What was on PHDays V: signs of interception of GSM-signal, the best time to hack Wi-Fi, the future of encryption

Technological singularity is expected only after 15 years, but the Positive Hack Days transition phase is happening right now. The fifth forum was attended by a record number of participants - more than 3,500 people, which is comparable with the leading international hacker conferences, and the number of reports, sections and various activities exceeded one hundred. An incredible competitive program was held at the site with burglary of rockets, electrical substations, ATMs, railways, and the main hacker competition of the year PHDays CTF was won by the More Smoked Leet Chicken team, having succeeded the most in the fascinating speculations of the exchange - congratulations! But we will tell about all this in detail later. In this material, we briefly consider a number of purely practical techniques and recommendations, which we noted on May 26 and 27 at the ITC.
The color of the day versus social engineering
Founder of the world's first themed social-engineering internet site, Chris Hadnagi, on PHDays, in a report “Social engineering for fun and seriously”, shared his experience in protecting businesses from hackers using psychological methods. One of his stories was about a pregnant girl who managed to get into the most critical part of the office — the server room, protected by various means of authentication.
When asked whether we want people to study all kinds of psychological effects, become soulless robots, Chris Hadnagi replied that only technologies change, and people will always remain people, and cited another example from his practice. In one of the companies on the corporate website every morning they began to post an image with the color of the day. And in the case of phishing attacks, when an attacker disguises himself as an employee of the IT or HR department in order to find out confidential information, it was enough for the employee to politely ask about the day's color. We use passes to enter the office, and other access channels should also have peculiar passes; there is nothing wrong with that.
')

How to know that the phone is tapped
Sergey Kharkov during the report “Protection against GSM signal interception” spoke about the main signs of wiretapping, as well as hardware and software diagnostic methods. For example, in order for a switch to occur, an attacker needs to force your device to connect to its virtual cell, otherwise the phone will find a better alternative. Therefore, one of the signs that your device is connected to the attacker's virtual base station is a high signal strength and an unnaturally high value of the C2 coefficient responsible for the cell selection priority.
PHDays V has generally paid a lot of attention to mobile security issues. Positive Technologies expert Dmitry Kurbatov held a separate master class on this topic, after which anyone could take part in the MiTM Mobile contest and try to penetrate the network of our small telecom operator, specially created for the contest. Participants could perform various operations: intercepting SMS, USSD, telephone conversations, working with an IMSI-catcher, hacking encryption keys using kraken, and cloning mobile phones. Raitap about the most interesting moments of the competition will be published soon.

Why do hackers attack the Olympics
Vladimir Kropotov, Fyodor Yarochkin, Kevin Williams, John Bombanek and other specialists in the protection of infrastructure facilities took part in a round table on the investigation of incidents in large infrastructures. In particular, Kevin, as an employee of the British special services NCCU, was directly involved in the defense of the Olympics in London, and Vladimir represented Positive Technologis, which helped defend the All-Russian State Television and Radio Broadcasting Company at the 2014 Olympics. As Fyodor Yarochkin noted, the model of threats in ensuring the security of major sporting events includes not only hacktivists or hooligans, the most dangerous category is various types of criminal business related to sweepstakes, any change in the situation can bring high profits. Kevin Williams said that in Britain, the practice of cooperation with CERT centers, which act as intermediaries between the state and companies, has proven itself well.

How to help the intrusion prevention system
Computer hackers have learned to confuse self-learning mechanisms embedded in network intrusion detection systems. Artificial Intelligence Specialist Clarence Chio, in his report "Methods of Detecting Network Attacks Based on Self-Learning Technology", reviewed a number of models used in IPS systems based on PSA, clustering, etc. Should people use techniques based on rules or machine learning? Clarence Chio believes that self-learning methods (ML-techniques) are only fine in theory, but in the real world they are not so impressive.


The safest mobile platform
Security experts Denis Gorchakov (who transferred to Alfa-Bank from Positive Technologies) and Nikolay Goncharov (MTS) in their report “Counteraction of mobile fraud on the operator’s network”, in particular, shared information about the most secure mobile operating system. The honorary title went to Windows Phone, for which no major epidemics have yet been registered. As for iOS, for example, there are many applications for this system, attacking devices both with and without jailbreak. With the most popular mobile system, everything is completely bad, and according to Android Security Report 2015, the level of malware distribution for Android in Russia is 3-4 times higher than the average.

Edward Snowden in your keyboard
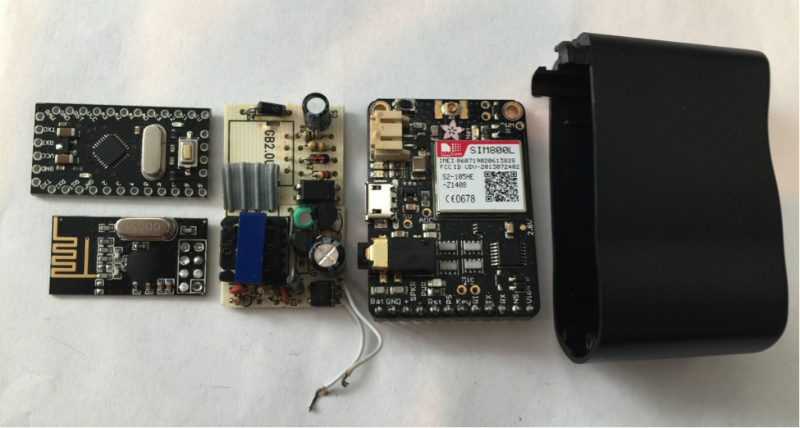
Wireless keyboards are not only able to discharge at the most inopportune moment, but can also reveal your confidential information. Andrei Biryukov, an information security system architect at MAYKOR, drew attention to this problem. He spoke about the concept of keysweeper - a simple device based on an Arduino prototype board in the form of a charge that intercepts signals from keys pressed on a wireless keyboard and transmits data to an attacker. Scanning for viruses and computer vulnerabilities can detect spyware on your PC, but will not protect against keysweeper.
Victim Browser as Scan Tool
Dmitry Bumov (ONsec), a well-known specialist on de-anonymization , in the report “Not with nmap single” told how you can scan the internal infrastructure using the victim's browser without using JavaScript (it can be disabled, which will require XSS) and without launching nmap. You just need to force the victim to follow the necessary link, waiting for the client to enter the required DNS address.


The best time to catch Wi-Fi
The researcher Oleg Kupreev in the report “Review of the little-known nuances of WiFi” drew attention to the time periods and weather conditions that are most preferable for hackers when hacking Wi-Fi. The power of the high-frequency signal during the rain will be lower, so a hacker would rather choose another day to attack the thousands of users of the metro. On a WFS DDoS hunt using mdk3, it usually goes beyond midnight. It is not only inconvenient to do this in the evening (the only non-intersecting channels are 1, 6, 11), but it is also risky if you overload the session every five seconds, a person who watches the show online may have suspicions. WAP Enterprise hack in the morning when computers are turned on in offices.

How to force vendor to close vulnerabilities
In March, FSTEC opened a general access to the official database of threats and vulnerabilities, where more than one hundred and fifty threats and more than 10 thousand vulnerabilities were described. During the round table “The Role of the Expert Community in Forming a Databank of Information Security Threats”, Head of the FSTEC of Russia Vitaly Lyutikov said that one of the reasons for the emergence of a state resource was the prohibition of lawyers to refer to third-party CVE databases in Russian documents. At the same time, FSTEC assumed obligations to verify zero-day vulnerabilities and correspondence with the manufacturer.
Onion space vulnerabilities
Preserving anonymity in onion-resources inside DarkNeta is not as simple as it seems at first glance. Kaspersky Lab experts Denis Makrushin and Maria Garnayeva told what information about Tor users external users can get. Denis, in particular, developed a passive traffic collection system for the Exit node, which had two key properties - it allowed traffic through all ports and contained a sniffer catching all HTTP connections with the Referer header. If a person inside Tor clicks on a link and goes to the external web, then this package is caught. Discovered sites contained mostly ads for the sale of passwords, ancient databases. The authors of the report “Where anonymity ends in anonymous networks” also found that about a third of onion-resources contain vulnerabilities and allow you to execute arbitrary Javascript code.

Masalovich and search for forgotten configuration files
Not everyone can tell stories so captivatingly as the five-time PHDays member Andrei Masalovich (Inforus) - after an hour the audience decided not to release the competitive intelligence expert and the organizers extended the No Shades of Gray report. After telling one of his 700 relatively fair ways to get access to the usernames, passwords and databases of the site (by guessing the name of the backup copy of the CMS configuration file forgotten by the administrator), Andrey proceeded to the main topic - the need to develop the habit of doubting the authenticity of multimedia, graphic and text information.


Below is a demonstration in France.

The definition of "Photoshop" in the photos
Problems of reliability of the information were discussed at the Almaz Capital competition among start-up projects in the field of cybersecurity. Take part in the competition could any group of developers and engineers. It was not required to create a company for this stage, but the team and the prototype of the solution should have been submitted.

A grant in the amount of 1.5 million rubles was received by the company SMTDP Tech , which invented a kind of “anti-photoshop” - a technology for identifying corrections in a photo or video. This development can be useful for detecting falsification of images of a static billboard when it is actually sold to several customers or retouched in a photo of a car after an accident for backdating.
What will be the encryption

Almaz Capital Advisor Whitfield Diffie was at the forefront of the concept of "electronic digital signature" and the principles of asymmetric encryption, and on May 26 he shared his predictions on PHDays. “We could now build real digital fortresses and raise information protection methods to a new height if we spent as much money on defense as on attack,” said Whitfield Diffie from the huge PHDays plasma screens. “Today, high hopes are associated with quantum cryptography, a more accurate term for which is quantum key distribution. I am sure that this technology will avoid most of the problems during transportation, but I still do not know how to implement it technically, perhaps through radio or vibro communications. Another technology that is talked about a lot is homomorphic encryption, but I am skeptical about this type of encryption - a person may simply not have enough productive computer to decrypt the message. ”
Linguists come out of the shadows

Carefully looked into the future at the section “ Information Security - Future Professions ”, moderated by Positive Technologies specialist Yevgeny Minkovsky, and among the panelists were a member of the Russian Academy of Sciences, director of one of the largest training centers, business and government representatives. What specialties and technologies will be in demand in the information security industry in five years? And in fifteen? At the end of the meeting, experts voted, which brought a very unexpected result - the main information security profession in the future will be ... linguists. However, this point of view is quite consistent with the “ Atlas of new professions ”, published by the agency for strategic initiatives Skolkovo. In this list, the specialty "digital linguist" is named among the most promising. Such specialists will develop linguistic systems for semantic translation and processing of textual information, as well as new communication interfaces between humans and computers in natural languages.

The video versions of these and other presentations made on PHDays can be found on the website of the forum at: www.phdays.ru/broadcast .

Source: https://habr.com/ru/post/259135/
All Articles