Antiviruses at gunpoint: a big hole in ESET and an attack on Kaspersky
The month of June was rich in news on the compromise of the two leaders of the Russian antivirus software market. The first of these stories was told by Kaspersky Lab itself, not without humor, naming the Duqu Bet report and hinting at the Israeli origin of the attackers. However, two days ago, more serious materials appeared on the same topic: the Intercept publication published another revelation of Snowden, which says that the American and British special services back in 2008 “reported on the work done” on hacking Kaspersky's antivirus products.
According to these documents, the British GCHQ studied the products of LC in order to prevent antiviruses from detecting the attacks of special services. And the American NSA was looking for vulnerabilities in the antivirus in order to keep track of users due to the high access privileges that security software receives on their users' computers.
')
In particular, NSA hackers discovered that they can intercept user data that is transmitted from antivirus client to LC servers in the User-Agent line in the HTTP request header. Intersept claims that a month ago it tested this feature on Kaspersky Small Business Security 4, and “although some of the traffic was encrypted, detailed information about the host configuration and the installed software was transmitted to Kaspersky servers without protection.” As proof, a screenshot is shown (the image is clickable):
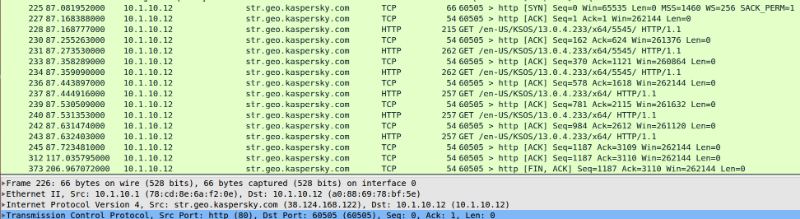
This data Intersept magazine published the day before yesterday, June 22. And just the next day, June 23, a team of researchers from Google (Project Zero) published a report on a more serious vulnerability in ESET NOD32 antivirus . Due to this vulnerability, an attacker can trick the emulator, which is used to check executable codes. The attack allows you to read, modify and delete any files on computers where ESET is installed, as well as install any other programs remotely, access any peripheral devices (cameras, microphones), record all system activity, etc.
The threat affects all versions of ESET and all platforms running ESET (Windows, Mac, OS X). At the same time, as the researchers emphasize, the exploitation of this vulnerability does not require user participation, but uses high system privileges that are given to the ESET scanner - that is, it is an ideal candidate for creating a self-propelled worm (for example, a mail worm). The report includes an example of a working root exploit, as well as a video that demonstrates an attack on ESET through a browser:
You can close the vulnerability with an ESET patch released on June 22 - and before that you can avoid an attack if you disable all scans in ESET (scheduled, real-time and manual). And although this publication by researchers from Google occurred after the release of the patch, it still seems that the publication of this hole somehow “deliberately podgadali” to the general campaign against antivirus programs from Eastern Europe.
Source: https://habr.com/ru/post/261075/
All Articles