Attackers use Linux / Moose to compromise Linux-embedded systems, part 3
In the previous parts of [ 1 ], [ 2 ] of the Linux / Moose malware analysis, we examined all its mechanisms for mail. In this part, we will look at the possibilities of removing other malicious programs from the system, as well as the protocol of the bot's operation with the C & C configuration server.

We have already mentioned that a bot has the ability to remove other malware from the system. The configuration C & C server sends it a list of names of executable process files. Every hour, the bot goes through the list of processes / proc / pid / and scans the command line with which the process was started. The command line contains the name of the process, as well as the arguments passed to it during the launch. Passing through this list of processes, Moose will send a kill signal to each process from the above black list. This list is tightly wired into the body of the malware.
This Moose function also requires the presence of a special cnccfg_flag_killprocess configuration flag. In the patterns we observed, this flag was always set. Below is an example of such a list.
')

All these lines refer to software that performs bitcoin mining operations and is used by other malware. Perhaps the killing of these processes is performed to free up the limited resources of the system that will be used by malicious software to perform their actions. The string "cmd.so" may refer to Synology Disk Miner software, and "/.usb2", "/.scan" and. "/ Ipt" to another worm that is engaged in mining Bitcoins on ARM Linux ( Linux / Svirtu ). This malware also uses weak credentials to enter the system, which makes them potential competitors with Moose.
Protocol of interaction with the configuration C & C server
A detailed description of the network protocol will allow affected organizations to use this information in order to work out the protection against malicious software. Linux / Moose operators use recompilation of Moose executable files, as well as their modification, in order to avoid detection by malicious products. On the other hand, changing the network protocol is a very laborious task and takes a lot of time, so publishing data on the functioning of the protocol can adversely affect the work of intruders.
For quick deobfuscation of captured traffic and its analysis, we recommend using the tool that we uploaded to our repository on Github. We added commands like tshark and Python code to view traffic.
There are two types of interaction between a bot and a configuration C & C server. The first is carried out every hour and the second every four hours. The main difference between the two is the transfer of different parameters to the bot. In the first case, a set of login / password pairs will be transmitted, which will be used when bruteforce performs attacks on routers to infect them. Below is a fragment of this interaction.
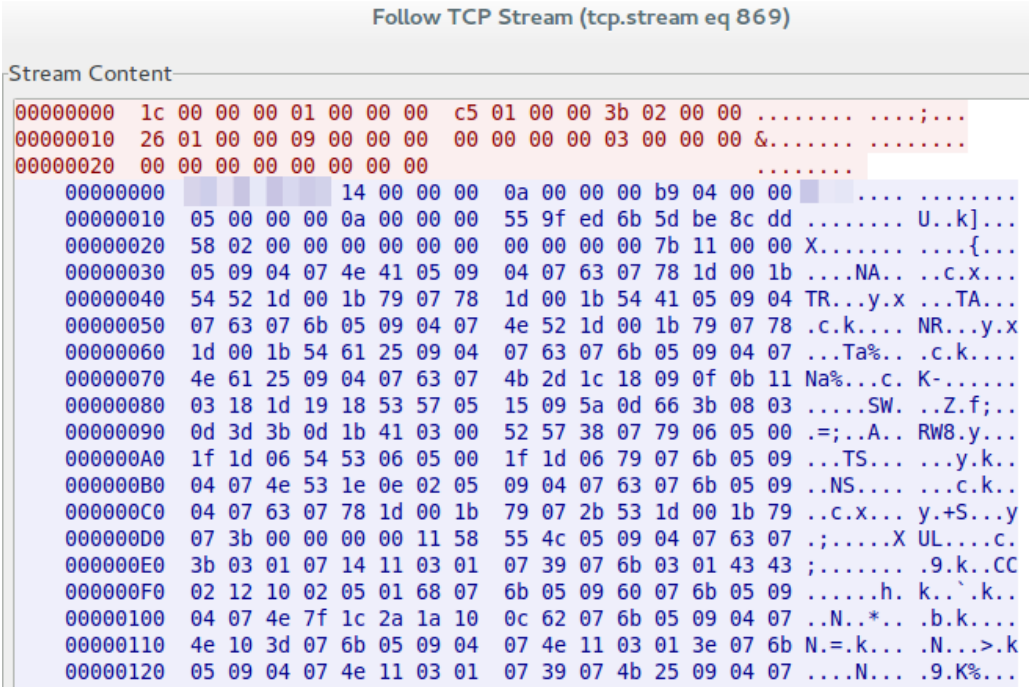
Fig. Fragment of the bot's interaction with the C & C server.
The bot sends the message of the following structure to the configuration C & C server.
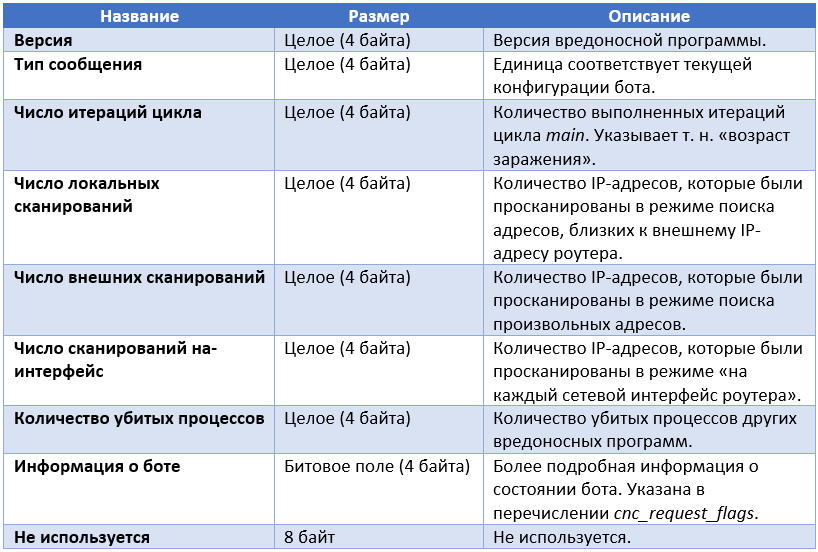
Below is the "Bot Information" bit field.

The configuration C & C server responds to the bot with the message of the following structure. It consists of information blocks with a configuration, some of which are optional. Below is the format of such a message.
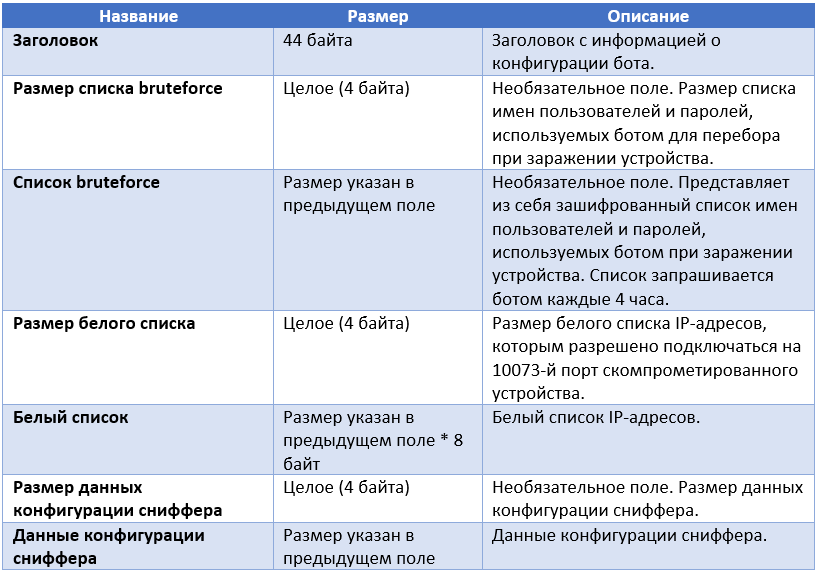
The following is the format of the server message header.

Below are the flags of the "Additional configuration".

Each element of the white list is presented in the format of the following structure. Their number is indicated by a separate “White list size” field.

The same applies to the sniffer configuration elements; a special structure is used for them.

The screenshot below shows an example of the configuration data sent to the bot. For their deobfuscation, a Python tool was used, which we mentioned earlier.
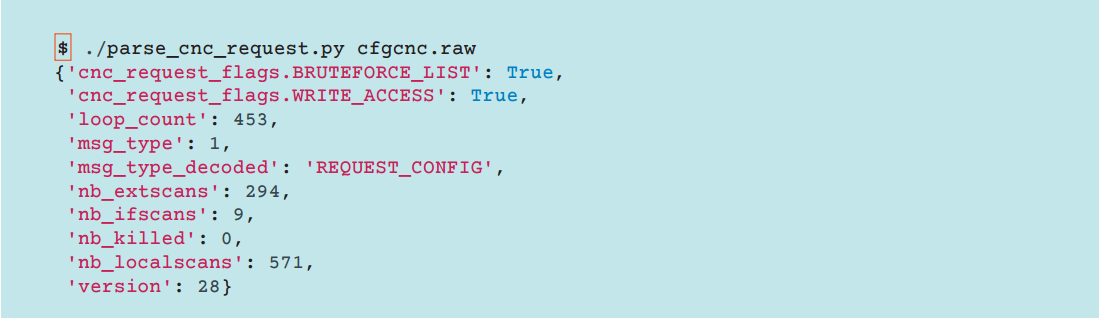
Fig. An example of a request that a bot sends to a configuration C & C server.
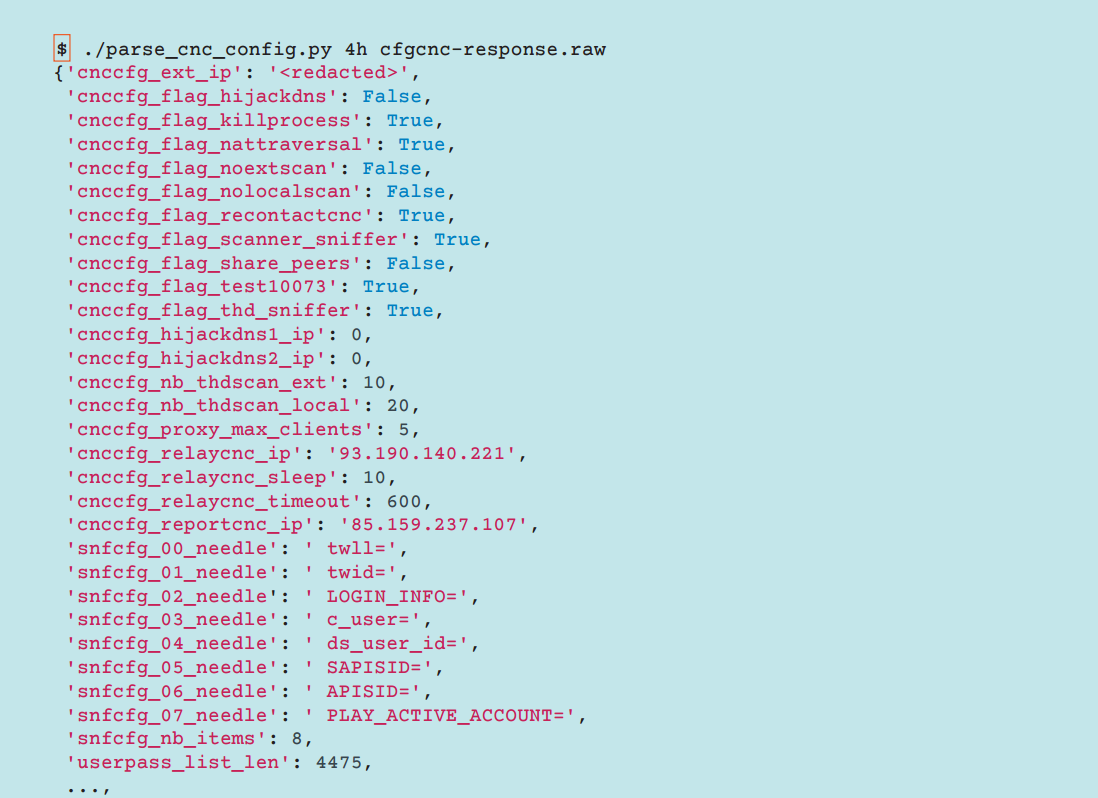
Fig. Example response configuration C & C server.
Malware Version History
Version 20
Versions 28-29
Versions 29-31
Conclusion
The Linux / Moose malware is a fairly new type of malware that is designed for Linux OS. This is primarily due to the fact that most of the threats to this OS are focused on performing DDoS attacks and sending spam. At the same time, the attackers implemented in Moose the most basic way to compromise routers, based on a simple search of credentials. Obviously, routers with low security settings may suffer from the activity of this malicious program.
Since the malware does not contain autoload mechanisms, a simple reboot of the device allows you to effectively disable its malicious activity. The user should also immediately change the credentials on the router, which will prevent its infection in the future. For routers, you should also check the security settings to eliminate the situation in which certain ports of the router will be accessible from the global network.
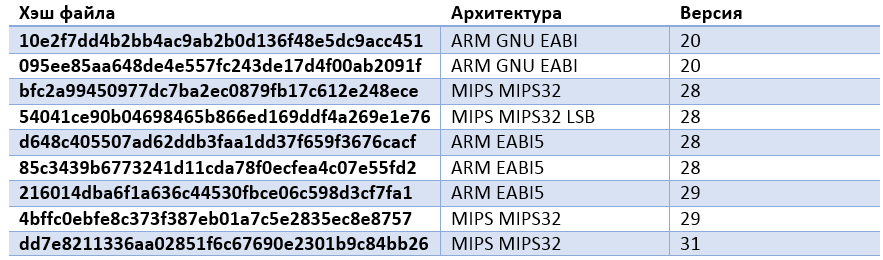
The SHA1 hashes of various modifications of this malware are listed below.
Compromise Indicators (IoC)
Traffic from an infected device to these IP_address: port.

Traffic from these IP addresses (white list) to the infected device (port 10073).

Indicators in the OS:
The last identifier specified can be verified using the netstat –anp command . Depending on the system configuration, the –p flag may not be available. If it is not available, use the lsof tool or manually copy the contents from the location of / proc / net / tcp / and / proc // fd as indicated here .
You can use the popular yara tool to identify a file or a set of malware files. To do this, use the rule linux-moose.yar , which is available on our repository in Github. Using it, you can identify the malware files by recursively traversing file directories.

If there is no output after executing this command, it means that no malicious Moose file was found. Otherwise, the names of the malware files will be printed. If the authors change the bot code to reset detection by antivirus products, this rule is likely to no longer be able to identify new Moose variants.
Compromise Devices
This link provides a list of credentials (login / password) that Moose uses to distribute on devices whose manufacturers use such credentials by default. The list also includes manufacturers whose devices allow Telnet connections. Here is a list of such manufacturers.
Network equipment vendors
3Com, Alcatel-Lucent, Allied Telesis, Avaya, Belkin, Brocade, Buffalo, Celerity, Cisco, D-link, Enterasys, Hewlett-Packard, Huawei, Linksys, Mikrotik, Netgear, Meridian, Nortel, SpeedStream, Thomson, TP-Link , Zhone, ZyXEL.
Appliances vendors
APC, Brother, Konica / Minolta, Kyocera, Microplex, Ricoh, Toshiba, Xerox
Internet of Things vendors
Hik Vision, Leviton
It is necessary to take into account the fact that this is a list of those vendors that Moose is potentially targeting. Current versions of the malware need access to the shell command line, and Moose must log in in successfully. On some devices, this type of access is protected by another pair of credentials or a secret password. Such Moose devices are not able to compromise.
If you work with the device of one of these vendors and can answer these questions, then let us know.
In the event that credentials can be used to log into Telnet or Telnet is allowed by default and access to the command line can be obtained by executing the sh command, the device can potentially be compromised by malware.
Manufacturers that are listed below use credentials from this list by default.
Ericsson, F5 Networks, Fortinet, Siemens, LSI Corporation, Maxim Integrated, Accelerated Network, Quantum, Advantek, Airtel, AirTies, Radware, Ubee Interactive, AOC, Applied Innovations, Arescom, ARtem, Asante, Ascend, ATL, Atlantis, AVM, Avocent, Axis, Aztech, Bay Networks, Bintec, BMC, Broadlogic, Canyon, Cellit, Ciphertrust, CNet, Compaq, Comtrend, Conceptronic, Conexant, Corecess, CTC Union, Cyclades, Davox, Demarc, Digicom, Draytek, Dynalink, E- Con, Efficient, Everfocus, Flowpoint, Gericom, IBM, iDirect, Inchon, Infacta, Infoblox, INOVA, Interbase, Intermec, Intracom, JD Edwards, Kasda, KTI, Lantronix, Laxo, LG, Livingston, Marconi, McAfee, McData, Mentec , Micronet, Milan, Motorola, Mro software, Netopia, Netport, Netscreen, Netstar, Niksun, Nokia, NOMADIX, Olitec (trendchip), OpenConnect, Osicom, Overland, Ovislink, Pansonic, Phoenix, Pirelli, Planet, Ptcl, QLogic, Quintum Technologies, RM, RoamAbout, Sagem, Samsung, Server TechnologyPower, Sharp, Signamax, Siips, Silex Technology , Simple Smdr, Sitecom, Smartswitch, SMC, Sonic-X, Spectra Logic, SpeedXess, Sphairon, SSA, Stratacom, Swissvoice, Symbol, System / 32, Tandem, Telewell, Telindus, Tellabs, Topsec, Troy, TVT System, US Robotics , Unisys, VASCO, VxWorks, Wang, Weidmüeller, Westell, X-Micro, xd, Xylan, Xyplex, Zebra, ZTE.

We have already mentioned that a bot has the ability to remove other malware from the system. The configuration C & C server sends it a list of names of executable process files. Every hour, the bot goes through the list of processes / proc / pid / and scans the command line with which the process was started. The command line contains the name of the process, as well as the arguments passed to it during the launch. Passing through this list of processes, Moose will send a kill signal to each process from the above black list. This list is tightly wired into the body of the malware.
This Moose function also requires the presence of a special cnccfg_flag_killprocess configuration flag. In the patterns we observed, this flag was always set. Below is an example of such a list.
')

All these lines refer to software that performs bitcoin mining operations and is used by other malware. Perhaps the killing of these processes is performed to free up the limited resources of the system that will be used by malicious software to perform their actions. The string "cmd.so" may refer to Synology Disk Miner software, and "/.usb2", "/.scan" and. "/ Ipt" to another worm that is engaged in mining Bitcoins on ARM Linux ( Linux / Svirtu ). This malware also uses weak credentials to enter the system, which makes them potential competitors with Moose.
Protocol of interaction with the configuration C & C server
A detailed description of the network protocol will allow affected organizations to use this information in order to work out the protection against malicious software. Linux / Moose operators use recompilation of Moose executable files, as well as their modification, in order to avoid detection by malicious products. On the other hand, changing the network protocol is a very laborious task and takes a lot of time, so publishing data on the functioning of the protocol can adversely affect the work of intruders.
For quick deobfuscation of captured traffic and its analysis, we recommend using the tool that we uploaded to our repository on Github. We added commands like tshark and Python code to view traffic.
There are two types of interaction between a bot and a configuration C & C server. The first is carried out every hour and the second every four hours. The main difference between the two is the transfer of different parameters to the bot. In the first case, a set of login / password pairs will be transmitted, which will be used when bruteforce performs attacks on routers to infect them. Below is a fragment of this interaction.

Fig. Fragment of the bot's interaction with the C & C server.
The bot sends the message of the following structure to the configuration C & C server.

Below is the "Bot Information" bit field.

The configuration C & C server responds to the bot with the message of the following structure. It consists of information blocks with a configuration, some of which are optional. Below is the format of such a message.

The following is the format of the server message header.

Below are the flags of the "Additional configuration".

Each element of the white list is presented in the format of the following structure. Their number is indicated by a separate “White list size” field.

The same applies to the sniffer configuration elements; a special structure is used for them.

The screenshot below shows an example of the configuration data sent to the bot. For their deobfuscation, a Python tool was used, which we mentioned earlier.

Fig. An example of a request that a bot sends to a configuration C & C server.

Fig. Example response configuration C & C server.
Malware Version History
Version 20
- The first version we found
- First ARM option
Versions 28-29
- The bot uses three different configuration C & C servers instead of one.
- Improved Telnet connection handling code.
- Improved detection of Telnet credential request (prompt).
Versions 29-31
- Improved handling of memory shortages.
- A new C & C server configuration request flag has been added: 0x80 - TIME_PROBLEM.
Conclusion
The Linux / Moose malware is a fairly new type of malware that is designed for Linux OS. This is primarily due to the fact that most of the threats to this OS are focused on performing DDoS attacks and sending spam. At the same time, the attackers implemented in Moose the most basic way to compromise routers, based on a simple search of credentials. Obviously, routers with low security settings may suffer from the activity of this malicious program.
Since the malware does not contain autoload mechanisms, a simple reboot of the device allows you to effectively disable its malicious activity. The user should also immediately change the credentials on the router, which will prevent its infection in the future. For routers, you should also check the security settings to eliminate the situation in which certain ports of the router will be accessible from the global network.
The SHA1 hashes of various modifications of this malware are listed below.

Compromise Indicators (IoC)
Traffic from an infected device to these IP_address: port.

Traffic from these IP addresses (white list) to the infected device (port 10073).

Indicators in the OS:
- the presence of a binary file called elan2;
- running process elan2;
- The process that is trying to listen on is 0.0.0.0:10073.
The last identifier specified can be verified using the netstat –anp command . Depending on the system configuration, the –p flag may not be available. If it is not available, use the lsof tool or manually copy the contents from the location of / proc / net / tcp / and / proc // fd as indicated here .
You can use the popular yara tool to identify a file or a set of malware files. To do this, use the rule linux-moose.yar , which is available on our repository in Github. Using it, you can identify the malware files by recursively traversing file directories.

If there is no output after executing this command, it means that no malicious Moose file was found. Otherwise, the names of the malware files will be printed. If the authors change the bot code to reset detection by antivirus products, this rule is likely to no longer be able to identify new Moose variants.
Compromise Devices
This link provides a list of credentials (login / password) that Moose uses to distribute on devices whose manufacturers use such credentials by default. The list also includes manufacturers whose devices allow Telnet connections. Here is a list of such manufacturers.
Network equipment vendors
3Com, Alcatel-Lucent, Allied Telesis, Avaya, Belkin, Brocade, Buffalo, Celerity, Cisco, D-link, Enterasys, Hewlett-Packard, Huawei, Linksys, Mikrotik, Netgear, Meridian, Nortel, SpeedStream, Thomson, TP-Link , Zhone, ZyXEL.
Appliances vendors
APC, Brother, Konica / Minolta, Kyocera, Microplex, Ricoh, Toshiba, Xerox
Internet of Things vendors
Hik Vision, Leviton
It is necessary to take into account the fact that this is a list of those vendors that Moose is potentially targeting. Current versions of the malware need access to the shell command line, and Moose must log in in successfully. On some devices, this type of access is protected by another pair of credentials or a secret password. Such Moose devices are not able to compromise.
If you work with the device of one of these vendors and can answer these questions, then let us know.
- Is telnet service enabled by default?
- Can you connect to your Telnet device with default credentials?
- What is your device model?
- What happens if you issue the sh command in Telnet?
In the event that credentials can be used to log into Telnet or Telnet is allowed by default and access to the command line can be obtained by executing the sh command, the device can potentially be compromised by malware.
Manufacturers that are listed below use credentials from this list by default.
Ericsson, F5 Networks, Fortinet, Siemens, LSI Corporation, Maxim Integrated, Accelerated Network, Quantum, Advantek, Airtel, AirTies, Radware, Ubee Interactive, AOC, Applied Innovations, Arescom, ARtem, Asante, Ascend, ATL, Atlantis, AVM, Avocent, Axis, Aztech, Bay Networks, Bintec, BMC, Broadlogic, Canyon, Cellit, Ciphertrust, CNet, Compaq, Comtrend, Conceptronic, Conexant, Corecess, CTC Union, Cyclades, Davox, Demarc, Digicom, Draytek, Dynalink, E- Con, Efficient, Everfocus, Flowpoint, Gericom, IBM, iDirect, Inchon, Infacta, Infoblox, INOVA, Interbase, Intermec, Intracom, JD Edwards, Kasda, KTI, Lantronix, Laxo, LG, Livingston, Marconi, McAfee, McData, Mentec , Micronet, Milan, Motorola, Mro software, Netopia, Netport, Netscreen, Netstar, Niksun, Nokia, NOMADIX, Olitec (trendchip), OpenConnect, Osicom, Overland, Ovislink, Pansonic, Phoenix, Pirelli, Planet, Ptcl, QLogic, Quintum Technologies, RM, RoamAbout, Sagem, Samsung, Server TechnologyPower, Sharp, Signamax, Siips, Silex Technology , Simple Smdr, Sitecom, Smartswitch, SMC, Sonic-X, Spectra Logic, SpeedXess, Sphairon, SSA, Stratacom, Swissvoice, Symbol, System / 32, Tandem, Telewell, Telindus, Tellabs, Topsec, Troy, TVT System, US Robotics , Unisys, VASCO, VxWorks, Wang, Weidmüeller, Westell, X-Micro, xd, Xylan, Xyplex, Zebra, ZTE.
Source: https://habr.com/ru/post/259555/
All Articles