Children's camp: Bisectral-Pythagorean triangles, brain reprogramming, radar detector and breaking handcuffs
All events and names are fictional.

Some of the things that I took with me
I thought that I was the most reckless person in the camp until the Yandex teacher arrived. Barefoot. He took a sip of water from the carafe and said: "Eeeh, I used to drink this vodka before." Then he gave a sparkling lecture and “drew” a multitude of elliptic curves.
')
Here is how Alexey Savvateev announced his lecture:
In the magazine “Kvant” number 8 for 1983 in the article “Around the bisector” on page 36 I. F. Sharygin formulates the following task:
“About this triangle it is known that the triangle formed by the bases of its bisectors is isosceles. Is it possible to assert that this triangle is isosceles? ”
The answer is no, but the article further states:
“Unfortunately, the author failed to build a specific example of a triangle (that is, to specify the exact values of all its angles or side lengths) with such an exotic property. Maybe this can be done by the readers of the magazine? ”
Since then, built three examples. The last example leads us to the theory of elliptic curves and the operation of addition of points.
In the lecture, we construct a whole triangle with the desired property. The question of the infinity of such triangles is still open. The school problem, thus, will lead us to the very heart of one of the most beautiful branches of modern mathematics.
The shift is in full swing, we have already managed to do something interesting, but something else is in the plans.
There are obligatory lectures in the camp, there are visiting lecturers, there are workshops, there is independent work on the project. The most interesting thing happensafter the end of the breaks and between events. It is there that I conduct my partisan activities.
I started with the simplest: in order to figure out something, you need to sort it out. This time, the radar detector is asked to be torn apart (not to be confused with an anti-radar detector). Following me, the guys disassembled two laptops, such as repair. (And they found a ruler and a table of recalculation of different quantities inside one of them.)
Past cuts: laser cut, stun gun cut, flashlight cut
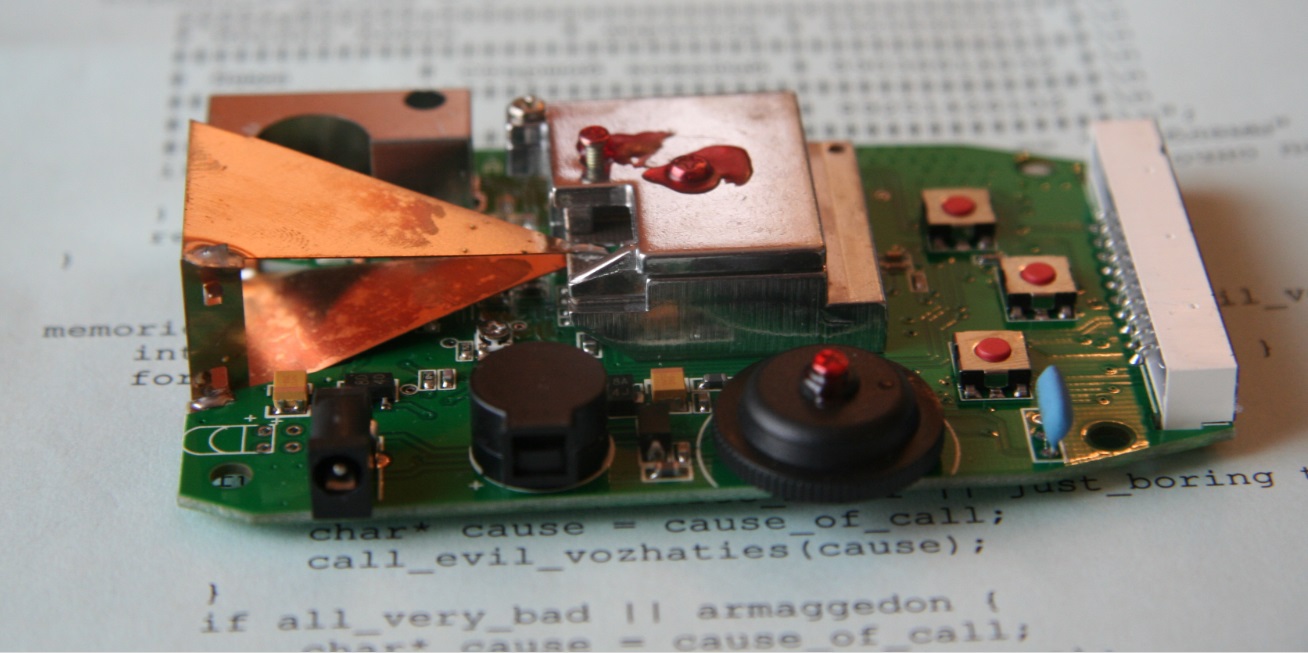
We will understand what the K a and K u ranges are, what the Doppler effect is, what the horn antenna is, how the police radar and lidar work, how the radio signal is jammed and what a laser jammer is.
I wrote a letter to Chris Burma , so that he would answer a couple of questions and inspire the feats of young gemdizaynerov. Let's see what he will answer.
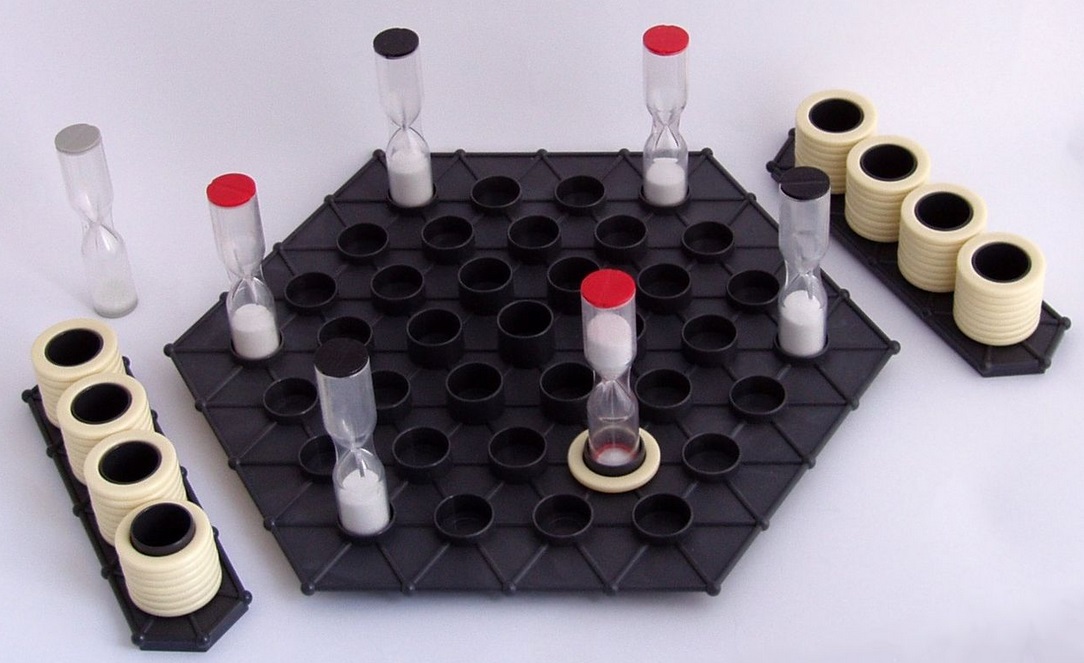
Several games have been released in Russia, but the game with the most interesting gameplay (in my opinion) has been consigned to oblivion. I wanted to reconstruct this masterpiece and give at least one constructive example to the guys. (And then all cut, but hacking).

GIPF (1998) is a bias game, TAMSK (1998) is a pressure game, ZÈRTZ (2000) is a donation game, DVONN (2001) is a mobility game, YINSH (2003) is a game of changes, PÜNCT (2005) is a join game, TZAAR ( 2007) - the game of balance.
First prototype

Work continues, and counselors and children lined up to play it. I hope to have time for the end of the shift. It is a pity that there is a bug: the clock has a different amount of sand, the error in time is up to 20%.

In 2004, German scientists from the University of Osnabruck, led by Peter König, successfully conducted an experiment to introduce a new feeling to a person. The participants of the experiment for a month and a half wore a massive belt with an electronic compass, the sensors of which vibrated while being directed north. They, like birds, learned to feel the magnetic field of the earth, and this is how they tried to describe their sensations: “I intuitively sensed the direction to my home or office. I could stand in line at a cafe and suddenly think: I live there. ” Or: “During the first two weeks I had to concentrate. Then it all happened intuitively. I could even imagine the location of the places and rooms where I once was. ”

Source code for the project

Belt of German colleagues
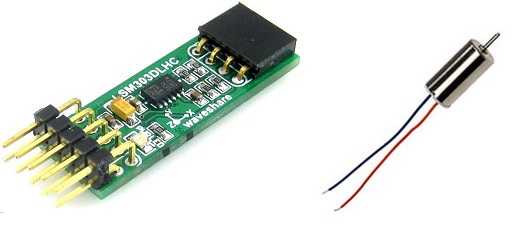
From this we will solder your absolute power belt.
Video about embedding in the brain of new feelings
http://www.youtube.com/watch?v=lmYyhuN0S2c
There are many myths about how handcuffs break open wrappers and toothpicks, break a chain with their hands.
Let's try to debunk the myths about breaking handcuffs and consider all the features and bugs of normal handcuffs that are in any online store.
Hackers crack handcuffs on DefCon
I sit, pick a pin in my handcuffs, and then a polite man in a tie knocked on the house and introduced himself as a security service of a cottage community. I turned a little pale. But it turned out he was interested in the question of whether my favorite Christmas tree would uproot my slackline.

The lecturer told about the games, Simpsons and Griffin in terms of design.

Listened very carefully
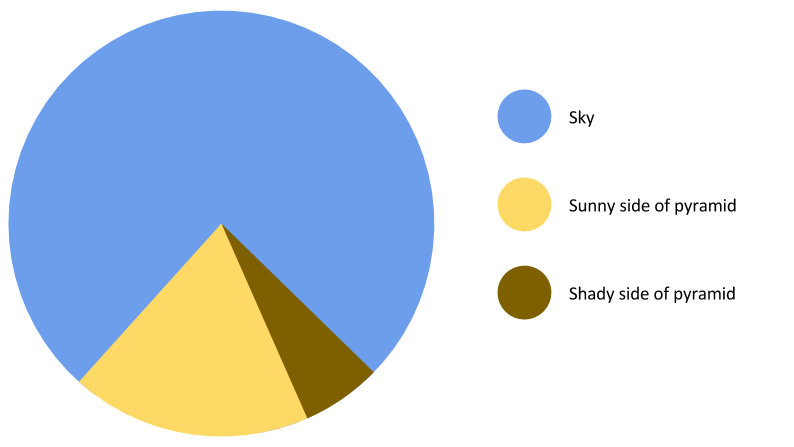
Here is a cool infographics from a lecture that I liked.

The lecture caused nostalgia, remembered how Sharygin came to Vladivostok and did an analysis of the Olympiad tasks. Savvateev burned no worse.
But back to our triangles.
In the course of the simplest calculations, you can come to the formula:
a / (b + c) + b / (a + c) = c / (a + b) is a necessary condition that is satisfied if the small triangle is isosceles, where a, b, c are sides of our original triangle.
The magic is that such a triangle satisfying the conditions is inscribed in the hexahedron

Further, Alexey quickly introduced the projective line, introduced the addition of points, showed how, knowing one rational solution, using the iteration method one can get a bunch of other solutions.

“My friend left mathematics for business. But since in the business the soul dies, and in mathematics the soul resurrects, a friend in the evenings resurrected his soul. He calls me once and says: "I have found."
Integer solution found - 18 800 081, 1 481 089, 19 214 131
This integer triangle is a solution of the form 9A + D
“With my deepest bestial intuition, I sense that a triangle of the form 16A is also integer. Who can program it and check it forward. ”The difficulty is that the length of the numbers doubles when you add the next A.

"For a week I invite you to learn and understand such concepts as field, group, homomorphism, ring ..."
One schoolboy wakes up - “Stop! You can't add points! ”
Naturally, I told him: “Ol'ga, you woke up in the wrong reality.”
- Tuk-tuk, is this Yandex Camp?
- Yes.
- Do you want me to read a mini-course on 3d printing?
- Let's try.
- Tuk-tuk, is it printbox3d? Do you want to be promoted in front of Yandex employees? Then you can provide your 3d printer for 3 weeks.
- It suits us.
It was a year ago, when we explored Mitnick’s book “The Ghost in the Net,” this time next in turn, the book “The Art of Deception”.

A couple of schoolchildren ran to download the book on your tablet.
Let's try to have time to write with students one more article on Habr ( last year’s article )
UPD Translate the Kingpin Book
Task: measure the height of this structure

Ideas:

The remaining tasks of the engineering Olympiad will be a little later.

The basis of the shift - work on projects in a team

The oxygen sensor is monitored by the CO2 sensor.
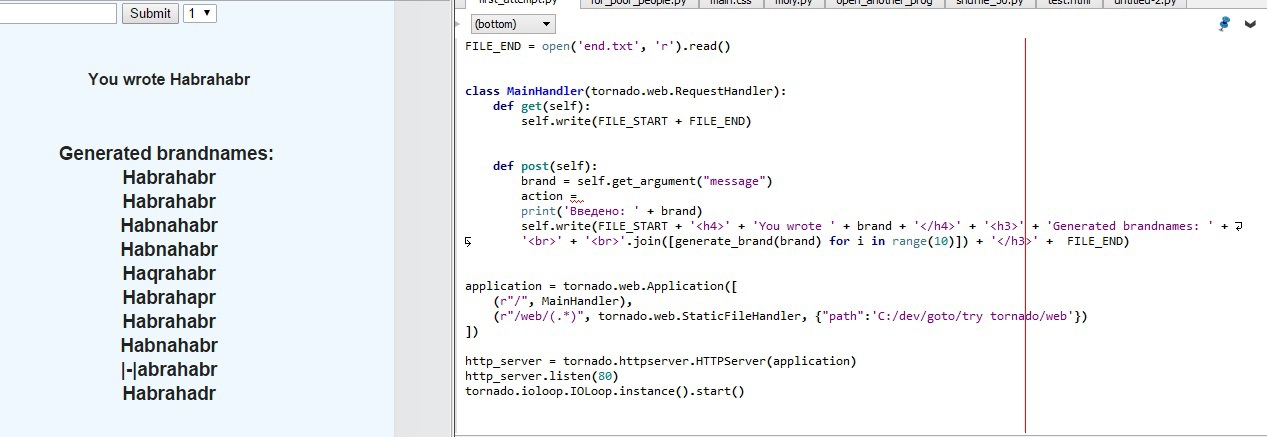
Programmers, meanwhile, code "solvers" of puzzles
and support Chinese manufacturers by helping them invent names like "Abibas"
P.S.
If you have interesting offers of games, tasks,social experiments , offer, there is still time and living children, you can test your hypotheses for free. Well, or share your experience, what tasks you asked the children or what tasks you asked when you were in the camp.
P.P.S.


Some of the things that I took with me
I thought that I was the most reckless person in the camp until the Yandex teacher arrived. Barefoot. He took a sip of water from the carafe and said: "Eeeh, I used to drink this vodka before." Then he gave a sparkling lecture and “drew” a multitude of elliptic curves.
')
Here is how Alexey Savvateev announced his lecture:
In the magazine “Kvant” number 8 for 1983 in the article “Around the bisector” on page 36 I. F. Sharygin formulates the following task:
“About this triangle it is known that the triangle formed by the bases of its bisectors is isosceles. Is it possible to assert that this triangle is isosceles? ”
The answer is no, but the article further states:
“Unfortunately, the author failed to build a specific example of a triangle (that is, to specify the exact values of all its angles or side lengths) with such an exotic property. Maybe this can be done by the readers of the magazine? ”
Since then, built three examples. The last example leads us to the theory of elliptic curves and the operation of addition of points.
In the lecture, we construct a whole triangle with the desired property. The question of the infinity of such triangles is still open. The school problem, thus, will lead us to the very heart of one of the most beautiful branches of modern mathematics.
The shift is in full swing, we have already managed to do something interesting, but something else is in the plans.
There are obligatory lectures in the camp, there are visiting lecturers, there are workshops, there is independent work on the project. The most interesting thing happens
I started with the simplest: in order to figure out something, you need to sort it out. This time, the radar detector is asked to be torn apart (not to be confused with an anti-radar detector). Following me, the guys disassembled two laptops, such as repair. (And they found a ruler and a table of recalculation of different quantities inside one of them.)
Past cuts: laser cut, stun gun cut, flashlight cut
Radar detector

We will understand what the K a and K u ranges are, what the Doppler effect is, what the horn antenna is, how the police radar and lidar work, how the radio signal is jammed and what a laser jammer is.
Saw the game TAMSK
“I never thought that I would become a professional game author. Just once the idea of an abstract game came to my mind, something between a puzzle and a cube-rubik. For 4 days I made it. A couple of years later, sitting in a bar, I met a guy who claimed that he was inventing board games. I told him about my game, he showed interest, came to visit me and carefully looked at her. And the next day I went and registered it in my name. There was little enjoyment here, but instead of filling his face with him, I decided to come up with a couple more games. That guy showed me that your ideas can somehow be implemented. If not for him, I would not do what I am doing now. " Chris Burme

I wrote a letter to Chris Burma , so that he would answer a couple of questions and inspire the feats of young gemdizaynerov. Let's see what he will answer.
Several games have been released in Russia, but the game with the most interesting gameplay (in my opinion) has been consigned to oblivion. I wanted to reconstruct this masterpiece and give at least one constructive example to the guys. (And then all cut, but hacking).

GIPF (1998) is a bias game, TAMSK (1998) is a pressure game, ZÈRTZ (2000) is a donation game, DVONN (2001) is a mobility game, YINSH (2003) is a game of changes, PÜNCT (2005) is a join game, TZAAR ( 2007) - the game of balance.
English Rules
Territorial game with a special feature.
The second game of Project GIPF. For 2 players.
Components
- 1 game board
- 3 red and 3 black hour-glasses (3 min.)
- 1 neutral hour-glass (15-second timer)
- 64 ivory rings
- 2 ring holders, each to hold 32 rings
Set-up
1. Starting position: see diagram below. See the alternating: black, red, black, red, black, red. The upper parts must be empty before starting a game.
2. Take a ring holder and fill it with 32 rings.
Aim
You and your opponent start the game with 32 rings each. The player is the winner. (This counts for all 3 levels.)
It is not necessary to make it.
Glasses without turning them over. Hour-glasses.
1. Start:
Draw lots to determine red hour-glasses. Red begins, then take turns moving your hour-glasses.
2. A move:
Each one of your hour-glasses. You can move it to any adjacent vacant space.
3. Dropping a ring:
After moving an hour-glass, you can play one ring: take it a ring from your ringholder; (For the remainder of the game, you will have to go through the ring before it’s been indicated earlier.)
Note: Since he wasn’t If you’re on a ring, you’ll still be able to make your regular move.
4. The different spaces:
The spaces (tubes) on the board have different heights. Once the rings have been ringed, it’s not.
· 18 spaces around the edge of the board.
· The next tier of 12 spaces may have a maximum of 2 rings.
· The inner tier of 6 spaces may have a maximum of 3 rings.
· The central space may have 4 rings.
Note: You can never move it. If you do, you lose the game at once. So, watch the rings carefully.
5. Passing your turn:
You must not be able to move on your turn. You need to move again - or until the game ends.
6. The end:
Ends can be made. The player with the fewest rings left wins the game. He has no idea what to lose. It’s not a bad idea.
7. A tie:
If the players have their hands on them
The second level is played with the rules for the hour-glasses. The 15-second hour-glass is still left out of the game. It is the time of your strategy.
Note: Level 1 is a level 3; Level 2 is an intermediate level; introduction to level 3.
1. Start:
The starting position remains the same.
2. The first 3 turns:
You and your opponent are obliged to be your 3 hour-glasses. When moving an hour-glass, it must be turned over. Your opponent has been making 3 moves.
3. A move:
You need to keep your hour-glasses alive. Each time you move it, it must be turned over. The time of one of your hour-glasses. A move must be made with a fluid motion; you may not keep an hour-glass in a horizontal position. You can’t let your opponent go. (See point 5 below: Timing of a move.)
4. Dropping a ring:
After moving an hour-glass, you may still play a ring. But you can do it immediately. If you don’t, you lose that ring. As described below, you can choose a ring for your opponent.
5. Timing of a move:
You may need your opponent to start his move. In other words, you have been dropped your ring. If he didn’t play one ring
6. Losing an hour-glass:
When it comes out of time, it is lost. But no matter what.
Note: you may lose an hour-glass on purpose!
7. 15-second rule:
Even though you don’t have to use the “gentlemen’s agreement” (Since it is a “gentlemen’s agreement” only, it’s not a penalty. Just play quickly.)
8. The end:
Remains the same: how many rings as possible.
9. No more tie:
Unlike level 1, this level cannot end in a tie. If you’re on the left, then it’s time to determine the winner:
Remove
· Watch the remaining hour-glasses closely. It is taken from the board to be baked.
Hour player hour player with
Players both both players players players players run run run
The game was played during the 15-second timer. This is a 15-second hour-glass.
1. Start:
Red begins; It’s time for the board
2. The 15-second rule:
The 15-second hour-glass is not obliged to use it. You can use it (ie turn it over) for 15 seconds. Of course, your opponent may use it too when it is your turn.
3. The use:
It’s easy to use it. So, it is possible to wait until it runs out.
He wasn’t his move; until the 15-second timer is empty.
4. Private:
If you’ve been running out of time, you can’t get it. , including dropping a ring. Your opponent may now have his turn. It’s not a problem. hour-glass (of either color) or not. Of course, it is not possible at all possible.
Note: this is an adjusted rule. This was the end of the game. That is fixed with this new rule.
5. Timing:
He hasn’t been able to move his car, so he hasn’t gotten his time. until your opponent releases the hour-glass).
6. Passing a turn:
If the 15-second timer runs out of time, you forfeit that turn. It is not clear that you can’t get it.
This is not counting as you pass by a turn. So, in this case the opponent may not drop 2 rings.
7. The end:
The game ends as described under level 1 and 2.
Option
It is also possible to have a game with the TAMSK. If you want to make it, then you can start dropping rings.
Enjoy the pressure!
The second game of Project GIPF. For 2 players.
Components
- 1 game board
- 3 red and 3 black hour-glasses (3 min.)
- 1 neutral hour-glass (15-second timer)
- 64 ivory rings
- 2 ring holders, each to hold 32 rings
Set-up
1. Starting position: see diagram below. See the alternating: black, red, black, red, black, red. The upper parts must be empty before starting a game.
2. Take a ring holder and fill it with 32 rings.
Aim
You and your opponent start the game with 32 rings each. The player is the winner. (This counts for all 3 levels.)
The game
It is not necessary to make it.
Level 1: without time pressure
Glasses without turning them over. Hour-glasses.
1. Start:
Draw lots to determine red hour-glasses. Red begins, then take turns moving your hour-glasses.
2. A move:
Each one of your hour-glasses. You can move it to any adjacent vacant space.
3. Dropping a ring:
After moving an hour-glass, you can play one ring: take it a ring from your ringholder; (For the remainder of the game, you will have to go through the ring before it’s been indicated earlier.)
Note: Since he wasn’t If you’re on a ring, you’ll still be able to make your regular move.
4. The different spaces:
The spaces (tubes) on the board have different heights. Once the rings have been ringed, it’s not.
· 18 spaces around the edge of the board.
· The next tier of 12 spaces may have a maximum of 2 rings.
· The inner tier of 6 spaces may have a maximum of 3 rings.
· The central space may have 4 rings.
Note: You can never move it. If you do, you lose the game at once. So, watch the rings carefully.
5. Passing your turn:
You must not be able to move on your turn. You need to move again - or until the game ends.
6. The end:
Ends can be made. The player with the fewest rings left wins the game. He has no idea what to lose. It’s not a bad idea.
7. A tie:
If the players have their hands on them
Level 2: with time pressure
The second level is played with the rules for the hour-glasses. The 15-second hour-glass is still left out of the game. It is the time of your strategy.
Note: Level 1 is a level 3; Level 2 is an intermediate level; introduction to level 3.
1. Start:
The starting position remains the same.
2. The first 3 turns:
You and your opponent are obliged to be your 3 hour-glasses. When moving an hour-glass, it must be turned over. Your opponent has been making 3 moves.
3. A move:
You need to keep your hour-glasses alive. Each time you move it, it must be turned over. The time of one of your hour-glasses. A move must be made with a fluid motion; you may not keep an hour-glass in a horizontal position. You can’t let your opponent go. (See point 5 below: Timing of a move.)
4. Dropping a ring:
After moving an hour-glass, you may still play a ring. But you can do it immediately. If you don’t, you lose that ring. As described below, you can choose a ring for your opponent.
5. Timing of a move:
You may need your opponent to start his move. In other words, you have been dropped your ring. If he didn’t play one ring
6. Losing an hour-glass:
When it comes out of time, it is lost. But no matter what.
Note: you may lose an hour-glass on purpose!
7. 15-second rule:
Even though you don’t have to use the “gentlemen’s agreement” (Since it is a “gentlemen’s agreement” only, it’s not a penalty. Just play quickly.)
8. The end:
Remains the same: how many rings as possible.
9. No more tie:
Unlike level 1, this level cannot end in a tie. If you’re on the left, then it’s time to determine the winner:
Remove
· Watch the remaining hour-glasses closely. It is taken from the board to be baked.
Hour player hour player with
Players both both players players players players run run run
Level 3: with the 15-second timer
The game was played during the 15-second timer. This is a 15-second hour-glass.
1. Start:
Red begins; It’s time for the board
2. The 15-second rule:
The 15-second hour-glass is not obliged to use it. You can use it (ie turn it over) for 15 seconds. Of course, your opponent may use it too when it is your turn.
3. The use:
It’s easy to use it. So, it is possible to wait until it runs out.
He wasn’t his move; until the 15-second timer is empty.
4. Private:
If you’ve been running out of time, you can’t get it. , including dropping a ring. Your opponent may now have his turn. It’s not a problem. hour-glass (of either color) or not. Of course, it is not possible at all possible.
Note: this is an adjusted rule. This was the end of the game. That is fixed with this new rule.
5. Timing:
He hasn’t been able to move his car, so he hasn’t gotten his time. until your opponent releases the hour-glass).
6. Passing a turn:
If the 15-second timer runs out of time, you forfeit that turn. It is not clear that you can’t get it.
This is not counting as you pass by a turn. So, in this case the opponent may not drop 2 rings.
7. The end:
The game ends as described under level 1 and 2.
Option
It is also possible to have a game with the TAMSK. If you want to make it, then you can start dropping rings.
Enjoy the pressure!
First prototype

Work continues, and counselors and children lined up to play it. I hope to have time for the end of the shift. It is a pity that there is a bug: the clock has a different amount of sand, the error in time is up to 20%.
Sensory replacement and neuroplasticity

In 2004, German scientists from the University of Osnabruck, led by Peter König, successfully conducted an experiment to introduce a new feeling to a person. The participants of the experiment for a month and a half wore a massive belt with an electronic compass, the sensors of which vibrated while being directed north. They, like birds, learned to feel the magnetic field of the earth, and this is how they tried to describe their sensations: “I intuitively sensed the direction to my home or office. I could stand in line at a cafe and suddenly think: I live there. ” Or: “During the first two weeks I had to concentrate. Then it all happened intuitively. I could even imagine the location of the places and rooms where I once was. ”

Source code for the project

Belt of German colleagues

From this we will solder your absolute power belt.
Video about embedding in the brain of new feelings
http://www.youtube.com/watch?v=lmYyhuN0S2c
Handcuffs
There are many myths about how handcuffs break open wrappers and toothpicks, break a chain with their hands.
Let's try to debunk the myths about breaking handcuffs and consider all the features and bugs of normal handcuffs that are in any online store.
Hackers crack handcuffs on DefCon
I sit, pick a pin in my handcuffs, and then a polite man in a tie knocked on the house and introduced himself as a security service of a cottage community. I turned a little pale. But it turned out he was interested in the question of whether my favorite Christmas tree would uproot my slackline.

Lecture from Rambler
The lecturer told about the games, Simpsons and Griffin in terms of design.

Listened very carefully
Here is a cool infographics from a lecture that I liked.

Lecture from Yandex

The lecture caused nostalgia, remembered how Sharygin came to Vladivostok and did an analysis of the Olympiad tasks. Savvateev burned no worse.
But back to our triangles.
In the course of the simplest calculations, you can come to the formula:
a / (b + c) + b / (a + c) = c / (a + b) is a necessary condition that is satisfied if the small triangle is isosceles, where a, b, c are sides of our original triangle.
The magic is that such a triangle satisfying the conditions is inscribed in the hexahedron

Further, Alexey quickly introduced the projective line, introduced the addition of points, showed how, knowing one rational solution, using the iteration method one can get a bunch of other solutions.

“My friend left mathematics for business. But since in the business the soul dies, and in mathematics the soul resurrects, a friend in the evenings resurrected his soul. He calls me once and says: "I have found."
Integer solution found - 18 800 081, 1 481 089, 19 214 131
This integer triangle is a solution of the form 9A + D
“With my deepest bestial intuition, I sense that a triangle of the form 16A is also integer. Who can program it and check it forward. ”The difficulty is that the length of the numbers doubles when you add the next A.

"For a week I invite you to learn and understand such concepts as field, group, homomorphism, ring ..."
One schoolboy wakes up - “Stop! You can't add points! ”
Naturally, I told him: “Ol'ga, you woke up in the wrong reality.”
Video with other lectures by Alexey Savvateev
Social engineering
- Tuk-tuk, is this Yandex Camp?
- Yes.
- Do you want me to read a mini-course on 3d printing?
- Let's try.
- Tuk-tuk, is it printbox3d? Do you want to be promoted in front of Yandex employees? Then you can provide your 3d printer for 3 weeks.
- It suits us.
It was a year ago, when we explored Mitnick’s book “The Ghost in the Net,” this time next in turn, the book “The Art of Deception”.

My transition from telephone phreaking to hacking occurred in high school when I ran into so-called social engineering and met another student who was also keen on phreaking. Phone phreaking is a form of hacking when you explore telephone networks, exploiting telephone systems and employees of telephone companies. He showed me some tricks he could do with phones, such as getting any information from the telephone company about its customers and using secret test numbers to make free long distance calls. Free only for us - much later I found out that these were not secret numbers at all: accounts came to some MCI subscriber. It was my acquaintance with social engineering - my kindergarten, so to speak. He and another phone phreaker, which I met later, let me listen to my calls to the telephone company. I learned how to make myself sound convincing and learned about the various offices and procedures of the telephone company. But this "training" did not last long. Soon I did it all myself, even better than my first teachers. The direction of my life for the next 15 years has been determined.
One of my favorite jokes was the seizure of unauthorized access to the telephone switchboard and the substitution of the class of the telephone service of my fellow phreaking. When he wanted to call from home, he received a message to lower the dime, because the telephone company’s switchboard perceived his phone as a public pay phone.
I studied everything related to telephones: not only electronics, switches and computers, but also corporate organization, procedures and terminology. Soon, I probably knew more about the telephone system than any of the employees.
And I developed my social engineering skills to such an extent that by the age of 17, I could talk with most of the Telco employees about almost anything, personally or by phone. My hacking career began in high school . Then we used the term hacker to a person who spent a tremendous amount of time digging with software and hardware, developing more effective programs or eliminating everything unnecessary to make work faster .
At the end of 1979 ( Kevin, 16 ), a group of hackers from the Los Angeles Unified School District suggested that I hack The Ark, a computer system from Digital Equipment Corporation, which was used to develop software for their RSTS / E operating system. I wanted to be accepted into this hacker group so that I could learn from them more about operating systems. These new “friends” knew the dial-up number of the DEC computer system. But they could not enter without an account name and password. When you underestimate someone, he can come back and strike from the flank. In this case, it was me who managed to hack the DEC system at such a young age. Posing as Anton Chernoff, one of the leading developers of the project, I just called the system administrator. I stated that I could not log into one of “my” accounts, and convinced this guy enough to give me access and let me choose a password on my own. In extra class protection, any user connecting to the system had to enter a dial-up password. The system administrator gave it to me. It was the password “buffoon” (clown), which, I think, he felt when it became clear what had happened. In less than 10 minutes, I got access to the DEC RSTE / E system. And I did not log in as a regular user, I had all the privileges of a system developer. At first, my new so-called friends did not believe that I had access to The Ark. One of them shoved me away from the keyboard with a face that expressed disbelief. His mouth opened when he saw that I was in a privileged account. Later, I discovered that they began copying the source code of the components to the DEC operating system. Now it was my turn to be surprised. When they copied the software, they called the security department of DEC Corporation and said that some had hacked into the company's corporate network. And they gave my name. My so-called friends first used my access to the high-security source code, and then they framed me.
It was a lesson, and more than one such lesson I had to learn. After a few years, I repeatedly ran into trouble, because I trusted people whom I considered to be my friends. After school, I studied computers at the Los Angeles Computer Training Center.
A few months later, my school computer administrator realized that I had discovered a vulnerability in their operating system and received full administrator privileges on their IBM minicomputer. The best computer experts from their teaching staff could not find how I did it. It was one of my early experiences of hiring. They made me an offer I couldn’t refuse: to make an honorable project to improve the security of a school computer or to face the charges of hacking the system. Of course, I chose the honorable project and with Honor I graduated from Cum Laude.
A couple of schoolchildren ran to download the book on your tablet.
Let's try to have time to write with students one more article on Habr ( last year’s article )
UPD Translate the Kingpin Book
Engineering Olympiad
Task: measure the height of this structure

Ideas:
- measure the speed of sound (did not)
- throw sneakers and measure the time of the fall (did not)
- sfotali with a man nearby and measured on a photo in parrots
- figured that the height is equal to the radius, and the radius measured
- a) in steps
b) growth
c) plates

The remaining tasks of the engineering Olympiad will be a little later.
Projects

The basis of the shift - work on projects in a team
Read more
At first, this is how all the projects looked.
Some have not stood the test.
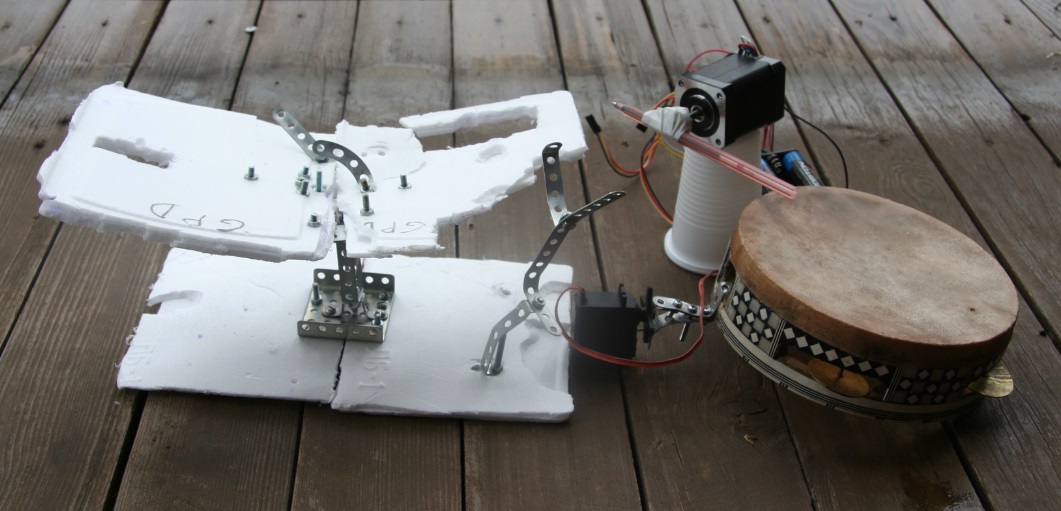
The remains of an amphibious robot met with the remnants of a robot drummer
Some successfully function
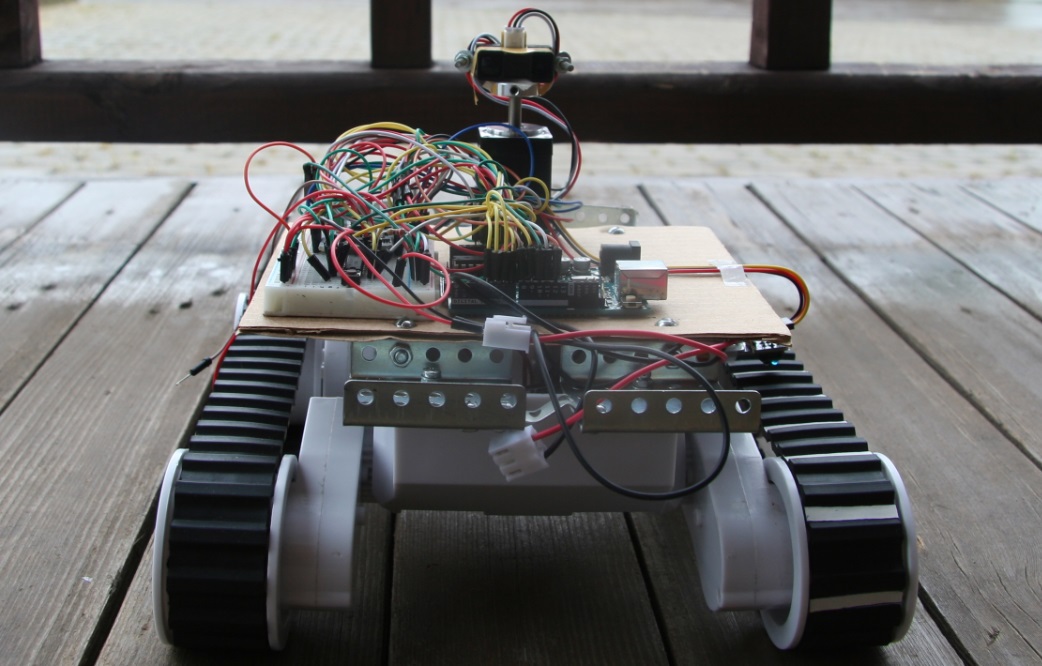
Room mapping robot scanner
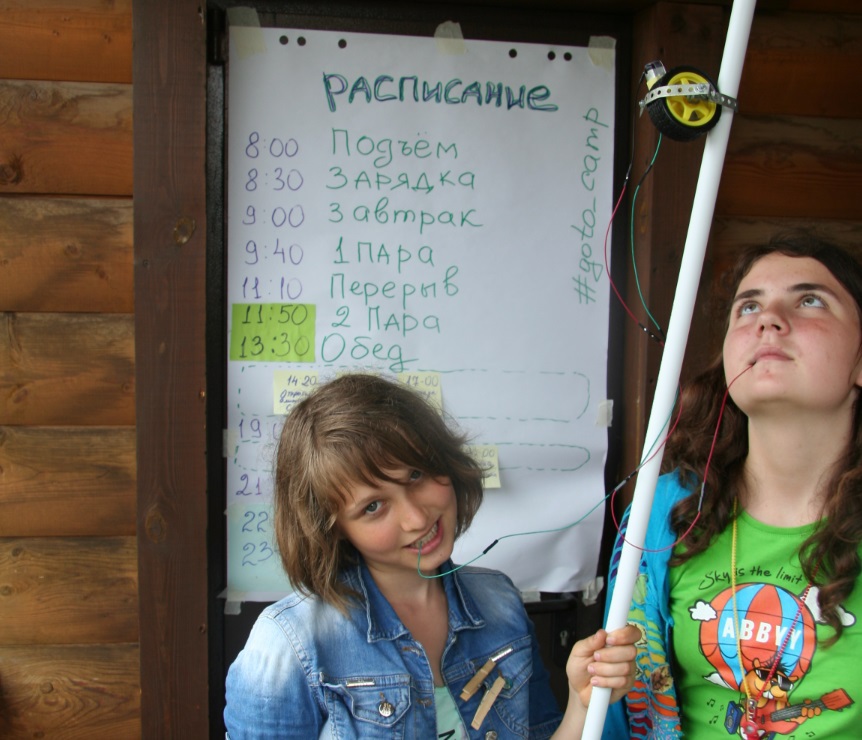
Robot-rider on a stick, to help cameramen

At first, this is how all the projects looked.
Some have not stood the test.

The remains of an amphibious robot met with the remnants of a robot drummer
Some successfully function

Room mapping robot scanner
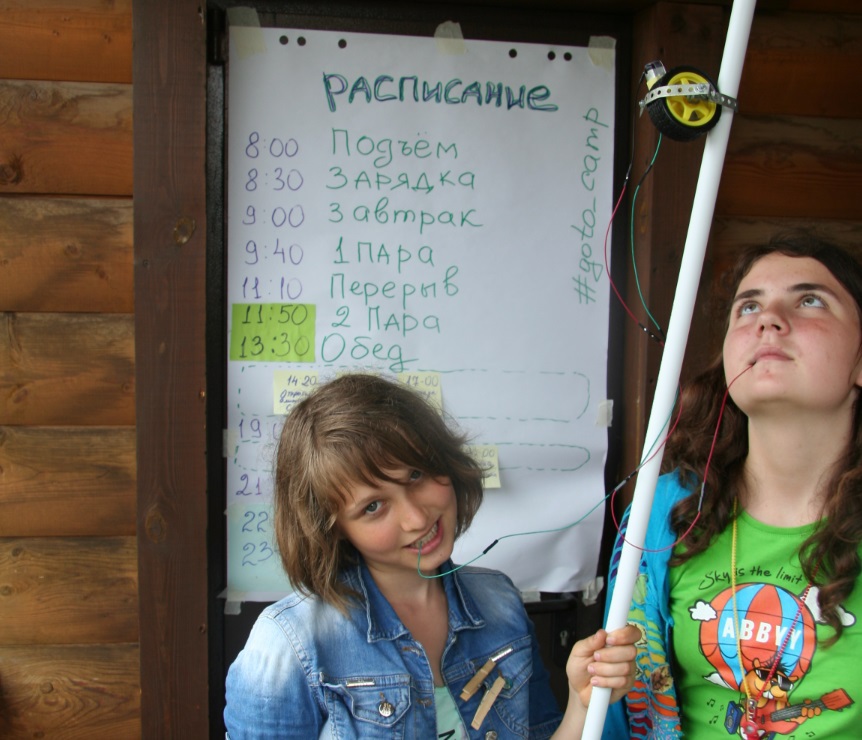
Robot-rider on a stick, to help cameramen

The oxygen sensor is monitored by the CO2 sensor.
Programmers, meanwhile, code "solvers" of puzzles

and support Chinese manufacturers by helping them invent names like "Abibas"

P.S.
If you have interesting offers of games, tasks,
P.P.S.

Source: https://habr.com/ru/post/261041/
All Articles