VKontakte does not pay users for found vulnerabilities
In late May, VKontakte solemnly announced the launch of an open program for rewards for vulnerabilities. This, like some other events, prompted me to write this article. The story began as early as September 2014, when, while I was writing a service based on the API of the social network, I discovered a vulnerability that allowed me to recognize both the community administrator who made the post and the person who offered this entry.
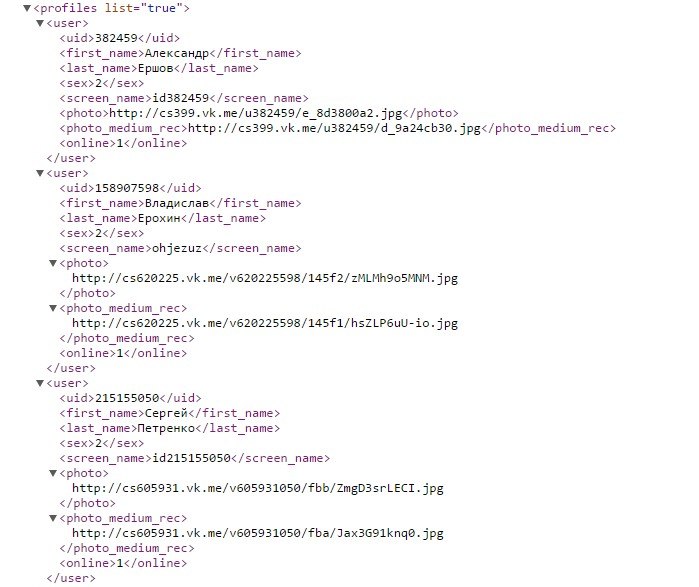
The vulnerability was in the newsfeed.get API method . When executing the most usual request to it, in an object, among others, an array of 4-5 users (profiles) was returned. Judging by the documentation, they were supposed to be users from the news feed. However, I could not find these people in the tape, and often only my own account was found in the array.
')
I was interested in this and I started testing this method on a news feed with posts from my own group. Having spent the evening on tests, I found patterns: in the array, the administrators returned, made an entry to the group, and people offered this entry to the group, and not for one post, but for the last four, and they were given alternately, in no particular order.
That is, making a request to the newsfeed.get for getting the last post in the news feed, in the profiles array I was returned by the administrator who wrote and the user who offered both this entry and the previous three.
This was already quite a serious vulnerability, but I wanted to link specific posts with specific people.
First of all, I started putting each analyzed community into a separate news list, so I was able to solve the problem when users from different communities were in the same array. My second step was to reduce the count parameter to one, so I got an array of profiles for each post in the group. After these actions, it became much easier to analyze the issue.

I wrote a script that first created a list of news with a certain community. Then he collected for each post of this community its own array with profiles. Here I faced API limits, it gave me posts only for the last 12 days, but it was also possible to work with this.
After collecting arrays for the maximum possible number of posts, the script began to analyze them. To begin with, there were those user id's that occur in exactly four arrays. Of the four posts related to these arrays, I found the earliest. This post was submitted to the community by the user whose id we found. Then these users were filtered from the arrays and I compiled a list of administrators.
If you wish, you can see the exploitation code of the vulnerability on Github .
Being a conscious user, after that I went to report a vulnerability. Since I found the open bug tracker not the best place for this kind of vulnerability, I immediately contacted the developers directly. The first developer simply did not respond to my message, the second answered 4 days later, thanked and promised to think about how to fix it.

I knew about the absence of the official bug bounty program from VKontakte, but I also knew that there were frequent cases of encouraging vulnerabilities in local currency (votes), but decided to postpone these issues at the time the vulnerability was fixed. After that, I began to monitor the vulnerability from time to time. This continued until April 2015, when after reading another article on vulnerability and reward, I checked my vulnerability again and it was not fixed.
I decided to contact me about the vulnerability with technical support where, after two weeks of waiting, they wrote to me that the code had been handed over to the developers and that they would notify me as soon as the news appeared.

May came, I decided to check the vulnerability again, and it was finally fixed. It took 8 months. Nobody contacted me, despite promises, so I decided to write myself, and at the same time find out the criteria by which the social network pays rewards. I was waiting for another week of waiting for a response from tech support, and the answer itself, in which I was offered to wait another.

I was contacted only on May 29, a few hours after the launch of the reward program for vulnerabilities, saying that once "the vulnerability has been fixed, it does not fall under the new program and I have nothing to offer them."
UPD : It seems that after the launch of the reward program the situation has not changed much .

1. Vulnerability Detection
The vulnerability was in the newsfeed.get API method . When executing the most usual request to it, in an object, among others, an array of 4-5 users (profiles) was returned. Judging by the documentation, they were supposed to be users from the news feed. However, I could not find these people in the tape, and often only my own account was found in the array.

')
I was interested in this and I started testing this method on a news feed with posts from my own group. Having spent the evening on tests, I found patterns: in the array, the administrators returned, made an entry to the group, and people offered this entry to the group, and not for one post, but for the last four, and they were given alternately, in no particular order.
That is, making a request to the newsfeed.get for getting the last post in the news feed, in the profiles array I was returned by the administrator who wrote and the user who offered both this entry and the previous three.
This was already quite a serious vulnerability, but I wanted to link specific posts with specific people.
First of all, I started putting each analyzed community into a separate news list, so I was able to solve the problem when users from different communities were in the same array. My second step was to reduce the count parameter to one, so I got an array of profiles for each post in the group. After these actions, it became much easier to analyze the issue.

I wrote a script that first created a list of news with a certain community. Then he collected for each post of this community its own array with profiles. Here I faced API limits, it gave me posts only for the last 12 days, but it was also possible to work with this.
After collecting arrays for the maximum possible number of posts, the script began to analyze them. To begin with, there were those user id's that occur in exactly four arrays. Of the four posts related to these arrays, I found the earliest. This post was submitted to the community by the user whose id we found. Then these users were filtered from the arrays and I compiled a list of administrators.
If you wish, you can see the exploitation code of the vulnerability on Github .
2. Reporting a vulnerability
Being a conscious user, after that I went to report a vulnerability. Since I found the open bug tracker not the best place for this kind of vulnerability, I immediately contacted the developers directly. The first developer simply did not respond to my message, the second answered 4 days later, thanked and promised to think about how to fix it.

I knew about the absence of the official bug bounty program from VKontakte, but I also knew that there were frequent cases of encouraging vulnerabilities in local currency (votes), but decided to postpone these issues at the time the vulnerability was fixed. After that, I began to monitor the vulnerability from time to time. This continued until April 2015, when after reading another article on vulnerability and reward, I checked my vulnerability again and it was not fixed.
I decided to contact me about the vulnerability with technical support where, after two weeks of waiting, they wrote to me that the code had been handed over to the developers and that they would notify me as soon as the news appeared.

May came, I decided to check the vulnerability again, and it was finally fixed. It took 8 months. Nobody contacted me, despite promises, so I decided to write myself, and at the same time find out the criteria by which the social network pays rewards. I was waiting for another week of waiting for a response from tech support, and the answer itself, in which I was offered to wait another.

I was contacted only on May 29, a few hours after the launch of the reward program for vulnerabilities, saying that once "the vulnerability has been fixed, it does not fall under the new program and I have nothing to offer them."
Results
- Another vulnerability in the privacy of VKontakte
- It took 8 months and 3 of my appeals to correct
- Questions about remuneration were ignored until the launch of the bug bounty program, after which, under her pretext, I was refused any payment
- Technical support chose long-term disregard for any actions
UPD : It seems that after the launch of the reward program the situation has not changed much .
Source: https://habr.com/ru/post/259363/
All Articles