Analysis of CPL malware, part 2
The fact that in most cases URLs are stored as plain text, or the decryption key is located in the decryption function itself, allows us to extract these URLs automatically from many samples of CPL malware using a special script. In the case of a sample that stores lines in clear text, the line with the address can be extracted directly from the CPL file. Otherwise, that is, in the case when the string with the address is encrypted, the script analyzes the decryption function in which the key is stored. The exceptions were some samples of malware for which the script could not decrypt the encrypted strings. In such samples, the decryption key was not available in the function, but was located in the resources of the CPL file. To extract the key from there, the malicious code uses standard APIs for working with resources: FindResource , LoadResource , SizeofResource and LockResource . The resource itself, in which the decryption key is located, is encrypted.

Fig. Sample CPL malware with a key to decrypt strings in resources.
As we mentioned above, the entry point to the DllMain library is executed before the exported CPlApplet function and does not contain any malicious code in most samples. However, in some samples, we discovered a special Anti-VM code that allowed a malicious program to detect the virtual machine environment. The screenshot below shows a fragment of such a code from DllMain .

Fig. The code snippet of the CPL malware, which checks the OS environment for a virtual machine.
')
The above code is responsible for checking the environment of three different environments: Wine, VMware, Virtual PC. If any of them is present, the save_str function is called . This function stores in memory a string describing the type of environment. Further, the CPlApplet function code will check the contents of this line on its first call. The presence of an identifier for one environment or another signals the CPlApplet function code to complete its execution without executing a block of code that processes the main CPL_DBLCLK message.
The figure below shows the code for checking the Wine environment. To do this, call the function GetProcAddress to get the addresses of the functions ntdll! Wine_get_version and ntdll! Wine_nt_to_unix_file_name . Obviously, such exports are absent in the conventional system.
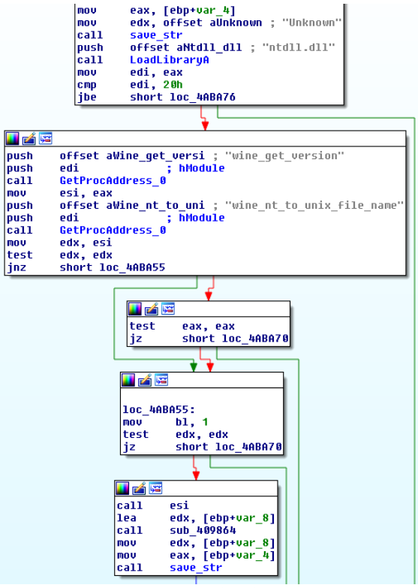
Fig. The code for checking the Wine environment.
The following screenshot shows the CPL malware code from DllMain , which is responsible for verifying the VMware environment. It uses a well-known mechanism for obtaining VMware versions using I / O ports. This check is possible because the virtual machine code takes control of the in instruction of the processor. The instruction is used for the interaction of the virtual machine and VMware software running on the user's system (host). The screenshot shows the arguments of this instruction, which lead to the fact that the value “VMXh” is returned to the calling code in the ebx register.
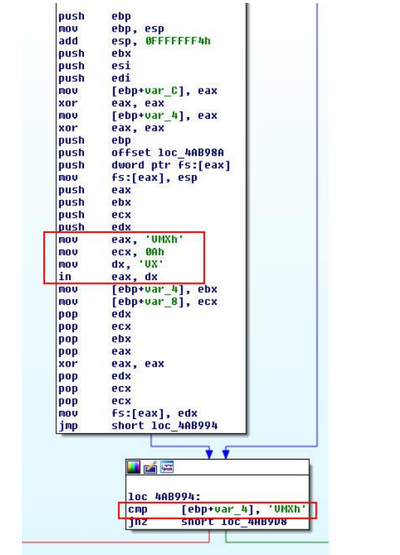
Fig. VMware environment verification code.
For Virtual PC, the check is presented below, while it can be seen that it is performed by executing a special instruction of the vpcext processor. In a normal OS environment that does not run in a virtual machine, the execution of this instruction will generate an exception.
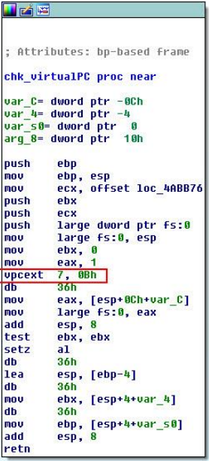
Fig. The verification code for the Virtual PC environment.
We mentioned that CPL malware is used as bootloaders or downloaders to download other malware into the system. In our case, the downloadable malware is a banking Trojan, although any other type of malware can be used instead.
We observed several samples of banking Trojans that are loaded with CPL malware. They all had similar characteristics. One of the samples of the banker studied by us has the following SHA-1: 3C73CA6A3914A6DF29F01A895C4495B19E71A234. This executable file is not packaged and the lines found there directly indicate the functions it performs, they are listed below in the list.

Fig. Encrypted bank malware strings.
We managed to decipher these lines, and we received additional information about what functions the banking Trojan performs and what services it focuses on. The lines contain the following information.
Thus, the analyzed bankers included the following possibilities: the introduction of malicious code into certain processes, the introduction of legitimate web pages of fake forms and text entry fields, capture of characters typed by the user on the keyboard and tracking the mouse cursor, the mechanism of encrypted interaction with a remote C & C server .
The diagram below shows the dynamics of the prevalence of malicious CPL files, according to the data of the virus laboratory of our Latin American office.
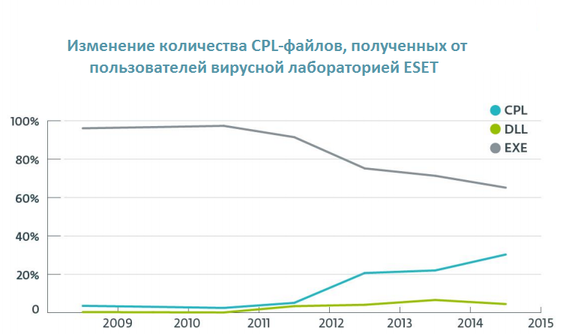
Fig. Statistics of malicious CPL files in comparison with other DLL and EXE files.
The graph above shows the dynamics and the relationship between the types of executable files in the interval between 2009 and the first months of 2015. From mid-2011, the growth of CPL malware files entering our virus lab began. Then this growth stabilized, but from mid-2013 resumed its trend.
The chart below shows the statistics on the distribution of malicious samples of CPL malware by year. It is seen that only for 2013 and 2014. the number of such samples accounted for 90% of the total flow of such malware.
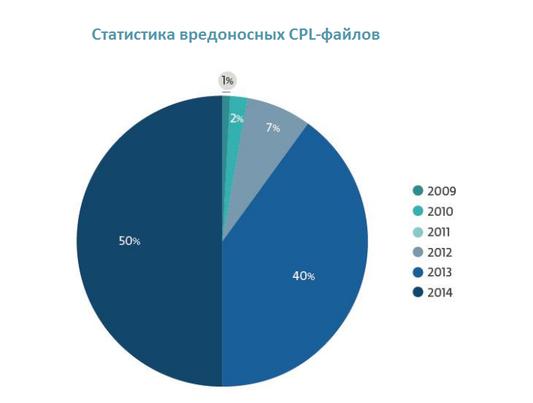
Fig. Distribution of CPL file detection by year.
Of the more than 1.5 thousand CPL malware samples that we observed, 82% of detections were in the Win32 / TrojanDownloader.Banload bootloader . This family of malware has prevailed in Brazil for many years. Our ESET LiveGrid telemetry system also points to Brazil as the country that has suffered the most from the actions of this malicious program (the largest number of infections).

Fig. Geography of distribution Win32 / TrojanDownloader.Banload .
In the diagram below you can see the percentage of Win32 / TrojanDownloader.Banload infections in different countries of the total. It can be seen that Brazil accounts for 76% of all detections in 2014. This fact once again confirms the targeting of intruders precisely in this region. The second place is occupied by Spain, which accounts for 11 times fewer infections than Brazil.
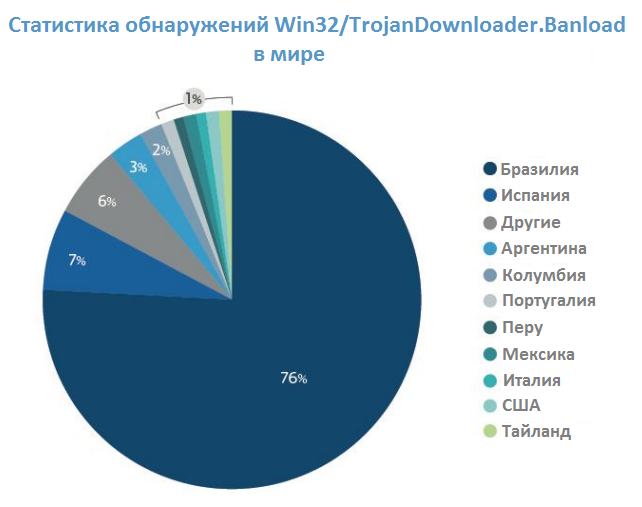
Fig. Win32 / TrojanDownloader.Banload detection statistics in the world.
This malware also ranks first in terms of prevalence in Brazil among other malware. Below is the threat rating for this country for March 2015.
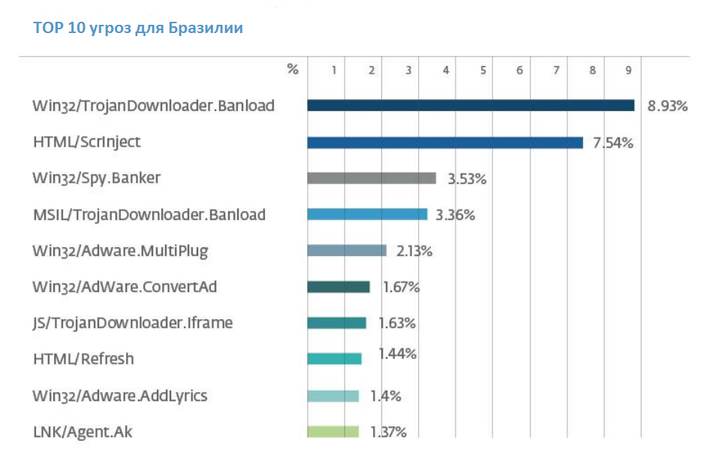
Fig. The most common threats in Brazil.
Over the course of several malicious campaigns used by cybercriminals to spread banking Trojans, we discovered 419 URLs that used about 300 different domains. All of these addresses pointed to malware files.
Of the 298 such domains that we observed between 2013 and 2015, 76 belonged to the compromised domains of Brazil. Some of the malicious links were shortened using a bit.ly type service. Based on the information that was collected by these services, we were able to obtain statistics on user referrals for these links and, thus, obtain the potential number of victims of a malicious campaign.
The attackers themselves used short link services to conceal the real URLs from the user's eyes, which could betray the intentions of the attackers. The chart below shows the statistics on the transition to shortened links for the period from the beginning of March 2014 to February 2015.
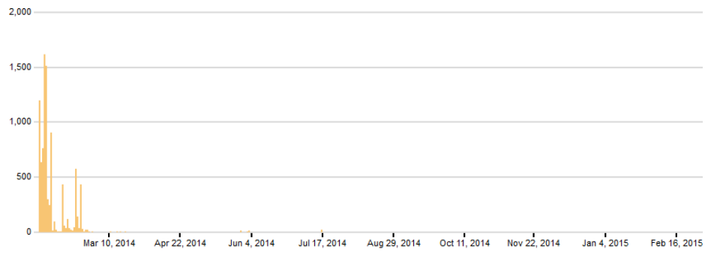
Fig. The number of clicks on shortened malicious links.
The table below shows the conversion statistics for multiple shortened links, as well as the malware that spread through them.

Another feature that we want to highlight for this malicious campaign and this type of malware as CPL malware is the statistics of packers and protectors used by attackers to complicate the detection of malware samples by antivirus solutions. As you can see, the most common packer is UPX - 27%.

Fig. Types of packers and protectors that are used in CPL malware.
Conclusion
We reviewed the mechanisms of this type of malware like CPL malware, as well as some banking malware that is downloaded to the user's computer by this type of malware. To spread CPL malware, attackers use the usual methods of delivering malware, which are no different from other instances of malicious campaigns.
Attackers supply this type of malware with special checks to detect the virtual machine environment. In addition, they use packers and protectors to complicate the detection of CPL malware by AV products.

Fig. Sample CPL malware with a key to decrypt strings in resources.
As we mentioned above, the entry point to the DllMain library is executed before the exported CPlApplet function and does not contain any malicious code in most samples. However, in some samples, we discovered a special Anti-VM code that allowed a malicious program to detect the virtual machine environment. The screenshot below shows a fragment of such a code from DllMain .

Fig. The code snippet of the CPL malware, which checks the OS environment for a virtual machine.
')
The above code is responsible for checking the environment of three different environments: Wine, VMware, Virtual PC. If any of them is present, the save_str function is called . This function stores in memory a string describing the type of environment. Further, the CPlApplet function code will check the contents of this line on its first call. The presence of an identifier for one environment or another signals the CPlApplet function code to complete its execution without executing a block of code that processes the main CPL_DBLCLK message.
The figure below shows the code for checking the Wine environment. To do this, call the function GetProcAddress to get the addresses of the functions ntdll! Wine_get_version and ntdll! Wine_nt_to_unix_file_name . Obviously, such exports are absent in the conventional system.

Fig. The code for checking the Wine environment.
The following screenshot shows the CPL malware code from DllMain , which is responsible for verifying the VMware environment. It uses a well-known mechanism for obtaining VMware versions using I / O ports. This check is possible because the virtual machine code takes control of the in instruction of the processor. The instruction is used for the interaction of the virtual machine and VMware software running on the user's system (host). The screenshot shows the arguments of this instruction, which lead to the fact that the value “VMXh” is returned to the calling code in the ebx register.

Fig. VMware environment verification code.
For Virtual PC, the check is presented below, while it can be seen that it is performed by executing a special instruction of the vpcext processor. In a normal OS environment that does not run in a virtual machine, the execution of this instruction will generate an exception.

Fig. The verification code for the Virtual PC environment.
We mentioned that CPL malware is used as bootloaders or downloaders to download other malware into the system. In our case, the downloadable malware is a banking Trojan, although any other type of malware can be used instead.
We observed several samples of banking Trojans that are loaded with CPL malware. They all had similar characteristics. One of the samples of the banker studied by us has the following SHA-1: 3C73CA6A3914A6DF29F01A895C4495B19E71A234. This executable file is not packaged and the lines found there directly indicate the functions it performs, they are listed below in the list.
- Track events and movements of the mouse cursor, keystrokes, and keyboard layouts. For example, “[enter]”, “[esp]”, (spacebar), “[cima]” (up arrow), “[baixo]”, (down).
- The functions of processing sockets and working with them.
- Functions of interaction with a remote server using an encrypted SSL connection.
- Handling messages in Portuguese related to online banking operations. "Utilize o teclado virtual."
- Support for various network protocols, for example, "ftpTransfer", "mailto:", ": //", "HTTP / 1.0 200 OK".
- Data collection accounts online services.
- Some strings are encrypted using the algorithm that was used in the CPL malware samples. The screenshot below shows these lines.

Fig. Encrypted bank malware strings.
We managed to decipher these lines, and we received additional information about what functions the banking Trojan performs and what services it focuses on. The lines contain the following information.
- The names of Brazilian financial institutions and banks: Sicredi, Banco Itaú, Santander, Bradesco, bb.com.br (Banco do Brasil), Caixa.
- Support for compromising the following browsers: Chrome, Opera, Firefox, IE, Safari.
- URLs: "hxxp: //www.sonucilaclama.com.tr/plugins/editors-xtd/pagebreak/oi/html/h/lg.php", "hxxp: //www.cvicak-polanka.cz/b /notify.php "," hxxp: //64.31.51.19/oi.txt "
- Track keystrokes such as “[Backspace]”, “[Page Up]”, “[Page Down]”.
- Data files and temporary files.
- Lines of various user agents.
- Commands like "cmd / c taskkill / f / im dwm.exe / t".
Thus, the analyzed bankers included the following possibilities: the introduction of malicious code into certain processes, the introduction of legitimate web pages of fake forms and text entry fields, capture of characters typed by the user on the keyboard and tracking the mouse cursor, the mechanism of encrypted interaction with a remote C & C server .
The diagram below shows the dynamics of the prevalence of malicious CPL files, according to the data of the virus laboratory of our Latin American office.

Fig. Statistics of malicious CPL files in comparison with other DLL and EXE files.
The graph above shows the dynamics and the relationship between the types of executable files in the interval between 2009 and the first months of 2015. From mid-2011, the growth of CPL malware files entering our virus lab began. Then this growth stabilized, but from mid-2013 resumed its trend.
The chart below shows the statistics on the distribution of malicious samples of CPL malware by year. It is seen that only for 2013 and 2014. the number of such samples accounted for 90% of the total flow of such malware.

Fig. Distribution of CPL file detection by year.
Of the more than 1.5 thousand CPL malware samples that we observed, 82% of detections were in the Win32 / TrojanDownloader.Banload bootloader . This family of malware has prevailed in Brazil for many years. Our ESET LiveGrid telemetry system also points to Brazil as the country that has suffered the most from the actions of this malicious program (the largest number of infections).

Fig. Geography of distribution Win32 / TrojanDownloader.Banload .
In the diagram below you can see the percentage of Win32 / TrojanDownloader.Banload infections in different countries of the total. It can be seen that Brazil accounts for 76% of all detections in 2014. This fact once again confirms the targeting of intruders precisely in this region. The second place is occupied by Spain, which accounts for 11 times fewer infections than Brazil.

Fig. Win32 / TrojanDownloader.Banload detection statistics in the world.
This malware also ranks first in terms of prevalence in Brazil among other malware. Below is the threat rating for this country for March 2015.

Fig. The most common threats in Brazil.
Over the course of several malicious campaigns used by cybercriminals to spread banking Trojans, we discovered 419 URLs that used about 300 different domains. All of these addresses pointed to malware files.
Of the 298 such domains that we observed between 2013 and 2015, 76 belonged to the compromised domains of Brazil. Some of the malicious links were shortened using a bit.ly type service. Based on the information that was collected by these services, we were able to obtain statistics on user referrals for these links and, thus, obtain the potential number of victims of a malicious campaign.
The attackers themselves used short link services to conceal the real URLs from the user's eyes, which could betray the intentions of the attackers. The chart below shows the statistics on the transition to shortened links for the period from the beginning of March 2014 to February 2015.

Fig. The number of clicks on shortened malicious links.
The table below shows the conversion statistics for multiple shortened links, as well as the malware that spread through them.

Another feature that we want to highlight for this malicious campaign and this type of malware as CPL malware is the statistics of packers and protectors used by attackers to complicate the detection of malware samples by antivirus solutions. As you can see, the most common packer is UPX - 27%.

Fig. Types of packers and protectors that are used in CPL malware.
Conclusion
We reviewed the mechanisms of this type of malware like CPL malware, as well as some banking malware that is downloaded to the user's computer by this type of malware. To spread CPL malware, attackers use the usual methods of delivering malware, which are no different from other instances of malicious campaigns.
Attackers supply this type of malware with special checks to detect the virtual machine environment. In addition, they use packers and protectors to complicate the detection of CPL malware by AV products.
Source: https://habr.com/ru/post/257835/
All Articles