Attackers used stolen digital certificate for Duqu2 malicious campaign
A few days ago, an executable PE file (driver) was received in our anti-virus laboratory, which contained a valid digital signature. We added it to the database as Win64 / Duqu.AC. The certificate was issued by a well-known Taiwanese company Foxconn (Hon Hai Precision Industry Co.), which specializes in the production of electronics, and is also one of the largest companies engaged in the production of components of the flagship devices of such famous companies as Apple, Canon, Sony.

Earlier we wrote about this malicious campaign, in which attackers used the new version of the state-sponsored malware Duqu (Duqu2, Duqu.B), as well as about other detections of this malware from our AV products. The specified driver is small (27,448 bytes) and is used by attackers to manipulate network traffic at the NDIS level in the compromised system.
')
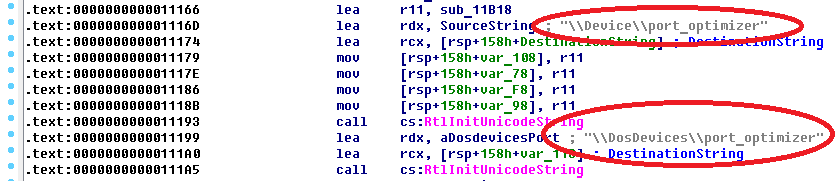
Fig. The name of the device object, as well as the symbolic link that the malicious driver creates in the system (infection indicator).
Already from the information on the driver import (ndis.sys), it is clear that it specializes in working with network traffic at the NDIS level.

Fig. Part of the imported Win64 / Duqu.AC functions.

Fig. Valid digital signature Win64 / Duqu.AC. The compromised certificate was still valid.
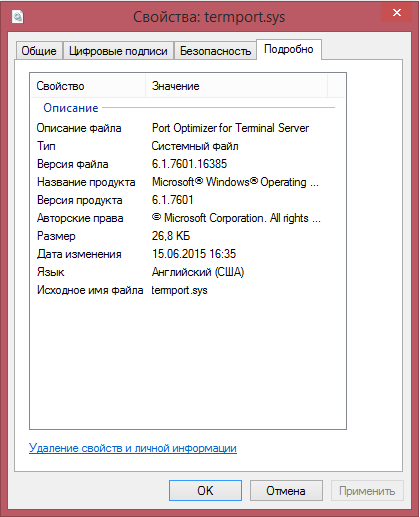
Fig. Properties of the malicious file.
The theft of the digital certificate is related to the malicious campaign to spread Duqu2 with another malicious company spreading the famous worm Stuxnet , its drivers also contained a digital signature, and the certificates were also stolen from technology companies: JMicron and Realtek. Supplying a malicious driver with a digital signature is a one hundred percent solution to ensure that such a driver is loaded in a 64-bit version of Windows.
The specified driver has the following prints:
MD5: 92e724291056a5e30eca038ee637a23f
SHA1: 478c076749bef74eaf9bed4af917aee228620b23
SHA256: bc4ae56434b45818f57724f4cd19354a13e5964fd097d1933a30e2e31c9bdfa5

Earlier we wrote about this malicious campaign, in which attackers used the new version of the state-sponsored malware Duqu (Duqu2, Duqu.B), as well as about other detections of this malware from our AV products. The specified driver is small (27,448 bytes) and is used by attackers to manipulate network traffic at the NDIS level in the compromised system.
')

Fig. The name of the device object, as well as the symbolic link that the malicious driver creates in the system (infection indicator).
Already from the information on the driver import (ndis.sys), it is clear that it specializes in working with network traffic at the NDIS level.

Fig. Part of the imported Win64 / Duqu.AC functions.

Fig. Valid digital signature Win64 / Duqu.AC. The compromised certificate was still valid.

Fig. Properties of the malicious file.
The theft of the digital certificate is related to the malicious campaign to spread Duqu2 with another malicious company spreading the famous worm Stuxnet , its drivers also contained a digital signature, and the certificates were also stolen from technology companies: JMicron and Realtek. Supplying a malicious driver with a digital signature is a one hundred percent solution to ensure that such a driver is loaded in a 64-bit version of Windows.
The specified driver has the following prints:
MD5: 92e724291056a5e30eca038ee637a23f
SHA1: 478c076749bef74eaf9bed4af917aee228620b23
SHA256: bc4ae56434b45818f57724f4cd19354a13e5964fd097d1933a30e2e31c9bdfa5
Source: https://habr.com/ru/post/260459/
All Articles