Attackers use Linux / Mumblehard to compromise servers, part 1
The Linux / Mumblehard malware family is a special attacker’s tool that compromised servers running various Linux and BSD modifications. The main purpose of this malware is to provide full access to the compromised system for intruders (backdoor) and send spam. After gaining such access, attackers can run other malicious programs on the remote system. Mumblehard also includes modules for organizing proxies and spam.

The components of this malware are Perl scripts that are encrypted and packaged inside an executable ELF file. In some cases, these scripts may contain another ELF executable file.
')
ESET analysts were able to perform a sinkhole operation to obtain statistics on infected systems, which allowed us to calculate their number and notify their owners. Our analysis led us to the following key findings:
Introduction
Our analysts encountered Linux / Mumblehard when a system administrator of one of the companies contacted our specialists to get advice on their server, which was blacklisted by the provider for sending spam. On this server, we recorded a suspicious process and dumped its memory. The process was a running Perl interpreter. This process executed a malicious script. We also found a suspicious ELF file in the / tmp directory. During the analysis it became clear that this file belongs to Linux / Mumblehard .
The attention of our analysts was attracted by the fact that the Perl malicious scripts themselves were located inside the executable ELF file, which is a rather unusual case of their storage. Our investigation revealed that the group of cybercriminals behind this malware had close ties with an IT company called Yellsoft. The first sample of the Mumblehard component responsible for sending spam was uploaded to the VirusTotal service back in 2009. At the same time, Yellsoft has been working since 2004. It is not clear to us whether this company had connections with attackers from 2004 to 2009 .

Fig. Yellsoft homepage, how it looked in 2004
Using our special server and the list of systems that have been infected, we have established two main vectors for the distribution of this malware. One such vector was the use of exploits by attackers for popular content management systems for Joomla and Wordpress sites. Another vector was the distribution by the attackers of pirated backdoored versions of the DirectMailer program for Linux & BSD. This program is sold by Yellsoft for $ 240. Pirated copies of the program specialize in installing the Mumblehard backdoor. The backdoor allows attackers to install other malicious programs on a compromised server.
Malware Analysis
We analyzed two different malware components that were used by a group of intruders. The first is a backdoor that will request commands from the C & C server manager. Command data contains URLs. They must be downloaded and executed on a compromised server. The second component is a spam component, the so-called. spammer daemon. Both components are written in Perl and obfuscated using the same packer, which is written in assembler and located in the ELF file. Below is a diagram showing the connections between the Mumblehard components and their control servers.

Fig. The interaction between the components of Mumblehard and their control servers.
One of the first interesting features that we noticed is the Perl script wrapper located inside the ELF file. It is written in assembler and consists of two hundred instructions. This code itself calls the Linux system services by using the int 80h instruction. The software functions of the packer are also deprived of the usual prologue responsible for servicing the stack.
Using the int 80h system call gives the packer code one significant advantage, depriving it of any external dependencies on the OS libraries. In addition, the packer itself can work normally on both Linux and BSD. The system type is determined at the beginning of the malware code by system call number 13 with an argument of 0. For Linux, this corresponds to the API call of the time function (NULL) , and on BSD the fchdir (stdin) call. In the case of BSD, a function call with this argument will fail and the return value will be a negative number, and in the case of Linux, the return value of the corresponding call will be positive, and it corresponds to the number of seconds since January 1, 1970.
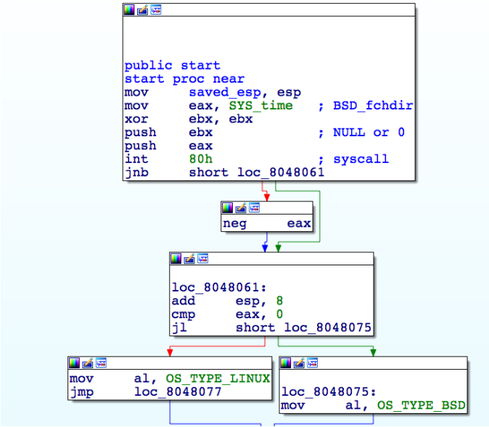
Fig. Entry point to the executable ELF file (beginning of the packer code). The service call with ID 13 (SYS_TIME) is visible.
Next, the malicious code will call the fork () function and start the Perl interpreter by calling execve ("/ usr / bin / perl", ...) . The body of the script itself will be sent to the interpreter process via the STDIN channel. Using the dup2 system call, the parent process will be able to transfer the decrypted script to the interpreter process via the duplicated file descriptor.
The backdoor itself performs simple work, it requests commands from the C & C server manager and reports the results of their execution to it. The backdoor does not start in the system as a service (daemon); instead, it uses the crontab task scheduler, which ensures that it runs every 15 minutes.

It also disguises itself as an httpd service.

At each launch, the backdoor polls all the C & C servers in the list to receive commands. In fact, it supports only one command with the identifier 0x10, which instructs the backdoor to download from the URL of the specified file and its subsequent execution in the system. As a rule, the list of C & C servers consists of ten addresses. The list we discovered was identical for all the Linux / Mumblehard samples we observed. We witnessed the activity of only one C & C server with the IP address 194.54.81.163. One of the servers with the domain behance.net in 2005 belonged to Adobe.
When the server with the address 194.54.81.163 contains a command to send, it can respond only in a fixed period of time.
The backdoor generates its HTTP GET request for each C & C server from the list. The server responds with a command that is masked in the Set-Cookie field of the HTTP header. Such a technique can be justified, since analyzing such a network packet, its analysis will not arouse suspicion.

Fig. Sample C & C Server Response.
The cookie parameter called PHPSESSID is encoded in hexadecimal. Strings within the commands themselves are also encrypted using a special algorithm. This algorithm is identical to the one used in the Perl script wrapper. It can be assumed that the same group or person was behind the development of both parts of the malware code.
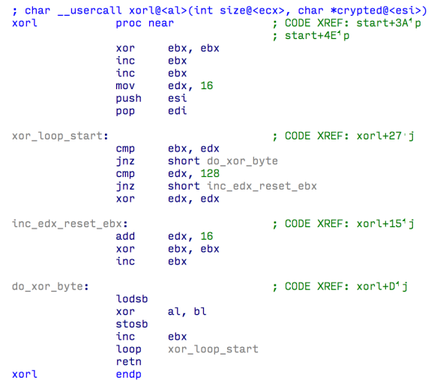
Fig. The function of decrypting the data of the command received from the C & C server.

Fig. The same decoding function in Perl.
Once the string has been decrypted, the following information will be extracted from the cookie.

Tab. Parameter list inside PHPSESSID cookie.

Tab. Example of parameter values inside PHPSESSID.
When requesting a command from a C & C server, the backdoor uses a hardcoded user agent string. The line is listed below and corresponds to the one used by Mozilla Firefox 7.0.1 on Windows 7.

After the file download to the URL and its execution are completed, the backdoor reports the status of the operation to each of the C & C servers from which the command was received. This information is masked inside the user agent string and has the following form.

The following figure shows an example of the user agent string that the backdoor sends when a successful (HTTP 200 OK) operation (download-and-execute) with code 0x18 (24) is executed to execute a file of 56,013 bytes.


The components of this malware are Perl scripts that are encrypted and packaged inside an executable ELF file. In some cases, these scripts may contain another ELF executable file.
')
ESET analysts were able to perform a sinkhole operation to obtain statistics on infected systems, which allowed us to calculate their number and notify their owners. Our analysis led us to the following key findings:
- The Linux / Mumblehard malware modules are Perl scripts, they are located in the Mumblehard executable ELF files, which are written using assembler.
- Using the sinkhole, it was possible to identify 8,867 unique IP addresses of the infected systems over a seven-month period.
- The largest number of such unique IP addresses per day was 3.292.
- The malware has been active since at least 2009.
- Web servers dominated all infected computers.
- There is a close relationship between Mumblehard and Yellsoft. The latter is a company that distributes software for mass mailing e-mails.
Introduction
Our analysts encountered Linux / Mumblehard when a system administrator of one of the companies contacted our specialists to get advice on their server, which was blacklisted by the provider for sending spam. On this server, we recorded a suspicious process and dumped its memory. The process was a running Perl interpreter. This process executed a malicious script. We also found a suspicious ELF file in the / tmp directory. During the analysis it became clear that this file belongs to Linux / Mumblehard .
The attention of our analysts was attracted by the fact that the Perl malicious scripts themselves were located inside the executable ELF file, which is a rather unusual case of their storage. Our investigation revealed that the group of cybercriminals behind this malware had close ties with an IT company called Yellsoft. The first sample of the Mumblehard component responsible for sending spam was uploaded to the VirusTotal service back in 2009. At the same time, Yellsoft has been working since 2004. It is not clear to us whether this company had connections with attackers from 2004 to 2009 .

Fig. Yellsoft homepage, how it looked in 2004
Using our special server and the list of systems that have been infected, we have established two main vectors for the distribution of this malware. One such vector was the use of exploits by attackers for popular content management systems for Joomla and Wordpress sites. Another vector was the distribution by the attackers of pirated backdoored versions of the DirectMailer program for Linux & BSD. This program is sold by Yellsoft for $ 240. Pirated copies of the program specialize in installing the Mumblehard backdoor. The backdoor allows attackers to install other malicious programs on a compromised server.
Malware Analysis
We analyzed two different malware components that were used by a group of intruders. The first is a backdoor that will request commands from the C & C server manager. Command data contains URLs. They must be downloaded and executed on a compromised server. The second component is a spam component, the so-called. spammer daemon. Both components are written in Perl and obfuscated using the same packer, which is written in assembler and located in the ELF file. Below is a diagram showing the connections between the Mumblehard components and their control servers.

Fig. The interaction between the components of Mumblehard and their control servers.
One of the first interesting features that we noticed is the Perl script wrapper located inside the ELF file. It is written in assembler and consists of two hundred instructions. This code itself calls the Linux system services by using the int 80h instruction. The software functions of the packer are also deprived of the usual prologue responsible for servicing the stack.
Using the int 80h system call gives the packer code one significant advantage, depriving it of any external dependencies on the OS libraries. In addition, the packer itself can work normally on both Linux and BSD. The system type is determined at the beginning of the malware code by system call number 13 with an argument of 0. For Linux, this corresponds to the API call of the time function (NULL) , and on BSD the fchdir (stdin) call. In the case of BSD, a function call with this argument will fail and the return value will be a negative number, and in the case of Linux, the return value of the corresponding call will be positive, and it corresponds to the number of seconds since January 1, 1970.

Fig. Entry point to the executable ELF file (beginning of the packer code). The service call with ID 13 (SYS_TIME) is visible.
Next, the malicious code will call the fork () function and start the Perl interpreter by calling execve ("/ usr / bin / perl", ...) . The body of the script itself will be sent to the interpreter process via the STDIN channel. Using the dup2 system call, the parent process will be able to transfer the decrypted script to the interpreter process via the duplicated file descriptor.
The backdoor itself performs simple work, it requests commands from the C & C server manager and reports the results of their execution to it. The backdoor does not start in the system as a service (daemon); instead, it uses the crontab task scheduler, which ensures that it runs every 15 minutes.

It also disguises itself as an httpd service.

At each launch, the backdoor polls all the C & C servers in the list to receive commands. In fact, it supports only one command with the identifier 0x10, which instructs the backdoor to download from the URL of the specified file and its subsequent execution in the system. As a rule, the list of C & C servers consists of ten addresses. The list we discovered was identical for all the Linux / Mumblehard samples we observed. We witnessed the activity of only one C & C server with the IP address 194.54.81.163. One of the servers with the domain behance.net in 2005 belonged to Adobe.
- 184.106.208.157
- 194.54.81.163
- advseedpromoan.com
- 50.28.24.79
- 67.221.183.105
- seoratingonlyup.net
- advertise.com
- 195.242.70.4
- pratioupstudios.org
- behance.net
When the server with the address 194.54.81.163 contains a command to send, it can respond only in a fixed period of time.
The backdoor generates its HTTP GET request for each C & C server from the list. The server responds with a command that is masked in the Set-Cookie field of the HTTP header. Such a technique can be justified, since analyzing such a network packet, its analysis will not arouse suspicion.

Fig. Sample C & C Server Response.
The cookie parameter called PHPSESSID is encoded in hexadecimal. Strings within the commands themselves are also encrypted using a special algorithm. This algorithm is identical to the one used in the Perl script wrapper. It can be assumed that the same group or person was behind the development of both parts of the malware code.

Fig. The function of decrypting the data of the command received from the C & C server.

Fig. The same decoding function in Perl.
Once the string has been decrypted, the following information will be extracted from the cookie.

Tab. Parameter list inside PHPSESSID cookie.

Tab. Example of parameter values inside PHPSESSID.
When requesting a command from a C & C server, the backdoor uses a hardcoded user agent string. The line is listed below and corresponds to the one used by Mozilla Firefox 7.0.1 on Windows 7.

After the file download to the URL and its execution are completed, the backdoor reports the status of the operation to each of the C & C servers from which the command was received. This information is masked inside the user agent string and has the following form.

The following figure shows an example of the user agent string that the backdoor sends when a successful (HTTP 200 OK) operation (download-and-execute) with code 0x18 (24) is executed to execute a file of 56,013 bytes.

Source: https://habr.com/ru/post/257109/
All Articles