10 ways to protect data in Office 365
The other day happened to hold a webinar on the topic of building enterprise ecosystems. When the topic of clouds was touched on, the most questions were raised about what Microsoft had done new in the field of data security in the clouds.
It is these issues that deprive sleep and become a headache for IT managers of companies using public cloud services. Answers to this question at the conference Microsoft Ignite, held from 4 to 8 May 2015 in Chicago, voiced by Brian Reid of NBConsult. Here is what he told about the methods of ensuring information security for organizations using Office 365.
Always use password policy and time limits to secure your data and application access. There are various settings for the timing of updating passwords depending on user profiles. Passwords for cloud service users lose their relevance after 90 days by default, while users synchronized with Active Directory obey the policy in accordance with the preferences settings. For cloud service users, a free password reset is available in self-service mode. With Azure Active Directory, you can allow users of the premium system to change passwords for cloud services. There are 4 ways to authenticate when resetting the password - via office phone, mobile phone, e-mail and secret questions.
The data loss prevention strategy ensures the safety of confidential and personal data from unauthorized downloading, distribution or e-mail. DLP is available in SharePoint Online and Exchange, and can be integrated with Enterprise Search. At the same time, you can create policies to restrict content to be saved in certain places, such as One Drive for Business and SharePoint Online. When you enable DLP for testing, it will report inconsistent data loading and storage of data that violates security policy.
')

Rights management protects documents and email using encryption and related access policies. Documents may only be used by certain users for specific purposes. You can set content matching rules and create offline access settings, as well as set document-level policies, which, for example, will not allow an unauthorized user to open a Word document saved to disk. This option requires an E3 license or rights management license in Azure.
Encrypting messages in Office 365 requires entering a login password to read and reply to emails. It usually works through a single access password for accessing an email. Message encryption is available in E3 Office 365.
Mobile device management allows you to protect data on users' devices. MDM allows you to set access conditions, demarcate policies for different users, manage mobile devices and delete data from them, if necessary, in part or in full. MDM has been freely offered in commercial subscription packages for Office 365 since May 2015.
Multi-factor authentication requires more than just a username and password to access Office 365. It can be set for each user individually. Users, in addition to the standard login and password, receive a call to a phone or text message. Answering a call or entering a received access code in a browser provides authentication with an increased level of security. The system can be switched on depending on the IP address, requesting an additional code only when accessing from public networks and deactivating when working in the office. Multi-factor authentication is a free option in all Office 365 plans.
Exchange Online Protection protects all Exchange Online mailboxes as part of a subscription. Extended threat protection will be available by the end of 2015 as an additional option to deal with serious issues such as phishing from trusted sources and malware attacks through application vulnerabilities.
Do not forget about the security of client devices that have access to Office 365. Be sure that updates to solve IS problems are installed in a timely manner. Using Active Directory Federation Services you can set security policies that restrict users from logging in from specific IP addresses. Keep in mind that the mobile device management functionality described above replaces this option.
This security method ensures that the client version is up to date.
Office by installing the latest updates. Users get the flexibility to customize updates at certain time intervals. You can control the situation through Click2Run's XML-based process, available only in the Office 365 Pro Plus subscription plans.
The admin portal provides the ability to enable or restrict content sharing. You can control content usage in Office 365, including sites, calendar, Skype for Business, and other applications. There are reports that show content sharing settings. The administrator can change the settings directly from the management console, without entering the application settings.
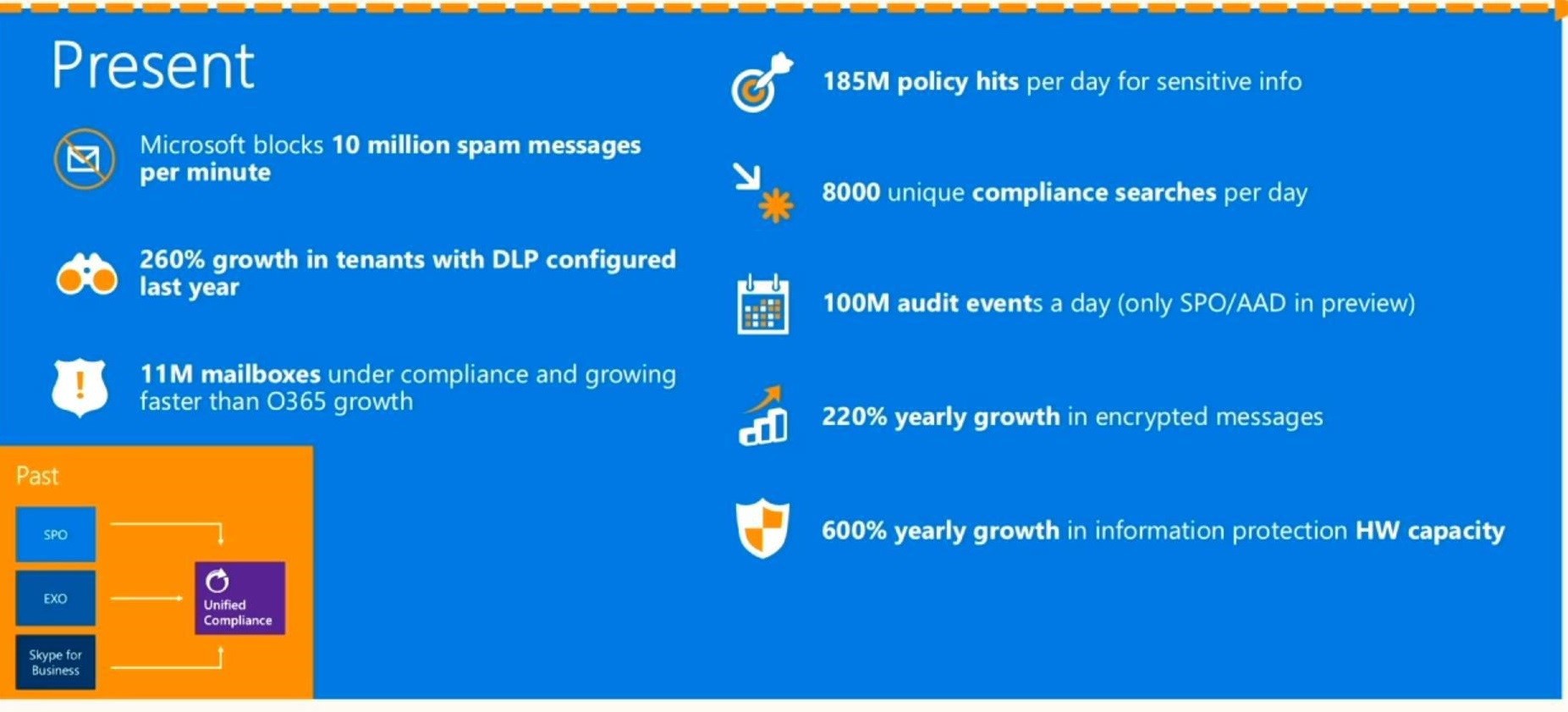
It is these issues that deprive sleep and become a headache for IT managers of companies using public cloud services. Answers to this question at the conference Microsoft Ignite, held from 4 to 8 May 2015 in Chicago, voiced by Brian Reid of NBConsult. Here is what he told about the methods of ensuring information security for organizations using Office 365.
1. Security Policy
Always use password policy and time limits to secure your data and application access. There are various settings for the timing of updating passwords depending on user profiles. Passwords for cloud service users lose their relevance after 90 days by default, while users synchronized with Active Directory obey the policy in accordance with the preferences settings. For cloud service users, a free password reset is available in self-service mode. With Azure Active Directory, you can allow users of the premium system to change passwords for cloud services. There are 4 ways to authenticate when resetting the password - via office phone, mobile phone, e-mail and secret questions.
2. Data Loss Prevention (DLP)
The data loss prevention strategy ensures the safety of confidential and personal data from unauthorized downloading, distribution or e-mail. DLP is available in SharePoint Online and Exchange, and can be integrated with Enterprise Search. At the same time, you can create policies to restrict content to be saved in certain places, such as One Drive for Business and SharePoint Online. When you enable DLP for testing, it will report inconsistent data loading and storage of data that violates security policy.
')

3. Rights Management
Rights management protects documents and email using encryption and related access policies. Documents may only be used by certain users for specific purposes. You can set content matching rules and create offline access settings, as well as set document-level policies, which, for example, will not allow an unauthorized user to open a Word document saved to disk. This option requires an E3 license or rights management license in Azure.
4. Encrypting Messages in Office 365
Encrypting messages in Office 365 requires entering a login password to read and reply to emails. It usually works through a single access password for accessing an email. Message encryption is available in E3 Office 365.
5. Mobile Device Management (MDM)
Mobile device management allows you to protect data on users' devices. MDM allows you to set access conditions, demarcate policies for different users, manage mobile devices and delete data from them, if necessary, in part or in full. MDM has been freely offered in commercial subscription packages for Office 365 since May 2015.
6. Multifactor authentication
Multi-factor authentication requires more than just a username and password to access Office 365. It can be set for each user individually. Users, in addition to the standard login and password, receive a call to a phone or text message. Answering a call or entering a received access code in a browser provides authentication with an increased level of security. The system can be switched on depending on the IP address, requesting an additional code only when accessing from public networks and deactivating when working in the office. Multi-factor authentication is a free option in all Office 365 plans.
7. Extended threat protection
Exchange Online Protection protects all Exchange Online mailboxes as part of a subscription. Extended threat protection will be available by the end of 2015 as an additional option to deal with serious issues such as phishing from trusted sources and malware attacks through application vulnerabilities.
8. Client Security
Do not forget about the security of client devices that have access to Office 365. Be sure that updates to solve IS problems are installed in a timely manner. Using Active Directory Federation Services you can set security policies that restrict users from logging in from specific IP addresses. Keep in mind that the mobile device management functionality described above replaces this option.
9. Deploying the Office Client
This security method ensures that the client version is up to date.
Office by installing the latest updates. Users get the flexibility to customize updates at certain time intervals. You can control the situation through Click2Run's XML-based process, available only in the Office 365 Pro Plus subscription plans.
10. Sharing content
The admin portal provides the ability to enable or restrict content sharing. You can control content usage in Office 365, including sites, calendar, Skype for Business, and other applications. There are reports that show content sharing settings. The administrator can change the settings directly from the management console, without entering the application settings.

Source: https://habr.com/ru/post/259253/
All Articles