Certificate Authority AD + Smart Card = Authorization of the user in the domain
Good day!
Today I will tell you how to configure user authorization in the domain using a smart card.
So, let's begin!
The first thing we need is the availability of a smart card reader and a card, as well as a desire to help users forget about the password.
')
For testing, we used the products of the company ESMART of the ISBC group of companies (esmart.ru):
Reader ACR 38U:

Reader ACR 39U:

Smart Card ESMART Token SC 64k:

The second is the availability of the domain.
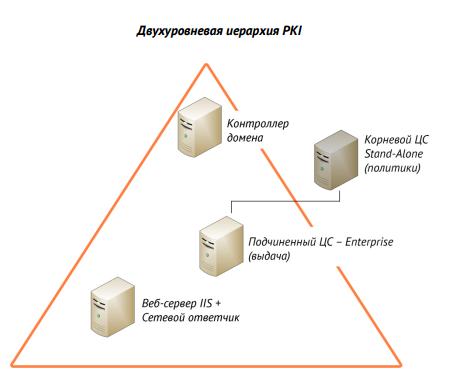
Initially, we will design the PKI infrastructure. When planning, it is necessary to determine the number and hierarchy of Certification Centers.
We used a two-tier PKI hierarchy with two CA centers. The scheme looks like this:
Install the ESMART PKI Client on the subordinate CA. The latest version of the client can be downloaded from the official site.
Add the IIS Web Server server role and leave all the default values (for a start).
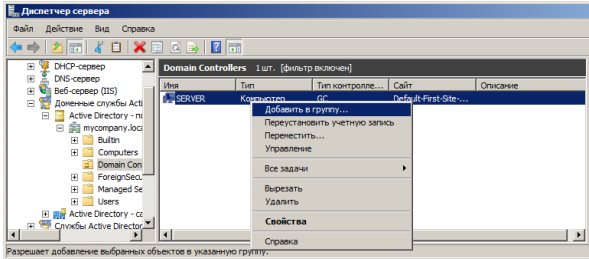
Add all domain controllers to the Certificate Service DCOM Access security group. This is necessary in order to be able to request a user certificate.
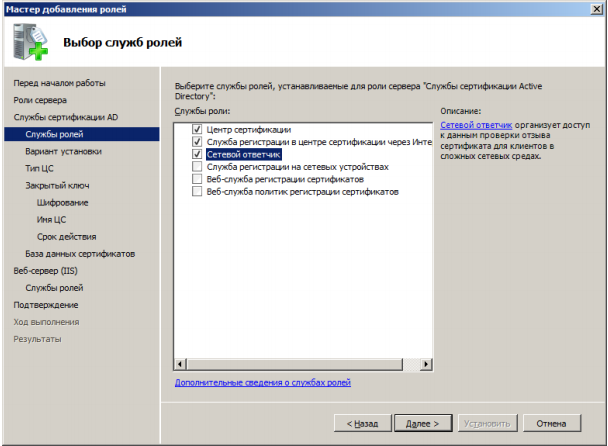
Now let's proceed directly to the installation and configuration of the CA.
Add server role:
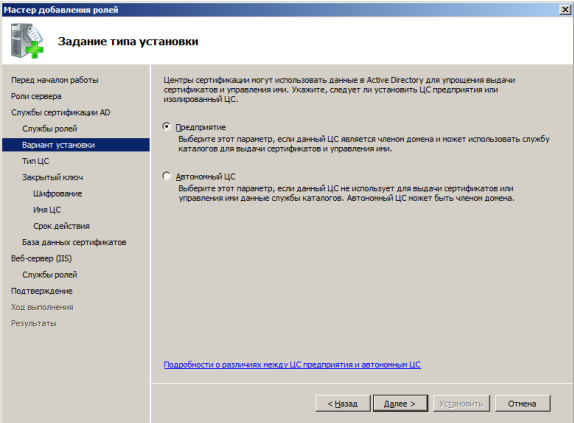
The CA server must be in the domain, otherwise you will not have an Enterprise item actively:
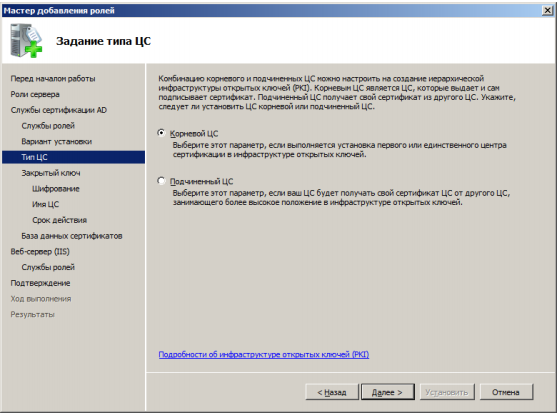
In the next installation step, select the necessary item depending on which CA is installed:
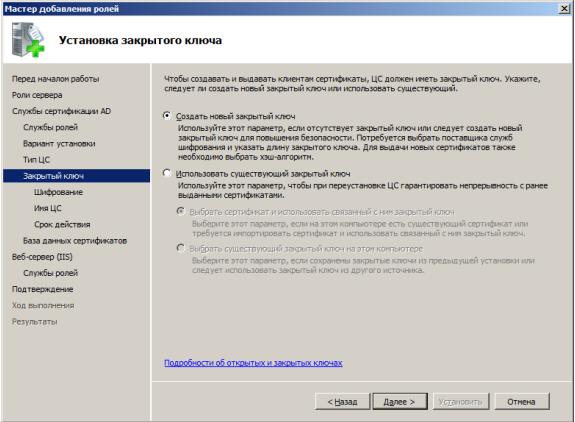
Create a private key:
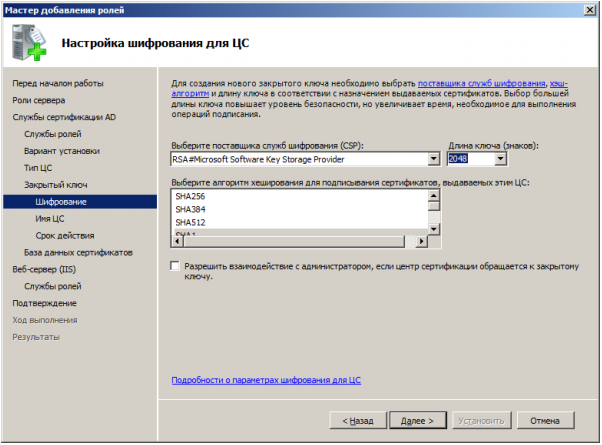
Select the necessary settings. We used the SHA-512 algorithm and the key length 2048:
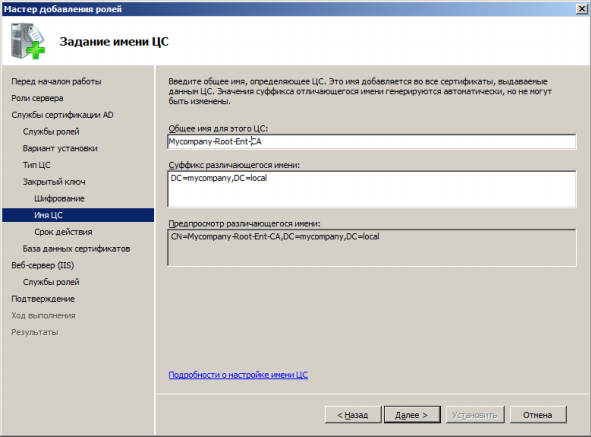
Set the name displayed in the certificate:
Select the validity period of the CA certificate. For the root CA we left it for 10 years, for a subordinate 5 years, for certificates of users 1 year:

Specify where we will store the logs:
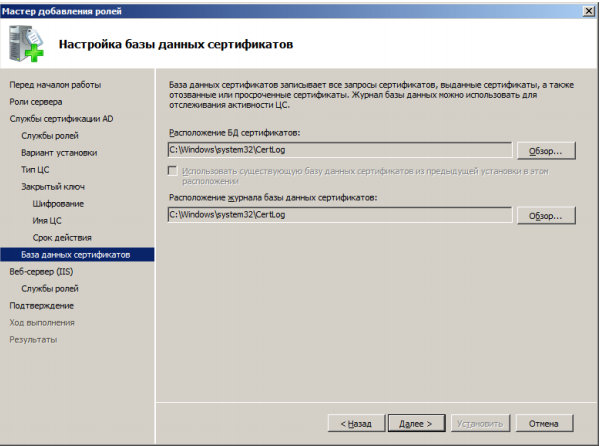
Next, in the wizard, leave everything by default:

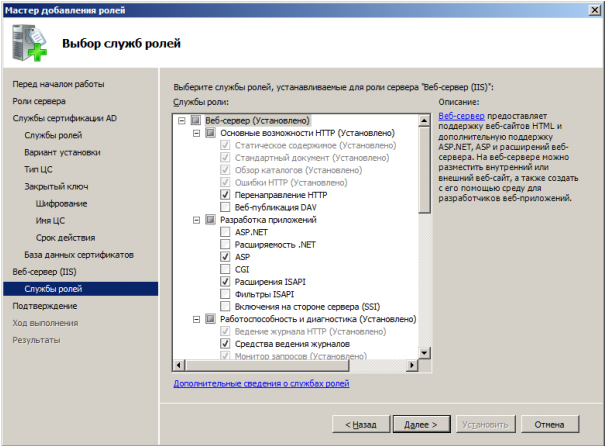
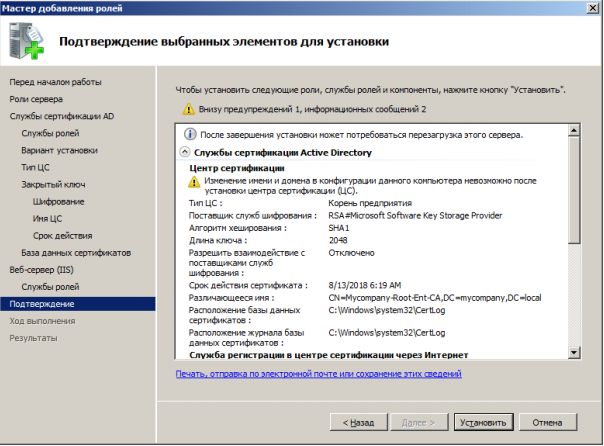
So, after installation, we have the registration service available at http (s): // IP address or DNS name of the CA / certsrv server. Configure the https protocol on IIS. For the certificate issuance service to work correctly, you must create a domain certificate and specify its IIS roles for the https protocol.
Opening certificates of serer:
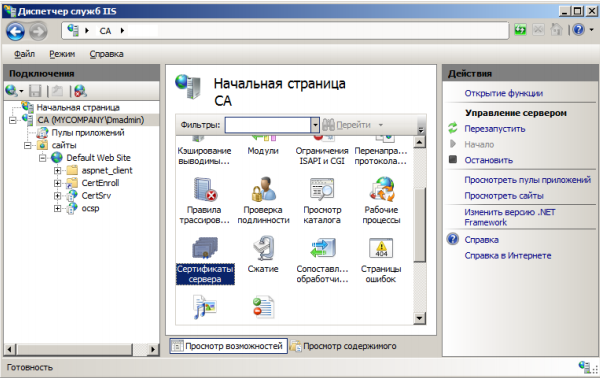
Click Create domain certificate:

Fill out the form:
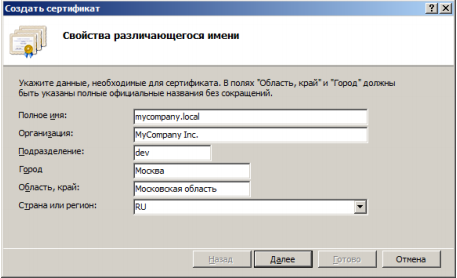
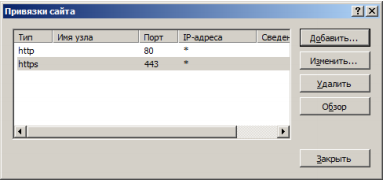
The issued certificate will appear in the list of server certificates. It must be linked to the https protocol. When binding, we left access only through https:

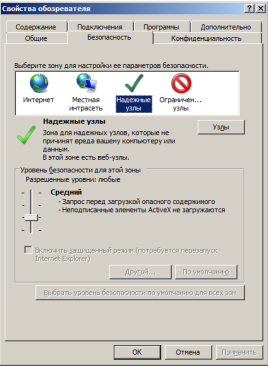
To avoid problems with ActiveX, you need to add a resource to trusted nodes. Added it through GPO.
So the floor is done. Now you need to configure the AWP users. We will do this through a GPO.
The first thing you need to do is set the launch parameter of the "Smart Card Removal Policy" service:
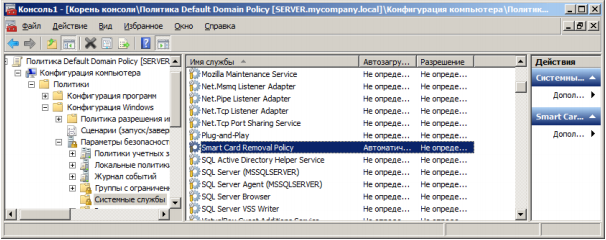
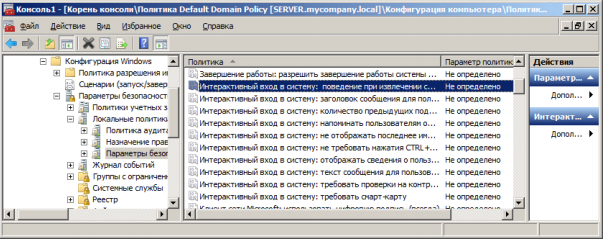
Through GPO we will configure an interactive input for users. Enable the option "Interactive login: Require smart card" and "Interactive login: Behavior when removing a smart card."
Next, configure the templates for issuing certificates.
In the Certification Authority snap-in, right-click on the “Certificate Templates” section and create three issued templates.
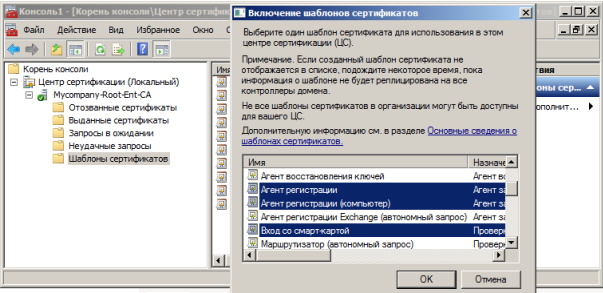
If necessary, you can edit the templates for the needs or requirements of the company. After the change, do not forget to publish templates in the domain.
In order to request certificates, you must request the certificate of the Certificate Request Agent. To do this, we make a request on behalf of a domain administrator or a user with delegated rights.
Open the certificates snap-in for the local user, the Personal section. In the context menu, select All tasks - Request new certificate. Click Next. On the next screen, mark the Enrollment Agent (Certificate Request Agent) and click Enroll. After that, the administrator will receive a new certificate:

And now we will make a request for a user certificate for a smart card.
In the Certificates console (certmgr.msc), right-click on the section Personal -> Additional operations -> Register on behalf of ... and request a new certificate. We select according to what policy the request will occur.
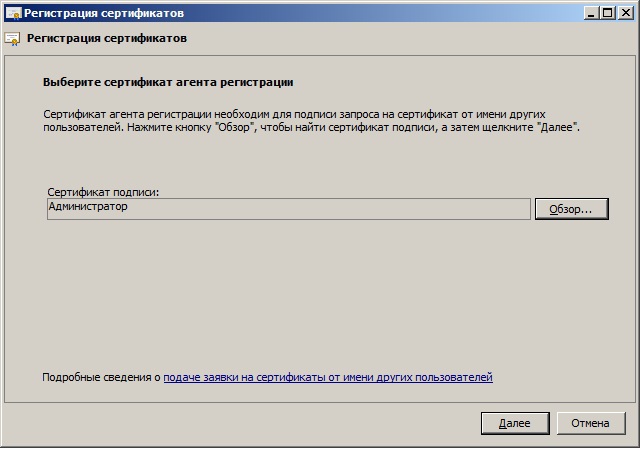
Specify the registration agent certificate:
In the list of requests we indicate “Login with smart card”:
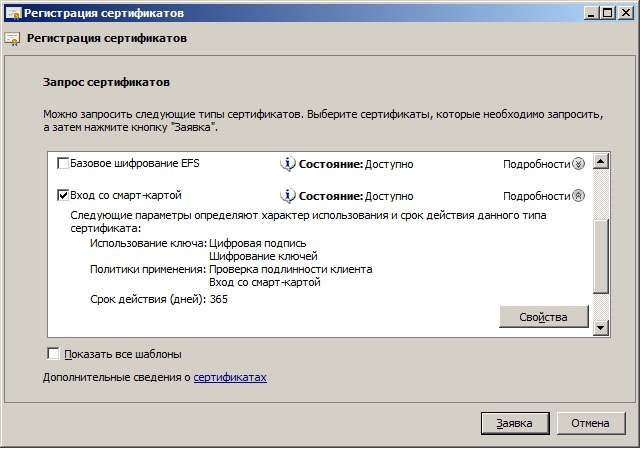
In the settings you must specify the cryptographic provider:

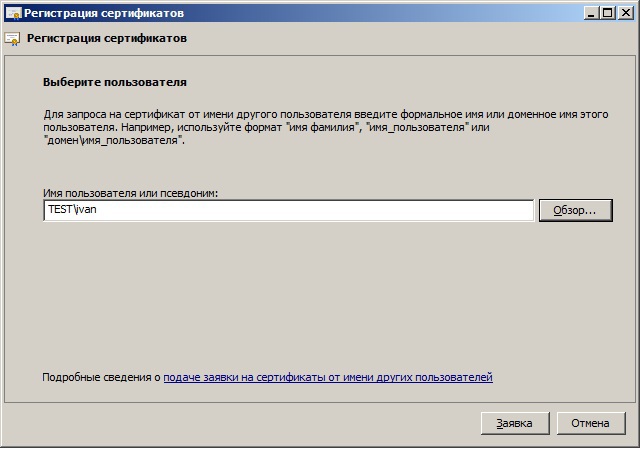
Select the user for whom the certificate will be issued:
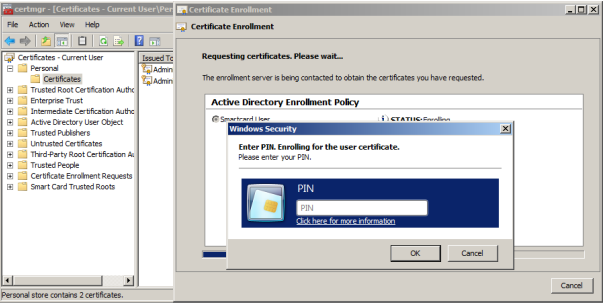
To issue a certificate, insert the smart card and enter the PIN from the card:
After all operations, you can check the map on the user's workstation.
A similar algorithm can be used to set up user authentication via etoken PRO (Java).
Thank you for reading this article. If you have questions, ask, I will be glad to answer!
Today I will tell you how to configure user authorization in the domain using a smart card.
So, let's begin!
The first thing we need is the availability of a smart card reader and a card, as well as a desire to help users forget about the password.
')
For testing, we used the products of the company ESMART of the ISBC group of companies (esmart.ru):
Reader ACR 38U:

Reader ACR 39U:

Smart Card ESMART Token SC 64k:

The second is the availability of the domain.
Initially, we will design the PKI infrastructure. When planning, it is necessary to determine the number and hierarchy of Certification Centers.
We used a two-tier PKI hierarchy with two CA centers. The scheme looks like this:

Install the ESMART PKI Client on the subordinate CA. The latest version of the client can be downloaded from the official site.
Add the IIS Web Server server role and leave all the default values (for a start).
Add all domain controllers to the Certificate Service DCOM Access security group. This is necessary in order to be able to request a user certificate.

Now let's proceed directly to the installation and configuration of the CA.
Add server role:

The CA server must be in the domain, otherwise you will not have an Enterprise item actively:

In the next installation step, select the necessary item depending on which CA is installed:

Create a private key:

Select the necessary settings. We used the SHA-512 algorithm and the key length 2048:

Set the name displayed in the certificate:

Select the validity period of the CA certificate. For the root CA we left it for 10 years, for a subordinate 5 years, for certificates of users 1 year:

Specify where we will store the logs:

Next, in the wizard, leave everything by default:



So, after installation, we have the registration service available at http (s): // IP address or DNS name of the CA / certsrv server. Configure the https protocol on IIS. For the certificate issuance service to work correctly, you must create a domain certificate and specify its IIS roles for the https protocol.
Opening certificates of serer:

Click Create domain certificate:

Fill out the form:

The issued certificate will appear in the list of server certificates. It must be linked to the https protocol. When binding, we left access only through https:


To avoid problems with ActiveX, you need to add a resource to trusted nodes. Added it through GPO.

So the floor is done. Now you need to configure the AWP users. We will do this through a GPO.
The first thing you need to do is set the launch parameter of the "Smart Card Removal Policy" service:

Through GPO we will configure an interactive input for users. Enable the option "Interactive login: Require smart card" and "Interactive login: Behavior when removing a smart card."

Next, configure the templates for issuing certificates.
In the Certification Authority snap-in, right-click on the “Certificate Templates” section and create three issued templates.

If necessary, you can edit the templates for the needs or requirements of the company. After the change, do not forget to publish templates in the domain.
In order to request certificates, you must request the certificate of the Certificate Request Agent. To do this, we make a request on behalf of a domain administrator or a user with delegated rights.
Open the certificates snap-in for the local user, the Personal section. In the context menu, select All tasks - Request new certificate. Click Next. On the next screen, mark the Enrollment Agent (Certificate Request Agent) and click Enroll. After that, the administrator will receive a new certificate:

And now we will make a request for a user certificate for a smart card.
In the Certificates console (certmgr.msc), right-click on the section Personal -> Additional operations -> Register on behalf of ... and request a new certificate. We select according to what policy the request will occur.
Specify the registration agent certificate:

In the list of requests we indicate “Login with smart card”:

In the settings you must specify the cryptographic provider:

Select the user for whom the certificate will be issued:

To issue a certificate, insert the smart card and enter the PIN from the card:

After all operations, you can check the map on the user's workstation.
A similar algorithm can be used to set up user authentication via etoken PRO (Java).
Thank you for reading this article. If you have questions, ask, I will be glad to answer!
Source: https://habr.com/ru/post/258183/
All Articles