PVS-Studio security research

Greetings This is my first post on Habré in principle, but not the first article about hacking software in general, so I have the skill to write everything from the beginning and in steps, for beginner crackers. In this article, I will talk about how PVS-Studio was weaned from triality.
Training
Before you begin, remember: you perform all actions at your own peril and risk. Respect the work of programmers!
First of all, download and install the program. It's simple.
What are we dealing with?
Let's find out what the program is written on and what we will have to “ treat ”. Old fighters use PEiD for this, but it’s very old now, the bases are not updated, and many compilers simply don’t understand it. Usually, I use the program ExeInfo PE .
')
Go to the directory with the program, and " by eye " decide that the first experimental file will be PVSStudioStandalone.exe . Its launch also indicates that it is the main executable file. We set ExeInfo PE on it and get:
Microsoft Visual C # / Basic .NET | Explore, browse, and analyze .NET assemblies with .NET Reflector
ExeInfo PE window

Dive EXE №1
We are recommended to install .NET Reflector , and open our experimental in it. So do.
Screen .NET Reflector

We see that the class names are not obfuscated (they look normal). Also with a code of methods of these classes if to walk on them. We draw the first conclusion : the main executable file is not protected at all. Okay Go ahead.
Let's find a license check and everything connected with it.
Launch PVS-Studio , go to Tools -> Options ... -> Registration . Let's try to enter the user name and a random key (I did not contact the author, I did not ask for the key, so I don’t know their format):
We enter random reg.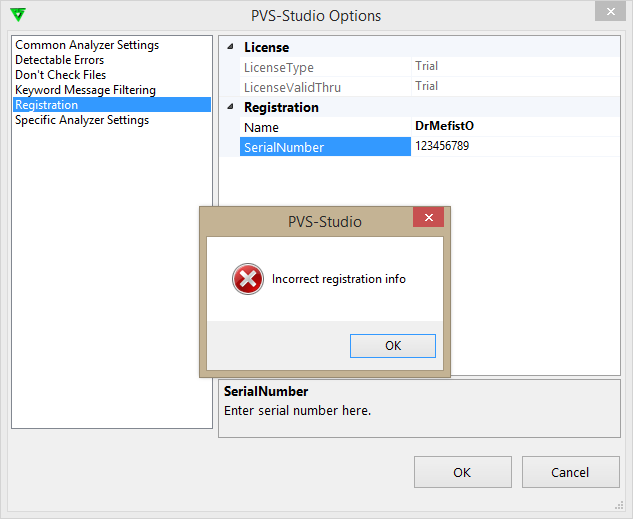



Now you can search the text of the error message in the .NET Reflector . Hit F3 ( Search ), then Ctrl + S ( Search String or Constant ). Enter " Incorrect registration info ". We get:
We are looking for Incorrect registration info

Double click on the link found, and we get the following code:
Method code get_LicenseType ()

Let's try to figure out where this method is called from. Click Ctrl + R ( Analyze ), expand the list, and in it expand the Used By list:
List of references to get_LicenseType () method

Right click on the found method, and there Go To Member .
ResetRegistrationInformation () method code

On the screen, I highlighted the place where we get the error message. In the condition of the if statement we see a check for the license type Invalid . So this type was installed somewhere above the code. We will simply go into all the methods in order until we find something suspicious ... And, here it is:
ProgramVerificationSystems.PVSStudio.LicenseInfo.Reload () Method

Happily go to the method GetLicenseInfo () !
GetLicenseInfo () method code

What's going on here? It seems that some exe-file is launched, with the argument --checkreg = yes , then its output to the console is parsed, and the license information is given on the basis of the results. What kind of file is launched? It is easy to figure out: go to the GetPVSStudioExePath () method and see:
GetPVSStudioExePath () method code

There is exe-shnik PVS-Studio.exe , which, it seems, lies in the x86 or x64 directories. Poryskav in the directory with the program, make sure that, yes - these folders, and we have such an executable file. Perfectly!
So, when passing a special parameter about a license request ( --checkreg = yes ), he should spit out information about our license.
Even deeper. EXE №2
Let's try to start PVS-Studio.exe separately through the command line, passing it our desire to find out info about the license.
We are requesting a license

Very good search line: " Unknown license type ". We will look for her through Olly Debugger v2 . Open PVS-Studio.exe in Olka , click PCM -> Search for -> All referenced strings :
All Referenced Text Strings

Press Ctrl + F ( Search for Text ), enter: Unknown license type . And, we find one link:
Search results Unknown license type

Double click on the link we get into the code:
Interesting code

On the screen, I selected a rectangle of interesting, in my opinion, function.
First, immediately after its call, the value in the EAX register is checked for a number from zero to three ( 0 - trial , 1 - invalid , 2 - timeout , 3 - valid ).
Then, the byte is checked under the address BYTE PTR SS: [LOCAL.12 + 3] (as Olka called it) for values from 0 to 3 ( 0 - Unknown license type , 1 - Single User License , 2 - Team License , 3 - Site License ). This address is given at the entrance to the function in the EAX register.
Somewhere further there is a date output in the console, but I did not begin to deal with it, since if the license type is valid , then it doesn't matter to date.
Patching EXE №1
Now the most interesting: you need to patch the code at the address pointed to by CALL (in my case - 0xA88570 ), to the one that gives us the type of license and mode we need. Let's compose a code:
First of all, let's fix the byte responsible for the type of license. I chose Site License (this number is 3 ). Judging by the information we have, we write the following code in Olka (press Space at address 0xA88570 ):
mov byte ptr [eax], 3
Then, we fix the return value in EAX . I also chose 3 ( valid ):
mov eax, 3
And finally, exit the function:
retn
Work results

Everything! Save the changes to the executable file, and enjoy a fully working license!
Patching EXE №2
This time, the executable file is 64-bit, so Olka cannot find the code. But, you can find it using x64dbg . Show some perseverance and you can patch it too!
PS As you can see, from the power of half an hour of research, and we are waiting for a good result.
the end

Thanks to all!
Source: https://habr.com/ru/post/255741/
All Articles