Attackers use Linux / Moose to compromise Linux-embedded systems, part 1
Malware Linux / Moose is used by attackers to compromise various devices running Linux, including network routers. On a compromised router or other Linux / Moose device, it will intercept network traffic and provide its operators with a proxy service. As a rule, intruders are interested in HTTP session files (cookies) from popular network services. They will be used by intruders to perform various illegal actions through a proxy.

The malware is represented by regular ELF executable files, from which all debug information has been removed. Linux / Moose uses multi-threading in its work; it creates more than 30 threads for performing various tasks. Many of them are used to automatically search and infect other devices.
General information
')
Linux / Moose uses unconventional network-penetration mechanisms in comparison with other malware targeted at routers. He also specializes in DNS traffic redirection (DNS hijacking) and the forced termination of other malware processes if they are active in the system.
We were able to collect various statistics on the work of Moose by creating a special environment, as well as to track the interaction of the infected system with network services, to compromise which the malicious code is aimed at. The malware does not have mechanisms in its arsenal that would allow it to survive after the device is rebooted. It also does not specialize in providing remote shell access to botnet operators.
Below are the key findings that we were able to obtain when analyzing Linux / Moose.
The Moose study showed us the following features of this malware.
The malware has no special mechanisms to compromise other systems. Only those that have weak login credentials are subject to compromise. Moose does not use any vulnerabilities in the OS or software to compromise other devices. In fact, such a simple method of compromise is still very effective, according to a recent report by FireEye, it is one of the ten most urgent reasons for the leakage or theft of these companies. Below is a general scheme of the Moose.

Fig. The general scheme of work Linux / Moose.
A malicious program periodically interacts with its managers C & C-servers, the list of which is hard-wired in its executable file. To do this, the malware selects one of these servers, which will later provide it with configuration information and send instructions. We call this server a configuration C & C server (configuration C & C server). There are also other types of management servers, to which we have named the reporting C & C server (report C & C server) and the C & C relay server (relay C & C server). At first, Moose sends reports of infection, and the second is used for NAT traversal operation.
Compromising network services and using proxies
In the analysis of Moose, we found many opportunities that it provides for attackers. These features have been indicated above. For a more detailed picture, we launched our own infected devices. Below are the HTTP cookies that the bot is trying to steal for further fraud on the part of intruders.
We monitored the state of one of the infected routers, which was protected by the firewall, and were able to obtain statistics of the proxy traffic passing through it. Statistics were collected for almost a month in the spring of 2015.

Fig. Statistics of proxy traffic distributed by ports.
The diagram above shows that most of this traffic is encrypted. The malware operator's traffic passes through TCP port number 2318. This port is used to communicate with the external IP address of the infected device and the proxy client. It should be noted that most of the traffic we recorded on the infected router belonged to the Instagram social service (HTTP), and the protocol level was then upgraded from HTTP to the HTTPS secure connection level using the Location: protocol field.
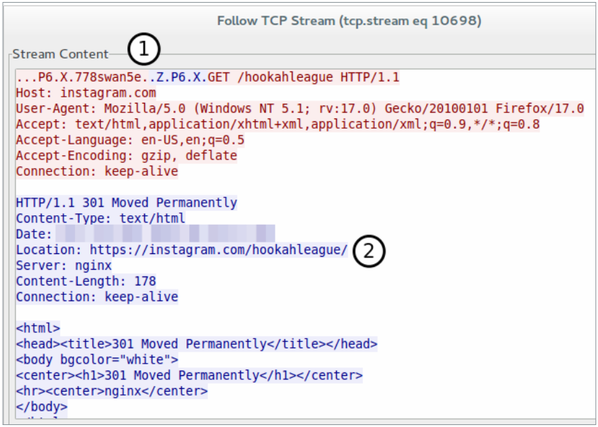
Fig. The Instagram service server translates a client (fake account) to use the HTTPS protocol using the HTTP field Location field.
At the first stage, you can see the use of a proxy using the SOCKS protocol, then the client can be switched to the HTTPS mode from the server side. Although the transmitted traffic is encrypted, we can see the IP address of the destination host. In addition, we can check the certificate that identifies the server and its so-called. Common Name (CN). CN is a required attribute that allows you to verify the authenticity of the website and provides us with an accurate description of the purpose of the transmitted traffic.

Fig. Distribution of HTTPS traffic (proxy) by services on the example of a compromised router.
It can be seen that most of the traffic belonged to the services of Twitter, Instagram, Soundcloud. The diagram on the right shows the services included in the "Other" item. In addition to the encrypted data, we were able to obtain data about autonomous systems (Autonomous Systems, AS), to which proxied traffic was sent through the passive DNS information mechanism. Below is a list of organizations that have been affected by Linux / Moose.
We were also able to obtain information on the number of requests for web services that were made through a proxy and for what task this proxy was used.

Fig. A visual representation of the proxy activity, the traffic is distributed according to the type of information transmitted.
The diagram above shows that most of the traffic belongs to network services that have been identified through the aforementioned CN certificates, passive DNS information, and the IP addresses of the autonomous system. Botnet traffic is the number of proxy requests that were sent to the managing C & C server and were always destined for TCP port 2318. All other requests are of the “Other” type. Obviously, the above statistics show that cybercriminals actively use infected computers for illegitimate access to social services, and, on average, more than 500 requests pass through the infected router every day.
Despite our efforts, we could not reliably count the number of compromised routers. Moose itself is designed to make such an operation more difficult. The bot does not use the P2P protocol; instead, the IP address of the manager of the C & C server is hard-wired in its code, it also allows only clients from a specific list of IP addresses to connect to the proxy. Another reason for our failure was the lack of desire of hosting providers to assist us in the investigation. We used different mechanisms for counting the number of infected devices, which are listed below.
One of such mechanisms for counting the activity of Moose on port 10073 is the Internet Storm Center . This port is not regulated by the IANA organization and is not used by any popular software, so the abnormally large amount of traffic passing through this port indicates the activity of this malicious program.
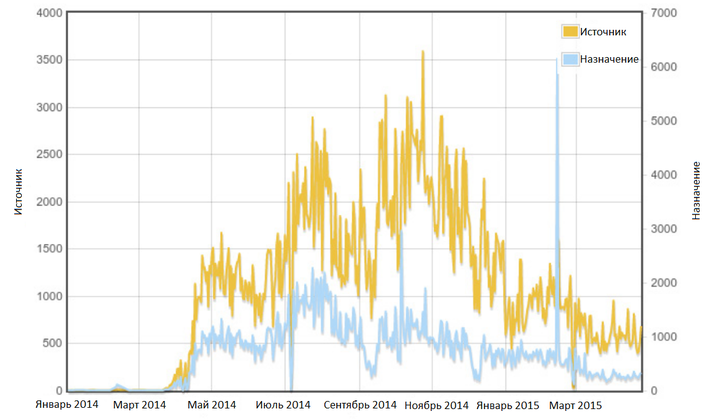
Fig. Activity of potentially compromised devices on port 10073.
Above in the figure, one can see that a significant increase in Moose activity has been observed since mid-2014, more precisely, from April. We first encountered this malware at the end of July 2014. At the end of 2014, its activity began to decline, despite the fact that the authors themselves are constantly engaged in updating the malware.
In the bot itself, the attackers laid quite aggressive propagation mechanisms. Below is the statistics of the activity of the bot to find new devices to compromise for 24 hours.

Fig. Statistics scanned by the bot new devices to compromise for 24 hours.
In 24 hours, the bot performed 170 thousand connection attempts on port 10073, which corresponds to 23 thousand unique hosts. Of these, 36 connections were successful and ended with TCP connections (handshake), which means the potential for compromising these devices. Of the 85 thousand attempts by Telnet connections that were made to 18 thousand unique hosts, 161 attempts ended with a request for Telnet credentials.
In fact, this statistic may be inaccurate, since it largely depends on the type of equipment on which the malware is running. We started the bot in software emulation mode, which is a slowing down factor in the operation of malware. In other words, we do not know how this data corresponds to the data on a really infected device.
We also asked our friends from Rapid7 to scan the Internet address space for the availability of both ports 10073 and 23 (Telnet) in order to get a general picture of devices and computers that fall under the “Moose orientation”. It turned out that 1 million IP addresses meet this requirement. If we subtract from this number the number of devices (IP) that did not request credentials for a Telnet connection, we will get about 50 thousand potentially infected hosts.
Malicious software Linux / Moose requires Linux OS as an environment for its execution. Moose executable ELF files depend on the popular C-library for embedded systems called uClibc . Today, many so-called. embedded systems running Linux, this applies to routers, as well as higher-level networking equipment. Some infected devices are easier to identify than others. For example, after its launch on the system, the malicious program checks the presence of the /home/hik/start.sh file on the disk. This file is usually located in HikVision's DVR devices, which have already become a victim of malware for embedded systems.
Devices of the following vendors are vulnerable to infection with Linux / Moose: Actiontec, HikVision, Netgear, Synology, TP-Link, ZyXEL, Zhone. In addition, medical devices like Hospira Drug Infusion Pump are also vulnerable.
As we already mentioned, attackers use Linux / Moose to steal HTTP session data for various social services. Then this data is used for fraudulent actions in these services, including operations like setting, cheating new Followers or subscribers. A bot is used to perform all of these operations, so on one of the infected routers we were able to observe malware attempts to gain access to more than 700 different Instagram accounts during the month. The following fake account was intentionally created by attackers for this purpose.

Fig. Fake account intruders.
A few days later this account was already following 30-40 social service accounts.

Fig. Fake accounts of intruders.
Below is a snapshot of the HTTP traffic in the Wireshark tool. In the Location field of the protocol header you can see the user name, this line is highlighted in yellow. The operators did not wind up the list of the Following-Users immediately, but at certain intervals of activity, masking the fraudulent activity.
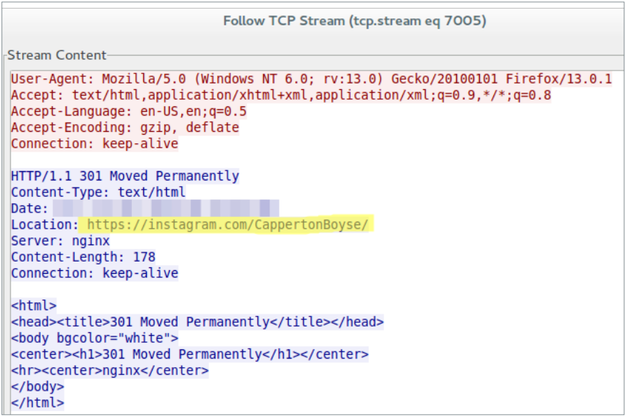
Fig. Fragment of the HTTP traffic of the Instagram service proxied by attackers.
A few hours later this account has already followed 36 users.

Fig. Fake Instagram account.
Fig. Users followed by a malicious user account.
We noticed one of the accounts followed by the fake Instagram user, which is listed below. Despite a small number of publications, he has an abnormally large number of followers.

Fig. Account of one of the users, followed by the above false account. A week later, the number of followers for him increased several times.
Compromise DNS Services Router
As we mentioned above, a bot is able to redirect DNS requests (DNS hijacking) of the router to the addresses that the attackers need. Such an operation is performed by the payload code, which is launched only during the infection process of the router. In addition, by default, the C & C server does not give the bot a command to use DNS redirection. Below is a typical DNS compromise pattern that attackers can use for their own purposes.
Further, the bot can configure the DNS records so that they point to phishing sites, malware, and also allow attackers to perform an attack like Man-in-the-Middle (MitM), which will prevent the client from switching to a secure HTTPS connection during operation. with this or that server.
General scheme of work
As we have already mentioned, Linux / Moose is represented by ELF executable files, in which debugging information is completely absent. These files are statically compiled with the uLibc library. In doing so, the malware relies on multithreading in its execution, simultaneously creating more than 30 threads during the infection procedure.
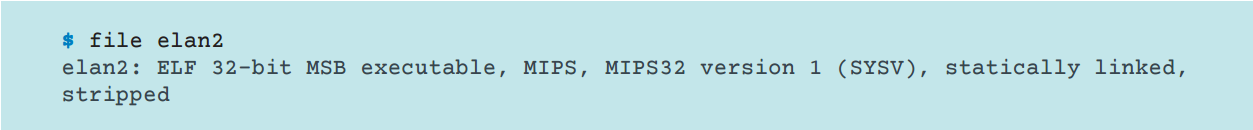
Fig. Information about the malicious executable file.
As a sample for analysis, we chose the version of the malicious program that runs on the MIPS architecture. Various screenshots of fragments of malicious code belong to this particular architecture. We also skimmed through similar samples for the ARM architecture, they turned out to be almost identical. Below is a diagram of the operation and interaction of the various components of Moose.

Fig. The scheme of interaction of components Moose.
The malware uses a special function to obfuscate messages sent to the C & C server. This feature is identical for the various options and components of Moose. Below is its Python code.
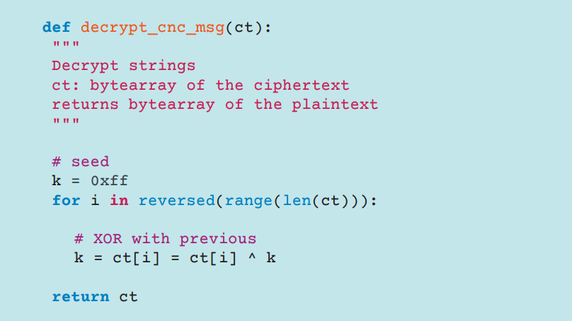
Fig. The function of obfuscation messages C & C-server.
Infection of devices
We attributed Moose to a class of malware like the worm (worm) because of its ability to automatically replicate. To do this, the bot launches three sets of streams, the first one is engaged in scanning arbitrary (random) IP addresses, the second one scans a certain range of addresses, the third one is the streams created on each network interface of the router. Threads execute the same code fragment, which we will call the scanner thread.
The number of threads for each of these sets is determined by the configuration C & C server. The cnccfg_nb_thdscan_local parameter determines the number of threads that will scan a range of IP addresses that are close to the external IP address of the router. The cnccfg_nb_thdscan_ext parameter determines the number of threads that will be used to scan randomly taken IP addresses. The cnccfg_flag_scanner_sniffer parameter defines the latter case. In a real situation, we observed 10 launched streams of the first set, 20 streams of the second and 1 stream for each interface of the router in the latter case.
The figure below shows the above IP address space scan.

Fig. The mechanism for finding new victims through the scanning of the space of IP addresses.
At each IP address, the malicious code performs the following actions: checks the connectivity to TCP port number 10073. If it successfully passes the TCP procedure of a handshake (handshake), it refuses further actions and considers that this host is already infected. Information about this will be sent to the reporting C & C server.

The malware is represented by regular ELF executable files, from which all debug information has been removed. Linux / Moose uses multi-threading in its work; it creates more than 30 threads for performing various tasks. Many of them are used to automatically search and infect other devices.
General information
')
Linux / Moose uses unconventional network-penetration mechanisms in comparison with other malware targeted at routers. He also specializes in DNS traffic redirection (DNS hijacking) and the forced termination of other malware processes if they are active in the system.
We were able to collect various statistics on the work of Moose by creating a special environment, as well as to track the interaction of the infected system with network services, to compromise which the malicious code is aimed at. The malware does not have mechanisms in its arsenal that would allow it to survive after the device is rebooted. It also does not specialize in providing remote shell access to botnet operators.
Below are the key findings that we were able to obtain when analyzing Linux / Moose.
- The malicious program is aimed at compromising home routers and modems, including those that are provided to users by ISP-providers.
- Linux / Moose contains mechanisms for its penetration into the network served by the router.
- The malware can intercept traffic that passes through a compromised device, so it can listen on various types of devices, including PCs, laptops, and smartphones.
- Moose runs a complex proxy service (SOCKS and HTTP) on a compromised device, which can only be accessed from a fixed list of IP addresses.
- Operators use infected devices to perform fraudulent activities on social services on Twitter, Facebook, Instagram, YouTube, etc.
- Attackers can configure the malware so that it will redirect the DNS traffic passing through the router. This technique allows them to organize a Man-in-the-Middle (MitM) attack.
- Moose infects t. Linux-based embedded devices that run on MIPS and ARM architecture.
The Moose study showed us the following features of this malware.
- It has mechanisms for distributing its files on the Internet using the LAN interfaces of a compromised router.
- The Moose service listens on port number 10073, which allows certain IP addresses to make proxy connections through a compromised device. For the organization of the proxy protocols are used HTTP / HTTPS and SOCKS.
- The malicious program can send traffic from the C & C server manager to other hosts, which allows you to effectively bypass the NAT security systems.
- Moose listens for network connections passing through the router and sends part of the received traffic to the C & C server.
- Moose periodically monitors the presence of other malicious programs in the compromised OS and forcibly terminates their processes in case of detection.
The malware has no special mechanisms to compromise other systems. Only those that have weak login credentials are subject to compromise. Moose does not use any vulnerabilities in the OS or software to compromise other devices. In fact, such a simple method of compromise is still very effective, according to a recent report by FireEye, it is one of the ten most urgent reasons for the leakage or theft of these companies. Below is a general scheme of the Moose.

Fig. The general scheme of work Linux / Moose.
A malicious program periodically interacts with its managers C & C-servers, the list of which is hard-wired in its executable file. To do this, the malware selects one of these servers, which will later provide it with configuration information and send instructions. We call this server a configuration C & C server (configuration C & C server). There are also other types of management servers, to which we have named the reporting C & C server (report C & C server) and the C & C relay server (relay C & C server). At first, Moose sends reports of infection, and the second is used for NAT traversal operation.
Compromising network services and using proxies
In the analysis of Moose, we found many opportunities that it provides for attackers. These features have been indicated above. For a more detailed picture, we launched our own infected devices. Below are the HTTP cookies that the bot is trying to steal for further fraud on the part of intruders.
- Twitter: twll, twid
- Facebook: c_user
- Instagram: ds_user_id
- Google: SAPISID, APISID
- Google Play / Android: LAY_ACTIVE_ACCOUNT
- Youtube: LOGIN_INFO
We monitored the state of one of the infected routers, which was protected by the firewall, and were able to obtain statistics of the proxy traffic passing through it. Statistics were collected for almost a month in the spring of 2015.

Fig. Statistics of proxy traffic distributed by ports.
The diagram above shows that most of this traffic is encrypted. The malware operator's traffic passes through TCP port number 2318. This port is used to communicate with the external IP address of the infected device and the proxy client. It should be noted that most of the traffic we recorded on the infected router belonged to the Instagram social service (HTTP), and the protocol level was then upgraded from HTTP to the HTTPS secure connection level using the Location: protocol field.

Fig. The Instagram service server translates a client (fake account) to use the HTTPS protocol using the HTTP field Location field.
At the first stage, you can see the use of a proxy using the SOCKS protocol, then the client can be switched to the HTTPS mode from the server side. Although the transmitted traffic is encrypted, we can see the IP address of the destination host. In addition, we can check the certificate that identifies the server and its so-called. Common Name (CN). CN is a required attribute that allows you to verify the authenticity of the website and provides us with an accurate description of the purpose of the transmitted traffic.

Fig. Distribution of HTTPS traffic (proxy) by services on the example of a compromised router.
It can be seen that most of the traffic belonged to the services of Twitter, Instagram, Soundcloud. The diagram on the right shows the services included in the "Other" item. In addition to the encrypted data, we were able to obtain data about autonomous systems (Autonomous Systems, AS), to which proxied traffic was sent through the passive DNS information mechanism. Below is a list of organizations that have been affected by Linux / Moose.
- Fotki (Yandex)
- Instagram (Facebook)
- Live (Microsoft)
- Soundcloud
- Vine
- Yahoo
- YouTube (Google)
We were also able to obtain information on the number of requests for web services that were made through a proxy and for what task this proxy was used.

Fig. A visual representation of the proxy activity, the traffic is distributed according to the type of information transmitted.
The diagram above shows that most of the traffic belongs to network services that have been identified through the aforementioned CN certificates, passive DNS information, and the IP addresses of the autonomous system. Botnet traffic is the number of proxy requests that were sent to the managing C & C server and were always destined for TCP port 2318. All other requests are of the “Other” type. Obviously, the above statistics show that cybercriminals actively use infected computers for illegitimate access to social services, and, on average, more than 500 requests pass through the infected router every day.
Despite our efforts, we could not reliably count the number of compromised routers. Moose itself is designed to make such an operation more difficult. The bot does not use the P2P protocol; instead, the IP address of the manager of the C & C server is hard-wired in its code, it also allows only clients from a specific list of IP addresses to connect to the proxy. Another reason for our failure was the lack of desire of hosting providers to assist us in the investigation. We used different mechanisms for counting the number of infected devices, which are listed below.
One of such mechanisms for counting the activity of Moose on port 10073 is the Internet Storm Center . This port is not regulated by the IANA organization and is not used by any popular software, so the abnormally large amount of traffic passing through this port indicates the activity of this malicious program.

Fig. Activity of potentially compromised devices on port 10073.
Above in the figure, one can see that a significant increase in Moose activity has been observed since mid-2014, more precisely, from April. We first encountered this malware at the end of July 2014. At the end of 2014, its activity began to decline, despite the fact that the authors themselves are constantly engaged in updating the malware.
In the bot itself, the attackers laid quite aggressive propagation mechanisms. Below is the statistics of the activity of the bot to find new devices to compromise for 24 hours.

Fig. Statistics scanned by the bot new devices to compromise for 24 hours.
In 24 hours, the bot performed 170 thousand connection attempts on port 10073, which corresponds to 23 thousand unique hosts. Of these, 36 connections were successful and ended with TCP connections (handshake), which means the potential for compromising these devices. Of the 85 thousand attempts by Telnet connections that were made to 18 thousand unique hosts, 161 attempts ended with a request for Telnet credentials.
In fact, this statistic may be inaccurate, since it largely depends on the type of equipment on which the malware is running. We started the bot in software emulation mode, which is a slowing down factor in the operation of malware. In other words, we do not know how this data corresponds to the data on a really infected device.
We also asked our friends from Rapid7 to scan the Internet address space for the availability of both ports 10073 and 23 (Telnet) in order to get a general picture of devices and computers that fall under the “Moose orientation”. It turned out that 1 million IP addresses meet this requirement. If we subtract from this number the number of devices (IP) that did not request credentials for a Telnet connection, we will get about 50 thousand potentially infected hosts.
Malicious software Linux / Moose requires Linux OS as an environment for its execution. Moose executable ELF files depend on the popular C-library for embedded systems called uClibc . Today, many so-called. embedded systems running Linux, this applies to routers, as well as higher-level networking equipment. Some infected devices are easier to identify than others. For example, after its launch on the system, the malicious program checks the presence of the /home/hik/start.sh file on the disk. This file is usually located in HikVision's DVR devices, which have already become a victim of malware for embedded systems.
Devices of the following vendors are vulnerable to infection with Linux / Moose: Actiontec, HikVision, Netgear, Synology, TP-Link, ZyXEL, Zhone. In addition, medical devices like Hospira Drug Infusion Pump are also vulnerable.
As we already mentioned, attackers use Linux / Moose to steal HTTP session data for various social services. Then this data is used for fraudulent actions in these services, including operations like setting, cheating new Followers or subscribers. A bot is used to perform all of these operations, so on one of the infected routers we were able to observe malware attempts to gain access to more than 700 different Instagram accounts during the month. The following fake account was intentionally created by attackers for this purpose.

Fig. Fake account intruders.
A few days later this account was already following 30-40 social service accounts.

Fig. Fake accounts of intruders.
Below is a snapshot of the HTTP traffic in the Wireshark tool. In the Location field of the protocol header you can see the user name, this line is highlighted in yellow. The operators did not wind up the list of the Following-Users immediately, but at certain intervals of activity, masking the fraudulent activity.

Fig. Fragment of the HTTP traffic of the Instagram service proxied by attackers.
A few hours later this account has already followed 36 users.

Fig. Fake Instagram account.

Fig. Users followed by a malicious user account.
We noticed one of the accounts followed by the fake Instagram user, which is listed below. Despite a small number of publications, he has an abnormally large number of followers.

Fig. Account of one of the users, followed by the above false account. A week later, the number of followers for him increased several times.
Compromise DNS Services Router
As we mentioned above, a bot is able to redirect DNS requests (DNS hijacking) of the router to the addresses that the attackers need. Such an operation is performed by the payload code, which is launched only during the infection process of the router. In addition, by default, the C & C server does not give the bot a command to use DNS redirection. Below is a typical DNS compromise pattern that attackers can use for their own purposes.
- Malicious users infect with a malicious program routers located close to each other, for example, home routers of users of one ISP provider.
- Moose is awaiting the interception of network service cookies.
- When a user logs into their service account, the malware sends this cookie data to attackers.
- The attackers send the command to the bot, setting it up accordingly: turning off the host check setting for compromise before connecting via Telnet, turning on the DNS hijacking setting, searching for new victim devices is balanced to infect hosts with an IP address range that is close to external IP address of the router.
- Due to the host check turned off for compromise, Moose will re-infect devices it has already compromised. In the process of this reinfection, the bot will trigger fake DNS IP addresses.
- The user remains unaware that his router has been compromised and redirects his programs to fake IP addresses.
Further, the bot can configure the DNS records so that they point to phishing sites, malware, and also allow attackers to perform an attack like Man-in-the-Middle (MitM), which will prevent the client from switching to a secure HTTPS connection during operation. with this or that server.
General scheme of work
As we have already mentioned, Linux / Moose is represented by ELF executable files, in which debugging information is completely absent. These files are statically compiled with the uLibc library. In doing so, the malware relies on multithreading in its execution, simultaneously creating more than 30 threads during the infection procedure.

Fig. Information about the malicious executable file.
As a sample for analysis, we chose the version of the malicious program that runs on the MIPS architecture. Various screenshots of fragments of malicious code belong to this particular architecture. We also skimmed through similar samples for the ARM architecture, they turned out to be almost identical. Below is a diagram of the operation and interaction of the various components of Moose.

Fig. The scheme of interaction of components Moose.
The malware uses a special function to obfuscate messages sent to the C & C server. This feature is identical for the various options and components of Moose. Below is its Python code.

Fig. The function of obfuscation messages C & C-server.
Infection of devices
We attributed Moose to a class of malware like the worm (worm) because of its ability to automatically replicate. To do this, the bot launches three sets of streams, the first one is engaged in scanning arbitrary (random) IP addresses, the second one scans a certain range of addresses, the third one is the streams created on each network interface of the router. Threads execute the same code fragment, which we will call the scanner thread.
The number of threads for each of these sets is determined by the configuration C & C server. The cnccfg_nb_thdscan_local parameter determines the number of threads that will scan a range of IP addresses that are close to the external IP address of the router. The cnccfg_nb_thdscan_ext parameter determines the number of threads that will be used to scan randomly taken IP addresses. The cnccfg_flag_scanner_sniffer parameter defines the latter case. In a real situation, we observed 10 launched streams of the first set, 20 streams of the second and 1 stream for each interface of the router in the latter case.
The figure below shows the above IP address space scan.

Fig. The mechanism for finding new victims through the scanning of the space of IP addresses.
At each IP address, the malicious code performs the following actions: checks the connectivity to TCP port number 10073. If it successfully passes the TCP procedure of a handshake (handshake), it refuses further actions and considers that this host is already infected. Information about this will be sent to the reporting C & C server.
Source: https://habr.com/ru/post/259175/
All Articles