Making a Callback from the site using Askozia PBX
The popularity of callbackhunter and zingaya sowed an idea into my head, to realize the possibility of a callback from our site, using IP ATC Askozia, which has already been working for many years. Earlier, I wrote about it in a separate post .

The situation was also complicated by the fact that the site was located in a public network, and Askozia was inside a local network, and it was scary to publish it in open access.
Much has been written about the algorithms for implementing the callback mechanism from the Asterisk website. The most common is the generation of the Originate AMI after the customer enters his phone number on the site. And so we begin.
In the latest version of Askozia, a mechanism has finally emerged for active protection against attacks on SIP telephone systems in the form of the iptables_fail2ban pair widely known in Linux circles. And this, in conjunction with the fact that Askozia has a read-only linux kernel, greatly enhances protection against hacking, even with respect to such a common distribution like FreePBX. Although of course you can argue with me :)
So, the source data:
The site www.telefon1c.ru has an ip address 93.188.40.98
Askozia is deployed as a virtual machine with a public address 93.188.40.99
First we activate the firewall and allow access to the system from our local network, indicating its subnet. In this case, setting 172.16.32.0/24 means all addresses in the range 172.16.32.0 ~ 172.16.32.255
')

When configuring the firewall, I chose the option of installing Askozia in the cloud and received the following default lock settings

Just in case, I indicated my home IP address to access the Askozia web interface in case of incorrect settings of the firewall, otherwise you can no longer get into the admin area :)
Next, activate fail2ban to block the selection of passwords. This is done with one tick, the rest of the settings will remain the default.

Add a custom rule for iptables so that the site can reach the AMI interface through the Firewall.
To do this, in the advanced section, add the following line:
iptables -A INPUT -p tcp -s 93.188.40.98 --dport 5038 -j ACCEPT
It should turn out as in the picture:

This completes the firewall configuration, saves the changes and proceeds to the AMI interface configuration.
Let's create a new webcall user with minimal rights and allow him access only from one IP address, our site.
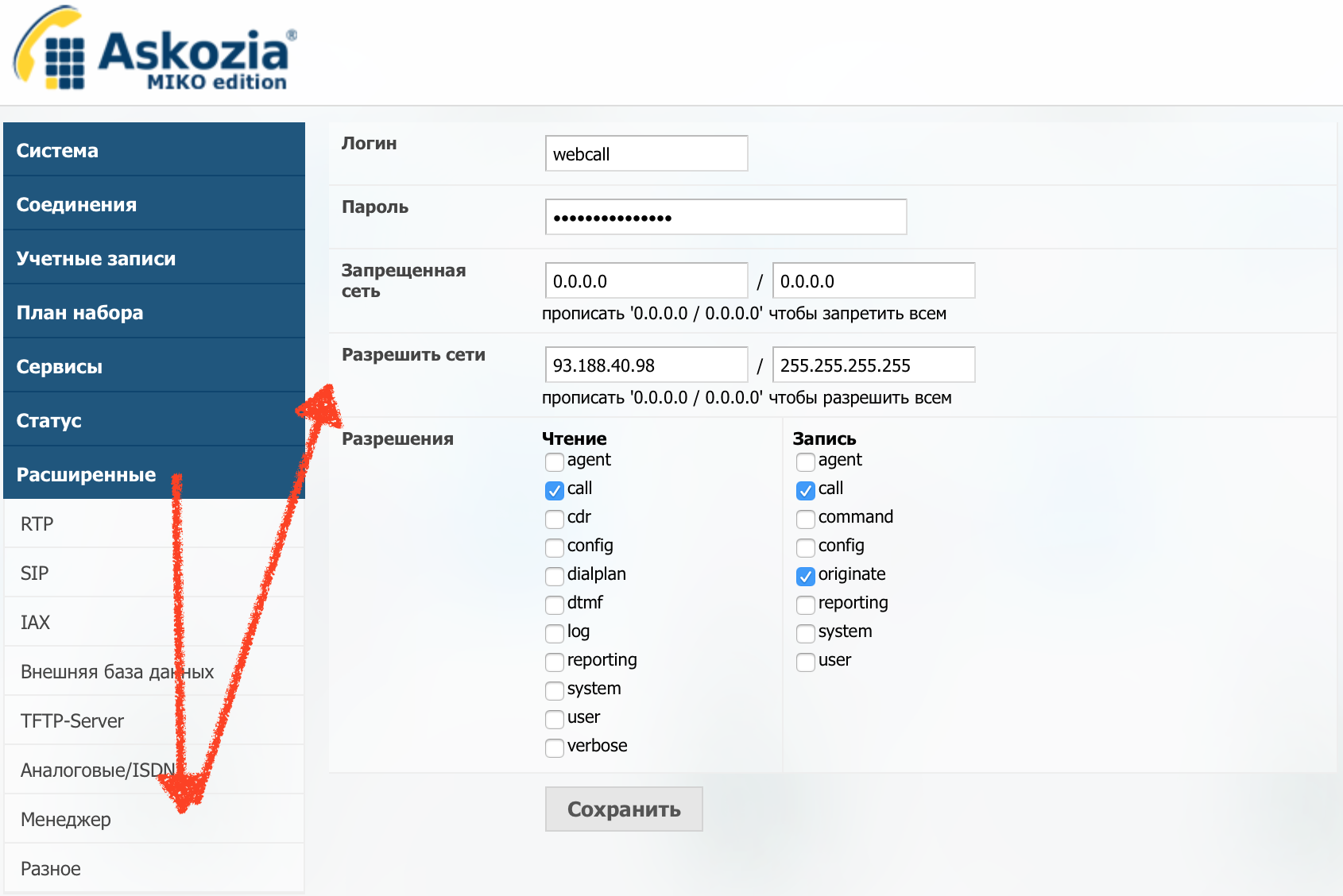
We give him a complex-complex password: 9 [U. [2o {9 $? H $$ su
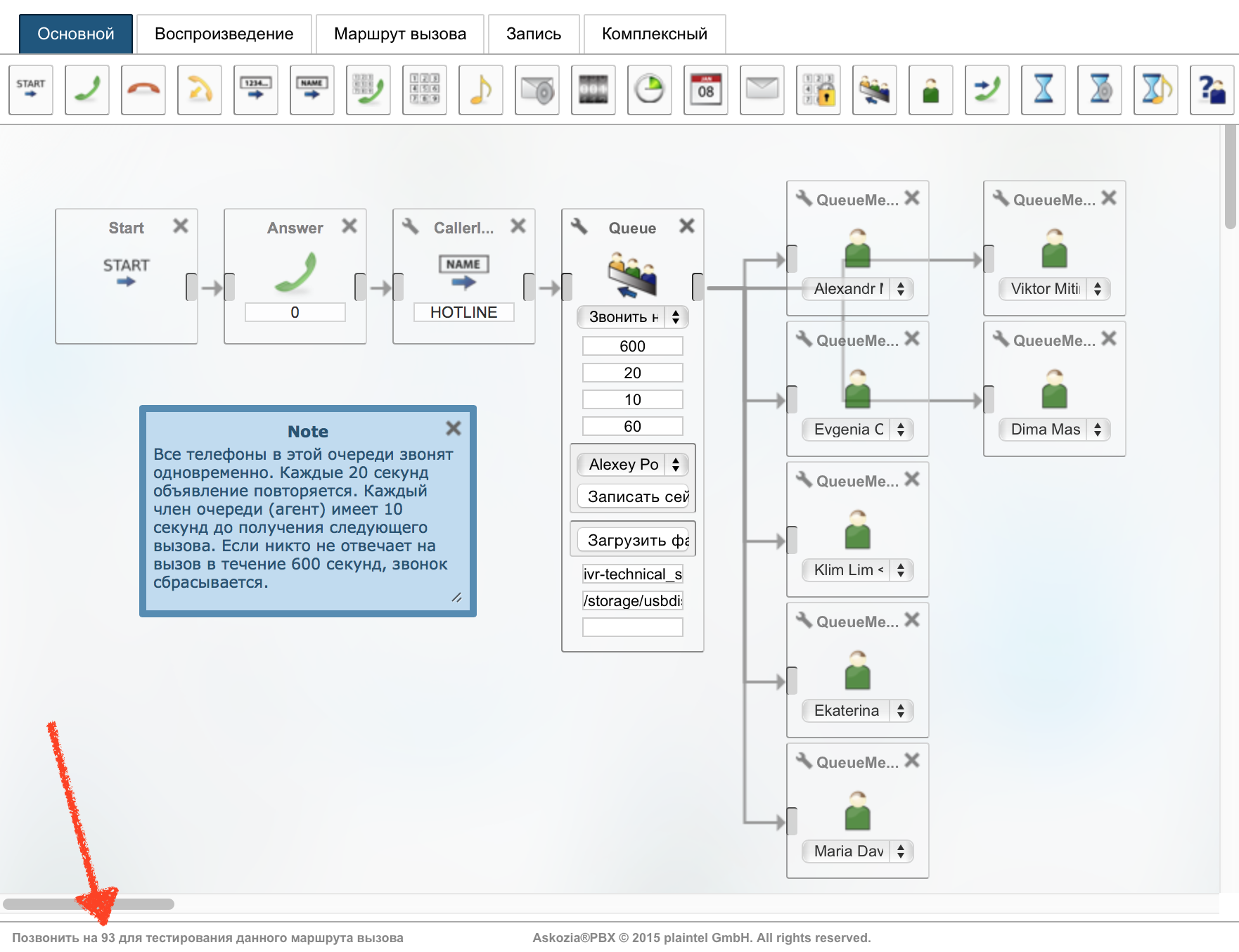
Now we need to understand where we will direct the call from the Web site. I decided not to invent anything tricky and send it along the same route that customers call us at HOTLINE. This is the call queue with extension 93
Well, the last thing we need is to get the context of the provider through which we will make a call to the client. To do this, open the provider settings editing card and copy its context from the address bar.

Now we have everything you need to set up a callback from the site:
First we need to draw a simple form for entering a phone number on the site.

What happened in the end:

The situation was also complicated by the fact that the site was located in a public network, and Askozia was inside a local network, and it was scary to publish it in open access.
Much has been written about the algorithms for implementing the callback mechanism from the Asterisk website. The most common is the generation of the Originate AMI after the customer enters his phone number on the site. And so we begin.
Setup on the Askozia side
In the latest version of Askozia, a mechanism has finally emerged for active protection against attacks on SIP telephone systems in the form of the iptables_fail2ban pair widely known in Linux circles. And this, in conjunction with the fact that Askozia has a read-only linux kernel, greatly enhances protection against hacking, even with respect to such a common distribution like FreePBX. Although of course you can argue with me :)
So, the source data:
The site www.telefon1c.ru has an ip address 93.188.40.98
Askozia is deployed as a virtual machine with a public address 93.188.40.99
Firewall tincture and fail2ban
First we activate the firewall and allow access to the system from our local network, indicating its subnet. In this case, setting 172.16.32.0/24 means all addresses in the range 172.16.32.0 ~ 172.16.32.255
')

When configuring the firewall, I chose the option of installing Askozia in the cloud and received the following default lock settings

Just in case, I indicated my home IP address to access the Askozia web interface in case of incorrect settings of the firewall, otherwise you can no longer get into the admin area :)
Next, activate fail2ban to block the selection of passwords. This is done with one tick, the rest of the settings will remain the default.

Add a custom rule for iptables so that the site can reach the AMI interface through the Firewall.
To do this, in the advanced section, add the following line:
iptables -A INPUT -p tcp -s 93.188.40.98 --dport 5038 -j ACCEPT
It should turn out as in the picture:

This completes the firewall configuration, saves the changes and proceeds to the AMI interface configuration.
Let's create a new webcall user with minimal rights and allow him access only from one IP address, our site.

We give him a complex-complex password: 9 [U. [2o {9 $? H $$ su
Now we need to understand where we will direct the call from the Web site. I decided not to invent anything tricky and send it along the same route that customers call us at HOTLINE. This is the call queue with extension 93

Well, the last thing we need is to get the context of the provider through which we will make a call to the client. To do this, open the provider settings editing card and copy its context from the address bar.

Now we have everything you need to set up a callback from the site:
- IP Address Askozia: 93.188.40.99
- User AMI login: webcall
- AMI User Password: 9 [U. [2o {9 $? H $$ su
- Provider context: SIP-PROVIDER-1646711234f40d80266c2f
- Internal call route number: 93
Setting up scripts on the site side
First we need to draw a simple form for entering a phone number on the site.

Form code from the Bitrix call.php site
<? // require($_SERVER["DOCUMENT_ROOT"]."/bitrix/header.php"); $APPLICATION->SetTitle(" "); ?> <div class="ui page grid"> <div class="column"> <div class="ui segment"> // Askozia <? // $APPLICATION->IncludeFile("/ajax/ajax_call_handler_inc.php", Array(), Array( "MODE" => "html", "NAME" => " " )); ?> // <h1 class="ui header block"> </h1> <div class="ui segment"> <h3 class="ui header"> callback</h3> , . <div class="ui form" id="CallOverAsterisk"> <form class="vertical" action="/call.php" method="post"> <div class="ui action large left icon input"> <input type="text" size="20" maxlength="10" name="txtphonenumber" placeholder=" , : +7 (495) 123-45-67" id="phone"> <div class="ui button orange" id="calloverasterbtn"></div> </div> <button type="submit" style="display:none" id="calloverasterbtnsbmnt" name="call_send"/></button> </form> </div> </div> </div> </div> </div> // , <script type="text/javascript"> $("#phone").mask("+7 (999) 999-99-99"); $("#phone").on("blur", function() { var last = $(this).val().substr( $(this).val().indexOf("-") + 1 ); if( last.length == 3 ) { var move = $(this).val().substr( $(this).val().indexOf("-") - 1, 1 ); var lastfour = move + last; var first = $(this).val().substr( 0, 9 ); $(this).val( first + '-' + lastfour ); } }); // POST "" $("#calloverasterbtn").click(function() { $("#calloverasterbtnsbmnt").click(); }); </script> // <?require($_SERVER["DOCUMENT_ROOT"]."/bitrix/footer.php");?> The handler php code for generating the AMI command /ajax/ajax_call_handler_inc.php
<?php if (isset($_REQUEST["call_send"])){ #-------------------------------------------------------------------------------------------- # Askozia #-------------------------------------------------------------------------------------------- $strHost = "93.188.40.99"; //IP Askozia $strUser = "webcall"; // AMI Manager $strSecret = "9[U.[2o{9$?H$$su"; // $strContext = "internal"; // . Askozia internal $strExten = "93"; // , $strwebnum = preg_replace('~\D+~','',$_REQUEST['txtphonenumber']); // $strChannel = "Local/".$strwebnum."@SIP-PROVIDER-1646711234f40d80266c2f"; // IP . : SIP-PROVIDER-1646711234f40d80266c2f $strWaitTime = "30"; // $strPriority = "1"; // #-------------------------------------------------------------------------------------------- # #-------------------------------------------------------------------------------------------- #specify the caller id for the call $strCallerId = "Web Call <$strwebnum>"; $length = strlen($strwebnum); if ($length == 11 && is_numeric($strwebnum)) { $oSocket = fsockopen($strHost, 5038, $errnum, $errdesc,30) or die("Connection to host failed"); stream_set_timeout($oSocket, 0, 500000); fputs($oSocket, "Action: login\r\n"); fputs($oSocket, "Events: off\r\n"); fputs($oSocket, "Username: $strUser\r\n"); fputs($oSocket, "Secret: $strSecret\r\n\r\n"); while ($line = fgets($oSocket)) $result .= $line; fputs($oSocket, "Action: originate\r\n"); fputs($oSocket, "Channel: $strChannel\r\n"); fputs($oSocket, "WaitTime: $strWaitTime\r\n"); fputs($oSocket, "CallerId: $strCallerId\r\n"); fputs($oSocket, "Exten: $strExten\r\n"); fputs($oSocket, "Context: $strContext\r\n"); fputs($oSocket, "Priority: $strPriority\r\n\r\n"); while ($line = fgets($oSocket)) $result .= $line; fputs($oSocket, "Action: Logoff\r\n\r\n"); while ($line = fgets($oSocket)) $result .= $line; fclose($oSocket); echo '<div class="ui success message"> '.htmlentities($_REQUEST["txtphonenumber"], ENT_QUOTES, "UTF-8").'. ! , . </div>'; } else { echo '<div class="ui negative message"> . 11 , +7 (495) 229-30-42</div>'; unset($_SESSION['call_send']); } } ?> What happened in the end:
Source: https://habr.com/ru/post/259165/
All Articles