PENTESTIT ethical hacking and penetration testing courses

If you are interested in practical information security and you want to get relevant knowledge "here and now", we suggest you to get acquainted with "Corporate Laboratories" - the Pentestit program of professional training in the field of information security.
Updating the course content with each set, we try to transfer the most relevant material in the field of practical safety. In addition to the strongest practical training, the training program “Corporate Laboratories” includes interesting courses, webinars, comparable in content to the material of professional information security conferences. In addition, Corporate Laboratories significantly broaden their horizons and awareness in the field of information security.
Training in "Corporate laboratories" allows you to:
- study specialized distributions and penetration testing tools;
- search and exploit vulnerabilities of varying complexity in the corporate environment;
- understand which vulnerability is a real threat and which is not;
- configure and maintain information security systems.
The uniqueness of the “Corporate Laboratories” lies in the symbiosis of the training format (fully distant, not requiring separation from work and study), the quality of the material, and the specialized sites where training is conducted. The program is divided into two components: theoretical training (webinar courses held on weekends from 13.00 to 18 hours Moscow time) and practical (specialized laboratories available on weekdays, during free time for the student). Practical training is a key element and makes up about 80% of the total training program.
')
Who is the course for?
- for system administrators: obtaining knowledge that allows you to safely configure the system;
- for information security specialists: studying the tools and psychology of the attacker, developing a more effective information security policy;
- for pentesters: mastering new tools and penetration testing methods, confirming qualifications;
- for all employees: raising general information security awareness;
Specialized sites
For comfortable learning, taking into account all the specifics and peculiarities of work, Pentestit employees created a unified training system, including subsystems:
Personal Area
The learning process begins with filling out a profile in the "Personal Account" and acquaintance with the system interface, including:
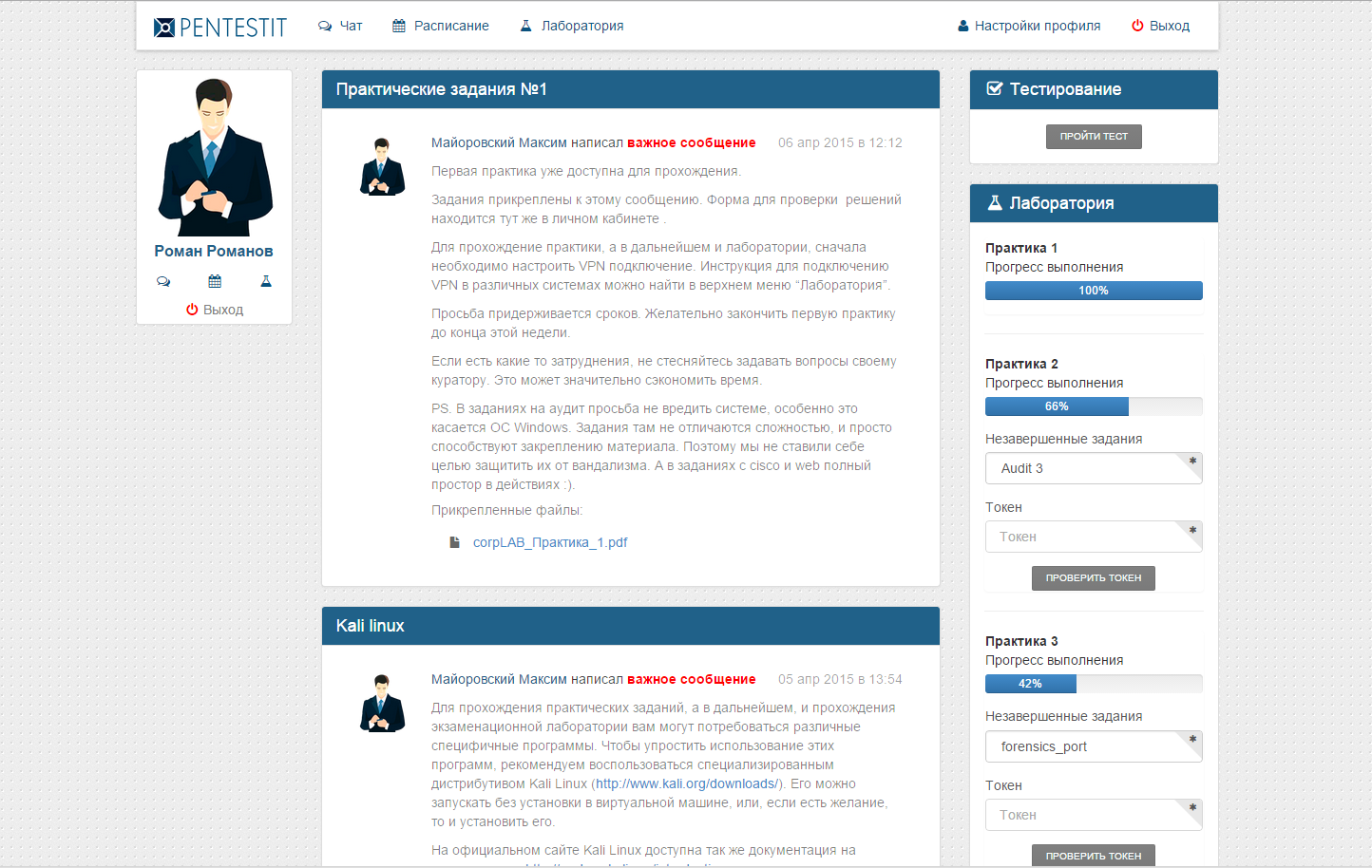
- Timetable of classes;
- information for connecting to laboratories;
- entry forms of tokens obtained in the laboratory;
- testing module for fixing the theoretical material;
- a bulletin board on which the group curator places information on training, as well as methodological material;
- as well as chat and contacts to interact with the curator.

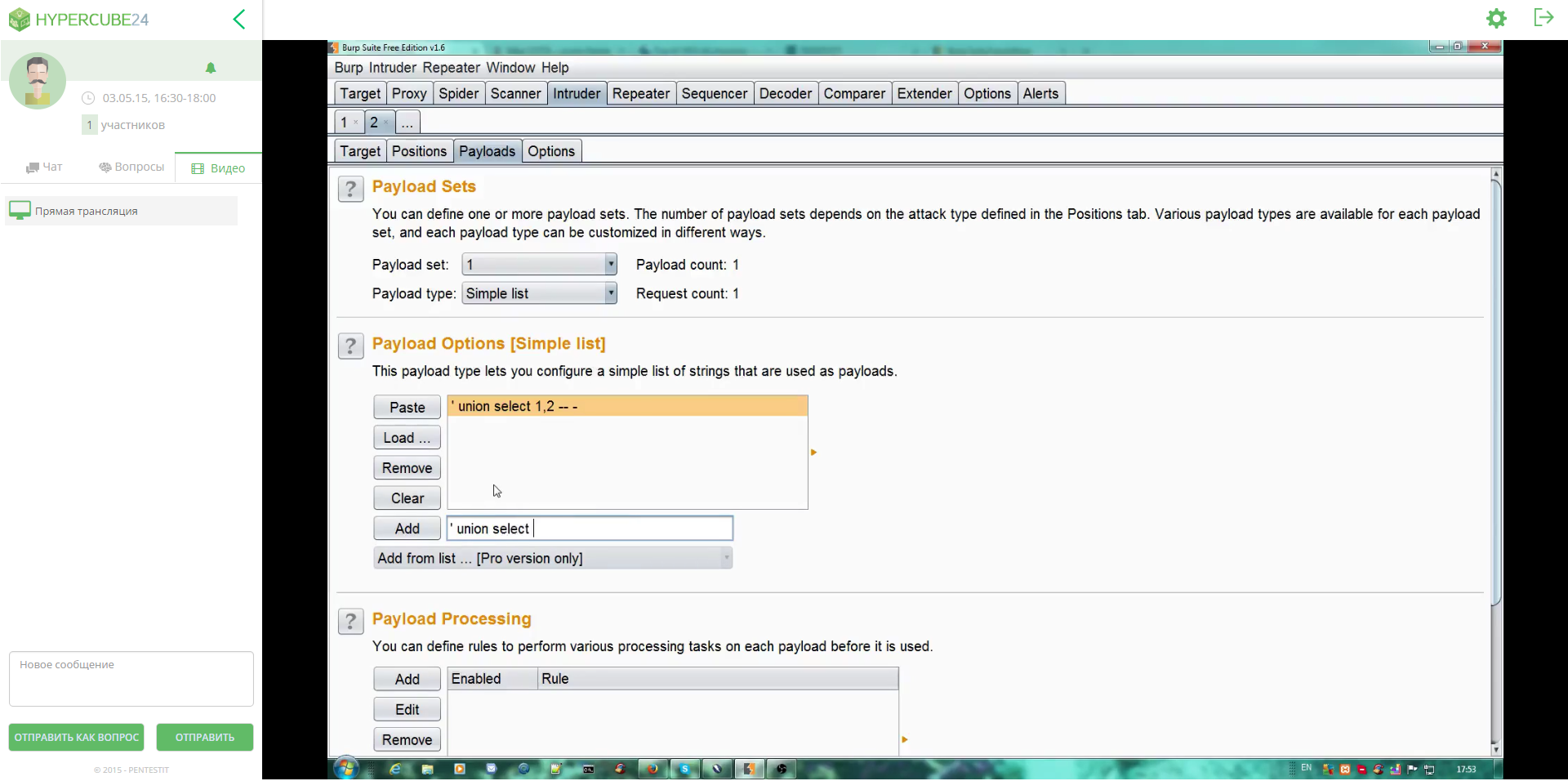
Platform for webinar behavior
Given the specifics of the training programs, Pentestit instructors often demonstrate the work of various utilities and software requiring high image quality. The Hypercube24 webinar site developed by us allows you to broadcast video in high quality at a high screen resolution, so listeners can comfortably study the material, and the presenter does not have to reduce the screen resolution. In addition, the platform has a user-friendly interface that allows you to hide the chat, ask questions, expand the video broadcast on the full screen, as well as promptly communicate with the moderator.

Penest laboratories
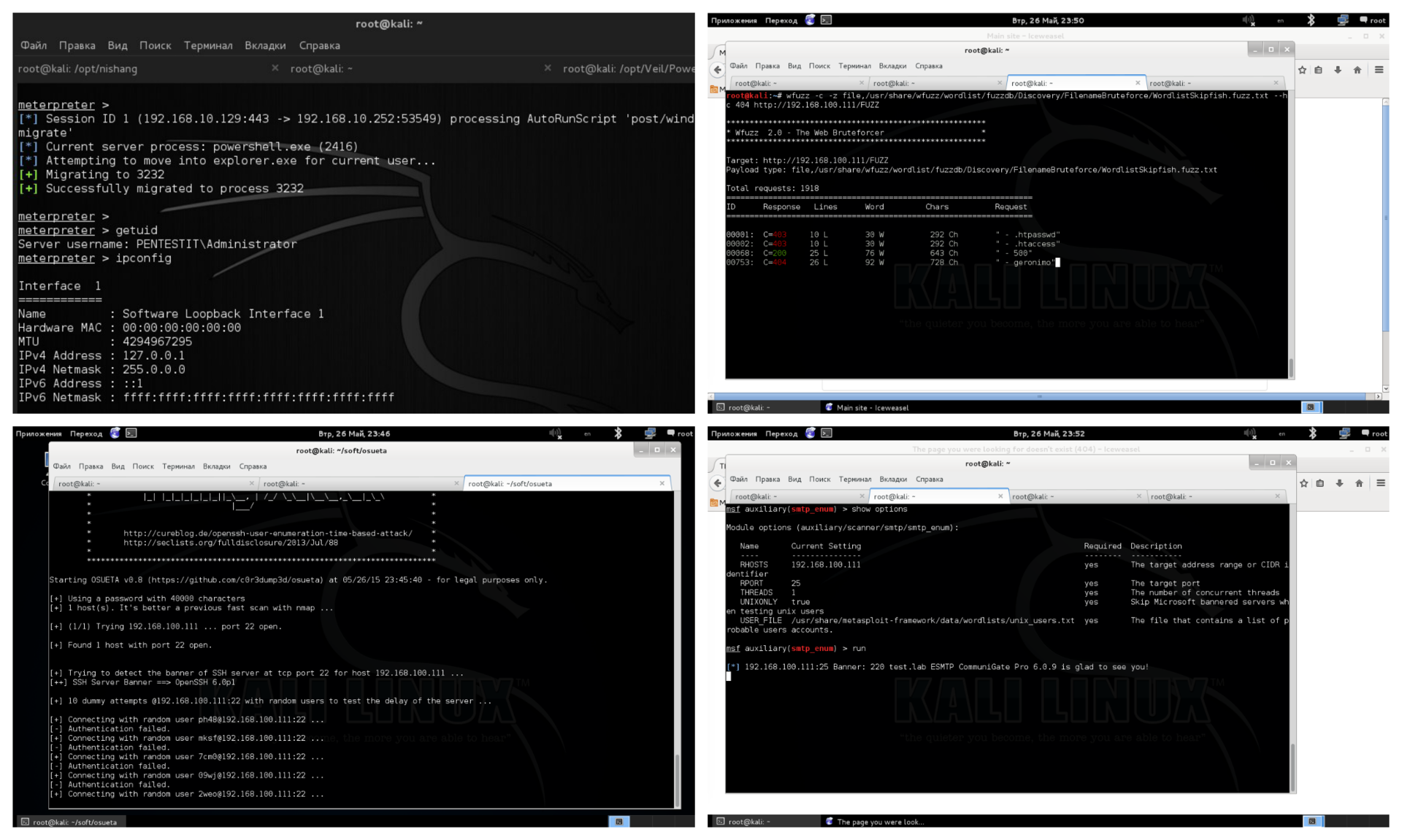
The main feature of the course is intensive practical work in the laboratory. In order for the knowledge gained to be effective, the practice must be conducted in conditions as close to real as possible, which is the main advantage of the Corporate Laboratories training programs. All laboratories are developed on the basis of corporate networks of real companies . Thus, having learned how to search for and exploit vulnerabilities in laboratories, a specialist undergoing training will probably be able to cope with a similar task in other corporate networks. In addition, by performing pentest in the laboratory, the specialist begins to understand which vulnerability is a real threat and which is not, and on the basis of this, he learns to implement the most effective protection mechanisms.

Learning process
The day before the start of the course, a letter will arrive with access to the “Personal Account” in order to fill out a profile in advance, familiarize yourself with the interface, get teaching material, and also get to know the curator, who will be available throughout the entire training process, from 10 to 22 of time.
After the acquaintance, the first series of webinar courses begins, which are held on weekends and constitute 20% of the total training program. At the webinar courses, experienced experts from Pentestit share their accumulated knowledge and experience, answer listeners' questions, demonstrate the most modern methods and tools for penetration testing, and introduce the offender's psychology.
Demo recordings of webinar courses "Corporate Laboratories"
On weekdays, the obtained skills are consolidated in specialized laboratories. To begin with, trained professionals are encouraged to start by trying to perform a laboratory on the basis of information obtained through webinars. As a rule, it seemed clear at webinars, in practice it requires quite a lot of effort and commitment. The curator tries to help understand the vector of attack, and only as a last resort explains the logic of the assignment. Of course, such an approach increases the time for searching and exploiting vulnerabilities, but it helps to acquire skills in full, to understand the process of the attacker's actions, by developing unconventional thinking. Each vulnerable laboratory node contains a token available after exploiting the vulnerability. Having received the token, the specialist enters it in the form of delivery of the token in the "Personal Account". After the whole cycle of webinars is completed, and the first laboratory is passed, the final (examination) laboratory, designed on the basis of networks of real companies, becomes available. To complete the training, it is necessary to demonstrate the acquired skills in the combat laboratory, as well as to pass a theoretical exam, also available in the personal account. Upon termination of training to the specialist the company certificate is issued.

Course modularity
The training program includes two modules: “Profi” and “Expert”. The modularity of the program lies in the fact that, for example, having completed training in the “Profi” module, you can visit the “Expert” module, paying the difference between the modules. This approach allows everyone to continue learning without re-passing the material.
The Profi module provides professional training not only for technical specialists, but also for ordinary employees, including advanced methods of “attack” and “defense”. This module covers most of the methods and toolkit of the Pentester and the information security specialist.
Additional Information
The Profi module provides in-depth theoretical and practical training due to the significant amount of material under consideration (methods, techniques, and attack vector), as well as the number and complexity of practical tasks.
In addition, the Profi module is perfect for both novice specialists with minimal knowledge of information security and experienced professionals who want to upgrade their skills in practical information security.
Course duration: 3-4 weeks, cost: 78,000 rubles.
In addition, the Profi module is perfect for both novice specialists with minimal knowledge of information security and experienced professionals who want to upgrade their skills in practical information security.
- Legislation in the field of information security in Russia and abroad;
- Penetration testing (methods; views; toolkit);
- Network security (scanning; configuration errors; exploitation; post-exploitation);
- Web security (the nature of SQL injection; XSS basics; an overview of tools for exploiting web vulnerabilities);
- Building effective information security systems (introductory information; review of existing IDS);
- Intercepter-NG;
- Enhanced network security (MITM class techniques using modern tools; advanced methods for finding vulnerabilities in network infrastructure);
- Advanced Workshop on SQLi (MySQL DBMS; MSSQL DBMS; PostgreSQL DBMS);
- Advanced Workshop on XSS (Demonstration of the most current varieties of XSS);
- Building effective information security systems (setting up and demonstrating specialized utilities and methods);
- Master class from guests of Corporate Laboratories (presentation of a report by an invited expert in the field of information security. Opportunity to talk and ask questions to the speaker);
- Strengthening the skills acquired in practice: CTF-tasks and an examination laboratory. Performance of a pentest of a corporate network.
Course duration: 3-4 weeks, cost: 78,000 rubles.
The entire “hardcore” program, in its composition comparable to the material of relevant conferences on practical security, is concentrated in the “Expert” module. In addition to the material on the post-operation of systems, the module contains material on the investigation of cybercrime and countering cybercriminals.
Additional Information
Expert level of training, including the material of the module "Profi" and being its continuation.
The module "Expert" is a unique occupation, its level is identical to the material that can be heard only in professional forums on practical safety. In addition, “Expert” includes training in computer forensics and countering violations, allowing not only to conduct an internal investigation of computer crimes, but also to correctly assemble the evidence base for transmission to law enforcement agencies.
The “Expert” module, which includes Pros, is designed for both novice information security professionals and system administrators, allowing them to gradually consolidate their computer security skills, as well as for professionals, to gain expert skills about modern threats and ways to counter them in information security.
Course duration: 4-5 weeks, cost: 130,000 rubles.
The module "Expert" is a unique occupation, its level is identical to the material that can be heard only in professional forums on practical safety. In addition, “Expert” includes training in computer forensics and countering violations, allowing not only to conduct an internal investigation of computer crimes, but also to correctly assemble the evidence base for transmission to law enforcement agencies.
The “Expert” module, which includes Pros, is designed for both novice information security professionals and system administrators, allowing them to gradually consolidate their computer security skills, as well as for professionals, to gain expert skills about modern threats and ways to counter them in information security.
- Legislation in the field of information security in Russia and abroad;
- Penetration testing (methods; views; toolkit);
- Network security (scanning; configuration errors; exploitation; post-exploitation);
- Web security (the nature of SQL injection; XSS basics; an overview of tools for exploiting web vulnerabilities);
- Building effective information security systems (introductory information; review of existing IDS);
- Intercepter-NG;
- Enhanced network security (MITM class techniques using modern tools; advanced methods for finding vulnerabilities in network infrastructure);
- Advanced Workshop on SQLi (MySQL DBMS; MSSQL DBMS; PostgreSQL DBMS);
- Advanced Workshop on XSS (Demonstration of the most current varieties of XSS);
- Building effective information security systems (setting up and demonstrating specialized utilities and methods);
- Master class from guests of Corporate Laboratories (presentation of a report by an invited expert in the field of information security. Opportunity to talk and ask questions to the speaker);
- Expert level of post-operation and privilege elevation in Linux (collection of information about the system; privilege elevation — exploits, SUID, Race conditions, etc .; collecting credentials and attaching to the system; hiding traces; working in Metasploit Framework);
- Expert level of post-operation and elevation of privileges in Windows (analysis of a compromised system; exploitation of vulnerabilities and configuration errors in the system and third-party applications; bypass "UAC"; methods of transferring files; extracting passwords in open form; "pass-the-hash");
- Investigation of cybercrime (reconstruction of the attacker's actions; collection of evidence, his points; data collection for transfer to law enforcement agencies; rules for dumping RAM and analysis, use of specialized utilities; analysis of file systems; determination of possible consequences and damage assessment; use of HoneyPot; counteraction to data collection, antifungal);
- Strengthening the skills acquired in practice: CTF-tasks and an examination laboratory. Performance of a pentest of a corporate network.
Course duration: 4-5 weeks, cost: 130,000 rubles.
In addition to the main training program, recognized experts, such as Grigory Zemskov ( Revizium ), Oleg Mikhalsky ( Acronis ), Maxim Lagutin ( Sitesecure ), Sergey Rebz (Antichat, Rebz.net ), Oleg, make interesting presentations as guests of the “Corporate Laboratories”. Bondarenko ( Qrator ). Professionals taking the opportunity to ask questions to guests in real time, and for everyone we publish video recordings of performances in the public domain. We will try to continue to follow this good tradition!
Summing up, it is worth noting the main points of the Corporate Laboratories training program:
- The course program is designed to be trained on the job, in order to complicate the material - from the “basis” to the “hardcore”;
- The course will undoubtedly be useful for IT and IS specialists who are interested in practical security issues;
- Despite the long course (from 3 weeks to 1.5 months, depending on the module), the course is very rich and includes the author's material of specialists dealing with practical information security for more than 10 years (Luka @exitusletaris Safonov, Alexander sinist3r Dmitrenko, Ares Intercepter , Vladimir Korennoy, etc.);
- In addition to the knowledge and skills gained in the courses, specialists develop their own horizons in the field of information security, which allows us to more accurately determine the direction for further development.
The course is aimed at obtaining practical training and requires great dedication. Learn more about the "Corporate Laboratories" by the link . Thank you for taking the time to read the full article. If you have questions - I will be glad to answer!
Source: https://habr.com/ru/post/258663/
All Articles