FastNetMon 1.1.2 release for open DoS / DDoS attack monitoring solution
Over the past almost 10 months since the release of 1.0.0, there has been a lot of work to improve the program.
Of the main changes, the following should be noted:
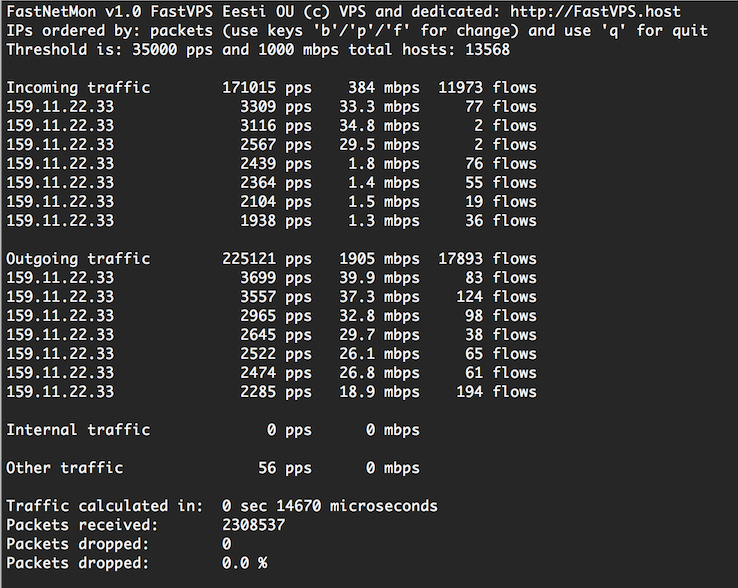
A complete list of changes can be found below:
On the development side, the following changes were made:
')
The list of supported platforms has undergone tremendous changes, added support for the following systems:
Binary packages were compiled for the following systems:
For other Linux systems, the automatic installer is recommended.
The new version allows you to achieve very high performance. The processing speed of sFLOW / Netflow is almost unlimited (up to tens and hundreds of gigabits per second). For PF_RING mode (not ZC), the maximum speed reached in the region of ~ 3mpps / 5GE. The highest speed can be achieved using PF_RING ZC or netmap traffic capture systems, both libraries allow processing of up to 10 million or more packets per second on mirror ports (10GE +). I draw your attention to the fact that at very high speed it is recommended to disable the connection tracking mode, which very heavily loads processor resources. All measurements are for Intel i7 2600 and Intel 82599 network card.
Of the things related to the community development, it is worth noting the connection of the Gitter project to effectively discuss issues relating to the project and in addition to it a classic mailing list has been added.
Separately, we would like to thank the people who have made a great contribution to helping the project and, above all, FastVPS , without which this project would have been impossible!
Of the main changes, the following should be noted:
- Ability to identify the most popular types of attacks: syn_flood, icmp_flood, udp_flood, ip_fragmentation_flood
- Adding support for Netflow protocol, supported 5, 9 and 10 (IPFIX) versions
- Adding support for sFLOW v5 protocol, which is supported by most modern network switches
- Added support for using netmap (Linux and FreeBSD are supported, a special version of the ixgbe driver is provided for Linux: github.com/pavel-odintsov/ixgbe-linux-netmap ) for capturing packets. This mode provides the highest traffic capture performance along with PF_RING ZC.
- Added support for PF_RING ZC (unfortunately, this mode requires a separate license for the PF_RING library)

A complete list of changes can be found below:
- Added the ability to collect netflow based on templates from multiple devices (including virtual ones within the same chassis)
- Basic IPv6 support in the Netflow module, the collector can listen on the IPv6 interface, protocol analysis is not yet supported
- Information about the attack now includes a very large number of fields, among which are the protocols used, packet types, TCP flags and much more, all this allows you to identify attacks as accurately as possible.
- Instead of every second calculation, the attack speed is averaged over the last X seconds, which allows minimizing false positives.
- Added ability to save attack fingerprints in separate files.
- Added the ability to specify the limit from which traffic is considered an attack in the number of streams, packets / second and bytes / second.
- Added integration with the ExaBGP project, with which you can announce blocked IP addresses directly on BGP routers of your own network or directly uplink
- Added support for plug-ins, it is now possible to develop your own traffic capture systems in addition to the existing ones.
- Added init files for systemd based systems
- Added ability to unlock IP after a specified period of time
- Added the ability to save attack data in Redis
- Added support for unpacking L2TP protocol in capture mode from mirrored ports
On the development side, the following changes were made:
- The transition to the build system cmake
- Added CI integration of the Travis CI system.
- For reasons of portability, the use of the C ++ 11 functional was denied.
')
The list of supported platforms has undergone tremendous changes, added support for the following systems:
- Fedora 21
- Debian 6, 7, 8
- CentOS 6, 7
- FreeBSD 9, 10, 11
- DragonflyBSD 4
- MacOS X 10.10
Binary packages were compiled for the following systems:
For other Linux systems, the automatic installer is recommended.
The new version allows you to achieve very high performance. The processing speed of sFLOW / Netflow is almost unlimited (up to tens and hundreds of gigabits per second). For PF_RING mode (not ZC), the maximum speed reached in the region of ~ 3mpps / 5GE. The highest speed can be achieved using PF_RING ZC or netmap traffic capture systems, both libraries allow processing of up to 10 million or more packets per second on mirror ports (10GE +). I draw your attention to the fact that at very high speed it is recommended to disable the connection tracking mode, which very heavily loads processor resources. All measurements are for Intel i7 2600 and Intel 82599 network card.
Of the things related to the community development, it is worth noting the connection of the Gitter project to effectively discuss issues relating to the project and in addition to it a classic mailing list has been added.
Separately, we would like to thank the people who have made a great contribution to helping the project and, above all, FastVPS , without which this project would have been impossible!
Source: https://habr.com/ru/post/259399/
All Articles