First day of PHDays V: from SMS interception to satellite hacking
On the very first day of the Positive Hack Days forum, launched on May 26, cybersecurity experts from around the world demonstrated various techniques of hacking ATMs, online banking, networks of mobile operators, energy management systems, transport and industrial enterprises. More than 50 reports were heard at the World Trade Center, master classes and round tables were held, and dozens of hacker contests were held. The most interesting was broadcast on the forum site in several streams.
Damage from cyber attacks is often measured in billions of dollars, but the real cost of hacking is usually small. According to the Positive Technologies research center, anyone who spends less than $ 10,000 on equipment can remotely access someone else's SIM card — and thus subscriber traffic, SMS, calls and location data. And for such attacks, 20% of the Sims are vulnerable! Confidential subscriber information can be obtained by attacking the operator’s equipment. The price of a question when preparing an attack on a GSM network cell is about $ 1000, and hacking an operator’s base station requires only a PC and access to an SS7 network.
')
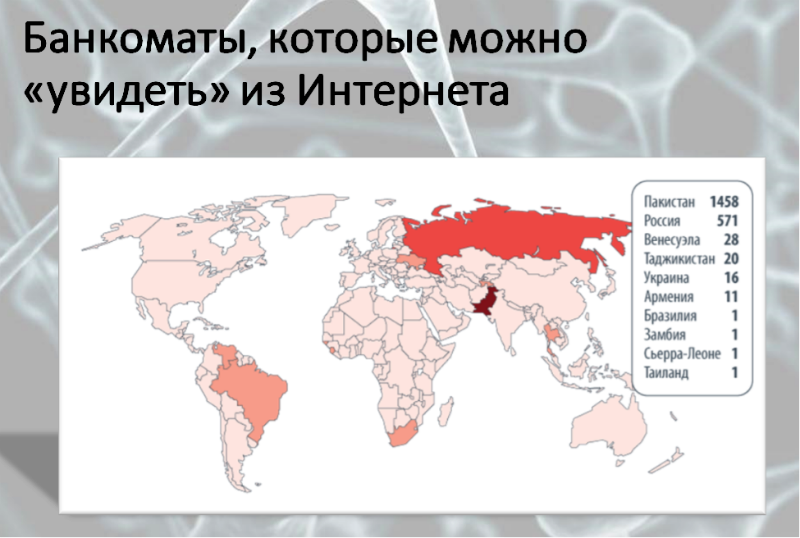
The banking industry is not far behind telecommunications. More than 10 million rubles can be in one ATM, and $ 60 is enough for intelligent ATM hacking if you use a Raspberry Pi or special equipment is not required at all. Last year, Russia ranked second in the world (after Pakistan) in the number of ATMs that can be detected using special search engines and remotely reprogrammed using insecure protocols and multiple vulnerabilities in Windows XP. With electronic money, the situation is no better: 70% of mobile apps for Android and 50% for iOS in 2014 contained vulnerabilities sufficient to gain access to the account.
Hazard for the user may be harmless at first sight devices, such as USB wireless modems for Internet access. If manufacturers of mobile OSs quickly enough eliminate vulnerabilities, then developers of firmware for modems have recently paid minimum attention to security: 27 out of 30 firmware investigated by Positive Technologies experts contained critically dangerous vulnerabilities. In his report, "Butkit via SMS: 4G network security assessment," Timur Yunusov showed how easily an attacker can automate the identification and infection of 4G modems to intercept traffic, manipulate SMS, manage money on the account and penetrate the computer to which the modem is connected.

The philosophical concept of the fifth PHDays included elements of the cosmological theory, but the practical aspects also interested the organizers, therefore for the first time the section “Radio Amateur Cosmic Communication” was held at the forum. The speakers discussed security issues at orbital stations in terms of information security; in particular, one of the versions that links the accident at the Phobos-Grunt interplanetary station with an external impact. According to radio amateur Dmitry Pashkov, it is a real task to drown out any signals between the control center and the spacecraft, and all the necessary equipment can be purchased at the radio market, with the exception of the antenna: you will have to do it yourself. A specialist from Mordovian Ruzayevka told how he got a photo of a solar eclipse from the Roscosmos satellite "Meteor-M2" using self-made equipment, and also used the signals of meteorological satellites to obtain an operational weather forecast before fishing.
The necessary measures to combat vulnerabilities - including to protect national interests - were discussed in the framework of the “state” section itself “We reboot, and we are growing stronger. What is it like to be Russia in an unfriendly cyber world? ”
Dmitry Finogenov (8th Department of the FSB), Alexander Radovitsky (MFA), Alexander Baranov (Tax Service), State Duma deputies Vadim Dengin, Andrey Tumanov and Ilya Kostunov took part in the discussion. Alexey Andreev (Positive Technologies) and Alexey Lukatsky (Cisco) spoke on the part of the expert community.
Representatives of state bodies promised that by the end of 2015 a new Russian concept of information security will be published. Vadim Dengin called on Russian Internet users, who are already over 70 million, to be responsible for their words (including in court), and noted that the safety of citizens, in particular the protection of personal data, is a priority for the state, therefore Law No. 242- The Federal Law on the transfer of data centers to Russia will not be postponed and “foreign business as a whole agrees with the law”. A colleague of Vadim, Ilya Kostunov, recently discovered that Google Analytics was installed in all Russian authorities, in connection with which he sent requests to the prosecutor's office and the Ministry of Economic Development. Ilya also noted that Russia had the opportunity to launch its payment system back in 2000, and immediately with chip cards.

When protecting data in large companies with an extensive infrastructure, they often say “the chain is as strong as its weak link”. Natalya Kukanova from Yandex in the report Cat in the Bag: Security at Mergers and Acquisitions noted that when acquiring third-party projects, Yandex deducts the cost of removing vulnerabilities from the profit from the transaction.
Growth problems can not only be a large business. PHDays traditionally holds events to support and promote new ideas and solutions in the field of information security. Almaz Capital Investment Fund, which was represented by managing partner Alexander Galitsky and general partner Jeffrey Baer, organized an open competition at PHDays among start-up projects in the field of cybersecurity. Jeffrey Baer told about 18 participants who fought for 1.5 million rubles, and gave some tips to the creators of new companies.

Photo: @ AlmazCapital
PHDays V organizers held a discussion on the creation of an international community of “white hackers”, gathering at one table the organizers of leading hacker conferences - Canadian CanSecWest, Korean Vangelis and Power of Community, Brazilian H2HC, Japanese CodeBlue, German Chaos Communication Congress and Russian ZeroNights and PHDays.
The evening of the first day culminated in the reading of the best stories, which were selected from 200 works sent to the Hacked Future competition . The final places were distributed by one of the founders of the genre Bruce Sterling, and they read about “cybernetic trojans, devourers and a controller in the woman’s head” of the radio project “Models for assembly”.
Winners of the contest "Hacked Future":
The details of the second day of Positive Hack Days V can be viewed live and on Twitter using the hashtag #phdays .
Damage from cyber attacks is often measured in billions of dollars, but the real cost of hacking is usually small. According to the Positive Technologies research center, anyone who spends less than $ 10,000 on equipment can remotely access someone else's SIM card — and thus subscriber traffic, SMS, calls and location data. And for such attacks, 20% of the Sims are vulnerable! Confidential subscriber information can be obtained by attacking the operator’s equipment. The price of a question when preparing an attack on a GSM network cell is about $ 1000, and hacking an operator’s base station requires only a PC and access to an SS7 network.

')
The banking industry is not far behind telecommunications. More than 10 million rubles can be in one ATM, and $ 60 is enough for intelligent ATM hacking if you use a Raspberry Pi or special equipment is not required at all. Last year, Russia ranked second in the world (after Pakistan) in the number of ATMs that can be detected using special search engines and remotely reprogrammed using insecure protocols and multiple vulnerabilities in Windows XP. With electronic money, the situation is no better: 70% of mobile apps for Android and 50% for iOS in 2014 contained vulnerabilities sufficient to gain access to the account.
Hazard for the user may be harmless at first sight devices, such as USB wireless modems for Internet access. If manufacturers of mobile OSs quickly enough eliminate vulnerabilities, then developers of firmware for modems have recently paid minimum attention to security: 27 out of 30 firmware investigated by Positive Technologies experts contained critically dangerous vulnerabilities. In his report, "Butkit via SMS: 4G network security assessment," Timur Yunusov showed how easily an attacker can automate the identification and infection of 4G modems to intercept traffic, manipulate SMS, manage money on the account and penetrate the computer to which the modem is connected.

The philosophical concept of the fifth PHDays included elements of the cosmological theory, but the practical aspects also interested the organizers, therefore for the first time the section “Radio Amateur Cosmic Communication” was held at the forum. The speakers discussed security issues at orbital stations in terms of information security; in particular, one of the versions that links the accident at the Phobos-Grunt interplanetary station with an external impact. According to radio amateur Dmitry Pashkov, it is a real task to drown out any signals between the control center and the spacecraft, and all the necessary equipment can be purchased at the radio market, with the exception of the antenna: you will have to do it yourself. A specialist from Mordovian Ruzayevka told how he got a photo of a solar eclipse from the Roscosmos satellite "Meteor-M2" using self-made equipment, and also used the signals of meteorological satellites to obtain an operational weather forecast before fishing.
How to protect
The necessary measures to combat vulnerabilities - including to protect national interests - were discussed in the framework of the “state” section itself “We reboot, and we are growing stronger. What is it like to be Russia in an unfriendly cyber world? ”
Dmitry Finogenov (8th Department of the FSB), Alexander Radovitsky (MFA), Alexander Baranov (Tax Service), State Duma deputies Vadim Dengin, Andrey Tumanov and Ilya Kostunov took part in the discussion. Alexey Andreev (Positive Technologies) and Alexey Lukatsky (Cisco) spoke on the part of the expert community.
Representatives of state bodies promised that by the end of 2015 a new Russian concept of information security will be published. Vadim Dengin called on Russian Internet users, who are already over 70 million, to be responsible for their words (including in court), and noted that the safety of citizens, in particular the protection of personal data, is a priority for the state, therefore Law No. 242- The Federal Law on the transfer of data centers to Russia will not be postponed and “foreign business as a whole agrees with the law”. A colleague of Vadim, Ilya Kostunov, recently discovered that Google Analytics was installed in all Russian authorities, in connection with which he sent requests to the prosecutor's office and the Ministry of Economic Development. Ilya also noted that Russia had the opportunity to launch its payment system back in 2000, and immediately with chip cards.

When protecting data in large companies with an extensive infrastructure, they often say “the chain is as strong as its weak link”. Natalya Kukanova from Yandex in the report Cat in the Bag: Security at Mergers and Acquisitions noted that when acquiring third-party projects, Yandex deducts the cost of removing vulnerabilities from the profit from the transaction.
Growth problems can not only be a large business. PHDays traditionally holds events to support and promote new ideas and solutions in the field of information security. Almaz Capital Investment Fund, which was represented by managing partner Alexander Galitsky and general partner Jeffrey Baer, organized an open competition at PHDays among start-up projects in the field of cybersecurity. Jeffrey Baer told about 18 participants who fought for 1.5 million rubles, and gave some tips to the creators of new companies.

Photo: @ AlmazCapital
PHDays V organizers held a discussion on the creation of an international community of “white hackers”, gathering at one table the organizers of leading hacker conferences - Canadian CanSecWest, Korean Vangelis and Power of Community, Brazilian H2HC, Japanese CodeBlue, German Chaos Communication Congress and Russian ZeroNights and PHDays.
The evening of the first day culminated in the reading of the best stories, which were selected from 200 works sent to the Hacked Future competition . The final places were distributed by one of the founders of the genre Bruce Sterling, and they read about “cybernetic trojans, devourers and a controller in the woman’s head” of the radio project “Models for assembly”.
Winners of the contest "Hacked Future":
- I place - Pavel Gubarev, the story "Uncle Zhenya",
- II place - Alexander Matyukhin, the story "Prestige",
- III place - Dmitry Bogutsky, the story "Throwing the dice",
- The fourth place was shared by Mikhail Savelichev with the story “Sixty Deaths of the Axial Maria”, Juliana Lebedinskaya with the Story “Shadow and Eliza” and Rumit Kin (Nikolai Murzin and Timur Denisov) with the story “Numb Man”.
The details of the second day of Positive Hack Days V can be viewed live and on Twitter using the hashtag #phdays .
Source: https://habr.com/ru/post/258921/
All Articles