Who Hacked the Electric Substation: Analysis of the Digital Substation Takeover Contest

As part of the Digital Substation Takeover contest presented by iGRIDS , PHDays visitors had the opportunity to try their hand at breaking into a real electrical substation built according to IEC 61850. For two days, the participants tried to launch a successful attack and gain control over the electrical control system.
What should have been done
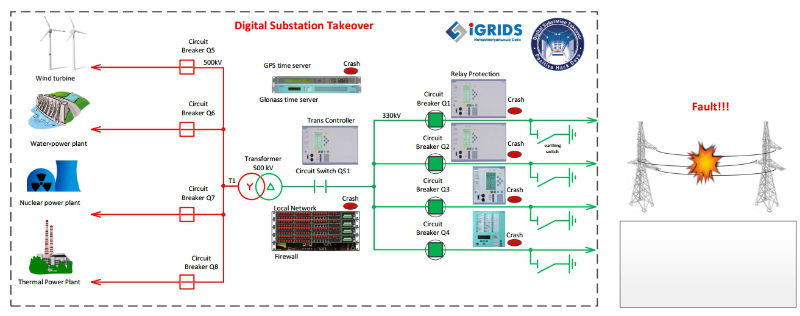
A model created specifically for the competition that imitated a high-voltage substation of 500 kV included switches, time servers, controllers and relay protection devices that are actually used in modern high-voltage electrical networks to protect against emergency and abnormal situations (short circuits, damage to power lines, etc.) P.).
')
Participants were offered several scenarios, each of which implied ultimately unauthorized control of switching devices - from simply turning off the switch to turning on the grounding knives, bypassing the operational locks. The most difficult task - creating an emergency at the facility - was supposed, according to the organizers, to be accompanied by a firework of burning wires on a simulated overhead power line.
This year, individual contests were part of the CTF: along with the guests of the forum, CTF teams could participate in them (for more details, see our article on Habrahabr ). In total, about 50 PHDays visitors and several CTF teams tried their hand at this competition.
Technical details
The following equipment was involved in the competitive layout:
- SICAM PAS v. most popular energy object management system. 7.0;
- the most popular relay protection terminals and controllers;
- GPS and GLONASS time servers;
- industrial switches.
The course of the competition
Since the competition was presented in the PHDays program for the first time, and the topic itself is rather specific, the entire first day the participants went on to figure out what relay protection, switches and operational locks are. It was necessary to search and analyze large volumes of information (on Wikipedia, on specialized forums, on the sites of equipment manufacturers).

The competition included several assignments that were submitted to participants with different success:
- temporary destruction of the information infrastructure of the substation (managed to be carried out 6 times);
- reprogramming time server (1 successful execution);
- unauthorized disconnection of consumers (completed 2 times);
- detection of previously unknown vulnerability (1 time).
The most important and difficult task - intercepting control of primary equipment and sending a command to bypass the blocking - was not carried out by anyone, although one of the participating teams was close to this.
First place went to Sergei Sidorov, Alexander Kalinin won the silver medal. In addition, the breaking of the substation brought points to two CTF teams - RDot and ReallyNonamesFor.
A bit uncomfortable
The burglary was observed by representatives of power grid companies, including specialists of FGC UES.
 “Honestly, after seeing people sitting on ottomans and trying to hack real RZA devices and an automated process control system for a certain virtual profit, I felt a little uneasy,” said Mikhail Seleznev, head of the automated control system department, in an interview with our colleagues from the Digital Substation electronic journal TP and Metrology of the Department of Relay Protection, Metrology and Process Control Systems of JSC FGC UES. - Where is the guarantee that the team of the same “inquisitive minds” after this event, already knowing how the RZA looks and how the automated process control system behaves, will not come together and, for the sake of sporting interest, will not begin to look for opportunities to hack a similar infrastructure, only already real? Will they be aware of all the possible severity of the consequences of their actions? ”
“Honestly, after seeing people sitting on ottomans and trying to hack real RZA devices and an automated process control system for a certain virtual profit, I felt a little uneasy,” said Mikhail Seleznev, head of the automated control system department, in an interview with our colleagues from the Digital Substation electronic journal TP and Metrology of the Department of Relay Protection, Metrology and Process Control Systems of JSC FGC UES. - Where is the guarantee that the team of the same “inquisitive minds” after this event, already knowing how the RZA looks and how the automated process control system behaves, will not come together and, for the sake of sporting interest, will not begin to look for opportunities to hack a similar infrastructure, only already real? Will they be aware of all the possible severity of the consequences of their actions? ”“I don’t think that some changes should be expected by IEC 61850,” continued Mikhail Seleznev. - It should live and develop in favor of the tasks for which it was created. Information security should be subject to other standards and tools. Recently, there has been a lot of talk on the topic of information security of an automated process control system. And it is conducted by people of different qualifications, which is why the impression is often created that the topic is artificially inflated by the market representatives. Therefore, first of all, a more active involvement of representatives of electric power companies to such practical events is needed. ”
Competition organizers from the company iGRIDS recorded and analyzed everything that happened on the stand. By the middle of the competition, it became clear that the spectrum of threats to the system they had created was wider than originally intended - the developers promise to take into account all the new attack options in their work and the next versions of the protection.
And they have already received an invitation to the next PHDays VI - so get ready for the new version of the substation hacking contest, which will be held in the spring of 2016!
Source: https://habr.com/ru/post/259905/
All Articles