How 3CX solves security problems (part 2)
Part 1
Passive safety
The module of passive protection, we will conditionally consider those components that simply close some possibilities and if you don’t touch these settings, everything will be fine.
So, the first is the default passwords generated by complex ones - 8 characters, such as 96q1d4h2. If you do not be lazy and prescribe them, then the probability of selection (especially if the Antihacking described in the first part works) is almost zero. By the way, for those who are lazy to write passwords, there is Autoprovisioning.
The second is that all new subscribers, by default, cannot connect outside the local network. Connection via 3CX Tunnel is also blocked.
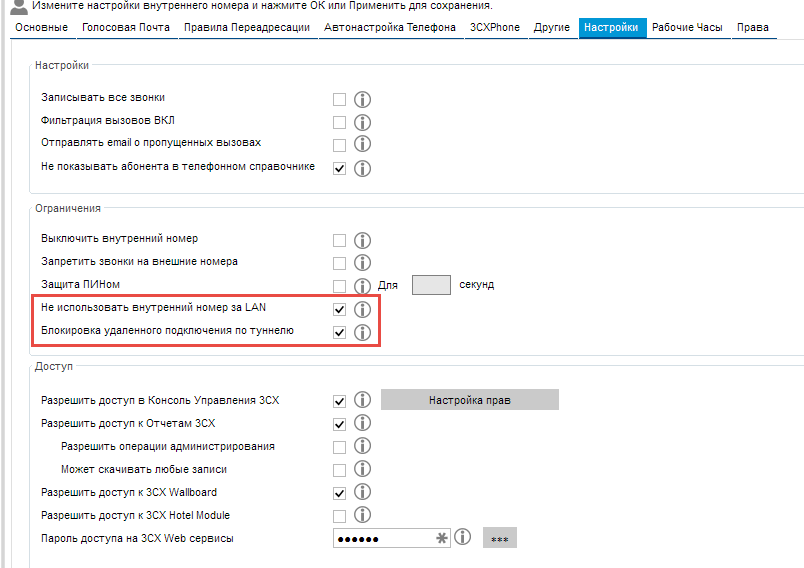
')
Subnets from which you can connect without additional permission are configured.
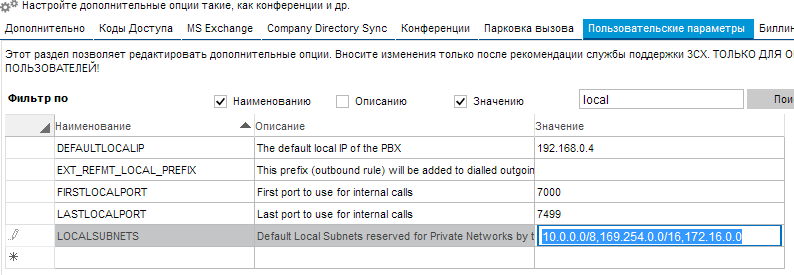
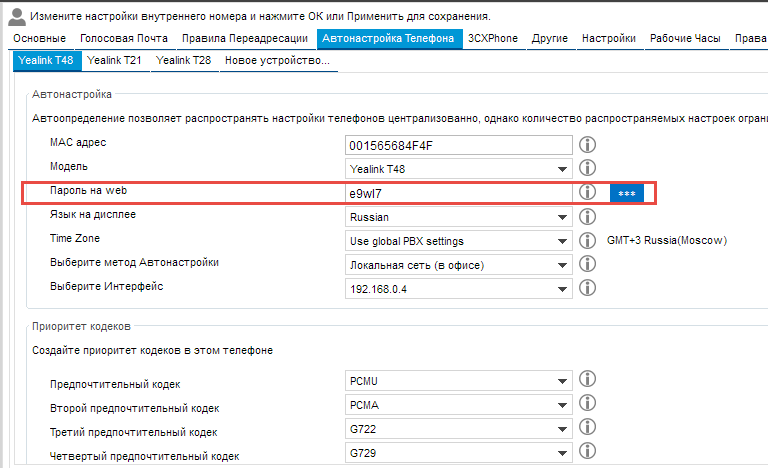
Now as for the IP phones themselves, at every second login / password is admin-admin. In a situation when this device sticks out via the web interface to the open Internet, you can easily access the webcam, download the config of the phone, get the password from there and you can call. By the way, this is an example from real life 2 years ago, the phone was Yealink and stood alone on the remote. Yealink now encrypts configuration files, but is not sure that all manufacturers do this.
So, if you go according to the mind and set up devices via Autoprovisioning, then the password for the webcam will also be generated complex.
Foolproof
Display weak passwords.

In the event that, after all, someone has thought of putting the login password 100-100, 3CX will warn about this, the number with potentially dangerous settings will be displayed in red. There are no locks at all.
An indication will also appear if the number and SIP ID match in the settings.

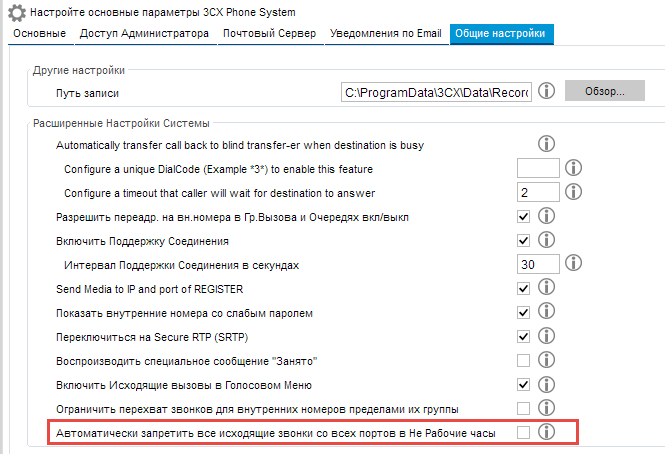
Working hours can also be considered as protection, a simple example, at night cleaning companies with employees from neighboring countries work in many offices. Call home from the office apparatus is quite a big temptation. During non-business hours, calls to the city can be turned off altogether. For special cases, there is a cancellation code, in addition there is a list of emergency numbers where you can add any numbers.
About calls from IVR
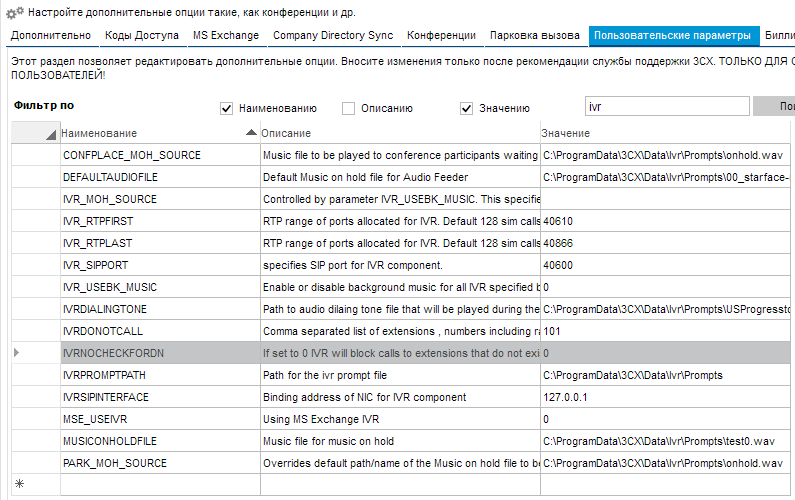
Another way to catch up on left-wing traffic is to call an IVR and dial an external number instead of an extension. In 3CX, there is a forced blocking on transferring a call to numbers that do not exist as internal ones.
Third-party funds
This is the last barrier, in the event that you already hacked. Internal billing with AntiFraud system and the ability to block numbers. For 3CX, Tariscope 3.5 is able to do such things. In addition to the usual counting of money spent on calls, Tariscope analyzes the traffic in real time (and not after unloading the CDR) and can forcibly break the connection when the balance of a particular subscriber is cleared, and then forcibly disconnect it.
What can not be protected
In my practice, once there was a case from which it was impossible to defend oneself, at least with one’s own strength. Apparently, at the height of competition, one company that provides car registration services set a caller through Skype on its competitor. Every 3-5 seconds a call arrived and scored lines, in theory it was possible to put the number on the black list and forget, but the numbers were determined different each time.
The problem was solved only through the intervention of a telecom operator.
If all the recommendations are followed, the probability of losing all the money on the personal account of the telecom operator is reduced to zero. Good luck!
Passive safety
The module of passive protection, we will conditionally consider those components that simply close some possibilities and if you don’t touch these settings, everything will be fine.
So, the first is the default passwords generated by complex ones - 8 characters, such as 96q1d4h2. If you do not be lazy and prescribe them, then the probability of selection (especially if the Antihacking described in the first part works) is almost zero. By the way, for those who are lazy to write passwords, there is Autoprovisioning.
The second is that all new subscribers, by default, cannot connect outside the local network. Connection via 3CX Tunnel is also blocked.

')
Subnets from which you can connect without additional permission are configured.

Now as for the IP phones themselves, at every second login / password is admin-admin. In a situation when this device sticks out via the web interface to the open Internet, you can easily access the webcam, download the config of the phone, get the password from there and you can call. By the way, this is an example from real life 2 years ago, the phone was Yealink and stood alone on the remote. Yealink now encrypts configuration files, but is not sure that all manufacturers do this.
So, if you go according to the mind and set up devices via Autoprovisioning, then the password for the webcam will also be generated complex.

Foolproof
Display weak passwords.

In the event that, after all, someone has thought of putting the login password 100-100, 3CX will warn about this, the number with potentially dangerous settings will be displayed in red. There are no locks at all.

An indication will also appear if the number and SIP ID match in the settings.

Working hours can also be considered as protection, a simple example, at night cleaning companies with employees from neighboring countries work in many offices. Call home from the office apparatus is quite a big temptation. During non-business hours, calls to the city can be turned off altogether. For special cases, there is a cancellation code, in addition there is a list of emergency numbers where you can add any numbers.

About calls from IVR
Another way to catch up on left-wing traffic is to call an IVR and dial an external number instead of an extension. In 3CX, there is a forced blocking on transferring a call to numbers that do not exist as internal ones.

Third-party funds
This is the last barrier, in the event that you already hacked. Internal billing with AntiFraud system and the ability to block numbers. For 3CX, Tariscope 3.5 is able to do such things. In addition to the usual counting of money spent on calls, Tariscope analyzes the traffic in real time (and not after unloading the CDR) and can forcibly break the connection when the balance of a particular subscriber is cleared, and then forcibly disconnect it.
What can not be protected
In my practice, once there was a case from which it was impossible to defend oneself, at least with one’s own strength. Apparently, at the height of competition, one company that provides car registration services set a caller through Skype on its competitor. Every 3-5 seconds a call arrived and scored lines, in theory it was possible to put the number on the black list and forget, but the numbers were determined different each time.

The problem was solved only through the intervention of a telecom operator.
If all the recommendations are followed, the probability of losing all the money on the personal account of the telecom operator is reduced to zero. Good luck!
Source: https://habr.com/ru/post/257673/
All Articles