Antivirus Self-Defense
As practice shows, any design antivirus is vulnerable, and implementing a new workaround for it is not a big problem.
Our research center was interested to check how the developers of antivirus solutions monitor the presence of descriptions of attack methods on the Internet. And is it always necessary to detect a 0-day vulnerability in an antivirus attack, or is it just enough to find useful information on the forums?
Most of the analytical work devoted to this topic, as a rule, is focused on assessing the efficiency of detecting malicious code by antiviruses, the performance of antiviruses, etc. As part of our research, we tried to find out whether the developers of solutions of this class are following the trends and modifying their products in accordance with the new methods of attack.
Self-defense of the antivirus and its circumvention in some cases means circumventing the entire mechanism for detecting malicious code. This and is often used in the implementation of targeted attacks or in programs with destructive, blocking this software functionality.
')
After the introduction of malicious code into the antivirus process, it is able to exist for a long time and imperceptibly in the user's system, which undoubtedly is a consequence of the main logical flaw in the self-defense architecture, as well as the methods of using trusted process lists.
The malicious code is being improved in parallel with the development of antivirus technologies, which is very similar to some kind of arms race. There are all new threats that compromise the software of this class, disable it, completely deactivate its functionality, etc. As a result, requirements for the development of antivirus solutions, which are positioned to protect after the fact, are growing. Antiviruses provide functionality for self-defense and protection against active threats. Perhaps the most controversial mechanism of software of this class — the mechanism of self-defense — is developing.
If you systematize internally the device of several anti-virus products, you can summarize the self-defense architecture. As a result, we will get the following features inherent in this mechanism and its implementation:
And, finally, the most controversial moment in the work of the self-defense mechanism: antivirus processes become a kind of super-privileged entity, they are inaccessible for the impact of both the attacker and the average user.
Consequences of introducing malicious code into the antivirus:
For the study, we selected several anti-virus products that meet the following requirements:
It turned out such a list (At the time of testing, these were the latest versions):
Testing methods took place on the Windows 7 operating system, x86_64 / x86_32, which was installed on the VMware virtual machine. In addition, individual solutions were installed on physical hardware (due to the use of hardware virtualization mechanisms VT-x / AMD-V).
For this study, several universal techniques were applied, each of which is not aimed at a specific solution and does not use the architectural weaknesses of this or that software.
The following techniques were chosen: ProxyInject, Duplicate Handle, Reparse Point, PageFile, RegSafe / RegRestore and Shim Engine. For a more detailed description of the technique, we recommend referring to the original text of the study “Self-defense of antiviruses” .
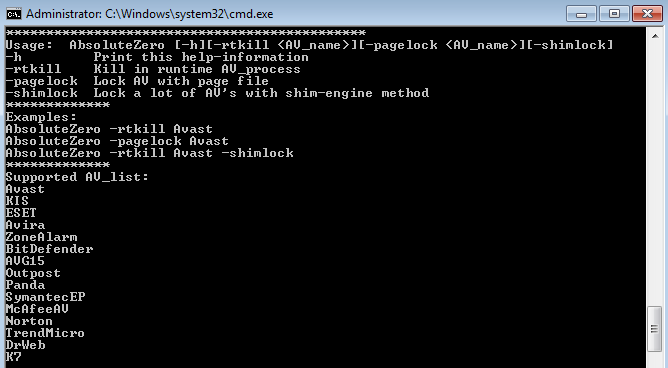
And for testing, a special program was used, which receives data on equipment and targets as parameters.

Thus, the results of testing with a specific methodology on this sampling of the technician revealed a very interesting result: the domestic antivirus developer improved and built his defense more qualitatively than foreign vendors did.
Obviously, some companies simply do not track the evolution of public methods of attack, only confirming the absurdity of their chosen architecture.
It is also worth noting that, despite all the results, the architecture as a whole does not change, and the developers react to the attacks after the fact and are protected from already known attack mechanisms. This provides attackers with greater freedom of action, and also provides opportunities for improving methods in the future. And until the situation changes, the attackers will always be one step ahead of defense.
Our research center was interested to check how the developers of antivirus solutions monitor the presence of descriptions of attack methods on the Internet. And is it always necessary to detect a 0-day vulnerability in an antivirus attack, or is it just enough to find useful information on the forums?
Introduction
Most of the analytical work devoted to this topic, as a rule, is focused on assessing the efficiency of detecting malicious code by antiviruses, the performance of antiviruses, etc. As part of our research, we tried to find out whether the developers of solutions of this class are following the trends and modifying their products in accordance with the new methods of attack.
Self-defense of the antivirus and its circumvention in some cases means circumventing the entire mechanism for detecting malicious code. This and is often used in the implementation of targeted attacks or in programs with destructive, blocking this software functionality.
')
After the introduction of malicious code into the antivirus process, it is able to exist for a long time and imperceptibly in the user's system, which undoubtedly is a consequence of the main logical flaw in the self-defense architecture, as well as the methods of using trusted process lists.
Antivirus self-defense
The malicious code is being improved in parallel with the development of antivirus technologies, which is very similar to some kind of arms race. There are all new threats that compromise the software of this class, disable it, completely deactivate its functionality, etc. As a result, requirements for the development of antivirus solutions, which are positioned to protect after the fact, are growing. Antiviruses provide functionality for self-defense and protection against active threats. Perhaps the most controversial mechanism of software of this class — the mechanism of self-defense — is developing.
If you systematize internally the device of several anti-virus products, you can summarize the self-defense architecture. As a result, we will get the following features inherent in this mechanism and its implementation:
- Protect your own files and directories
- Usually implemented with a kernel level file filter.
- Protect your own configuration data in the registry
- It is implemented using a combination of hooks and / or the RegistryCallback interface of the kernel.
- Protection of antivirus interfaces
- Control access to various control interfaces in ring0.
- Protection of own processes
- Implementations vary, it can be a combination of various interceptions of the kernel’s system functions, object types, use of a callback to create a process.
And, finally, the most controversial moment in the work of the self-defense mechanism: antivirus processes become a kind of super-privileged entity, they are inaccessible for the impact of both the attacker and the average user.
Consequences of introducing malicious code into the antivirus:
- Global disabling / blocking antivirus
- Manipulating whitelists
- Hidden operation in a super-privileged process
- Firewall rules bypass
- ...
Testing Methodology
Considered Antivirus Solutions
For the study, we selected several anti-virus products that meet the following requirements:
- Software using the self-defense architecture declares itself as capable of responding to an active, launched threat; it has a proactive defense function;
- Included in the list of the most popular solutions that have previously been tested using various methodologies.
It turned out such a list (At the time of testing, these were the latest versions):
| Developer | Product Name, Version |
|---|---|
| Mcafee | McAfee Total Security 2015 (15.4.0.470.7) |
| ESET | ESET Smart Security (8.0.312.3) |
| Symantec | Norton Security (22.2.0.31) |
| Avg | AVG Internet Security 2015 (2015.0.5941) |
| BitDefender | BitDefender Total Security 2015 (18.20.0.1429) |
| Trend micro | Trend Micro Antivirus + 2015 (AMSP 3.5.1186) |
| Avira | Avira (15.0.8.652) |
| Dr.Web | Dr.Web 10 (10.0.1.03310) |
| Kaspersky | Kaspersky Internet Security 15 (15.0.2.361) |
| Panda | Panda Internet Security 2015 (15.1.0) |
| Avast | Avast Free Antivirus (2015.10.2.2218) |
Testing environment
Testing methods took place on the Windows 7 operating system, x86_64 / x86_32, which was installed on the VMware virtual machine. In addition, individual solutions were installed on physical hardware (due to the use of hardware virtualization mechanisms VT-x / AMD-V).
Applied technology
For this study, several universal techniques were applied, each of which is not aimed at a specific solution and does not use the architectural weaknesses of this or that software.
All the techniques used in this test are available on open Internet resources for 1-3 years. Their code is not intentionally demonstrated. Links to public sources describing these techniques can only be provided to anti-virus companies only upon their official request.
The following techniques were chosen: ProxyInject, Duplicate Handle, Reparse Point, PageFile, RegSafe / RegRestore and Shim Engine. For a more detailed description of the technique, we recommend referring to the original text of the study “Self-defense of antiviruses” .
And for testing, a special program was used, which receives data on equipment and targets as parameters.

results
At a specific formulation of the problem, the same techniques are used by our specialists during penetration tests. In the process of work, it is necessary both to use the previously mentioned ones and to develop new techniques.

It should be understood that, in addition to these techniques, there are many others (inaccessible publicly), which also aim at introducing an antivirus product into the work or at terminating it. And of course, there are universal tools and specific anti-virus product.
findings
Thus, the results of testing with a specific methodology on this sampling of the technician revealed a very interesting result: the domestic antivirus developer improved and built his defense more qualitatively than foreign vendors did.
Obviously, some companies simply do not track the evolution of public methods of attack, only confirming the absurdity of their chosen architecture.
It is also worth noting that, despite all the results, the architecture as a whole does not change, and the developers react to the attacks after the fact and are protected from already known attack mechanisms. This provides attackers with greater freedom of action, and also provides opportunities for improving methods in the future. And until the situation changes, the attackers will always be one step ahead of defense.
Source: https://habr.com/ru/post/260269/
All Articles