Car Hacking: Are car safety systems safe?

Cars are overgrown with a huge amount of electronics, starting with the speedometer and ending with the brake system controller. All these devices are connected to a single local area network, which gives room for attempts to get into it and settle down a bit. In this article I will tell you how the average car is arranged, and I will try to sow in you paranoia and fear (smile).
What for?
The question is actually quite relevant. The Internet is full of materials on the topic "hack the car", there is even a clear manual for the study of your car. Some enthusiasts answer the question “why?”: “Because I can”, but forget to mention that it is very dangerous. The onboard system of the car is a rather fragile thing, despite all the responsibility assigned to it. Failures in the onboard system can lead to both domestic and legal problems, as well as to human victims. If you are not sure about your actions, do not try to interfere with the operation of the car. In the world media, there are many examples of failures of the on-board auto system, which lead to brake failure (for some reason, the most vulnerable part, judging by the media, and perhaps just the most tasty food for journalists), and this is without any (and is it?) interventions by hackers.
Be alert
The main thing that drives the attacker, is the thirst to seize your property: from the values inside the car to the car itself. To implement this venture, you must either get into the car while it is empty, or force the owner to leave his car in a secluded place where to do his dirty work. How to make the driver get out of the car? For example, tell the on-board computer that tire pressure is much lower than normal. Normally, 99% of car owners will stop to go out and see what's wrong. However, there were also shrewd drivers who, having swept along the “hedgehogs” on the highway in the middle of the forest, traveled several miles on the disks, saving their lives and cars. Be vigilant and careful if your car suddenly broke down in a deaf place. Perhaps this is no accident.
Introduction
Cars for negligible time passed a huge scale of technological progress. Today, almost any car is stuffed with electronics so much that there is almost no room left for the usual “analog” mechanisms connecting directly the driver and the car. All these "electronic" power steering, traction control, brake system, accelerator pedal - all this is controlled by a computer.
Cars are gradually overgrown with various buns and lotions for the comfort of the driver and passengers, which creates new dangers of penetration into the network of on-board electronics. With the advent of wireless channels of communication with the car (Bluetooth headset, Wi-Fi), the hacker range has expanded significantly. In this article we will not directly affect the options for penetration through wireless channels, and look in the direction of wired technology.
')
For the automotive industry, microcontroller manufacturers produce individual special product lines. And they do it quietly, on special orders, and for the general public (and narrow too) such products are not available. The main features of such controllers:
- specific set of peripherals;
- encrypting firmware and decrypting code on the fly at runtime;
- multi-core with built-in shared memory and shared access to this memory.
The firmware code is attempted to be protected from disassembling, reverse engineering and, as a result, microcontroller flashing. However, in addition to the possibility of direct "poisoning" of the firmware, there is one global problem. The car, as I said, just stuffed with electronics. All this silicone (oops, of course, silicon :)) army of microcontrollers must somehow communicate with each other, as well as interact with the person (driver, passenger) and external factors. To ensure these dialogues between the controllers in the car there is a real internal network.
At first, as in any industry, for quite a long time every car builder made his own garden and went his own way. But, as is usually the case, auto builders wanted to install third-party modules made by the same craftsmen. So it became necessary to standardize hardware and software protocols. The main to date has been the physical CAN protocol (although there are many variations of this CAN as well).
Network structure
Not so long ago, the main task assigned to the on-board car system was to align the sensors at the control points (fuel level, oil temperature) and display the status on the dashboard. These were mostly independent devices that were assembled on a central unit with a huge bundle. As you understand, the analysis of a single signal is two wires, the control of one actuator is also two wires (Fig. 1).
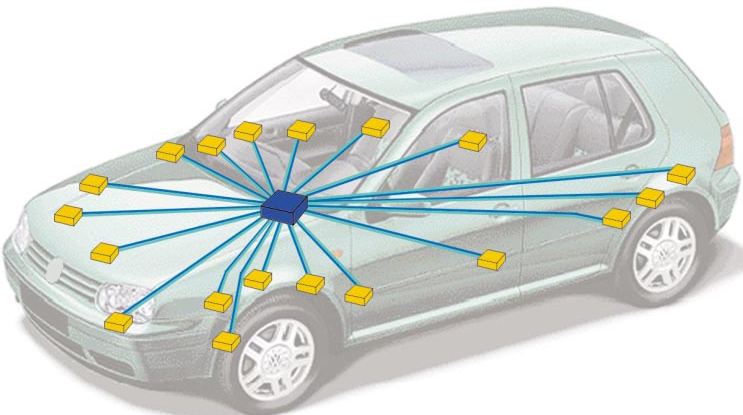
Fig. 1. One central control unit
But over time, automotive electronics management systems became more complex, and automakers began to allocate functional blocks. In this situation, the same sensors are used by different functional blocks, which entails a nightmare, as in Fig. 2
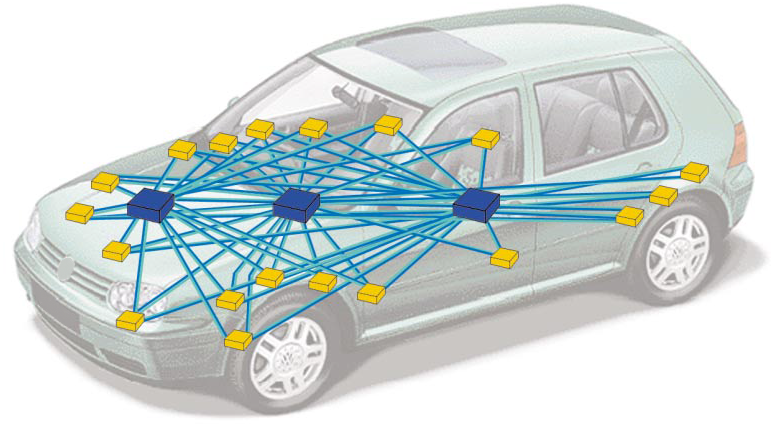
Fig. 2. Three functional blocks
The solution is to merge everything into a network. In this case, each functional unit polls the sensors “native” to it, and upon request it can give the measurement results to the “neighbors” (or sends it in the “beacon” mode) and also transmit a control command from the “neighbor” to the “native” sensor.
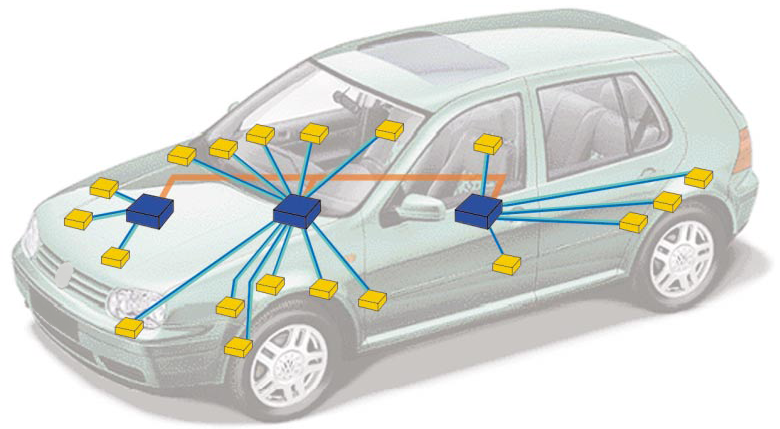
Fig. 3. Three functional units networked
It would seem that the peak of evolution, but there is a question-problem: there are control units and monitoring of critical parameters (for example, brakes or ABS). There are also comfort blocks (air conditioning, window control). If at the same time traffic for air conditioner and brakes starts to go along one bus, then it may happen that you make the last time in your life cooler. To resolve this situation, the tires are physically separated, and for critical systems, data is exchanged at higher speeds.
But still, this is a network, which means that you need to switch the buses together. To do this, use a gateway (CAN gateway), which actually performs the functions of such an ordinary Ethernet network router:
- logical bus interconnection (media converter);
- arbitrates traffic by severity level (QoS);
- It is a firewall and does not allow traffic to the bus that is not intended for this bus (in fact, it is a firewall);
- has a port for connecting diagnostic equipment.
As already mentioned, there are sensors and control units of nodes of varying degrees of criticality for the life of the car. I will highlight three main groups:
- Nodes requiring real-time response. Engine management, braking system, ABS, electric power steering, airbags and so on. Common name will be used ECU-BUS (Engine Control Unit).
- Nodes with an average level of reaction time. Central locking, parking sensors, outdoor lighting (lights, turn signals), tire pressure sensors. We will call further MS-BUS (Middle Speed Bus).
- Nodes of secondary importance. Navigation system, multimedia system and other buns. We will call LS-BUS (Low Speed Bus).
This graduation is not official, different manufacturers add their divisions of control units into groups, but this is enough for you and me.
Besides the fact that ECU-BUS data has a high priority on the so-called common “virtual” car tire, inside this group data is transmitted at a very high speed (it is still desirable to start braking as soon as possible after the driver has made a decision about it, but Throw the airbag is desirable before the driver's nose reaches the steering wheel). In some cars, MS-BUS and LS-BUS are combined, which introduces additional security problems (after all, it turns out that the central lock “hangs” on the same bus as the radio tape recorder).
INFO
Different automakers follow different standards; What specific standard is used in your car, you can easily find on the Internet.
CAN bus communication
Physical level
CAN is an acronym for the Controller Area Network, that is, a specially designed network for exchanging data between different controllers. It is used not only in the automotive industry, but also in many automation systems.
The CAN bus is a two-wire interface, that is, only two signal lines are sufficient for data exchange:
- CAN +, CANH, CAN HIGH - positive pulse signal;
- CAN-, CANL, CAN LOW - signal of a negative impulse.
I chose the terminology for a reason, since the interface is differential. That is, 0 is transmitted via two lines at once, a positive impulse is sent via CAN +, and CAN is simultaneously negative via CAN- (see the oscillogram of data exchange on the CAN bus). This method of physical data transmission is allowed to deal with noise on the line (noise distorts the equally positive and negative signal component).
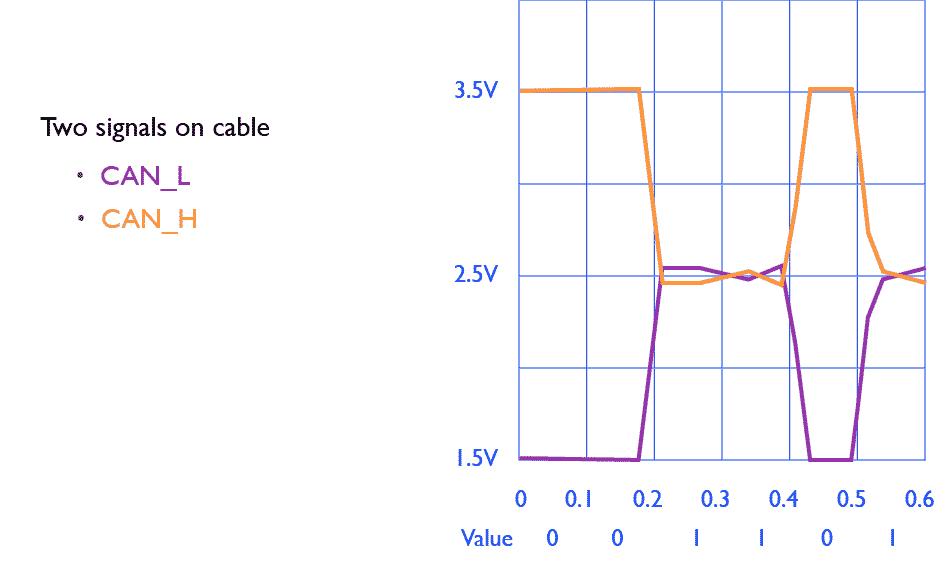
Fig. 4. Oscillogram of data exchange via CAN bus
The reference voltage is 2.5 V (remember this value), 0 is called the dominant bit, 1 is recessive. Why dominant? Because it is the active signal, and if two devices want to transmit simultaneously one 1 and the second 0, then the receiver will be 0.
So who is still 0, and who is 1
In electrical engineering, it is assumed that 0 is transmitted by the active signal, and 1 is passive. In this connection, confusion may arise when you see a physically (measured by a multimeter, an oscilloscope) on the line, it would seem to be 0, but logically it is 1. A bit simpler - the “hanging passively in the air” interface will produce 0xFF (if the control bits are not used ).
The CAN bus is serial, that is, the bits are transmitted one after the other from the most significant bit to the least significant bit. The concept of bytes to CAN is hardly applicable, and basically they use the term “field”; the field length does not have to be a multiple of a byte (8 bits).
Exchange protocol
Data is exchanged with frames. The frame consists of four main fields:
- the sender's identifier, which is also the basis of data transfer arbitration
- control field;
- data;
- check sum.
Fig. 5. CAN frame diagram
The interface feature is such that the transmitted bit is heard by the CAN receiver. Thus, the correctness of the bit transmission is controlled. This feature allows arbitration on the line between those who want to transfer data.
I will explain. Look at the frame: the transfer goes "from left to right", that is, the identifier leaves first. When transmitting an identifier, the node listens attentively to what is happening on the line. If he passed 1, and suddenly 0 appeared on the line, it would mean that someone of higher priority is trying to transfer his data. In this situation, the transmitter, catching 0 instead of transmitted 1, becomes silent. Thus, the lower the identifier of the transmitting node, the higher its priority.
In fig. 6 depicts the arbitration procedure on the CAN bus. For convenience, we set the identifier length to 8 bits, `node3` has ID> 0x10 (00010000b),` node2` has ID> 0x20 (00100000b), and `node1` has ID = 0x3 (00000011b). As you can see, when `node2` wanted to transfer 1 from its identifier, it was` hammered 'by `node1` and` node3`, therefore `node2` will be silent for the time of frame transmission. A similar situation happened with `node3`, its 1 was scored by` node1` with its own 0. As a result, there was only one `node1`, displacing everyone with its 0 in the identifier.
Fig. 6. CAN line arbitration
Error control
Many controllers keep track of line collisions. If for some reason the two nodes start transmitting at the same time, not paying attention to arbitration (for example, some node got into the middle of sending a frame from another node), then the checksum of the packet does not converge. In this case, the node that reported the error sends a transmission error message to the line. The node that transmitted the frame again tries to transmit it. If the number of consecutive transmission errors reaches a certain limit, the node becomes silent for a certain time. For the automotive network, the central node makes a note that there are problems for such a network node. In addition to the sufferer who could not send the frame, the node that registered the error is also recorded. So it turns out the onboard network fault card. An on-board computer based on this card may decide to refuse the electronics and bring the driver a message about it. For errors in critical lines, the on-board computer may even decide to stop the car in an emergency.
Possible connection points
It's time to look for where we stick. The most desirable connection point is the debug port, OBD (OnBoard Debug). OBD is used to diagnose a car at a workshop.

Fig. 7. Photo OBD connector
Why is it such a tasty place? Now I will explain and even show in the picture. Look at the pinout of the connector:
1. Manufacturer discretion - * GM: J2411 GMLAN / SWC / Single-Wire CAN [12]
* VW / Audi: Switched to whether or not the ignition is on.
* Ford: Infotainment CAN High [12]
2. Bus Positive Line of SAE J1850 PWM and VPW
3. Manufacturer discretion - * Ford: DCL (+) Argentina, Brazil (pre OBD-II) 1997-2000, USA, Europe, etc.
* Ford: Medium Speed CAN-High [12]
* Chrysler: CCD Bus (+) [12]
4. Chassis ground
5. Signal ground
6. CAN-High (ISO 15765-4 and SAE J2284)
7. K-Line of ISO 9141-2 and ISO 14230-4
8. Manufacturer discretion - * BMW: Second K-Line for non OBD-II (Body / Chassis / Infotainment) systems.
9. Manufacturer discretion - * GM: 8192 bit / s ALDL where fitted.
* Ford: Infotainment CAN-Low
10. Bus Negative Line of SAE J1850 PWM only (not SAE J1850 VPW)
11. Manufacturer Discretion - * Ford: DCL (-) Argentina, Brazil (pre OBD-II) 1997-2000, USA, Europe, etc.
* Ford: Medium Speed CAN-Low [12]
* Chrysler: CCD Bus (-) [12]
12. Manufacturer discretion - 13. Manufacturer discretion - * Ford: FEPS - Programming PCM voltage
14. CAN-Low (ISO 15765-4 and SAE J2284)
15. L-Line of ISO 9141-2 and ISO 14230-4
16. Battery voltage
Fig. 8. ODB pinout
Contacts 6 and 14 immediately catch the eye (and not only because they are highlighted in green in the picture). According to the specification, this is CAN + and CAN-, respectively. But that's not all, on pins 3 and 11, as well as 1 and 9, Ford pulled out its internal tires. I focus on this for good reason. Established CAN + and CAN- (6th and 14th pins of the connector) in the general case are not required to connect directly to the vehicle's physical tires. Frequently, the diagnostic controller responds to commands via this bus, or requests go through the gateway, which copes well with the filtering function (including it can filter traffic when the car is moving). The exchange protocol on this bus is standardized, and for compatibility all manufacturers put there diagnostics. But to give access to the rest of the tires no one is obliged to anyone.
CAN can be “felt” in three ways:
- On the OBD connector, you can use a multimeter to “touch” the 2.5 V level (yes, the same reference) relative to the ground (4th and 5th contacts).
- Using a two-channel oscilloscope, you find a twisted pair of wires, you cling onto it with probes and watch the relative signal “do you have cho?” :). With the ignition turned off, as a rule, silence is on CAN, when the ignition is switched on, the on-board electronics begin to “chatter”. You can poke the glass control buttons, lock the doors, saw a “strange” coincidence - you are at the goal (we'll talk about this later).
- The latter is a rather unreliable method, but, as they say, something is better than nothing at all. The resistance of the termination resistor in the CAN line is equal to the characteristic impedance of the wires, and it, in turn, is 120 ohms. Two resistors (one for each end of the line) give 60 ohms between CAN + and CAN-.
Do not forget about the need for 12V power from the vehicle's onboard battery. Most likely, without electricity, you certainly will not stay, but only if the automaker has not done a dirty trick in the form of powering the OBD port only when the key is inserted and the ignition is on.
Also note the following feature: the modern car controls almost everything with the help of controllers. Accordingly, if you study a car of a certain model, you can find the bus wires in the most unexpected places. For example, the cable from the PDC passes close to the rear lights, and access to them can be obtained through the technological opening of the replacement of light bulbs in the headlights.
Under the hood, finding the CAN lines is more difficult, but they are there. Access to the engine compartment is not as easy as car interior, but we will not exclude this option.
We listen and remember
So, you read up to this place, CAN-bus found what's next? Further the most interesting begins.
First, you need an “honest” CAN driver. By driver, I mean a level conversion chip that implements the physical part of the CAN protocol. There are so many on the Internet, there is even a shield for the Arduino CAN-Schield. Why honest, because you can take a conventional chip that converts the logic level of the TTL microcontroller to the CAN bus signal? It is possible, but not necessary. Remember about fixing errors, it’s better to put the whole arbitration and line control on the piece of iron, than to analyze the echo bits from the bus yourself (it’s also not so easy to do because of the high speeds on the bus), to make a mistake somewhere and eventually give yourself away by scoring the counter mistakes. This advice, of course, is relevant only if the goal is not to drive the driver to insanity by littering the CAN bus and raising the error counter on the line :).
Further two options:
- Use the search and find on the car a description of the protocol.
- Reverse engineering.
The first way you yourself are able to go, let's go the second. We must somehow connect to the bus. For this, of course, it is better to use a USB or Ethernet-CAN hub. Regular USART (RS232) will definitely not work for you, the speeds are serious, and ordinary microcircuits are simply not designed for them.
Having connected to the bus, start the sniffer. An ordinary terminal will not work for you, there is no RS232 protocol in CAN, and you need to catch raw bit traffic. It is necessary to search a little specialized software on the Internet - it is enough both paid, and free, I will not give references.
The easiest way is to repeat this sequence of actions:
- enable sniffer;
- press the button window;
- stop sniffer;
- play in line overheard;
- watch the result.
That's right, most likely you will fail. This is due to the fact that the traffic will still have to disassemble, find something in common, pull the glass up and down. In general, the usual procedures in the analysis of protocols, except that it will have to work with an unusual format.
Potential attack
CAN Bus Attack
Having run through the above material, we conclude that everything is bad with safety in cars. Everything is very bad. Not so long ago, a review of the hole in SCADA systems was published in the journal. But in order to penetrate into the SCADA system, it is necessary to gain access to the object, after which you physically get into the system (if the system does not have access to the outside world, of course, otherwise everything is simplified). In the car access to the object is much easier to get.
Probably, it will be logical to ask: what was it that a long time to grovel about CAN? The answer to the surface: getting access to the tire (in any form), you get full access to all the electronics of the car in one form or another. This means that you can do almost anything with the engine, brakes, central locking and other nodes connected to the CAN network (or associated with it).
Microcontrollers used in automotive automation contain a hardware encryption module. However, traffic for some reason is not encrypted (at least what I met). True, there is one bonus as opposed to: after all, in some cars, sensors must be registered on the gate.
I will say a few words about the safety of the long-suffering OBD-connector. Its location is hidden from view. But from whose eyes? The user, that is, the car owner. Observe a gadget in the OBD connector is quite problematic. On the Internet, there are a lot of “adapters” for this OBD-connector, which allow using Wi-Fi and Bluetooth to access “diagnostic” data.
OBD connector protection
I have gained enough passion, but what to do, how to save myself? Craftsmen are not asleep, as are engineers - professionals in their field. The first ones offer to buy a special mini-safe for the OBD connector ... with a key ... Yes, you read that correctly, the connector is pulled out of the regular place and locked with a key in a metal box. The second, which are engineers, suggest putting a jumper connected to the ignition, or an electronic key in the ignition circuit. You insert the key into the lock, turn on the ignition - the OBD-connector wires are switched and the connector is functional, the key is pulled out - the connector is “hanging in the air”.
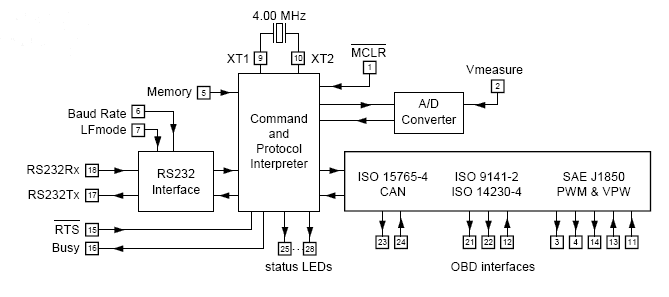
ELM327 Universal Modem
ELM327 block diagram
By dropping a request to Google on the subject of OBD-adapters, you will receive such a number of devices that your eyes run. There are popular, there is not very. On horseback is the company ELM Electronics , which manufactures chips of the ELM series. Based on these chips built most adapters. Chips are a bridge between the USART and OBD ports, at one end are CAN physics, at the other are USART with an AT command interface. The chip receives AT commands, chats with the car on the CAN bus and returns the answer in a universal format. The coolest chip is ELM327, it supports a huge number of protocols, car models, supports adding parameters that are not yet contained in the internal memory. Periodically, there are new versions of this chip, expanding the list of cars and readable parameters. Must have, if you want to make your cool piece of auto diagnostics. One of the nice chips - ELM327 has the ability to work in sniffer mode and show you all the CAN-bus traffic. The microcircuit is produced in two versions: normal power consumption and low power consumption. A less voracious microcircuit also has an insignificant difference in the appointment of one output (for more details, see the datasheet on the manufacturer's website).
INFO
Having connected to the car with a piece of iron, you still want beauty. ELM327-based OBD adapters grow like mushrooms after rain, and the protocol is supported in many applications, the most popular ones are OBD Auto Doctor, DashBoard.
These devices are positioned either as a “toy” (that is, just an additional screen on a mobile gadget that shows speed, fuel level and many more parameters that the on-board computer does not display), or as a convenient way to diagnose or reset errors on the on-board computer of a car without wires. What is there to say? The firmware of this “adapter” is known only to the manufacturer, we have already passed massive bookmarks in the BIOS, and it’s not difficult to assemble the same adapter, since there are only spare parts: a microcontroller, a wireless module, a CAN driver. As a result, by collecting a simple device that receives a Wi-Fi or Bluetooth command, you can open the car. Installing such a “gadget” will not be visible to the owner, and, believe me, there are more than enough opportunities to install it (count in minutes how much your car is open, unattended, and plugging a piece of iron into the connector is a matter of seconds).
While you were looking for CAN bus wires all over the car, you might have noticed the places where this same tire is almost at hand. With a certain skill, hooking a spy on the tire is a matter of the same seconds.
A separate layer are airborne multimedia systems. Listening to the radio is already the last century, now bring cartoons to children on the monitors in the front seats, video passenger, driver navigation, and also it’s good to cross the phone with cars and the Internet in order to read the news and mail in traffic. All these beauties are not easy to get if you make them from scratch, BUT! But in multimedia cars there are operating systems such as Windows, Linux, Android, ported to ARM (there is nothing special about Android). The ARM architecture, of course, complicates life, not all hack chips work the same way as on x86 (or even do not work at all), but there are some special features and bugs. One of the doors to the system is “poisoned” video or sound files, sticking flash drives with autorun (I stumbled once on a system that suddenly decided to start autorun from a flash drive inserted into a USB connector). A separate topic is “CDs for the navigation system” :). For a while, it was a popular way to capture the axis of a car, since the navigation software was really well full of holes.
A nice bonus for a hacker is the ever-growing popularity of newfangled wireless technologies (newfangled for cars). Since these technologies are new to the on-board technology, they are still experiencing a period of still full development (home-based routers have been on the market for many years, and the holes there are one funnier than the other).Published many results of the analysis of the security of wireless connections with the onboard computer, every year they are more comforting, but it is too early to talk about maturity.
Having received access to the multimedia system (if access through the wireless channel is provided only to it), you automatically access the CAN bus (at least some), then the scenario is clear.
Signaling
Howling at night is a boring thing. So the alarm will be called in any city where cars are parked in the yard. Alarms have passed a difficult path of development from ordinary chants, triggered by the closing of the limit switches on the doors and the hood, to whole security systems with a satellite modem.
The main technique of opening the alarm is wiretapping the air. This old technique has not lost its relevance from the time of simple systems with manual coding of the key fob (the binary code was set by switches in the key fob and on the car) to this day. The air is heard during the setting and disarming of the car, the sequence without owner is repeated, the car is opened. Only the systems have become more difficult, more and more the car wants to “chat” with the key fob in order to determine whether it is yours or someone else's, complex algorithms for encoding dialogue sequences between the car and the key fob have appeared. However, reverse engineering has not been canceled, hackers listen, remember, parse the protocol in pieces and open cars. Here, as in the general problem of encryption, the struggle continues to enhance the strength of the cipher in order to make the hacking method more expensive,than the hacking object itself, without having made a data center from the key fob of the alarm system.
, ? , , , , . Why? -, . — . , , . ( ), . . But what is it?And here just comes the factor of reliability of the on-board protection of the car from theft and opening. The more difficult and more stress-resistant electronics in a car is against a hacker's “scrap,” the more reliable the car, the less chance it will be stolen, and the less the insurance company risks its money. I will not poke a finger, but in my memory there is more than one fact, when hackers found an easy way to open the central lock of a car of a certain brand and the insurance amount for these cars immediately took off.
The trend in our time can be called an alarm with a GSM modem and a GPS tracker. Two corresponding attack targets appear here:
- GPS;
- GSM
With GPS, everything is more or less unambiguous: to confuse GPS so that the exit from the security zone does not work, or to “divert” the dummy coordinates of the car in the opposite direction.
GSM . , , — GSM, . keepalive. «» , . GSM, , «». « », , , «» . , . , , . - , . , .
A separate island remains additional protection in the form of an immobilizer. However, if we recall that immobilizers are a regular RFID tag with all its advantages and disadvantages, the attack vector instantly becomes clear.
Instead of conclusion
No matter how much I dramatize here, real car hacking is far from trivial and expensive. Automakers are constantly coming up with some chips to make it impossible to connect to the car's tire, close the holes in the software available to the user. However, hackers are not asleep, the war has already been declared. Adds Google oil to the fire, wanting to release a fully automated Google Mobile. In response to the desire of the “corporation of good”, hackers and skeptics warn that it is probably too early to release an autopilot for a car. The car is not a plane behind ten fences and with a bunch of guards, it’s a living target in every yard. Be attentive, do not let unfamiliar personalities to your property, do not forget to put on the alarm, well, show general vigilance.
WARNING
-, .
WARNING
, , , . ( , ).
INFO
. , , .

«» 03/2015.
: (anton.sysoev@gmail.com)
Subscribe to "Hacker"
Source: https://habr.com/ru/post/256661/
All Articles