Win32 / Spy.Bebloh banking trojan is used to steal online banking data
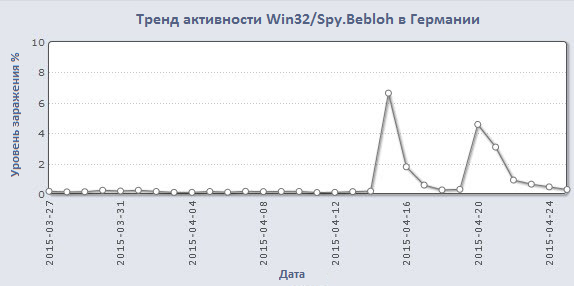
Recently, the Win32 / Spy.Bebloh banking Trojan program has significantly increased its activity in German-speaking countries. This malware was discovered in 2009 and, as new versions of Windows were released, were updated by hackers.

Win32 / Spy.Bebloh uses a well-known user OS compromise mechanism called Man-in-the-Browser (MitB), i.e., the Trojan program injects its malicious code into the running browser process. Using this method, the confidential data of online banking is stolen due to the introduction of phishing content to legitimate pages.
')
To distribute Win32 / Spy.Bebloh, attackers use phishing emails. The potential victim receives a malicious attachment in the form of a ZIP archive with a Bebloh dropper inside. An example of such a message is shown below in the screenshot.

Attackers use a convincing message subject to lure the user into installing malware. Usually, topics similar to other malicious campaigns are used, i.e. the postal status of a shipment, an account from a bank or another important document. The following are the names of the attachment files used by the attackers.
Below are the names of executable files droppers Bebloh from these archives.
As in the case of other similar banker Trojans, Win32 / Spy.Bebloh consists of the payload and malicious code being introduced into the processes. To disguise malicious functions, useful is embedded in the running process of Windows Explorer (explorer.exe). The first action that is performed by its code is responsible for checking a working internet connection through a call to the Google search engine. In the case of the presence of a connection, the malicious program reports a successful infection to its remote C & C server. The message that Bebloh sends to the server also contains some additional information about the victim: IP address, OS information, etc.
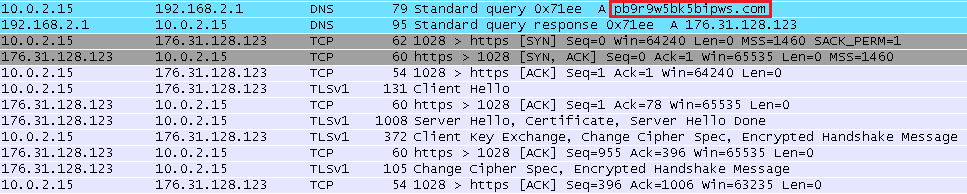
Interaction with a remote server is carried out through a secure SSL connection. The server sends an encrypted configuration file to Bebloh, which will be stored in the Windows registry. The file contains instructions from Bebloh on which online banking systems it should discredit.
The malicious program uses the mechanism of intercepting API calls in the context of running processes; below is a list of such processes:
Bebloh also controls user authentication on FTP and mail services through similar interception of API in the following software:
Bebloh can download files from the Internet and then execute on a compromised user system. In addition, it can create screenshots of the desktop and update its files to a more current version. To ensure its survival after a reboot, the malware uses a known registry key.
Conclusion
Earlier, we looked at various members of the malware families known as banker Trojans. Some of them target specific regions, for example, Corkow, which specializes in compromising users from Russia and Ukraine. The same can be said about Win32 / Spy.Bebloh . We recorded its greatest focus on users in Germany. The propagation mechanism of Bebloh is not special and has been observed in use in many malicious campaigns.

Win32 / Spy.Bebloh uses a well-known user OS compromise mechanism called Man-in-the-Browser (MitB), i.e., the Trojan program injects its malicious code into the running browser process. Using this method, the confidential data of online banking is stolen due to the introduction of phishing content to legitimate pages.

')
To distribute Win32 / Spy.Bebloh, attackers use phishing emails. The potential victim receives a malicious attachment in the form of a ZIP archive with a Bebloh dropper inside. An example of such a message is shown below in the screenshot.

Attackers use a convincing message subject to lure the user into installing malware. Usually, topics similar to other malicious campaigns are used, i.e. the postal status of a shipment, an account from a bank or another important document. The following are the names of the attachment files used by the attackers.
- Ihre Rechnung vom 04/15/2015_als_pdf.zip
- DOC_Bewerbung-Februar_2015.zip
- VodafoneWillkommen_713153127333.zip
- DHL_Paket-907628066996.zip
- DPD_Status Ihres Paketes_04727471384232 _pdf.zip
- Anwendung-april2015-DOC.zip
Below are the names of executable files droppers Bebloh from these archives.
- Ihre Rechnung vom 04/15/2015_als_pdf.PDF.exe
- DOC_Bewerbung-Februar_2015.doc.exe
- VodafoneWillkommen_769054799033.PDF.exe
- DHL_Paket-649888400277.xml.exe
- DPD_Status Ihres Paketes_01377200117628 _pdf.exe
- Anwendung-april2015-DOC.DOC_.exe
As in the case of other similar banker Trojans, Win32 / Spy.Bebloh consists of the payload and malicious code being introduced into the processes. To disguise malicious functions, useful is embedded in the running process of Windows Explorer (explorer.exe). The first action that is performed by its code is responsible for checking a working internet connection through a call to the Google search engine. In the case of the presence of a connection, the malicious program reports a successful infection to its remote C & C server. The message that Bebloh sends to the server also contains some additional information about the victim: IP address, OS information, etc.

Interaction with a remote server is carried out through a secure SSL connection. The server sends an encrypted configuration file to Bebloh, which will be stored in the Windows registry. The file contains instructions from Bebloh on which online banking systems it should discredit.
The malicious program uses the mechanism of intercepting API calls in the context of running processes; below is a list of such processes:
- Avant Web Browser (avant.exe)
- Google Chrome (chrome.exe)
- Internet Explorer (iexplore.exe)
- Maxthon Web Browser (maxthon.exe)
- Mozilla web browser (mozilla.exe)
- MyIE web browser (myie.exe)
- Opera (opera.exe)
Bebloh also controls user authentication on FTP and mail services through similar interception of API in the following software:
- • Core FTP (coreftp.exe)
- • CuteFTP (ftpte.exe)
- • FileZilla (filezilla.exe)
- • FTP Commander Pro (cftp.exe)
- • FTP Voyager (FTPVoyager.exe)
- • SmartFTP (SmartFTP.exe)
- • Total Commander (TOTALCMD.EXE)
- • WinSCP (WinSCP.exe)
- • Microsoft Outlook (OUTLOOK.EXE)
- • Outlook Express (msimn.exe)
- • The Bat! (thebat.exe)
Bebloh can download files from the Internet and then execute on a compromised user system. In addition, it can create screenshots of the desktop and update its files to a more current version. To ensure its survival after a reboot, the malware uses a known registry key.
Conclusion
Earlier, we looked at various members of the malware families known as banker Trojans. Some of them target specific regions, for example, Corkow, which specializes in compromising users from Russia and Ukraine. The same can be said about Win32 / Spy.Bebloh . We recorded its greatest focus on users in Germany. The propagation mechanism of Bebloh is not special and has been observed in use in many malicious campaigns.
Source: https://habr.com/ru/post/258321/
All Articles