Fake Minecraft apps on Google Play downloaded hundreds of thousands of times
ESET specialists discovered more than 30 fake applications (so-called scareware) that simulate either the Minecraft game itself or special cracker applications for this game. These applications have been downloaded by Android users over 600 thousand times. The latest security innovations of this application store have significantly complicated the download mechanism for malicious and fake applications. At the same time, our research has shown that Google’s efforts are not enough.

Attackers use these applications to make money on clicks from special intimidating banners. Such banners notify the user that his device is "infected with a dangerous virus." After the user follows the link, a paid SMS subscription will be activated for him, which costs 4.80 euros per week.
All the fake applications we found had similar behavior, the differences between them consisted only in the names of the applications themselves and in the form of their icons. At the same time, they were uploaded to Google Play from different accounts, but we assume that the same person or group of people was behind their development. The first applications were uploaded to the store in August 2014. Since their publication, they received unsatisfactory user ratings and the same comments to them. Nevertheless, according to statistics recorded by Google Play, some of them were installed from 100 thousand to 500 thousand times, and the total number of installations of all 33 applications varies from 660 thousand to 2 mil. 800 thousand
')
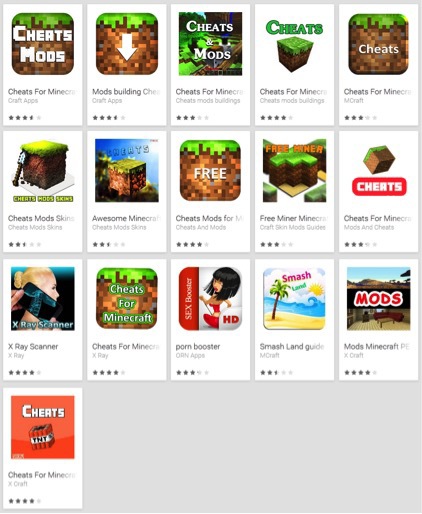
Fig. Fake Minecraft apps.
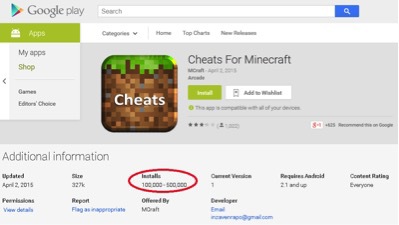
Fig. One of these applications. It can be seen that it was downloaded from 100 thousand to 500 thousand times.
ESET AV products detect various modifications of these applications like Android / FakeApp.AL . After our complaint to Google, these applications were removed from the store.
After installing applications in Android, they all look identical and have similar behavior. The icons of the installed applications correspond to their Minecraft counterparts. They are shown in the picture below.

Fig. Fake application icons.
After launching one of these applications, it can be seen that the start screen of the application consists almost entirely of banner ads. The application itself has three buttons: Start, Options, Exit. No code snippets were found in the code for this application to handle the actions of the buttons. The text language of advertising banners is adapted to the user's geographical location. This practice is often used in another form of malware - extortionists (ransomware).
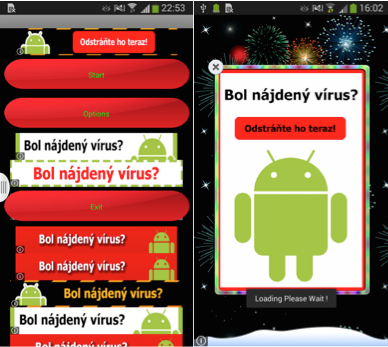
Fig. Screen one of the applications.
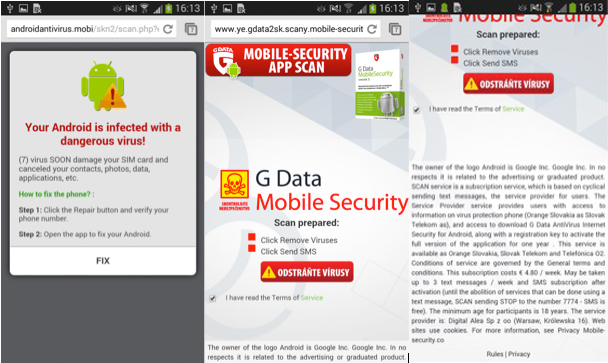
Any attempt by the user to interact with the application by clicking the above Start, Options, Exit buttons or clicking on the banner will result in the same response from the application: a pop-up window display that notifies the user of the infection of his device with malware. In addition, the program also suggests that this malware be removed. When clicking on a link from a pop-up window, the user is shown another window with information about the infection of the device. One of these web pages is disguised as a legitimate site of the antivirus vendor, see the picture below.
At the end of its work, the malicious application generates a special SMS message for its further sending. Since the application itself is denied the right to send SMS messages, the attackers disguise this operation. The user is prompted to activate antivirus protection by sending an SMS. After that, it will automatically be subscribed to the paid newsletter.
Earlier we wrote about other malware for Android - Android / Simplocker.A . He is an extortionist, encrypting files on the device. Despite the fact that the fake Minecraft applications described by us are less dangerous for users, such an impressive amount of downloads tells us that these applications are an effective means of earning for intruders.
A special protective Google service called Bouncer has been used in the Play app store since 2011 for all applications downloaded there. This reduced the number of malicious applications that could be placed there by 40%. In March of this year, Google announced that all applications downloaded to Play will be checked more carefully, and a human resource will be involved for this.
Android device users should avoid installing unwanted or malicious applications. You should also refrain from downloading applications from third-party sources and use anti-virus software in your work (for example, ESET Mobile Security ). Attention should be paid to the reviews of other users about this or that application, as well as the rights required by the application during installation.

Attackers use these applications to make money on clicks from special intimidating banners. Such banners notify the user that his device is "infected with a dangerous virus." After the user follows the link, a paid SMS subscription will be activated for him, which costs 4.80 euros per week.
All the fake applications we found had similar behavior, the differences between them consisted only in the names of the applications themselves and in the form of their icons. At the same time, they were uploaded to Google Play from different accounts, but we assume that the same person or group of people was behind their development. The first applications were uploaded to the store in August 2014. Since their publication, they received unsatisfactory user ratings and the same comments to them. Nevertheless, according to statistics recorded by Google Play, some of them were installed from 100 thousand to 500 thousand times, and the total number of installations of all 33 applications varies from 660 thousand to 2 mil. 800 thousand
')

Fig. Fake Minecraft apps.

Fig. One of these applications. It can be seen that it was downloaded from 100 thousand to 500 thousand times.
ESET AV products detect various modifications of these applications like Android / FakeApp.AL . After our complaint to Google, these applications were removed from the store.
After installing applications in Android, they all look identical and have similar behavior. The icons of the installed applications correspond to their Minecraft counterparts. They are shown in the picture below.

Fig. Fake application icons.
After launching one of these applications, it can be seen that the start screen of the application consists almost entirely of banner ads. The application itself has three buttons: Start, Options, Exit. No code snippets were found in the code for this application to handle the actions of the buttons. The text language of advertising banners is adapted to the user's geographical location. This practice is often used in another form of malware - extortionists (ransomware).

Fig. Screen one of the applications.
Any attempt by the user to interact with the application by clicking the above Start, Options, Exit buttons or clicking on the banner will result in the same response from the application: a pop-up window display that notifies the user of the infection of his device with malware. In addition, the program also suggests that this malware be removed. When clicking on a link from a pop-up window, the user is shown another window with information about the infection of the device. One of these web pages is disguised as a legitimate site of the antivirus vendor, see the picture below.

At the end of its work, the malicious application generates a special SMS message for its further sending. Since the application itself is denied the right to send SMS messages, the attackers disguise this operation. The user is prompted to activate antivirus protection by sending an SMS. After that, it will automatically be subscribed to the paid newsletter.
Earlier we wrote about other malware for Android - Android / Simplocker.A . He is an extortionist, encrypting files on the device. Despite the fact that the fake Minecraft applications described by us are less dangerous for users, such an impressive amount of downloads tells us that these applications are an effective means of earning for intruders.
A special protective Google service called Bouncer has been used in the Play app store since 2011 for all applications downloaded there. This reduced the number of malicious applications that could be placed there by 40%. In March of this year, Google announced that all applications downloaded to Play will be checked more carefully, and a human resource will be involved for this.
Android device users should avoid installing unwanted or malicious applications. You should also refrain from downloading applications from third-party sources and use anti-virus software in your work (for example, ESET Mobile Security ). Attention should be paid to the reviews of other users about this or that application, as well as the rights required by the application during installation.
Source: https://habr.com/ru/post/258853/
All Articles