Vulnerability CVE-2015-1635 (MS15-034) is exploited in-the-wild
This week we wrote about the critical update MS15-034 for the http.sys driver on Windows 7+ (including Windows 10 TP). An attacker using a specially crafted HTTP request header can remotely execute code, organize a DoS attack, or drop the system into the BSOD on both client and server editions of Windows. The http.sys driver itself is loaded by Windows at the earliest stages and is responsible for implementing the HTTP protocol logic (implements the application layer of the OSI model on Windows).
This vulnerability directly relates to the server editions of Windows, since IIS, which is responsible for the web server implementation mechanisms, uses this driver to open and maintain HTTP ports for incoming connections, which can be used to compromise the system. However, on some modern client releases of Windows (depending on the configuration of the system and its services), running services can also open HTTP ports to listen for incoming connections.
')
The operation itself ( integer-overflow ) is possible by setting a special value for the Range field of the HTTP header (the value is regulated by RFC 2616, 14.35.1). Below is an example of such a request.
This query can also be used to check the system for vulnerability.
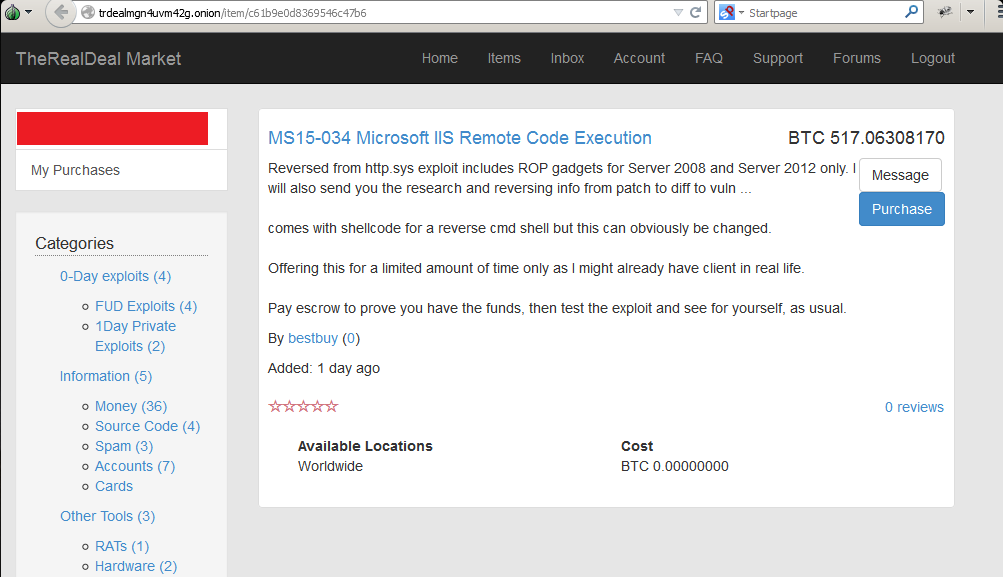
Fig. Offer on the underground forum for the sale of an exploit for MS15-034.
isc.sans.edu
One of the detected versions of the ITW exploit was:

This vulnerability directly relates to the server editions of Windows, since IIS, which is responsible for the web server implementation mechanisms, uses this driver to open and maintain HTTP ports for incoming connections, which can be used to compromise the system. However, on some modern client releases of Windows (depending on the configuration of the system and its services), running services can also open HTTP ports to listen for incoming connections.
')

The operation itself ( integer-overflow ) is possible by setting a special value for the Range field of the HTTP header (the value is regulated by RFC 2616, 14.35.1). Below is an example of such a request.
GET / HTTP / 1.1
Host: MS15034
Range: bytes = 0-18446744073709551615
This query can also be used to check the system for vulnerability.

Fig. Offer on the underground forum for the sale of an exploit for MS15-034.
Update: We are seeing active exploits hitting our honeypots from 78.186.123.180 . Use the DoS version, not the "detection" version of the exploit. The scans appear to be "Internet wide".
isc.sans.edu
One of the detected versions of the ITW exploit was:
GET /%7Bwelcome.png HTTP / 1.1
User-Agent: Wget / 1.13.4 (linux-gnu)
Accept: * / *
Host: [server-ip]
Connection: Keep-Alive
Range: bytes = 18-18446744073709551615
Source: https://habr.com/ru/post/256037/
All Articles