CTB-Locker. We decided to pay
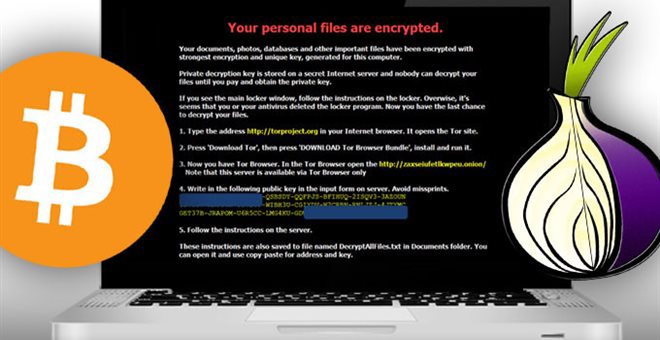
CTB Locker is a very well thought out and dangerous virus. I will not write about it - there is a lot of information about this virus on the Internet.
Over the past 3 months, some of our customers have caught this beast, despite warnings, updated corporate antiviruses and other protection solutions. Some suffered from a separate working machine, while others had a terminal server. But the backup tools saved everyone.
')
The last infection of one of the clients led to the loss of a large amount of data, as well as some backup copies. The responsibility for this lay on the client - funding for the expansion of the backup server could not allocate half a year. But that's not the point. We were given the task of paying the creators of the virus (and then funding was sharply found).
I do not agitate users of the community to pay intruders (I am opposed to this), but perhaps this small manual will help someone.
Next, I will describe step by step how I paid bad people for decoding customer data.
1. So we hit. I got infected with the user's computer (as I got infected - we are still figuring out; there is antispam, there is an antivirus, user rights are curtailed). Over the network, the virus encrypted the file server, the disk of which was connected to the user as a network one. The virus encrypted those folders on the server that had write access to this user. Local disks on the user's computer were also encrypted.
2. When the virus has finished encryption - issued a banner to the user. We were asked to decrypt data for 3.5 Bitcoin, which is approximately $ 805. We were given 90 hours to make a decision.
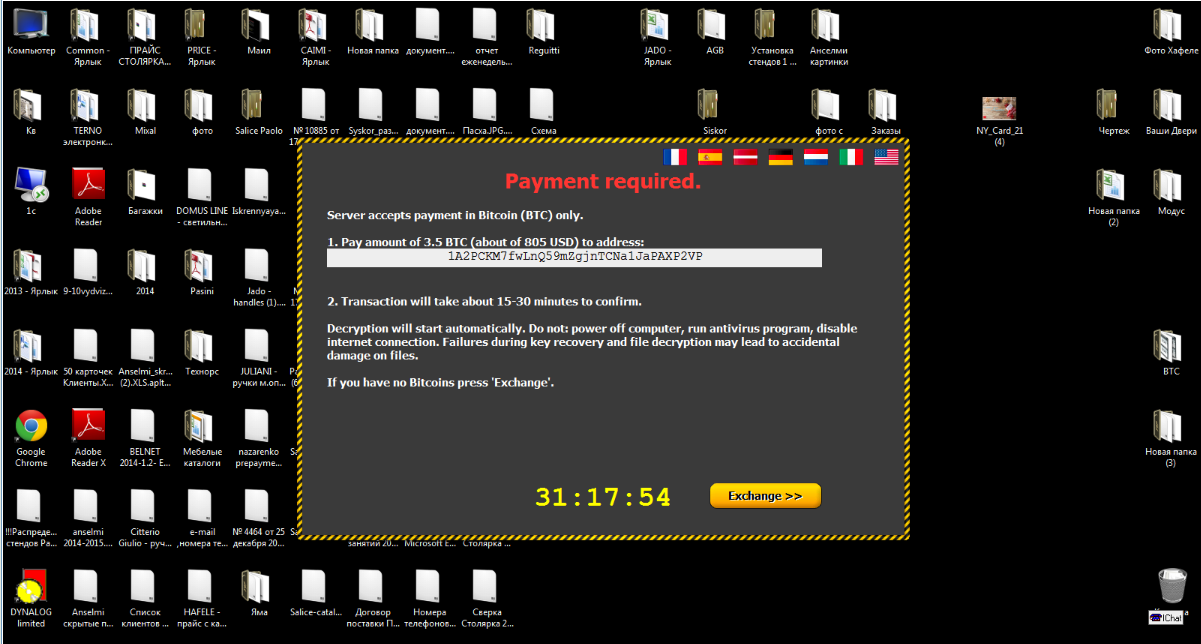
3. On the local disk, in the Documents folder, instructions were found on how to proceed.
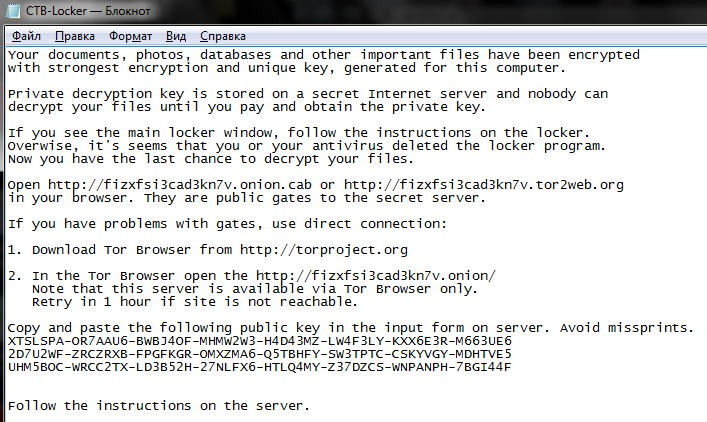
We were asked to go to the Tor-network and enter the public key on this website from this text file. Alas, I did not take a screenshot of the site, the site opens very rarely and I did not see anything new there. The site duplicates information from the banner on the user's desktop: information about the amount of the ransom, links to the site where you can buy bitcoins, wallet number where to transfer, etc., as well as a proposal to decrypt two files up to 1 megabyte each in proof of the possibility of decryption .
4. Before starting all work, the infected user's computer and file server were isolated into a separate network with separate access to the Internet. I checked the availability of a network drive. All OK. Getting started.
5. Search for bitcoins. I did not buy bitcoins before. Sites proposed by attackers to buy Bitcoins did not suit us. We need to buy the crypto-currency with a payment card of a Ukrainian bank (created a virtual card). I went to look for ways to buy cryptocurrency. On the Internet, a Ukrainian Bitcoin buying and selling site was found.
a) register on the site (specify your mobile when registering - confirmation of transactions will be sent to it), we enter UAH to the account.
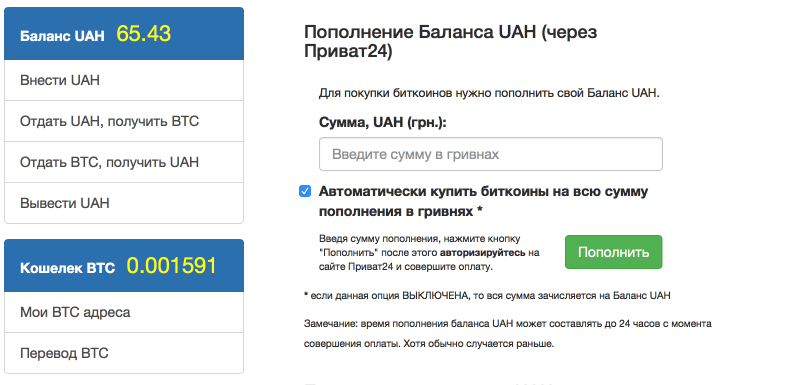
b) Buy bitcoins for the hryvnia.
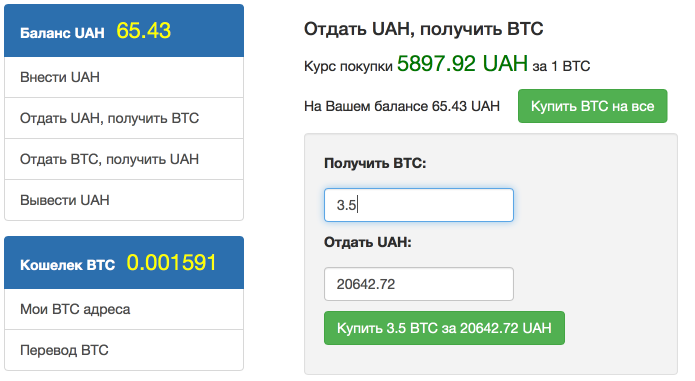
c) We transfer Bitcoins to the wallet specified by the attackers. Pay attention to the commission bitcoin network.

We confirm the transaction via SMS from the phone specified during registration on the site. The transaction took about 10-15 minutes.
6. Waiting. So, we have fulfilled all the conditions of the intruders. What to do next? A site on the Tor network is still not available. As it turned out, we were not deceived. The banner on the user's computer has changed from the money requirement to the information and the fact that our information is now decrypted. Everything happened automatically.

7. Decoding lasted about 2 hours. We check the file server - everything is in place, everything is perfectly decrypted. Banner suggests that we make Rescan in case we forgot to connect a network drive or insert a USB Flash / HDD, which was also previously encrypted, before starting decryption. Or click Close and he will delete himself from the computer.
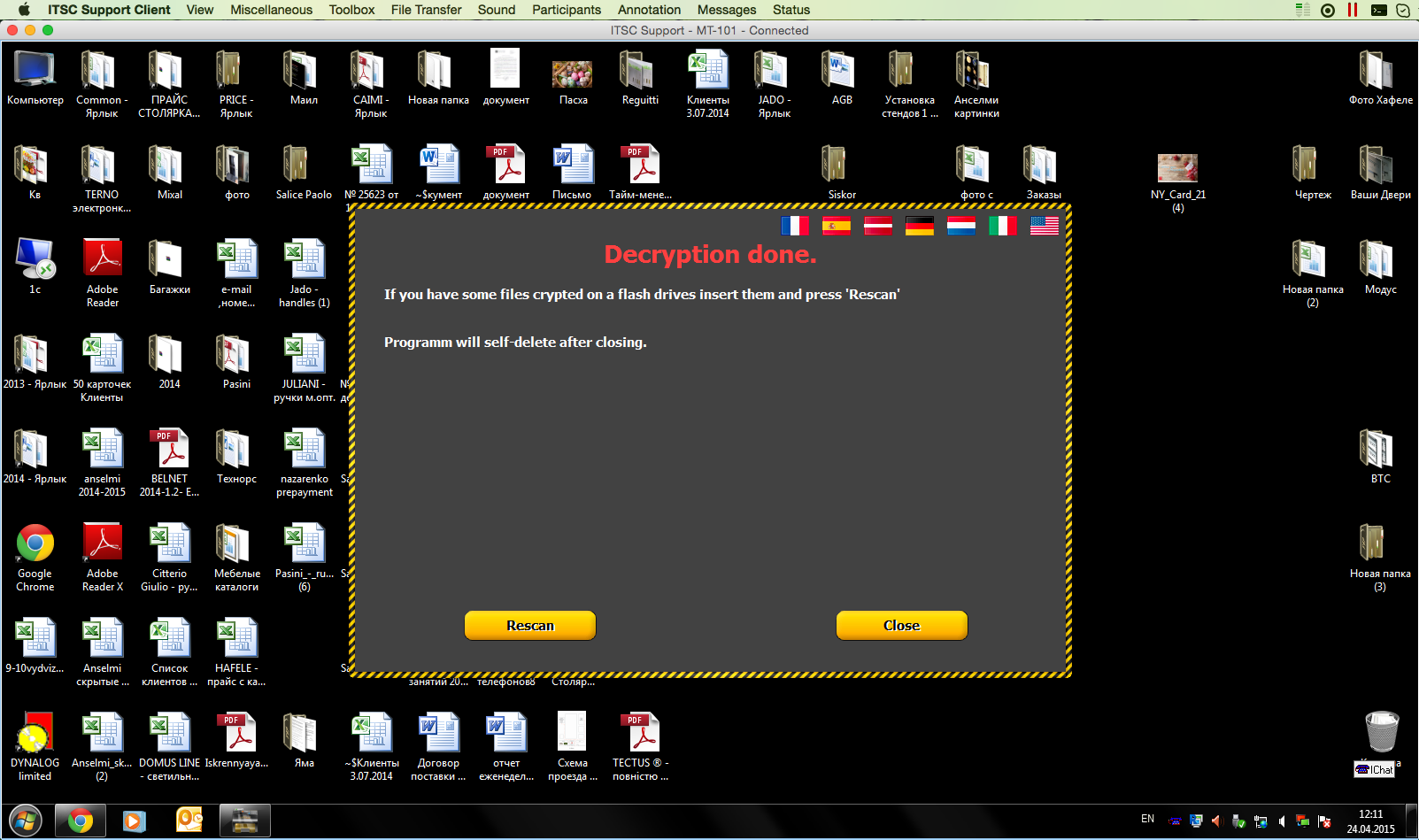
8. Make a backup copy of the file server (again, funding was quickly found on the expansion of the space for backup copies).
9. We connect the file server back to the network users. We format the user's computer, install Windows, etc.
10. We are thinking about changing antivirus.
I hope this publication has helped someone. Or, at least, reminded about the importance of backup and fresh anti-virus databases.
Source: https://habr.com/ru/post/256573/
All Articles