Forensic and steganography in a video file: analysis of tasks for the online stage NeoQUEST-2015
 The past online stage of the annual cybersecurity competition NeoQUEST-2015 was extremely rich in interesting and non-trivial tasks! In this article we:
The past online stage of the annual cybersecurity competition NeoQUEST-2015 was extremely rich in interesting and non-trivial tasks! In this article we:- let's deal with video steganography and the esoteric programming language Piet, examining the task “Truth is inside”
- We climbed into the skin of a computer criminologist, work with TrueCrypt and answer the question “Was there a key?”.
Great news: the date of the "confrontation" of NeoQUEST-2015 is approved! The event will take place on July 2 (Thursday) in St. Petersburg, in the CLUB HOUSE ! As before, the entrance is free - you just need to register on our site .
1. “Truth inside” - steganography in video
Download the file apple.avi, the link to which is given in the task. We draw attention to the hint in the text of the legend to the task, hinting that comparing the received video with the original video on the Apple channel will help you to understand what to do next! Go to youtube.com, look for our video on the Apple channel.

We download it by any service for saving videos from youtube.com in .flv format. Why in .flv? Well, not for nothing that the newly installed flv-codecs are mentioned for some reason in the task.
')
It would be logical to compare these two videos frame by frame, for this we use the software solution ffmpeg . We split both videos into frames, each in its own directory:
ffmpeg -i ./youtube.flv ./1/%d.png ffmpeg -i ./apple.avi ./2/%d.png For comparison, the synchronization of directories in Total Commander is suitable:

The screenshot shows frames that are different in both videos, these 24 pieces. We will try to compare some pair of frames, for example, the 21st. To do this, use ImageMagic :
compare.exe 21.png 21.2.png diff.png 
In the upper left corner we see a rectangular area. In a detailed study, we understand that the low bit in the red pixel channel changes. Information hiding in the lower bits is a fairly common method of steganography. We have 24 frames, with modified low-order bits in a rectangular area. 24 bits is enough to encode 3 bytes of pixel color.

Now we need to collect an image from the lower bits, for this we use Python and, for example, PIL :

It is not difficult to guess that we have a program in the esoteric programming language Piet . We'll have to tinker a bit with the interpreter, after starting which the program displays a message containing the key to the task:
“Hello! Secret Key: 8aec4bb34fbdd11c2aef4fea391b4fe2 »
2. “Was there a key?” - forensic and TrueCrypt
Participants were given a disk dump in which they needed to find the key. Passage can be divided into the following stages:
- Mount disk
- Search for installed software
- Search for an encrypted logical drive
- Search volume encryption key
- Search for the key to the task
Mount disk
Windows 7 - 8.1 will allow you to mount a disk image without additional software. On other operating systems, you can use Virtual Box, VMWare and other virtualization software for mounting.
After mounting in Windows 8.1, 2 disks will appear.
The contents of the system disk:
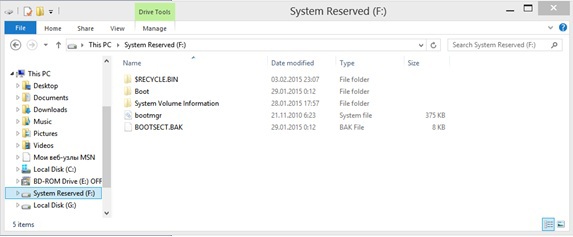
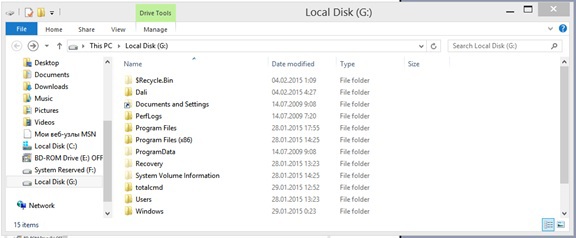
Disk with user data, which, of course, interest us in the first place:
Search for installed software
It is necessary to enable the display of hidden and system files, after which we check the main folders Program Files and Program Files (x86), where the TrueCrypt program is located. TrueCrypt is a computer program for on-the-fly encryption. It allows you to create a virtual encrypted logical drive that is stored as a file.

Search for an encrypted logical drive
In the description of the program indicated that with it you can create a virtual encrypted logical drive. To find this disk, use the program TChunt .
tchunt.exe -d ../ > tchunt.txt 
Open the tchunt.txt file

The X: \ Users \ JohnSmith \ files file is an encrypted container.
Search volume encryption key
In the root of the disk there is a folder Dali. Among all the images there is a file key.jpg. Based on this, we can assume that it is not the password that is used, but the key file. When you try to substitute this file as a key for a container, TrueCrypt reports an invalid password.

From which it can be concluded that the key is either hidden in the file key.jpg, or deleted, or key.jpg has nothing to do with the encrypted disk. Check the most simple version - the file is deleted (logical action, if you suddenly come after you!).

Restore key-x.jpg and try to use it as a key - the virtual disk is successfully mounted!

Search for the key to the task
The disk contains a very large number of files (all with the extension .jpg) and the key is most likely hidden in one of them. Let's try to check the latest open files with this extension in the system, for this you need to go to the registry of the installed OS. If the hard disk is mounted on a virtual machine, then just run the regedit command. If not, then you need to connect the necessary part of the registry - hive.
To do this, click File> Load Hive and select X: \ Users \ JohnSmith \ NTUSER.dat. Next, go on the path: Software \ Microsoft \ Windows \ CurrentVersion \ Explorer \ RecentDocs \ .jpg

Among the contents are the names of the last open files. Enumerate them and check the presence of the key in the image.
The key was on the image of "Peter I on a dog hunt.jpg"

And that is not all!
Ahead is an analysis of the remaining tasks of the online stage NeoQUEST-2015 and the expectation of a bright and sunny (despite the fact that in St. Petersburg) the event NeoQUEST-2015. The participants will face tense struggle at 8 o'clock, and the guests - contests, reports, practical workshops, gifts and communication with colleagues! We remind you that for this - just a couple of steps: register and (for those who are not here) buy tickets to Peter!
Source: https://habr.com/ru/post/257737/
All Articles