An example of a multi-vendor WLAN access control solution
In a series of articles, we will try to highlight the configuration of various technologies for organizing access to a wireless local area network (WLAN).
The purpose of this article is to demonstrate the possibility of applying open standards to dock equipment from different manufacturers with each other, bringing certain advantages or disadvantages, you decide. We made certain conclusions for ourselves and brought them at the end of the article.
Currently, wireless access to the network is becoming increasingly popular and the number of users who want to connect to the network from their mobile devices is growing.
The number of access device types (endpoint *) is growing. Now it can be a personal computer, laptop, smartphone, tablet, IP phone, printer, other mobile wearable devices.
Authentication methods * may also vary. This can be 802.x authentication, user authentication via the WEB portal, VPN user authentication, MAC address authentication, etc.
Authentication methods (authentication methods *) can also be varied. This can be username / password authentication, certificate authentication, username / password + preshared key authentication for VPN users, username / password authentication + certificate. It can also be transparent portal authentication for intelligent mobile devices, to be able to give the user self-registration to the network, we in turn receive data about his device, also, it can be transparent MAC authentication when the user's MAC address is further associated with user account. Another authentication method exists for devices that cannot independently provide their authentication data.
')
A wide variety of models of wearable devices, operating systems, browsers, and manufacturers that modern security systems must also be able to determine add to the whole variety of methods and methods of authentication.
Access conditions may vary in access time, group of access points, group of access devices, group of IP addresses, group of MAC addresses, group of wireless networks.
Also, modern network access systems provide for checking the user's device before entering the network (posture checking), when the user's endpoint is also checked for compliance with the security policies adopted in the network. Anti-virus software, anti-spyware, Anti-phishing, Firewall software, hard disk encryption, Patch-Management Software, NAC using ACL, VLAN, registry contents, shared folders, password complexity, and other parameters are analyzed before accessing network.
Do not forget also about the requirements of regulators for public access in wireless networks.
In this article, we will consider the option of guest access to WLAN with self-registration of a guest and receiving a password via SMS. Moreover, we will do this in a multi-vendor network. The wireless access controller will be the model of the controller WLC_5508, the access point AIR-CAP3602E-R-K9 and all other functionality will be performed by the infrastructure built on HP networking equipment. The main components of the infrastructure are shown in Figure 1.
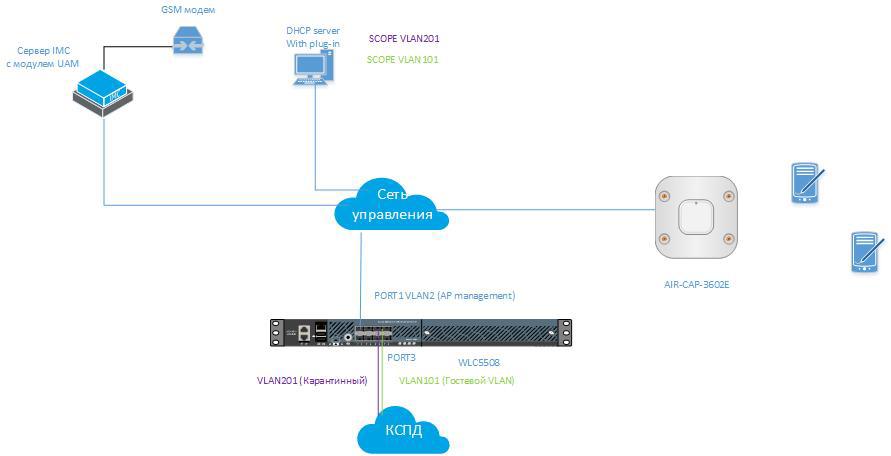
Pic1
Why do I need a wireless access point controller and a wireless access point I will not describe.
The Intelligent Management Center (IMC) server with the User Access Manager (UAM) module installed on it performs the above authentication mechanisms for various types of user devices and browsers.
The types of access devices are divided into two categories: a laptop type and a smartphone type for the ability to display a registration page designed for a small screen of a wearable device.
The user portal and transparent MAC authentication of the subscriber device are selected as the authentication method .
The authentication method is the username / password scheme, where the username is the user's phone number and the password is an arbitrary value of letters and numbers generated by the UAM server and sent to the user by email.
The user account is associated with the user's device. This helps to make the DCHP plug-in installed on the DHCP server. It also helps to profile the device and the guest browser based on the MAC address (device manufacturer), DHCP option (produce, device type, operating system), HTTP User Agent details (browser type).
The access conditions selected are different SSIDs configured on the controller. This helps us to group users according to common features, give them a common registration page, place them in one group or another, set common access policies, place them on certain registration and working VLANs.
The solution provides for two VLANs - one for onboarding (a) or quarantine, the second guest for permanent work.
Posture checking of the user's device is not performed, although it is possible to associate an IMC server with such systems like Citirx XenMobile or MobileIron.
The IMC server also provides several ways to send SMS messages to the user. Messages can be sent using an external GSM modem connected to the IMC server's COM port, messages can be sent as email to the provider's email address, they can also be sent to a third-party carrier system via API.
So, after describing the main components of the access system, let's see the process of setting up a wireless controller to work in such a topology.
In this solution, centralized transmission of authentication traffic (through the controller) and subscriber traffic is applied.
Through the built-in logic management interface of the controller, access points are managed. The logical management interface is “tied” to the physical interface PORT1 and works in VLAN 2, see Figure 2.

Pic2
Interfaces VLAN_100 and VLAN_200 are dynamic user interfaces that transmit traffic in a tagged form through the PORT3 controller to the local network, Fig.3,4

Pic.3

Pic.4
The VLAN_200 interface serves to transfer quarantine traffic to VLAN201, where the initial transparent MAC and portal subscriber authentication are performed. The subscriber enters the VLAN_100 (VLAN101) interface after a successful self-registration of the subscriber on the captive portal. The trigger for switching to VLAN101 is the successful confirmation of the user account by entering the correct subscriber password received via SMS. The UAM server uses the Disconnect Request (RFC3576) message sent to the controller to terminate the user session in VLAN201.
Basic controller settings:
A wireless network is created with ssid corg-guest. Pic.5

Pic.5
In the security settings of the wireless network L2 indicated the use of MAC filtering, Fig.6

Pic.6
Nothing is specified in the security settings of the L3 wireless network, because the portal authentication will be carried out through an external device that accepts VLAN 101, VLAN201.
The AAA Servers tab of the wireless network indicates the AAA servers and enables the Radius Server Overwrite interface mode, Fig.7

Fig.7
Other tabs leave unchanged and reach the Advanced tab of the wireless network, Fig.8

Fig.8
On the Advanced tab, we specify the Allow AAA Override mode to allow VLANs to be assigned to our subscribers through the RFC3576 Dynamic Authorization Extensions to RADIUS mechanism.
In addition, we also need to configure the controller's security settings, namely, make the settings for AAA servers.
On the Security tab -> AAA -> Radius we enter the parameters of our AAA server IMC, Fig.9.10 parameters of the authentication and accounting server.

Fig.9

Pic.10
Check that the access point is connected in the Wireless Access Points section, Fig.11

Figure 11
Wireless Subscriber Authentication Process
The authentication process of a wireless subscriber begins with connecting it from a wireless network with ssid org-guest, fig.12

Fig.12
After the subscriber has received the IP address, a pop-up message appears, inviting you to pass through the portal authentication, Fig.13,14

Fig.13

Fig.14
A window appears prompting you to enter a phone number and password, and when registering a new subscriber, the password will be sent to your mobile phone. The page is customized for a mobile device, because primary device identification occurred using a DHCP agent for the server. Fig.15, 16

Fig.15

Figure 16
There is a countdown for entering the password, during this time the user receives the password by SMS.

Pic.18
After entering the password, the IMC system considers that the user has registered on the network, and switches the user to the desired VLAN by sending the Disconnect-Request message to the wireless access point controller. Also, IMC is configured to automatically transfer the subscriber to the desired web resource. During this procedure, the user sees the page fig.18. After the timeout on the listed actions expires, the user moves to the specified resource, p.19

P.19
Open standards help solve the problem of dependence on a single manufacturer in the network, especially if this dependence has become a problem. The basis of such a solution is a full-fledged control system that can then monitor and partially manage the multi-vendor network.
The purpose of this article is to demonstrate the possibility of applying open standards to dock equipment from different manufacturers with each other, bringing certain advantages or disadvantages, you decide. We made certain conclusions for ourselves and brought them at the end of the article.
Currently, wireless access to the network is becoming increasingly popular and the number of users who want to connect to the network from their mobile devices is growing.
The number of access device types (endpoint *) is growing. Now it can be a personal computer, laptop, smartphone, tablet, IP phone, printer, other mobile wearable devices.
Authentication methods * may also vary. This can be 802.x authentication, user authentication via the WEB portal, VPN user authentication, MAC address authentication, etc.
Authentication methods (authentication methods *) can also be varied. This can be username / password authentication, certificate authentication, username / password + preshared key authentication for VPN users, username / password authentication + certificate. It can also be transparent portal authentication for intelligent mobile devices, to be able to give the user self-registration to the network, we in turn receive data about his device, also, it can be transparent MAC authentication when the user's MAC address is further associated with user account. Another authentication method exists for devices that cannot independently provide their authentication data.
')
A wide variety of models of wearable devices, operating systems, browsers, and manufacturers that modern security systems must also be able to determine add to the whole variety of methods and methods of authentication.
Access conditions may vary in access time, group of access points, group of access devices, group of IP addresses, group of MAC addresses, group of wireless networks.
Also, modern network access systems provide for checking the user's device before entering the network (posture checking), when the user's endpoint is also checked for compliance with the security policies adopted in the network. Anti-virus software, anti-spyware, Anti-phishing, Firewall software, hard disk encryption, Patch-Management Software, NAC using ACL, VLAN, registry contents, shared folders, password complexity, and other parameters are analyzed before accessing network.
Do not forget also about the requirements of regulators for public access in wireless networks.
In this article, we will consider the option of guest access to WLAN with self-registration of a guest and receiving a password via SMS. Moreover, we will do this in a multi-vendor network. The wireless access controller will be the model of the controller WLC_5508, the access point AIR-CAP3602E-R-K9 and all other functionality will be performed by the infrastructure built on HP networking equipment. The main components of the infrastructure are shown in Figure 1.

Pic1
Why do I need a wireless access point controller and a wireless access point I will not describe.
The Intelligent Management Center (IMC) server with the User Access Manager (UAM) module installed on it performs the above authentication mechanisms for various types of user devices and browsers.
The types of access devices are divided into two categories: a laptop type and a smartphone type for the ability to display a registration page designed for a small screen of a wearable device.
The user portal and transparent MAC authentication of the subscriber device are selected as the authentication method .
The authentication method is the username / password scheme, where the username is the user's phone number and the password is an arbitrary value of letters and numbers generated by the UAM server and sent to the user by email.
The user account is associated with the user's device. This helps to make the DCHP plug-in installed on the DHCP server. It also helps to profile the device and the guest browser based on the MAC address (device manufacturer), DHCP option (produce, device type, operating system), HTTP User Agent details (browser type).
The access conditions selected are different SSIDs configured on the controller. This helps us to group users according to common features, give them a common registration page, place them in one group or another, set common access policies, place them on certain registration and working VLANs.
The solution provides for two VLANs - one for onboarding (a) or quarantine, the second guest for permanent work.
Posture checking of the user's device is not performed, although it is possible to associate an IMC server with such systems like Citirx XenMobile or MobileIron.
The IMC server also provides several ways to send SMS messages to the user. Messages can be sent using an external GSM modem connected to the IMC server's COM port, messages can be sent as email to the provider's email address, they can also be sent to a third-party carrier system via API.
So, after describing the main components of the access system, let's see the process of setting up a wireless controller to work in such a topology.
In this solution, centralized transmission of authentication traffic (through the controller) and subscriber traffic is applied.
Through the built-in logic management interface of the controller, access points are managed. The logical management interface is “tied” to the physical interface PORT1 and works in VLAN 2, see Figure 2.

Pic2
Interfaces VLAN_100 and VLAN_200 are dynamic user interfaces that transmit traffic in a tagged form through the PORT3 controller to the local network, Fig.3,4

Pic.3

Pic.4
The VLAN_200 interface serves to transfer quarantine traffic to VLAN201, where the initial transparent MAC and portal subscriber authentication are performed. The subscriber enters the VLAN_100 (VLAN101) interface after a successful self-registration of the subscriber on the captive portal. The trigger for switching to VLAN101 is the successful confirmation of the user account by entering the correct subscriber password received via SMS. The UAM server uses the Disconnect Request (RFC3576) message sent to the controller to terminate the user session in VLAN201.
Basic controller settings:
A wireless network is created with ssid corg-guest. Pic.5

Pic.5
In the security settings of the wireless network L2 indicated the use of MAC filtering, Fig.6

Pic.6
Nothing is specified in the security settings of the L3 wireless network, because the portal authentication will be carried out through an external device that accepts VLAN 101, VLAN201.
The AAA Servers tab of the wireless network indicates the AAA servers and enables the Radius Server Overwrite interface mode, Fig.7

Fig.7
Other tabs leave unchanged and reach the Advanced tab of the wireless network, Fig.8

Fig.8
On the Advanced tab, we specify the Allow AAA Override mode to allow VLANs to be assigned to our subscribers through the RFC3576 Dynamic Authorization Extensions to RADIUS mechanism.
In addition, we also need to configure the controller's security settings, namely, make the settings for AAA servers.
On the Security tab -> AAA -> Radius we enter the parameters of our AAA server IMC, Fig.9.10 parameters of the authentication and accounting server.

Fig.9

Pic.10
Check that the access point is connected in the Wireless Access Points section, Fig.11

Figure 11
Wireless Subscriber Authentication Process
The authentication process of a wireless subscriber begins with connecting it from a wireless network with ssid org-guest, fig.12

Fig.12
After the subscriber has received the IP address, a pop-up message appears, inviting you to pass through the portal authentication, Fig.13,14

Fig.13

Fig.14
A window appears prompting you to enter a phone number and password, and when registering a new subscriber, the password will be sent to your mobile phone. The page is customized for a mobile device, because primary device identification occurred using a DHCP agent for the server. Fig.15, 16

Fig.15

Figure 16
There is a countdown for entering the password, during this time the user receives the password by SMS.

Pic.18
After entering the password, the IMC system considers that the user has registered on the network, and switches the user to the desired VLAN by sending the Disconnect-Request message to the wireless access point controller. Also, IMC is configured to automatically transfer the subscriber to the desired web resource. During this procedure, the user sees the page fig.18. After the timeout on the listed actions expires, the user moves to the specified resource, p.19

P.19
Open standards help solve the problem of dependence on a single manufacturer in the network, especially if this dependence has become a problem. The basis of such a solution is a full-fledged control system that can then monitor and partially manage the multi-vendor network.
Source: https://habr.com/ru/post/258941/
All Articles