Laboratory penetration testing "Test lab v.7" eyes hackers
Review article on the results of participation in the free test lab "Test lab v.7" codenamed "Achilles Heel". The article contains information about the work on the preparation of the laboratory, partial passage, as well as comments of the winners.

“Test lab v.7” is a corporate network of a virtual company “SecureSoft LLC” based on Windows and Linux. A virtual company specializes in software development and has some security holes. The participants are invited, using the found vulnerabilities, to penetrate the network and get access to all the nodes of “SecureSoft LLC”, each of which contains a secret token (there are only 10).
The laboratory was launched on 01.05.2015 at 22:00 Moscow time and is available to this day. At the time of launch, about 1,200 participants from different countries were registered. For the convenience of communication and problem solving a forum was prepared in Russian and English. The actions of the participants could be observed on the Cyberattack world map.
')
The first to make a successful attack on all the nodes of the laboratory was Omar Ganiev (Beched). After 6 days of intense attack, Omar picked up the last token, thus becoming the test lab champion for the third time in a row.
Attention. The section contains instructions on the passage of the laboratory.
A feature of all the “Test labs” laboratories is the proximity to the real working conditions of the corporate network and the modeling of vectors and attack scenarios encountered in real life. This write-up describes the first tasks of the laboratory and the direction for the passage of the following. Before we complete the tasks, we need to register on the laboratory's website and configure settings in the distribution kit, which we will use to perform the pentest of the virtual network. It is recommended to use the Kali Linux distribution. This is a specialized distribution kit created for information security specialists and containing a large number of penetration testing tools. After passing the registration and connecting via VPN to the laboratory, the following information is available to us:
In the context of laboratories, penetration testing occurs in GrayBox mode — when partial information about the infrastructure under attack is known. In this case, we have a network map with nodes marked on it and their roles.
The first thing you need to do penetration testing is gathering information. We use the popular port scanning utility - nmap. After that, we manually check the received information, namely, we check the responses from the connection to the open ports using telnet and look at the generated code of the html pages.
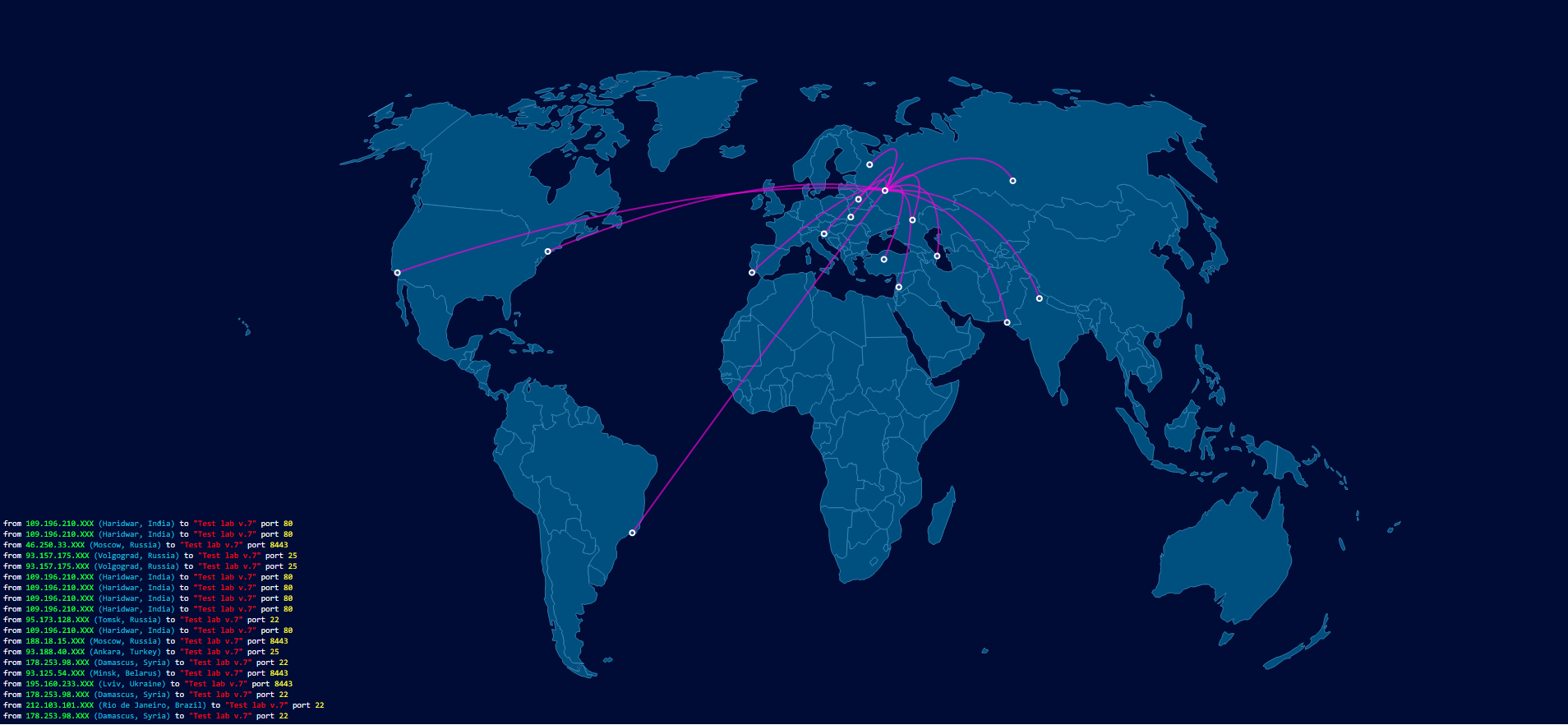
Especially for the launch of the 7th laboratory, a global attack map was implemented. Visualization of the attacks allowed to see the geography of the participants. According to the data at the time of this writing, specialists from 63 countries and 194 cities took part in the laboratory. The largest number of participants was from Russia (322 IP), followed by the United States (64 IP) and closes the top three Ukraine (37 IP). Moscow is in the lead in the rating of unique IP by cities (242 addresses), Kiev is in second place (25 addresses) and Petrozavodsk is in third place (18 addresses).
Full list of participating countries: Algeria, Andorra, Armenia, Australia, Austria, Belarus, Belgium, Bosnia and Herzegovina, Brazil, Bulgaria, Canada, Chile, China, Croatia, Cyprus, Czech Republic, Denmark, Egypt, Estonia, Finland, France, Georgia, Germany, Greece, Hong Kong (SAR), Hungary, India, Israel, Israel, Israel, Japan, Kazakhstan, Korea, Korea, Lithuania, Mexico, Moldova, Norway, Pakistan , Panama, Philippines, Poland, Portugal, Romania, Russia, Slovenia, Spain, Sweden, Syria, United Kingdom, United States, Uzbekistan, Zambia.
Work on the laboratory, as we have already done, is carried out in several stages:
1. Proposal and discussion of ideas for assignments.
2. Implementation of the bench version of the task, verification.
3. "Finishing" to the final version.
4. Combining into a common scenario.
In order to avoid problems during the launch of the laboratory, in the implementation of tasks are always taken into account:
- the fact of simultaneous execution of the task by more than one participant;
- not all participants are “white and fluffy”. It is necessary to exclude the possibility of vandalism or attempts to impede access to other participants.
In some cases, when the task requires complete control over the system, but it is so interesting that you want to include it in the laboratory, you have to make some compromise. Then we try to minimize the risks. For example, to provide for a script to restrict access for the minimum number of participants simultaneously.
Of course, it is very interesting to watch attacks in real time, being “on the other side”. In this laboratory, we did not use any intrusion detection systems, so the participants did not have any limitations in this regard. But, based on observations, the presence of such a system would reflect most of the attacks. Perhaps in the next lab we will include IDS / IPS bypass tasks.
Most port scans, brute force, directory scans, etc. it was made publicly available with the default settings: the nmap scripting engine and the DirBuster in the User-Agent, for example. On one of the tasks, we left two options for passing, but the second allowed us to prevent others - so we decided to see which option the participants would prefer. Unfortunately, as it was supposed, vandalism began after some time :)
At first, we decided to play along and imitate the presence of the administrator, who is trying to figure out what is happening and close the holes. For about an hour, the connections to the shelters were interrupted, deleted them and in every way interfered, but not closing the very possibility of exploitation. Then, nevertheless, the alternative option had to be closed, because some unscrupulous participants constantly tried to remove the token itself, making it difficult for others to complete this task - apparently, this exercise gave them more pleasure than going through the lab itself.
I hope the collective work of the authors of the article was not in vain and it turned out to be useful. I will be glad to consider all the wishes and comments in the drug. Have a nice day, everyone!

A couple of words about the lab
“Test lab v.7” is a corporate network of a virtual company “SecureSoft LLC” based on Windows and Linux. A virtual company specializes in software development and has some security holes. The participants are invited, using the found vulnerabilities, to penetrate the network and get access to all the nodes of “SecureSoft LLC”, each of which contains a secret token (there are only 10).
Chronology of events
The laboratory was launched on 01.05.2015 at 22:00 Moscow time and is available to this day. At the time of launch, about 1,200 participants from different countries were registered. For the convenience of communication and problem solving a forum was prepared in Russian and English. The actions of the participants could be observed on the Cyberattack world map.
')
The first to make a successful attack on all the nodes of the laboratory was Omar Ganiev (Beched). After 6 days of intense attack, Omar picked up the last token, thus becoming the test lab champion for the third time in a row.
In this laboratory, as in the previous ones, I grumbled that I had to beat a lot or guess a lot, but I still made the useful things for myself =). One of the most non-trivial tasks was the exploitation of vulnerabilities on the terminal server, where it was necessary to conduct DLL-hijacking around the MSE antivirus. Also, despite the distracting false paths, the task of the forum was highlighted, in which it was necessary to exploit vulnerabilities with the hands, and in which the fuzzing dictionaries by default in Burp Suite were let down. Other tasks are useful for practicing standard skills and the ability to compare different finds. Thanks to the organizers for the training ground!After Omar, after some time, the participants of MERRON, DarkCat and AV1ct0r managed to collect all the tokens. Despite the fact that the laboratory is considered to have been passed, it does not lose the essence, namely, to give everyone the opportunity to consolidate the skills of practical pentest, as well as get new ones. Given the complexity of the tasks, we have prepared a partial passage of the laboratory.
Omar Ganiev (Beched), incsecurity.ru
Write-up
Attention. The section contains instructions on the passage of the laboratory.
A feature of all the “Test labs” laboratories is the proximity to the real working conditions of the corporate network and the modeling of vectors and attack scenarios encountered in real life. This write-up describes the first tasks of the laboratory and the direction for the passage of the following. Before we complete the tasks, we need to register on the laboratory's website and configure settings in the distribution kit, which we will use to perform the pentest of the virtual network. It is recommended to use the Kali Linux distribution. This is a specialized distribution kit created for information security specialists and containing a large number of penetration testing tools. After passing the registration and connecting via VPN to the laboratory, the following information is available to us:
Initial information
- Testing company network: SecureSoft LLC.
- Server's IP address: 192.168.101.5
- Network map

In the context of laboratories, penetration testing occurs in GrayBox mode — when partial information about the infrastructure under attack is known. In this case, we have a network map with nodes marked on it and their roles.
The first thing you need to do penetration testing is gathering information. We use the popular port scanning utility - nmap. After that, we manually check the received information, namely, we check the responses from the connection to the open ports using telnet and look at the generated code of the html pages.
Collection of information
Running the "nmap 192.168.101.5" utility produced the following information:
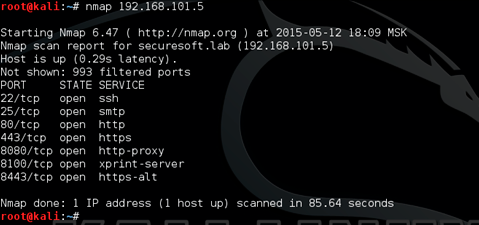
Open port 22 provides SSH access. For now, remember this.
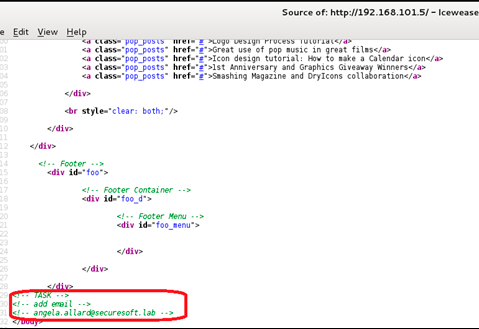
The open 25 port of the mail server says that we can try to perform password matching (BruteForce) at a high enough speed (unlike web-bruteforce), Hydra is well suited for bruteforce-attacks. Checking the website on port 80 provided us with information on the account login rule used. In the source code of the web page, you can find the e-mail of one of the company's employees.

Open port 22 provides SSH access. For now, remember this.
The open 25 port of the mail server says that we can try to perform password matching (BruteForce) at a high enough speed (unlike web-bruteforce), Hydra is well suited for bruteforce-attacks. Checking the website on port 80 provided us with information on the account login rule used. In the source code of the web page, you can find the e-mail of one of the company's employees.

We use this information to attack
After checking the website on port 8100, we see that this is the web interface to the mail server on port 25. We will use this information later, but for now let's execute the selection of the password for the detected account.
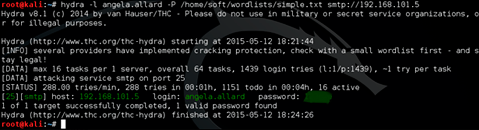
The found login and password provides access to the SecureSoft LLC angela.allard employee’s mail via the web interface.
Looking through the mail angela.allard, we find a list of employees of the company SecureSoft LLC.
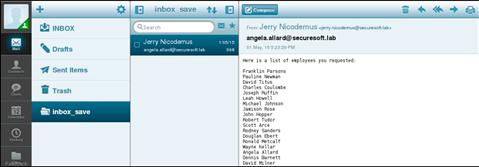
Now we have at our disposal a large list of company employees, which we will bring to the logic of forming account logins <name>. <Surname>.
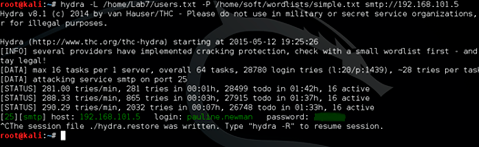
The resulting list is fed Hydra and ... And wait a bit. After some time, we get the password from the pauline.newman account. For the attack of Bruteforce (selection of passwords) a dictionary was used, consisting of popular passwords of 2014, found through a google request (it took 5 minutes to prepare the dictionary).
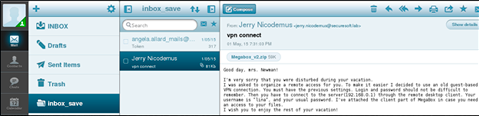
The post of the second employee provided us with more interesting information. First, we received the coveted token from the Mail task, and second, we received additional information for the passage of the laboratory.

The found login and password provides access to the SecureSoft LLC angela.allard employee’s mail via the web interface.
Looking through the mail angela.allard, we find a list of employees of the company SecureSoft LLC.

Now we have at our disposal a large list of company employees, which we will bring to the logic of forming account logins <name>. <Surname>.
The resulting list is fed Hydra and ... And wait a bit. After some time, we get the password from the pauline.newman account. For the attack of Bruteforce (selection of passwords) a dictionary was used, consisting of popular passwords of 2014, found through a google request (it took 5 minutes to prepare the dictionary).

The post of the second employee provided us with more interesting information. First, we received the coveted token from the Mail task, and second, we received additional information for the passage of the laboratory.

Implement an additional attack vector
This is the introductory part of the laboratory, I hope it will help you understand the logic of the tasks and solve the remaining tasks on your own.As in the real penetration testing, the attacker collects information about the attacked system in any possible and accessible places.
The most interesting may be resources for IT / IB staff - there may be extremely critical information that will help access the entire network. An interesting resource is marked on the provided scheme - Admin Tools. Using the nmap utility, scan the port range 1–10,000 of the resource that interests us.
.
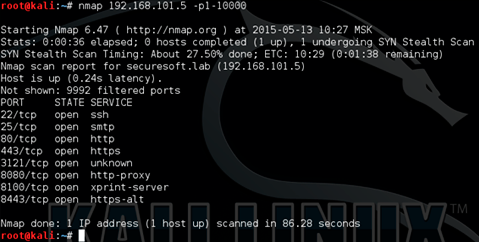
We see that some application is hanging on a non-standard port 3121. Empirically, we determine that the Admin Tools website is running there.
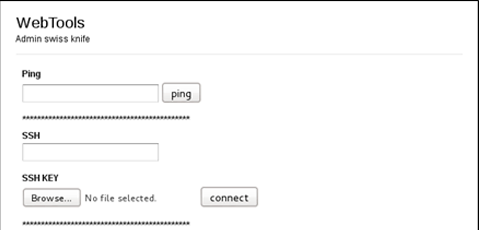
The functionality of this site turned out to be inoperative. It contained utilities that facilitate the work of the system administrator. The tool tip to the submission form was found indicating that the SSH key was loaded, suggesting that the file could be located on this server. After studying the site structure and html-code, nothing useful was found, so it was decided to scan the site directories with the dirb utility.
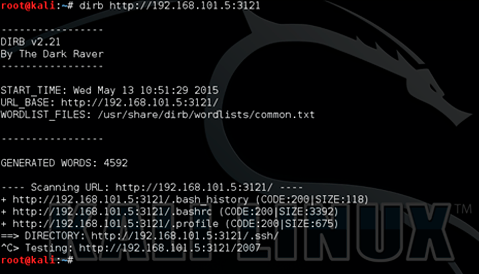
A .bash_history file was found. This file contains the history of commands that were executed in the console, for example, via SSH. In this file, the name of the SSH private key was found - ssh_key.priv, which was immediately downloaded from the site.

Now we have data for access to the internal network of the company SecureSoft LLC through port 22 using ssh. Also, in the ssh_key.priv file you can find the token to the Admin Tools task.
The most interesting may be resources for IT / IB staff - there may be extremely critical information that will help access the entire network. An interesting resource is marked on the provided scheme - Admin Tools. Using the nmap utility, scan the port range 1–10,000 of the resource that interests us.
.

We see that some application is hanging on a non-standard port 3121. Empirically, we determine that the Admin Tools website is running there.

The functionality of this site turned out to be inoperative. It contained utilities that facilitate the work of the system administrator. The tool tip to the submission form was found indicating that the SSH key was loaded, suggesting that the file could be located on this server. After studying the site structure and html-code, nothing useful was found, so it was decided to scan the site directories with the dirb utility.

A .bash_history file was found. This file contains the history of commands that were executed in the console, for example, via SSH. In this file, the name of the SSH private key was found - ssh_key.priv, which was immediately downloaded from the site.

Now we have data for access to the internal network of the company SecureSoft LLC through port 22 using ssh. Also, in the ssh_key.priv file you can find the token to the Admin Tools task.
Cyberattack world map

Especially for the launch of the 7th laboratory, a global attack map was implemented. Visualization of the attacks allowed to see the geography of the participants. According to the data at the time of this writing, specialists from 63 countries and 194 cities took part in the laboratory. The largest number of participants was from Russia (322 IP), followed by the United States (64 IP) and closes the top three Ukraine (37 IP). Moscow is in the lead in the rating of unique IP by cities (242 addresses), Kiev is in second place (25 addresses) and Petrozavodsk is in third place (18 addresses).
Full list of participating countries: Algeria, Andorra, Armenia, Australia, Austria, Belarus, Belgium, Bosnia and Herzegovina, Brazil, Bulgaria, Canada, Chile, China, Croatia, Cyprus, Czech Republic, Denmark, Egypt, Estonia, Finland, France, Georgia, Germany, Greece, Hong Kong (SAR), Hungary, India, Israel, Israel, Israel, Japan, Kazakhstan, Korea, Korea, Lithuania, Mexico, Moldova, Norway, Pakistan , Panama, Philippines, Poland, Portugal, Romania, Russia, Slovenia, Spain, Sweden, Syria, United Kingdom, United States, Uzbekistan, Zambia.
On the other side of the barricades. Organizer Comments
Work on the laboratory, as we have already done, is carried out in several stages:
1. Proposal and discussion of ideas for assignments.
2. Implementation of the bench version of the task, verification.
3. "Finishing" to the final version.
4. Combining into a common scenario.
In order to avoid problems during the launch of the laboratory, in the implementation of tasks are always taken into account:
- the fact of simultaneous execution of the task by more than one participant;
- not all participants are “white and fluffy”. It is necessary to exclude the possibility of vandalism or attempts to impede access to other participants.
In some cases, when the task requires complete control over the system, but it is so interesting that you want to include it in the laboratory, you have to make some compromise. Then we try to minimize the risks. For example, to provide for a script to restrict access for the minimum number of participants simultaneously.
Of course, it is very interesting to watch attacks in real time, being “on the other side”. In this laboratory, we did not use any intrusion detection systems, so the participants did not have any limitations in this regard. But, based on observations, the presence of such a system would reflect most of the attacks. Perhaps in the next lab we will include IDS / IPS bypass tasks.
Most port scans, brute force, directory scans, etc. it was made publicly available with the default settings: the nmap scripting engine and the DirBuster in the User-Agent, for example. On one of the tasks, we left two options for passing, but the second allowed us to prevent others - so we decided to see which option the participants would prefer. Unfortunately, as it was supposed, vandalism began after some time :)
At first, we decided to play along and imitate the presence of the administrator, who is trying to figure out what is happening and close the holes. For about an hour, the connections to the shelters were interrupted, deleted them and in every way interfered, but not closing the very possibility of exploitation. Then, nevertheless, the alternative option had to be closed, because some unscrupulous participants constantly tried to remove the token itself, making it difficult for others to complete this task - apparently, this exercise gave them more pleasure than going through the lab itself.
Comments of participants
Thank you very much for creating the laboratory. All the tasks were interesting, although the decision of some was not obvious. Most liked the task "ssh": it was very exciting to try to understand what was the vulnerability. As a result, the laboratory is a great opportunity to get new knowledge and put into practice the existing ones.
MERRON
About the laboratory I can say that it was very interesting, some tasks were very difficult. Since I love the web most of all, I would like to mention the task called “forum”, a rather interesting idea, and a very cool implementation) I want to wish good luck and development to the whole team, well, thank you very much for the laboratory, I will wait for the following laboratories.
Darkcat
I hope the collective work of the authors of the article was not in vain and it turned out to be useful. I will be glad to consider all the wishes and comments in the drug. Have a nice day, everyone!
References:
Laboratory "Test lab v.7" | Discussion | Attack Map | Hall of FameSource: https://habr.com/ru/post/257675/
All Articles