We connect Microsoft Azure and a cloud of service provider in a uniform network
Today we will talk about how to create a hybrid cloud based on Microsoft Azure cloud and a cloud of a Russian service provider based on Microsoft Azure Pack, combining them into a single network space through Site-to-Site VPN. Plus we will create a single Active Directory domain based on this hybrid.
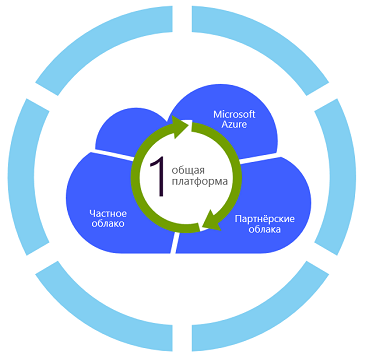
This scenario is a practical application of the concept of Microsoft Cloud OS - a single cloud platform for a private cloud, a Microsoft Azure public cloud and a partner cloud from a local service provider.
AzuRus service from Oblakoteka company will be used as a cloud of the service provider. This solution was implemented as part of the Microsoft Cloud OS Network Russia program with the participation of Microsoft engineers, and uses the Microsoft Azure Pack platform as a cloud management system. Due to this, it seamlessly integrates with the Microsoft Azure cloud.
')
Implementation details below.
Why do you need this?
1) You have a part of the services that you want to transfer to the cloud of the Russian service provider. It can be domain controllers, 1C and other internal services that you traditionally have hosted. You want these services to move painlessly to the cloud of a service provider somewhere near you, so that ping is good, and that the servers are in the territory of the Russian Federation.
2) You connect the service provider cloud and your local network either via Site-to-Site VPN via the Internet or through an MPLS tunnel (the implementation will depend on which service provider you choose and which network equipment is on your side) .
3) The part of services that requires maximum reliability and scalability (external web services, b2b-systems, business analytics and others), you plan to transfer to Microsoft Azure cloud.
4) You want to link these 3 sites into a single network space and be able to place services on any of the three sites.
The whole procedure is divided into the following steps:
1) Creating a virtual network in the cloud "Cloud" through the portal Azure Pack
2) Deploying a new Active Directory domain controller in the Cloud Library (if you already have your own domain that you want to use, you can skip this step)
3) Creating a virtual network in the Microsoft Azure cloud
4) Configuring Site-to-Site VPN between clouds
5) Deployment of a virtual machine in the Microsoft Azure cloud and adding it to the domain serviced by the domain controller in the cloud cloud library, conducting tests.
What is remarkable - all actions are performed by the consumer of cloud services on their own, without any connection of the technical support of the service provider.
We go to the Azure Pack portal as part of the AzuRus service in the cloud “Cloud libraries”. See the following picture:

Click Create - Virtual Network - Custom creation:

Specify the network name. In our case, this is Moscow01 . In principle, the name can be any.

We don’t specify DNS servers yet, as we don’t yet know the IP address of the future domain controller. But if you already know him - you can specify. We put one checkbox - "Network Address Translation" to give access from this virtual network to the Internet via NAT. The subnet of the gateway is set automatically and in most cases it does not need to be changed. At this stage, creating a Site-to-Site VPN is not required.

Configure the address space. In our case, there will be a 192.168.1.0/24 network in Oblakotek, and a 192.168.2.0/24 network in Microsoft Azure.

Network successfully created. The next step is to deploy the virtual machine and make it a domain controller. Click Create - Autonomous Virtual Machine - From Gallery.

For a domain controller, we need a small virtual machine A0 with one virtual processor and 1 gigabyte of RAM.

Let's call our virtual machine DC01 and specify the password for the local administrator. The name of the virtual machine and the computer name in Windows does not match, keep this in mind.

We connect this virtual machine to the Moscow01 network created at the previous stage:

After the virtual machine is created, connect to it via the console:

Next you need to press CTRL + ALT + DEL to unlock the virtual machine console:

Since you most likely will not be able to transfer such a combination of keys inside the VM, remember the hint - you need to press CTRL + ALT + END and the virtual machine will unlock:

We configure the network interface on the future domain controller. The IP address was taken from the one that was issued to the virtual machine via the Azure Pack.

Open the Server Manager, add the Active Directory Domain Services role to the server:

We start the procedure for creating a new domain. Let's call it hybridcloud.local :

After rebooting the server, we go to it already with the help of a domain administrator and check that the controller installation was successful.

The following steps are done from the Microsoft Azure Management Portal. To begin, create a new virtual network. To do this, click "Create a virtual network."

For understanding, let's call it Azure01 . The region of location is Northern Europe, as the closest to Russia, in order to have the best ping.

As the DNS server, we specify DC01 - 192.168.1.2. Formally, the server received the name DC01001, but we will not complicate it and specify the name of the virtual machine. Also put the checkbox "Configure VPN connection type network-to-network."

Specify the name of the remote network. In order not to be confused, we will use the same name that was entered into the Azure Pack - Moscow01. We do not yet know the IP address of the VPN device in the Cloud Library, so we’ll specify any IP address. We also indicate the address space of the remote network, in our case it is 192.168.1.0/24.

Now we will specify the address space of the virtual network in the Microsoft Azure cloud. In our case, this will be 192.168.2.0/24. You also need to click on the Add Gateway Subnet button to allocate a certain number of addresses for the virtual VPN gateway.

After the network is created, go to its settings and on the tab "Monitoring Panel" click Create Gateway - Dynamic Routing. It is necessary to choose dynamic routing, because only in this case the IKEv2 protocol will be used. In the case of static routing, Azure will use the IKEv1 protocol, which the Azure Pack does not support.

Creating a virtual gateway in Microsoft Azure takes enough time, from 15 to 60 minutes. Be patient and wait for the operation to complete.

So, when the virtual gateway in Microsoft Azure is successfully created, you can get down to the most interesting part - setting up a Site-to-Site VPN between the Microsoft Azure cloud and the Cloud Library based on the Azure Pack.
From the Microsoft Azure Management Portal, take the IP address of the gateway in Azure:

We also click on “Key Management” and copy the Shared Key that was generated when the gateway was created:

After that, go to the portal Azure Pack and set up Site-to-Site VPN in the cloud "Cloud libraries". We need to register the DNS server - the IP address of the created domain controller is 192.168.1.2.

After that, go to the tab "VPN type Network-Network" and click "Create VPN":

Specify the name of the connection. In order not to be confused, let's call it like a virtual network in Microsoft Azure - Azure01. We also indicate the IP address of the gateway from Azure and Shared Key, obtained in one of the previous steps from the Microsoft Azure portal.
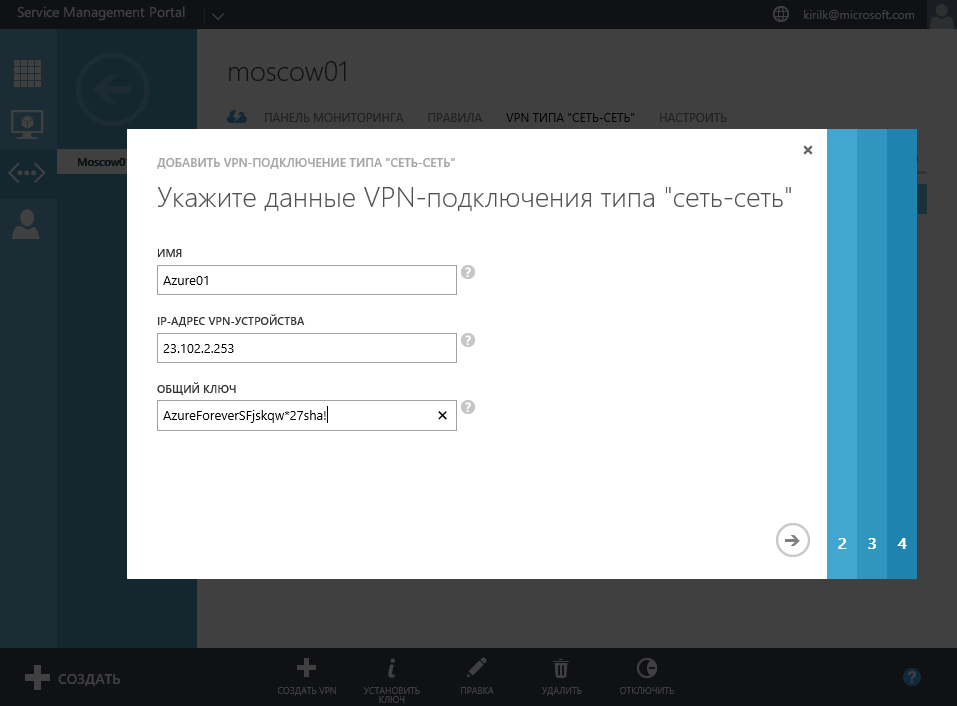
Specify the address space of the remote network. In our case, this is 192.168.2.0/24:

We are waiting for a few minutes while the gateway in the cloud of “Cloud libraries” is created and configured. After the task is completed, we will see the IP address of the gateway in the cloud cloud library, which will need to be copied and then pasted into the Microsoft Azure console. Do not confuse with the external IP address allocated for the virtual network.

Now we return to the Microsoft Azure portal, in the “Local networks” tab we find the Moscow01 network (it was created when we created the Azure01 virtual network) and click “Edit”:

And insert the IP address of the gateway in the cloud "Clouds":

We wait a few minutes (or click on the "Connect" button) and see the following picture, showing that the connection through the Site-to-site VPN tunnel has been successfully established:

That's it, now the virtual network in the cloud "Clouds" is united into a single network with a virtual network in the cloud Microsoft Azure. And all this is done independently, without calls to technical support. We now turn to testing the solution.
Since we want to get not only a single network space, but also a single Active Directory domain, we’ll show that a virtual machine from the Microsoft Azure cloud can be added to a domain running on our domain controller in the Cloud Cloud cloud based on the Azure Pack .
Go to the Microsoft Azure portal and create a virtual machine. For example, let's create a virtual machine with Microsoft SQL Server 2014 Web Edition preinstalled.

Select the “Standard” level to be able to add the created VM to our single network, and also set the username and password for the local server administrator:

Choose a DNS name for the new cloud service and choose our virtual network - Azure01:

After deploying a virtual machine in the Microsoft Azure cloud, log in as a local administrator and check the ping to the domain controller in the Cloud Cloud Library:

We see that there is a ping, and it is very good. A stable 62ms between Moscow and Dublin is enough for many applications.
After that we add a virtual machine to our domain:

Voila, the virtual machine from the Microsoft Azure cloud is connected to a domain running on a controller in the Cloud Cloud cloud. Now let's do a throughput test.
Let's start copying a file weighing 356 megabytes from a virtual machine in the Microsoft Azure cloud to a domain controller in the Cloud Cloud library via SMB. Copying began at a speed of 8 megabytes per second, ended at a speed of more than 17 megabytes per second, that is, the capacity of the Site-to-Site VPN was almost 140 megabits, with a ping of 62ms.

As you can see, on the Microsoft Azure portal, we see counters for traffic passing through the tunnel:

In this scenario, we have connected 2 virtual networks — in the Microsoft Azure cloud and in the Cloud Library cloud — into a single, routable address space. At the same time, consumers can connect to their virtual machines via the Internet to the Cloud Oblakoteka cloud in Moscow, and to the Microsoft Azure data center, the traffic will go through independent independent highways from the Cloud Cloud cloud.
We recommend testing this scenario yourself and try to transfer your existing services to the hybrid cloud. Oblakoteka provides a trial period of 14 days so that you can assess all the possible solutions.
This scenario is a practical application of the concept of Microsoft Cloud OS - a single cloud platform for a private cloud, a Microsoft Azure public cloud and a partner cloud from a local service provider.

AzuRus service from Oblakoteka company will be used as a cloud of the service provider. This solution was implemented as part of the Microsoft Cloud OS Network Russia program with the participation of Microsoft engineers, and uses the Microsoft Azure Pack platform as a cloud management system. Due to this, it seamlessly integrates with the Microsoft Azure cloud.
')
Implementation details below.
Why do you need this?
1) You have a part of the services that you want to transfer to the cloud of the Russian service provider. It can be domain controllers, 1C and other internal services that you traditionally have hosted. You want these services to move painlessly to the cloud of a service provider somewhere near you, so that ping is good, and that the servers are in the territory of the Russian Federation.
2) You connect the service provider cloud and your local network either via Site-to-Site VPN via the Internet or through an MPLS tunnel (the implementation will depend on which service provider you choose and which network equipment is on your side) .
3) The part of services that requires maximum reliability and scalability (external web services, b2b-systems, business analytics and others), you plan to transfer to Microsoft Azure cloud.
4) You want to link these 3 sites into a single network space and be able to place services on any of the three sites.
The whole procedure is divided into the following steps:
1) Creating a virtual network in the cloud "Cloud" through the portal Azure Pack
2) Deploying a new Active Directory domain controller in the Cloud Library (if you already have your own domain that you want to use, you can skip this step)
3) Creating a virtual network in the Microsoft Azure cloud
4) Configuring Site-to-Site VPN between clouds
5) Deployment of a virtual machine in the Microsoft Azure cloud and adding it to the domain serviced by the domain controller in the cloud cloud library, conducting tests.
What is remarkable - all actions are performed by the consumer of cloud services on their own, without any connection of the technical support of the service provider.
Creating a virtual network in the cloud "Clouds"
We go to the Azure Pack portal as part of the AzuRus service in the cloud “Cloud libraries”. See the following picture:

Click Create - Virtual Network - Custom creation:

Specify the network name. In our case, this is Moscow01 . In principle, the name can be any.

We don’t specify DNS servers yet, as we don’t yet know the IP address of the future domain controller. But if you already know him - you can specify. We put one checkbox - "Network Address Translation" to give access from this virtual network to the Internet via NAT. The subnet of the gateway is set automatically and in most cases it does not need to be changed. At this stage, creating a Site-to-Site VPN is not required.

Configure the address space. In our case, there will be a 192.168.1.0/24 network in Oblakotek, and a 192.168.2.0/24 network in Microsoft Azure.

Creating a domain controller in the cloud "Cloud"
Network successfully created. The next step is to deploy the virtual machine and make it a domain controller. Click Create - Autonomous Virtual Machine - From Gallery.

For a domain controller, we need a small virtual machine A0 with one virtual processor and 1 gigabyte of RAM.

Let's call our virtual machine DC01 and specify the password for the local administrator. The name of the virtual machine and the computer name in Windows does not match, keep this in mind.

We connect this virtual machine to the Moscow01 network created at the previous stage:

After the virtual machine is created, connect to it via the console:

Next you need to press CTRL + ALT + DEL to unlock the virtual machine console:

Since you most likely will not be able to transfer such a combination of keys inside the VM, remember the hint - you need to press CTRL + ALT + END and the virtual machine will unlock:

We configure the network interface on the future domain controller. The IP address was taken from the one that was issued to the virtual machine via the Azure Pack.

Open the Server Manager, add the Active Directory Domain Services role to the server:

We start the procedure for creating a new domain. Let's call it hybridcloud.local :

After rebooting the server, we go to it already with the help of a domain administrator and check that the controller installation was successful.

Creating a virtual network in Microsoft Azure
The following steps are done from the Microsoft Azure Management Portal. To begin, create a new virtual network. To do this, click "Create a virtual network."

For understanding, let's call it Azure01 . The region of location is Northern Europe, as the closest to Russia, in order to have the best ping.

As the DNS server, we specify DC01 - 192.168.1.2. Formally, the server received the name DC01001, but we will not complicate it and specify the name of the virtual machine. Also put the checkbox "Configure VPN connection type network-to-network."

Specify the name of the remote network. In order not to be confused, we will use the same name that was entered into the Azure Pack - Moscow01. We do not yet know the IP address of the VPN device in the Cloud Library, so we’ll specify any IP address. We also indicate the address space of the remote network, in our case it is 192.168.1.0/24.

Now we will specify the address space of the virtual network in the Microsoft Azure cloud. In our case, this will be 192.168.2.0/24. You also need to click on the Add Gateway Subnet button to allocate a certain number of addresses for the virtual VPN gateway.

After the network is created, go to its settings and on the tab "Monitoring Panel" click Create Gateway - Dynamic Routing. It is necessary to choose dynamic routing, because only in this case the IKEv2 protocol will be used. In the case of static routing, Azure will use the IKEv1 protocol, which the Azure Pack does not support.

Creating a virtual gateway in Microsoft Azure takes enough time, from 15 to 60 minutes. Be patient and wait for the operation to complete.

Configuring Site-to-Site VPN
So, when the virtual gateway in Microsoft Azure is successfully created, you can get down to the most interesting part - setting up a Site-to-Site VPN between the Microsoft Azure cloud and the Cloud Library based on the Azure Pack.
From the Microsoft Azure Management Portal, take the IP address of the gateway in Azure:

We also click on “Key Management” and copy the Shared Key that was generated when the gateway was created:

After that, go to the portal Azure Pack and set up Site-to-Site VPN in the cloud "Cloud libraries". We need to register the DNS server - the IP address of the created domain controller is 192.168.1.2.

After that, go to the tab "VPN type Network-Network" and click "Create VPN":

Specify the name of the connection. In order not to be confused, let's call it like a virtual network in Microsoft Azure - Azure01. We also indicate the IP address of the gateway from Azure and Shared Key, obtained in one of the previous steps from the Microsoft Azure portal.

Specify the address space of the remote network. In our case, this is 192.168.2.0/24:

We are waiting for a few minutes while the gateway in the cloud of “Cloud libraries” is created and configured. After the task is completed, we will see the IP address of the gateway in the cloud cloud library, which will need to be copied and then pasted into the Microsoft Azure console. Do not confuse with the external IP address allocated for the virtual network.

Now we return to the Microsoft Azure portal, in the “Local networks” tab we find the Moscow01 network (it was created when we created the Azure01 virtual network) and click “Edit”:

And insert the IP address of the gateway in the cloud "Clouds":

We wait a few minutes (or click on the "Connect" button) and see the following picture, showing that the connection through the Site-to-site VPN tunnel has been successfully established:

That's it, now the virtual network in the cloud "Clouds" is united into a single network with a virtual network in the cloud Microsoft Azure. And all this is done independently, without calls to technical support. We now turn to testing the solution.
Deploy VMs in Azure and add to the domain in Cloud Storage, test the solution
Since we want to get not only a single network space, but also a single Active Directory domain, we’ll show that a virtual machine from the Microsoft Azure cloud can be added to a domain running on our domain controller in the Cloud Cloud cloud based on the Azure Pack .
Go to the Microsoft Azure portal and create a virtual machine. For example, let's create a virtual machine with Microsoft SQL Server 2014 Web Edition preinstalled.

Select the “Standard” level to be able to add the created VM to our single network, and also set the username and password for the local server administrator:

Choose a DNS name for the new cloud service and choose our virtual network - Azure01:

After deploying a virtual machine in the Microsoft Azure cloud, log in as a local administrator and check the ping to the domain controller in the Cloud Cloud Library:

We see that there is a ping, and it is very good. A stable 62ms between Moscow and Dublin is enough for many applications.
After that we add a virtual machine to our domain:

Voila, the virtual machine from the Microsoft Azure cloud is connected to a domain running on a controller in the Cloud Cloud cloud. Now let's do a throughput test.
Let's start copying a file weighing 356 megabytes from a virtual machine in the Microsoft Azure cloud to a domain controller in the Cloud Cloud library via SMB. Copying began at a speed of 8 megabytes per second, ended at a speed of more than 17 megabytes per second, that is, the capacity of the Site-to-Site VPN was almost 140 megabits, with a ping of 62ms.

As you can see, on the Microsoft Azure portal, we see counters for traffic passing through the tunnel:

findings
In this scenario, we have connected 2 virtual networks — in the Microsoft Azure cloud and in the Cloud Library cloud — into a single, routable address space. At the same time, consumers can connect to their virtual machines via the Internet to the Cloud Oblakoteka cloud in Moscow, and to the Microsoft Azure data center, the traffic will go through independent independent highways from the Cloud Cloud cloud.
We recommend testing this scenario yourself and try to transfer your existing services to the hybrid cloud. Oblakoteka provides a trial period of 14 days so that you can assess all the possible solutions.
Source: https://habr.com/ru/post/259111/
All Articles