Vulnerability in proftpd CVE-2015-3306
Recently it was discovered that some of the sites were cracked and web shells were flooded. The study of hacking revealed that the reason lies in proftpd.
A search on this topic revealed that recently ( 04/10/2015 ) a vulnerability was identified under the number CVE-2015-3306 (Debian, Red Hat, Ubuntu, Gentoo, more) .
Source: http://bugs.proftpd.org/show_bug.cgi?id=4169
For example, the situation with debian:
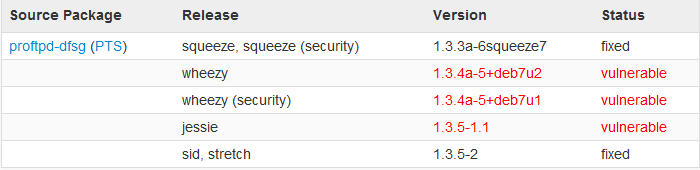
Ie, at the moment, all current debian versions are vulnerable. And since the update has not yet fallen into the current stable repositories, it is possible to eliminate the vulnerability by updating proftpd from the sid repository.
Starting from 1.3.5-2, the problem is fixed.
Check what version you have, for example (in debian), like this:
Description from securitylab.ru:
A search on this topic revealed that recently ( 04/10/2015 ) a vulnerability was identified under the number CVE-2015-3306 (Debian, Red Hat, Ubuntu, Gentoo, more) .
Source: http://bugs.proftpd.org/show_bug.cgi?id=4169
For example, the situation with debian:

Ie, at the moment, all current debian versions are vulnerable. And since the update has not yet fallen into the current stable repositories, it is possible to eliminate the vulnerability by updating proftpd from the sid repository.
Starting from 1.3.5-2, the problem is fixed.
Check what version you have, for example (in debian), like this:
sh: ~ # aptitude -F "% p |% v |% V" search ~ V | grep proftpd
proftpd-basic | 1.3.5-1.1 | 1.3.5-1.1
Description from securitylab.ru:
Unauthorized data modification in ProFTPD
')
Vulnerable versions:
ProFTPD 1.3.5, possibly earlier versions
Description:
Vulnerability allows a remote user to change data without authorization.
Vulnerability exists due to access control error in mod_copy module. A remote user can copy arbitrary files without authentication.
Source: https://habr.com/ru/post/257027/
All Articles