GPS: jammers, spoofing and vulnerabilities

The dynasty of GPS-spoofers at work
I wrote how the drones were hijacking , “hacking” their GPS, and came across a wonderful character - Todd Humphries - who not only reproduced the UAV hijacking, but also prompted the students to “hijack” the yacht.
GPS Spoofing
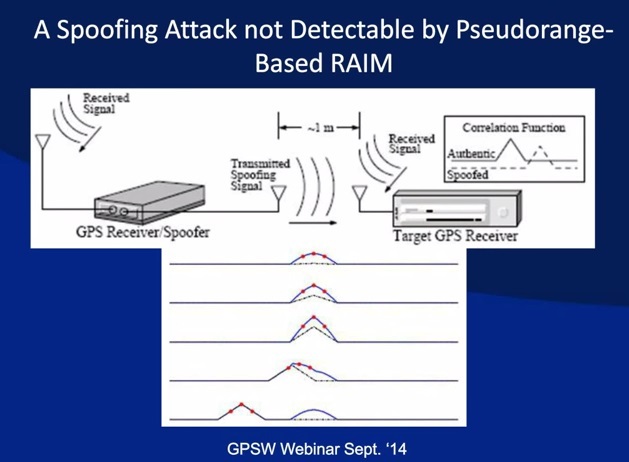
Spoofing a GPS attack — an attack that attempts to fool a GPS receiver by broadcasting a slightly more powerful signal than that received from GPS satellites, such as to resemble a series of normal GPS signals. These simulated signals are modified in such a way as to force the recipient to incorrectly determine his location, considering him as the attacker will send. Since GPS systems work by measuring the time it takes for a signal to travel from satellite to receiver, successful spoofing requires the attacker to know exactly where his target is — so that the simulated signal can be structured with proper signal delays.
')
The GPS spoofing attack begins by broadcasting a slightly more powerful signal that indicates the correct position, and then slowly deflects far to the position given by the attacker, because moving too quickly will result in a loss of signal blocking, and at this point the spoofer will only work as a transmitter interference. One of the versions of the capture of the American drone Lockheed RQ 170 in northeastern Iran in December 2011, is the result of such an attack.
Spoofing GPS was predicted and discussed in the GPS community earlier, but no known example of such a malicious spoofing attack has yet been confirmed.
Under the cut there are several useful videos with scenarios of attacks on GPS, analysis of cryptographic solutions used in navigation, detectors of jammers, spoofers, and, well, an overview of several portable GPS jammers that I sorted out in Hackspace.
Speech at TED of the main GPS hijacker, king of spoofing.

Who manages the drone: you or the hacker?

Students do not hunt for grandmothers, lenders and multimillion yachts
On July 29, 2013, students from the University of Austin, Texas, managed to divert a 213-foot yacht (worth $ 80 million) from the course using the GPS spoofing method.
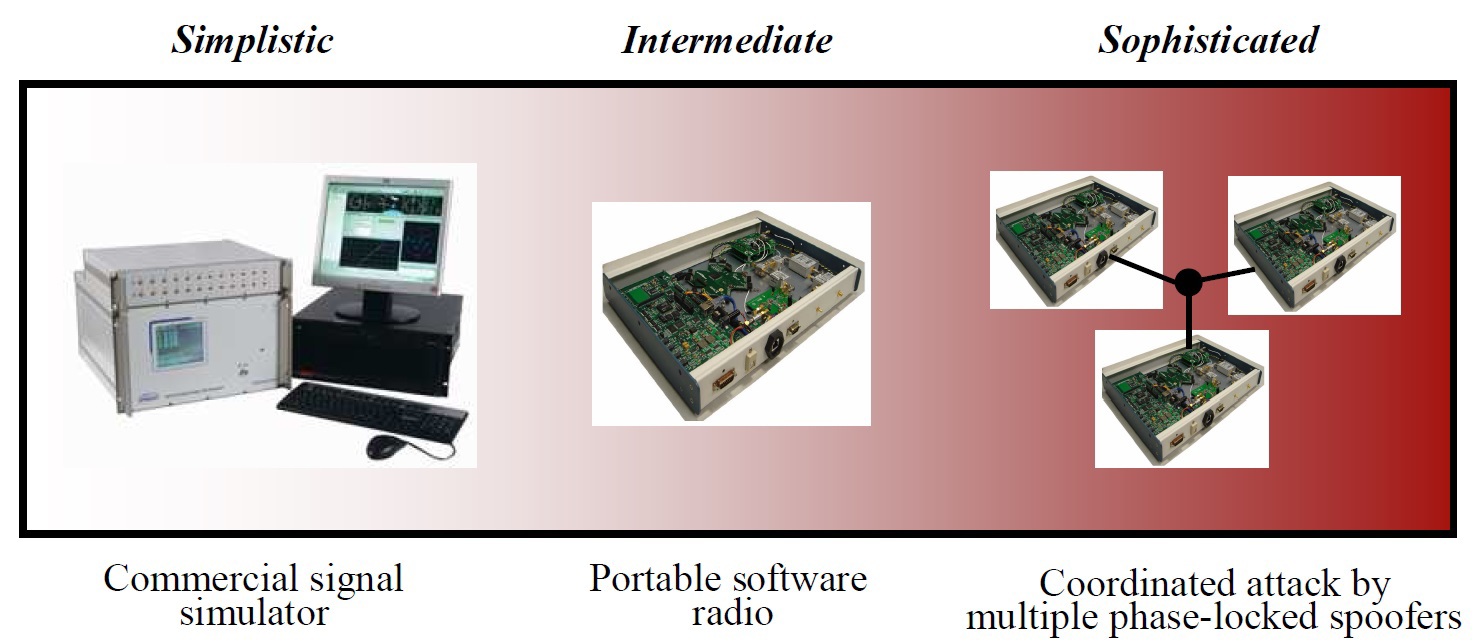
The main component of the spoofer has become a GPS signal simulator. These devices are manufactured in series and are intended for testing navigation systems. In most countries, they are sold freely and cost from a thousand dollars.
By itself, such a GPS signal simulator is low-powered and operates within a radius of ten meters. Therefore, amplifiers that have increased the power of a false GPS signal dozens of times have become the second component of the spoofer.
During the experiment, all the equipment of the attacking side was on board the yacht, sailing in the Mediterranean Sea off the coast of Italy. Figuratively speaking, she was immersed in a cloud of false GPS signals, the power of which was greater than the real ones.
At the first stage, Todd launched the process of duplicating real signals from satellites, seeking their full compliance with the characteristics taken into account. Having achieved the merging of both signals, he slightly increased the power of those sent by the spoofer. The navigation system began to consider them as basic and filtered out real satellite data as interference. After gaining control, Todd gradually began to distort the calculated positional information, leading the yacht north of the desired course.
The captain of the yacht was convinced of the effectiveness of the technique when the deviation exceeded three degrees. After that, Todd played the final chord. By changing the data to determine the height above sea level, the head of the group was able to force the navigation computer of the yacht to “count” that the vessel was under water.
Former Todd mentor, Professor at Cornell University, Mark Psiaki, proposed a scheme to protect against GPS spoofing . Now, together with graduate students, he has already implemented the described idea. His group created a modified GPS receiver with an antenna changing its position with a certain frequency. Since the satellites are at a considerable distance from each other, and the false signals come from one close place, the phase of the carrier wave in for such a receiver will change differently, which will allow to recognize the deception.
How to make a portable GPS-spoofer yourself (the price is about $ 2 thousand)

Civilian Spoofer GPS Assessing the Spoofing Threat: Development of a Portable GPS
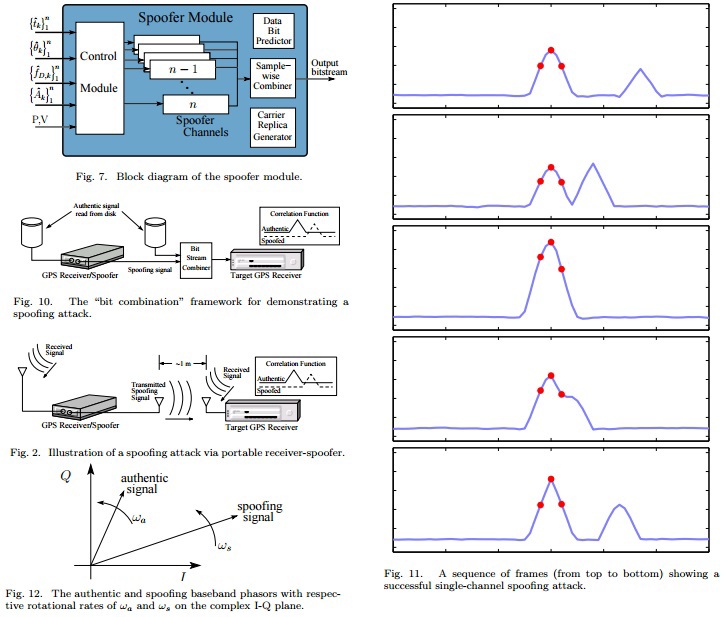
In the same publication, the author offers 2 options for protection against spoofing: Data Bit Latency Defense and Vestigial Signal Defense
More helpful videos
Todd Humphrey developed a budget centimeter accuracy combined with a GPS video camera.
[ source ]
The most recent video of June 2015, where Todd talks about the future of GPS (there are footage from his lab)
Spoofing, Detection, and Navigation Vulnerability (September 18, 2014)
In this program, Todd considers several GNSS security scenarios.
several slides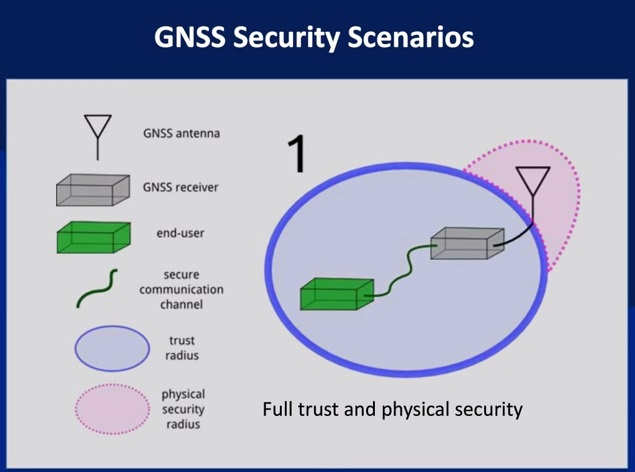



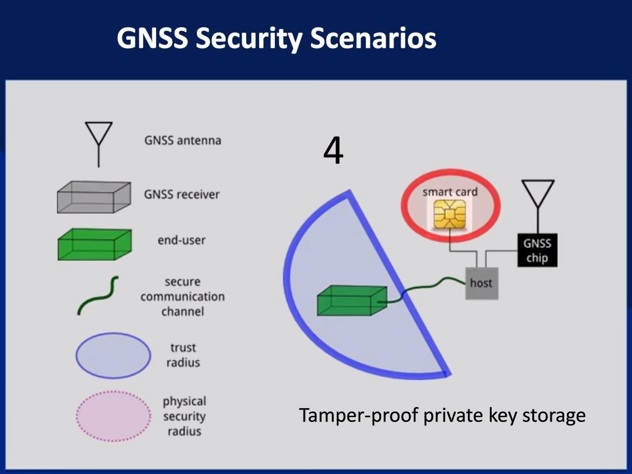

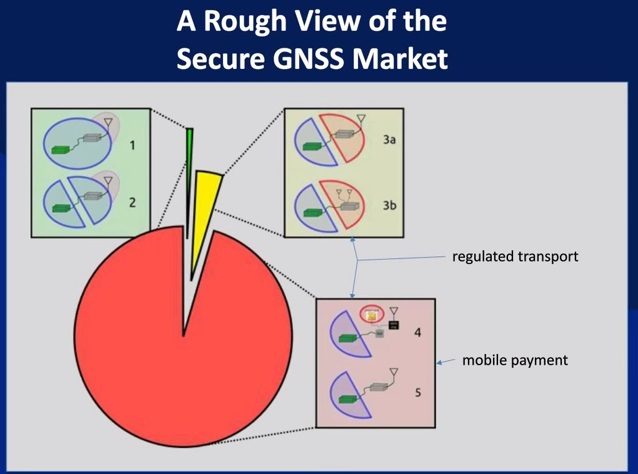
GNSS security market structure

Who's Afraid of the Spoofer? GPS / GNSS Spoofing Detection via Automatic Gain Control (AGC)

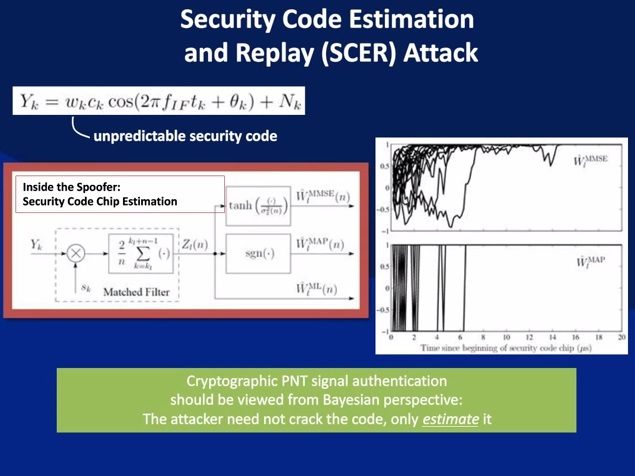

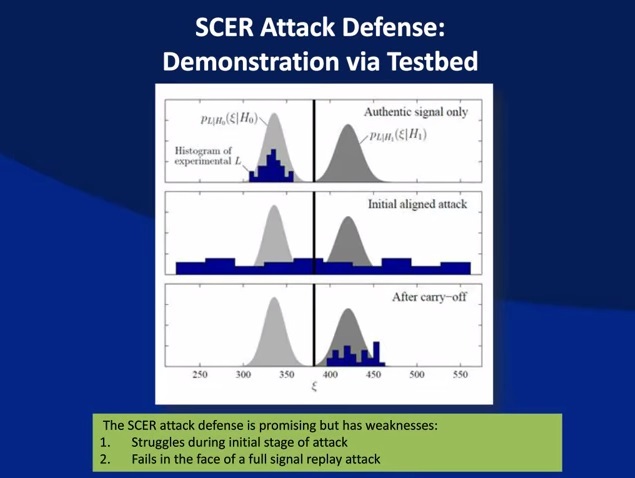







GNSS security market structure


Who's Afraid of the Spoofer? GPS / GNSS Spoofing Detection via Automatic Gain Control (AGC)







Security For and From GPS
Detect and Locate GPS Jamming: Provide Actionable Intelligence
Portable GPS Stubs

Alas, I did not have time to find a real tracker / beacon, so I tested it on a smartphone. Each of these devices "felled" satellites at a distance of more than 15 meters indoors.
more about jammers available on the Russian market (jammers)
GP50

Total output power: 70 mW
Price: 2600 rubles
G600 and G600s

It is possible to charge from the cigarette lighter
G600 suppresses L1: 1500-1600 MHz
G600s suppresses L1: 1560-1580 MHz and L2: 1217-1273 MHz
Total output power: 150 mW
Battery life: 120 minutes (G600) and 60 minutes (G600s),
Radius: 2-15 meters
Price: 3900 rubles (G600) and 4200 rubles (G600s)
Black wolf gt-12g

It suppresses all known satellite tracking frequencies.
This satellite lock can simultaneously jam a satellite signal in five different GPS / GLONASS bands:
L1 is the carrier signal, L2 is the auxiliary range, L3 is the military range, L4 is the range for studying the ionosphere, L5 is the new auxiliary range.
L1: 1500-1615 MHz
L2 / L3: 1200-1230 MHz
L4: 1250-1280 MHz
L5: 1170-1180 MHz
Signal blocking radius: 5-15 meters
Total power output: 2 watts
Battery life: 90 minutes
Price: 10400 rub.
Especially for hackers, airsoft there is a convenient "field" mount


GP50

Total output power: 70 mW
Price: 2600 rubles
G600 and G600s

It is possible to charge from the cigarette lighter
G600 suppresses L1: 1500-1600 MHz
G600s suppresses L1: 1560-1580 MHz and L2: 1217-1273 MHz
Total output power: 150 mW
Battery life: 120 minutes (G600) and 60 minutes (G600s),
Radius: 2-15 meters
Price: 3900 rubles (G600) and 4200 rubles (G600s)
Black wolf gt-12g

It suppresses all known satellite tracking frequencies.
This satellite lock can simultaneously jam a satellite signal in five different GPS / GLONASS bands:
L1 is the carrier signal, L2 is the auxiliary range, L3 is the military range, L4 is the range for studying the ionosphere, L5 is the new auxiliary range.
L1: 1500-1615 MHz
L2 / L3: 1200-1230 MHz
L4: 1250-1280 MHz
L5: 1170-1180 MHz
Signal blocking radius: 5-15 meters
Total power output: 2 watts
Battery life: 90 minutes
Price: 10400 rub.
Especially for hackers, airsoft there is a convenient "field" mount

Articles on Habré about GPS security
From the publication on Habré (2011):
According to the GPS World magazine, more than a billion GPS receivers are in use in the world, and more than 90% of them are used only to receive accurate time signals.
Interestingly, enthusiasts have already created working samples of a new generation of such devices that can not only jam, but distort GPS signals. Fraudsters can use this to implement some large scams (for example, all applications on the stock exchange are marked with accurate time signals, so that sabotage in a competitor's network will allow you to manipulate stock quotes).
The FBI ordered the court to shut off 3,000 GPS bugs, now it cannot find them
d In 2012, the US Supreme Court ruled that the use of tracking GPS devices without a court order was unconstitutional and decided to discontinue this practice. Since the decision of the court entered into force immediately, the Federal Bureau of Investigation was forced on the same day to turn off signal reception from about 3,000 active GPS bugs.
GPS Bug Device

I don’t know how in Russia, but citizens in the United States periodically find tracking GPS devices installed by special services under the bottom of a car. Last time, when it became known to the press, a student of Arab origin, by inexperience, took the device to the “manufacturer”, without having had time to investigate it properly. A similar device on her car a few years ago found an activist for animal rights Katie Thomas. She refused to return it to the FBI, and now she dared to give the device to study.
Where is my cart, sir? GPS tracking security
If an attacker wants to get a large amount of data on the movement of various objects, then he needs to compromise one of the public servers for monitoring. As practice shows, it is not difficult at all, because most of these web services contain quite trivial vulnerabilities from the OWASP TOP 10 list.
Interference Tests in the GATE Lab
The Germans were confused and approached the problem of a GPS jammer on a large scale.
As a result of the use of car jammers, GNSS signals are completely destroyed not only in the car where it is located, but also in closely located ones. This creates a real threat to the future of intelligent transport systems.
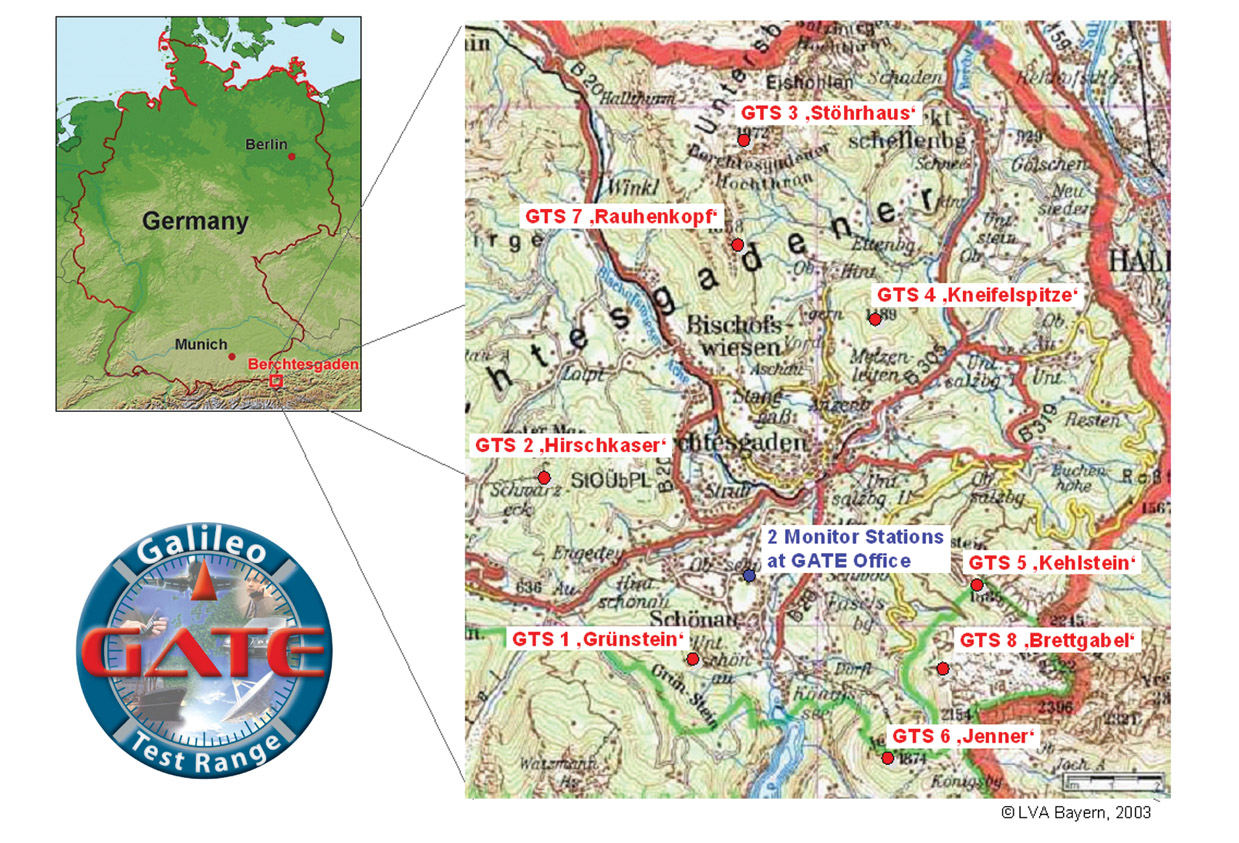
The figure shows a test lab where the transmitters, monitoring stations and the central GATE are visible. GNSS suppressor interference testing was conducted in an area close to this central point.
To counter such a threat, the University of the Federal Armed Forces, located in Munich, Germany, has acquired several automotive suppressors for conducting laboratory tests and tests in the GATE (Galileo Test Range) laboratory, in which real conditions are simulated. The measurements were carried out using an experimental software receiver developed at the Institute of Space Technologies and Applications. The receiver allows you to record samples of intermediate frequencies and analyze the effect of interference on the receiver.
The purpose of the study is to understand how jamming works in order to develop countermeasures. They dug up a bunch of data and made a serious analytics.
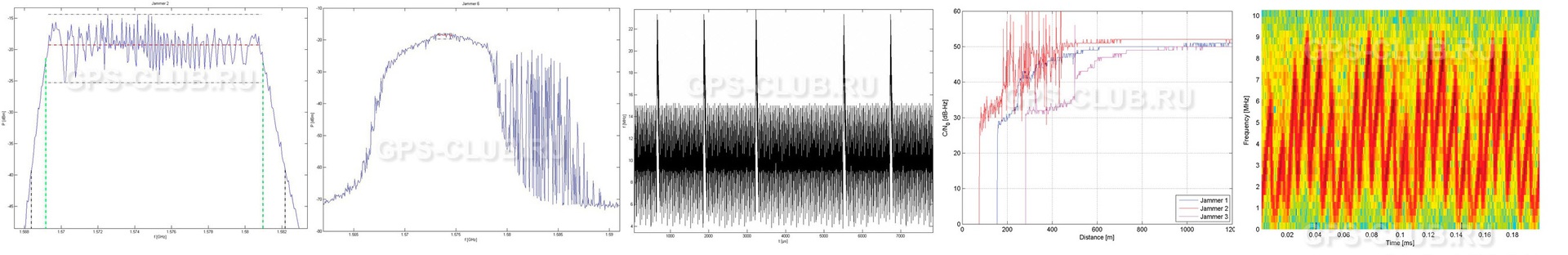
The conclusion was:
The analysis showed that the range of the suppressor is very much dependent on the architecture of the receiver. In each scenario, the suppressors had a strong impact. It is necessary to take measures against the use of automotive suppressors. For charges of using suppressors it is necessary to place detectors. This measure will also allow you to calculate the number of used suppressors. The degradation of GNSS positioning is a threat to the use of intelligent transport systems designed to improve driving safety. Therefore, the prevention and mitigation of interference effects should be the object of research for developers of automotive communication systems. There is a need to deal with interference in GNSS systems in the same way as other road hazards.
Analysis, Detection and Mitigation of InCar GNSS Jammer in Intelligent Transport Systems ( PDF )
Car Jammers: Interference Analysis ( translation into Russian ).
So, if you need to
PS
Thanks to the company Diktos for the equipment provided.
Source: https://habr.com/ru/post/254877/
All Articles