grown, but their number is not
Smartphones have long been part of our lives, but the smartphone itself is not very interesting, the set of applications with which the user interacts is important. On the question of how the qualitative and quantitative consumption of applications has changed, analysts from Nielsen tried to answer .
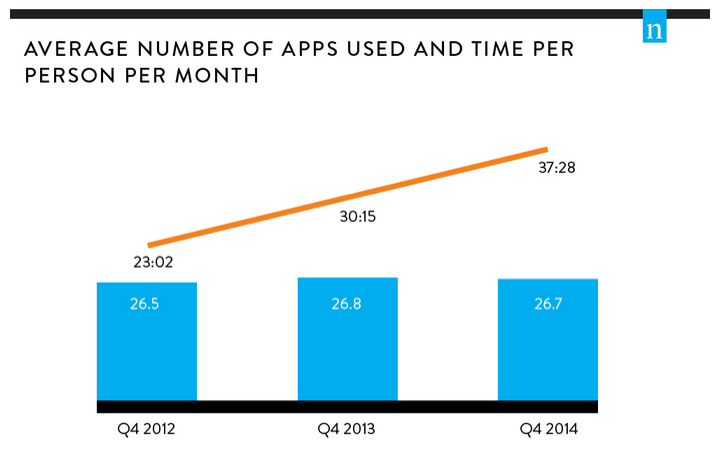
When the data is already known, it seems very logical. According to the data obtained, now a spherical person in a vacuum spends 47 hours and 28 minutes a month with applications. This is significantly more than in 2012 at 23 hours and 2 minutes. By the way, this is not so much, just 1 hour 35 minutes a day. I, for example, by virtue of the profession, spend more :) But the number of applications that we use remained at the same level - on average, 26.7 applications pass through the user per month. Moreover, 70% of them are applications from the Top 200. I suspect that the rest are old applications that are firmly established on users' phones.
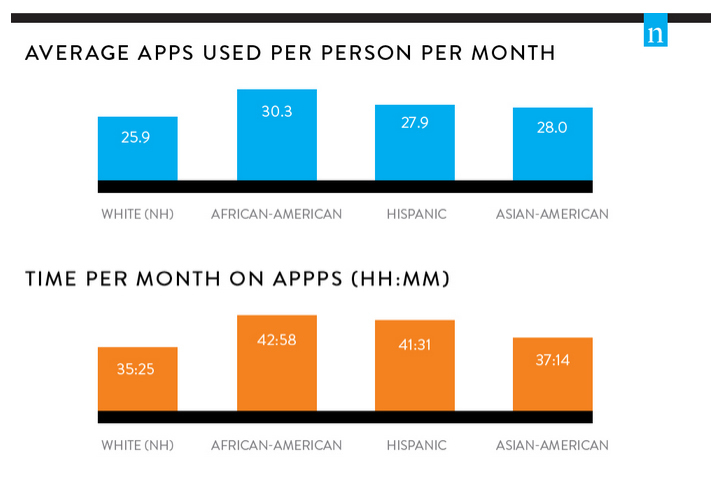
And interestingly, women were more active users - 27.2 versus 26.3, and they spend an hour more time.
Google pays for its mistakes
Google not only recognizes the presence of weak points in its products, but is also willing to pay for their detection. To improve the quality and security of its software, Google decided to attract third-party forces. Now anyone who finds a vulnerability in Android will be rewarded with a special program Android Security Rewards.
The size of the rewards depends on how critical the vulnerability is: from $ 8,000 to $ 30,000. The maximum amount can be obtained, for example, for the TrustZone remote hacking. More information about the devices and OS versions involved in the program can be found on the link .
The company began to cash in on the researchers who discovered the vulnerability from 2010. Since then, $ 4 million has been paid, and $ 1.5 of them just last year. This approach is a good way to pay for the discovered vulnerabilities now, so as not to overpay for their elimination later.
************************************************** ************************************************** *****************************************
If you liked the material and you had time to evaluate the professionalism of the authors of this blog - there is an opportunity to join them. The KamaGames Studio website has a list of vacancies and information about our company. Let's do mobile games together!
Source: https://habr.com/ru/post/261133/
All Articles