Dubsmash 2 - regular porn clicker for Android
Recently, experts from the antivirus company Avast discovered a Trojan program, which is a porn clicker for Android. It was placed in the Google Play Store and was called Dubsmash 2. The malware disguised as a legitimate application and was downloaded more than 100 thousand times. It does not directly damage the user, such as stealing online banking data or account data. Instead, the clicker generates traffic or clicks on porn resources. If the victim uses the mobile Internet, such an operation can cost the user significant expenses.

Less than a month later, our researchers also discovered many variants of this malicious program on Google Play. The screenshot below shows this malicious application in Google Play.
')
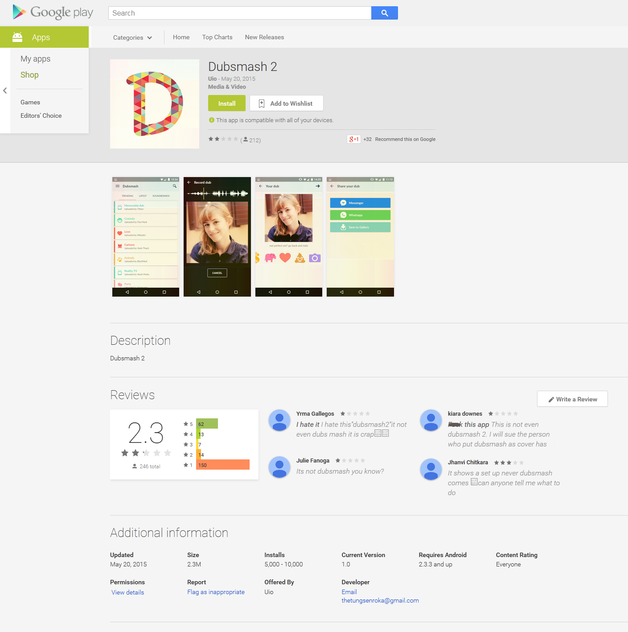
Fig. The fake Dubsmash 2 app on Google Play, which was available for download from May 20 to May 22 of this year.
One of the last fake Dubsmash 2 applications known to us was uploaded on Google Play on May 20 and removed from there on May 22 of this year. Such a short period of time was enough for it to be downloaded more than 5 thousand times. The application contained a clicker mechanism, as in the case of its previous versions.
The authors of the fake application did not wait a long time before downloading a new version of it to the Play store, and on the 23rd a new version was posted. Within three days after its placement, this version was downloaded more than 10 thousand times. Further, on the 25th and 26th of May, new modifications of the Dubsmash 2 were uploaded to Play for the fourth and fifth time. They contained the same malicious functions as previous versions. In fact, this is a very rare case for the Google Play app store, when a malicious application with the same features was downloaded there several times in a short period of time.

Fig. Fake application Dubsmash 2, posted on May 23rd.
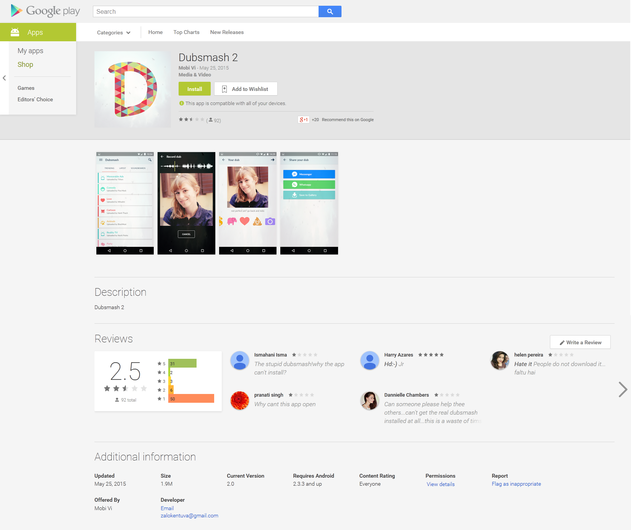
Fig. Fake application Dubsmash v2, posted on the 25th of May.
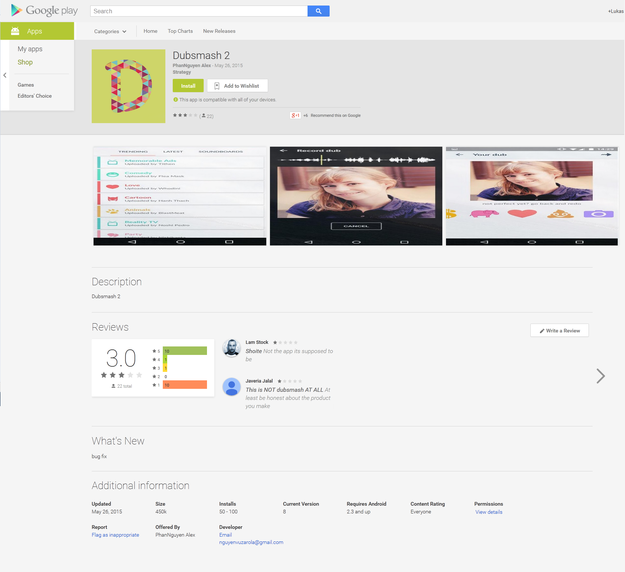
Fig. Fake application Dubsmash v2, posted on May 26th.
Malicious software has been added to ESET anti-virus databases as Android / Clicker . The files themselves were deleted by Google from the app store after our notice.

Fig. Android / Clicker icons on Google Play.
After installing this application, the user will not be able to see the icon of this application Dubsmash 2 on his device. Instead, it gets another icon and application that has nothing to do with Dubsmash. On the device, the fake application is disguised as a simple arcade game or system application. After its launch, the application hides the start icon, but continues to work in the background. At the same time continues to generate traffic to porn sites.

Fig. Fake application icons.
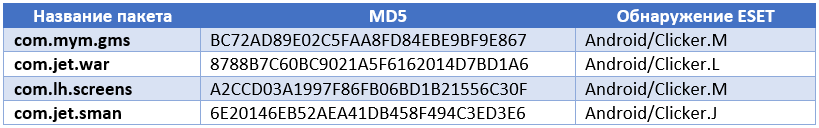
Malicious activity of the application is triggered at the moment when the device changes the connection to the network. In fact, it is not difficult to get a list of URLs that are used for clicks, as they are stored in clear text. The list of URLs is downloaded from the remote server of the attackers, and the address of this server is stored in clear text in the body of the application. However, in the latest version of the malicious application, there is an interesting feature: the malicious code will not perform its actions if any anti-virus product is present on the device. It checks installed applications based on package names, and the list of names includes 16 anti-virus vendors (see the table below). Package names are requested from the C & C server. After installing the application, it may not be detected by antivirus products, however, there is a chance that its malicious activity will be blocked by the URL for which the click is made. It is extremely suspicious for the user that the device may request data from a server that has already been blocked for malicious activity.

If none of the above applications are installed, the malicious application starts its work and requests links from the remote server for clicks. These links will be downloaded every 60 seconds. to a WebView type widget inside an invisible window, and a special arbitrary link template is used.
Using the example of this malicious application, we saw that the Google Play application distribution store still has weak spots; more than 10 thousand users downloaded the applications located there. The authors specifically used the name of the legitimate application to disguise their fake program. We encourage users to read reviews about applications, even if the application does not request any suspicious security permissions.

Less than a month later, our researchers also discovered many variants of this malicious program on Google Play. The screenshot below shows this malicious application in Google Play.
')

Fig. The fake Dubsmash 2 app on Google Play, which was available for download from May 20 to May 22 of this year.
One of the last fake Dubsmash 2 applications known to us was uploaded on Google Play on May 20 and removed from there on May 22 of this year. Such a short period of time was enough for it to be downloaded more than 5 thousand times. The application contained a clicker mechanism, as in the case of its previous versions.
The authors of the fake application did not wait a long time before downloading a new version of it to the Play store, and on the 23rd a new version was posted. Within three days after its placement, this version was downloaded more than 10 thousand times. Further, on the 25th and 26th of May, new modifications of the Dubsmash 2 were uploaded to Play for the fourth and fifth time. They contained the same malicious functions as previous versions. In fact, this is a very rare case for the Google Play app store, when a malicious application with the same features was downloaded there several times in a short period of time.

Fig. Fake application Dubsmash 2, posted on May 23rd.

Fig. Fake application Dubsmash v2, posted on the 25th of May.

Fig. Fake application Dubsmash v2, posted on May 26th.
Malicious software has been added to ESET anti-virus databases as Android / Clicker . The files themselves were deleted by Google from the app store after our notice.

Fig. Android / Clicker icons on Google Play.
After installing this application, the user will not be able to see the icon of this application Dubsmash 2 on his device. Instead, it gets another icon and application that has nothing to do with Dubsmash. On the device, the fake application is disguised as a simple arcade game or system application. After its launch, the application hides the start icon, but continues to work in the background. At the same time continues to generate traffic to porn sites.

Fig. Fake application icons.
Malicious activity of the application is triggered at the moment when the device changes the connection to the network. In fact, it is not difficult to get a list of URLs that are used for clicks, as they are stored in clear text. The list of URLs is downloaded from the remote server of the attackers, and the address of this server is stored in clear text in the body of the application. However, in the latest version of the malicious application, there is an interesting feature: the malicious code will not perform its actions if any anti-virus product is present on the device. It checks installed applications based on package names, and the list of names includes 16 anti-virus vendors (see the table below). Package names are requested from the C & C server. After installing the application, it may not be detected by antivirus products, however, there is a chance that its malicious activity will be blocked by the URL for which the click is made. It is extremely suspicious for the user that the device may request data from a server that has already been blocked for malicious activity.

If none of the above applications are installed, the malicious application starts its work and requests links from the remote server for clicks. These links will be downloaded every 60 seconds. to a WebView type widget inside an invisible window, and a special arbitrary link template is used.
Using the example of this malicious application, we saw that the Google Play application distribution store still has weak spots; more than 10 thousand users downloaded the applications located there. The authors specifically used the name of the legitimate application to disguise their fake program. We encourage users to read reviews about applications, even if the application does not request any suspicious security permissions.

Source: https://habr.com/ru/post/260011/
All Articles