Monitoring and alerting about events in Windows logs: sending to E-mail in Windows Server 2012 R2
Not so long ago, in order to successfully pass an audit for compliance with PCI DSS standards, it was necessary to enable auditing of Windows server events and, most importantly, to set up sending notifications of critical events to E-mail. For Linux servers, the issue is solved by installing and configuring OSSEC (well, syslog ws loganalyzer and auditd may also be needed), for Windows Server 2012 R2, and even the Russian version, it did not fit (later we managed to configure it adequately, if it’s interesting, I can describe as). So we decided to look for other ways ...
The first thing to do is to include an audit of all necessary operations (account management and file integrity control) in the domain policy. And if everything is simple with the audit of operations on Active Directory objects, then you have to tinker with the audit of file operations. Here, at an opportune time, the company Netwrix (do not consider it an advertisement, the company is the author of commercial audit software) prepared a wonderful article: “Setting up an audit of file servers: detailed instructions and a cheat sheet” (.pdf).
But back to our "crutches". After successful activation of the audit of all the necessary operations and detection of events of interest in the Windows logs, the question arose of sending them to the monitoring server ... It would be logical to use the built-in tools (" Attach Task To This Event " is not the most informative tool, but native for Windows ), but here the first curious and unpleasant moment from Microsoft comes up - “Send an email message and display a message . ”
')
According to the recommendations from Microsoft, as a replacement for the built-in “deprecated” functionality, they decided to use PowerShell scripts to filter the logs and send by E-mail, since there are detailed instructions:
"Active Directory Audit Powershell Change Alert . "
“Audit of deleting and accessing files and recording events to a log file using Powershell”
But then another difficulty arose: the above scripts sent only the headers (themes) of events to the E-mail, the message body was empty :( For all this, if you run the PowerShell script in ISE PowerShell "as Administrator", then the full message comes, as it was intended!
In general, if you have real working scripts for such a case - you are welcome in the comments.
We switched to another method (inspired by this article: " Monitoring and notifying about events in Windows logs: event triggers " and rescued this utility: sendEmail ):
As a result, should get something like this:
PS Thanks to all the authors of the sources mentioned earlier!
The first thing to do is to include an audit of all necessary operations (account management and file integrity control) in the domain policy. And if everything is simple with the audit of operations on Active Directory objects, then you have to tinker with the audit of file operations. Here, at an opportune time, the company Netwrix (do not consider it an advertisement, the company is the author of commercial audit software) prepared a wonderful article: “Setting up an audit of file servers: detailed instructions and a cheat sheet” (.pdf).
But back to our "crutches". After successful activation of the audit of all the necessary operations and detection of events of interest in the Windows logs, the question arose of sending them to the monitoring server ... It would be logical to use the built-in tools (" Attach Task To This Event " is not the most informative tool, but native for Windows ), but here the first curious and unpleasant moment from Microsoft comes up - “Send an email message and display a message . ”
')
Send an e-mail (deprecated)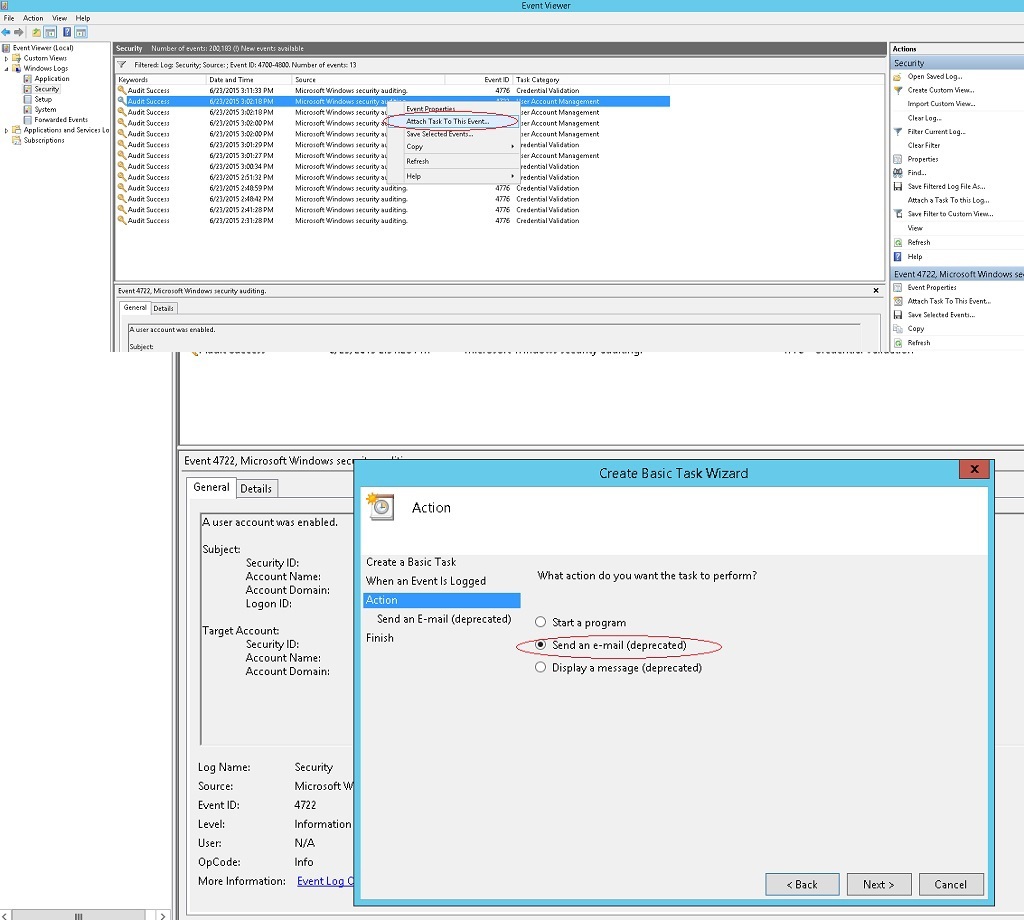
...
According to the recommendations from Microsoft, as a replacement for the built-in “deprecated” functionality, they decided to use PowerShell scripts to filter the logs and send by E-mail, since there are detailed instructions:
"Active Directory Audit Powershell Change Alert . "
“Audit of deleting and accessing files and recording events to a log file using Powershell”
But then another difficulty arose: the above scripts sent only the headers (themes) of events to the E-mail, the message body was empty :( For all this, if you run the PowerShell script in ISE PowerShell "as Administrator", then the full message comes, as it was intended!
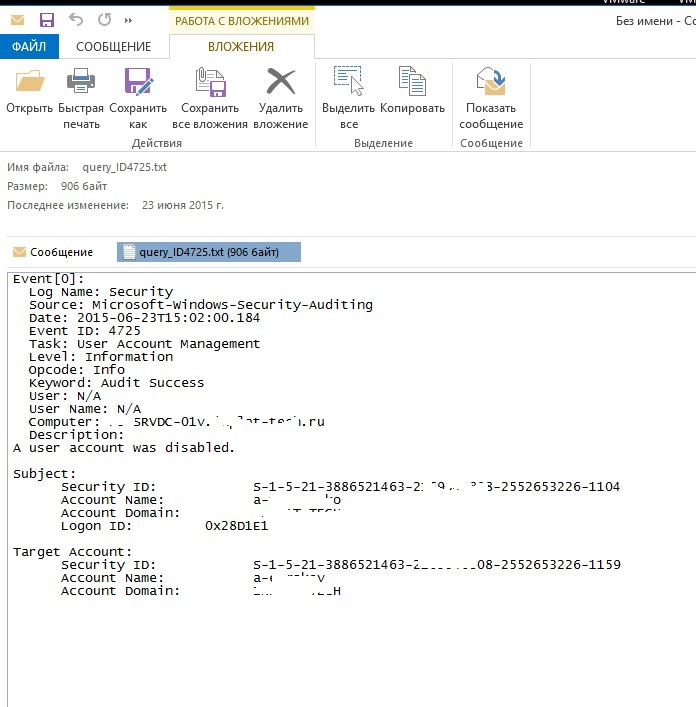
An example of the script to send a notification about the event "Account is blocked" - Event ID 4725:
$time = (get-date) - (new-timespan -min 60) $Subject = “ " $Theme = “ ” $Server = “smtp.server.local” $From = “AD@domain.local” $To = “support@domain.local” $encoding = [System.Text.Encoding]::UTF8 # ID. $TimeSpan = new-TimeSpan -sec 1 foreach($event in $events) { $PrevEvent = $Event. $PrevEvent = $PrevEvent - 1 $TimeEvent = $Event.TimeCreated $TimeEventEnd = $TimeEvent+$TimeSpan $TimeEventStart = $TimeEvent- (new-timespan -sec 1) $Body=Get-WinEvent -maxevents 1 -FilterHashtable @{LogName=”Security”;ID=4725;StartTime=$TimeEventStart;} | Select TimeCreated,@{n=”Account Name”;e={([xml]$_.ToXml()).Event.EventData.Data | ? {$_.Name -eq “TargetUserName”} |%{$_.'#text'}}},@{n=”Computer”;e={([xml]$_.ToXml()).Event.EventData.Data | ? {$_.Name -eq “TargetDomainName”}| %{$_.'#text'}}} $body = $body -replace "@{" -replace "}" -replace "=", ": " -replace ";","`n" -replace "TimeCreated"," " -replace "^","`n" $BodyM = $Body } Send-MailMessage -From $From -To $To -SmtpServer $server -Body “$BodyM `n$Theme” -Subject $Subject -Encoding $encoding In general, if you have real working scripts for such a case - you are welcome in the comments.
We switched to another method (inspired by this article: " Monitoring and notifying about events in Windows logs: event triggers " and rescued this utility: sendEmail ):
- Add a task for the event of interest to the Task Scheduler (directly from the " Security " -> " Attach Task To This Event ... " log)

- In Actions, we specify the launch of the script, in which we use the wevtutil utility to make a selection from the log and save the result to a file.script example - event selection with Event ID 4726
del c:\Audit\query_ID4726.txt wevtutil qe Security /q:"*[System[(EventID=4726)]]" /f:text /rd:true /c:1 > c:\Audit\query_ID4726.txt - In the second step, using the sendEmail utility, we send the saved file to the destination:example arguments for the sendEmail start command:
-f audit_AD@domain.local -s smtp.domain.local:25 -t support@domain.local -m "AD User Account Management - Event ID 426 - Account was Deleted" -a C:\Audit\query_ID4726.txt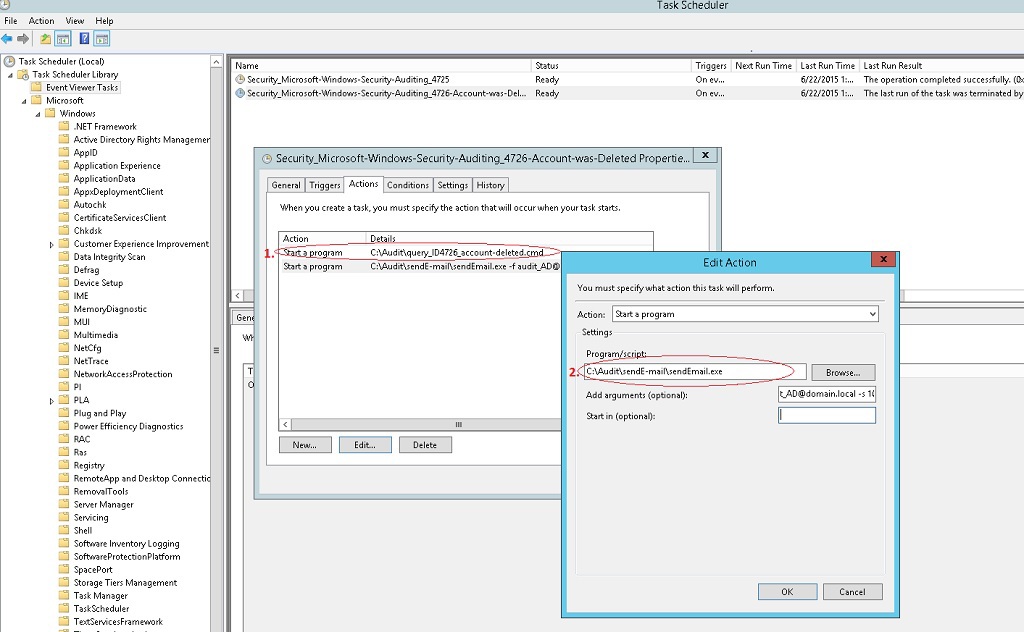
As a result, should get something like this:

PS Thanks to all the authors of the sources mentioned earlier!
Source: https://habr.com/ru/post/260947/
All Articles