Top 3 common errors found during site security audits

Today I will continue the series of articles on web security. For some, this information may not seem new, for someone it may become a reason for reflection.
Errors will be indicated by average frequency and numbered according to the Top 10 Open Web Application Security Project (OWASP).
')
So, I would put XSS (OWASP A3) in the first place - cross-site scripting.
Like the author of http://habrahabr.ru/post/149152/ , I consider XSS not as a vulnerability, but as an attack vector, since methods of operation can be quite a lot.
They are passive, active, dom-based and are found both on large commercial sites and on self-written home pages. Cross-site scripting (XSS) is associated with the ability to embed HTML code into a vulnerable page. The implementation of the code is carried out through all available methods for entering information. Successful exploitation of the vulnerability could allow attackers to use the values of various variables available in the context of the site, record information, intercept user sessions, etc.
The specific nature of such attacks is that instead of directly attacking the server, they use the vulnerable server as a means of attacking the client.
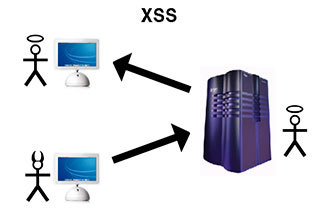
What is the danger of such attacks: it is possible to intercept a privileged account to access the control panel, and from there download / modify data, fill the shell.
The second place is honored by various leaks of critical data - OWASP A4, A6 and A7.
I would call this group of vulnerabilities a lack of proper attention to the storage and transmission of critical data.
What this includes: various vulnerabilities like session prediction, when sorting through the ID values you can get access to other people's data, for example:
- / download / ******* - changing the parameters you can parse all files from the server
- / user / ticket = ****** - you can view all messages in tech support from all users
Critical data in the root of the site: backups, service scripts, repositories and more.
For example, a service script grep.php was found on one of the sites, which allowed searching using regular expressions by site content. With the help of this script, data for connecting to MySQL was found through the phpmyadmin site left in the folder.
On sites with one well-known commercial CMS, you can find files that simplify access to the system (auth bypass), scripts that simplify backups, with the name of the backup file in the root of the site, which you can’t find by simply bruising; scripts for testing a web server and more. The level of access to these scripts is not set properly, and, as a result, anyone who knows the features of this CMS can try to find them:
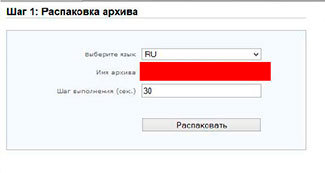
Sometimes, the developers in the form of haste or other factors forget to delete some specific scripts that can help an attacker compile a list of all the files on the server:
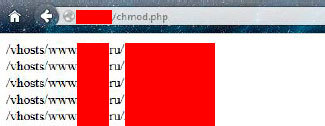
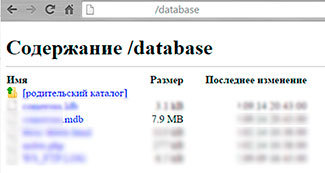
Sometimes a simple search in the directories of the site gives simply stunning results, for example:
database (lies and waits until someone downloads it):
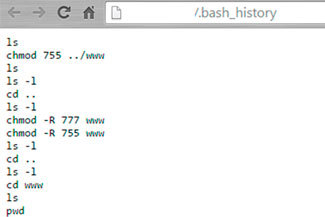
bash history (command history):
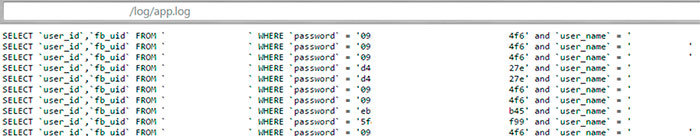
logs (from which you can get useful information):
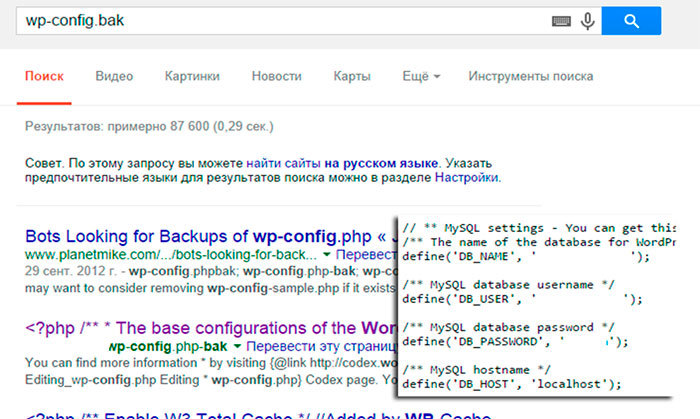
backups:
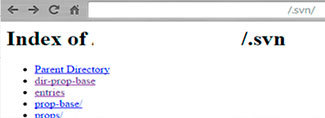
repositories:
The third place in popularity is occupied by all sorts of injections OWASP A1.
It would seem, in 2015, about sql injection, everything is painted and chewed on every corner, and is it more and more difficult to meet them in nature? Somehow not so. According to statistics, sql injection class vulnerabilities are quite common in one form or another.
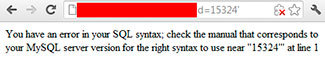
The exploitation of web vulnerabilities can lead to serious consequences: there is a possibility to pull data from the database, fill the shell (if the rights allow), etc.
For example, such a POST request login=admin@domain.name'+and+1=1+--+&password=pass allows you to bypass authorization on the site and log in as administrator.
And although this vulnerability is in last place in terms of popularity - you should not underestimate it, for good reason it ranks first in the OWASP rating.
What is the result?
Most of these errors can be removed in minimal time and they are not conceptual and difficult to exploit, but they need to be detected in time, assessed risks and minimize the consequences.
It is necessary to conduct timely site security audits for vulnerabilities.
Source: https://habr.com/ru/post/259887/
All Articles