Hacking drones

It is very strange that at hacker conferences there were one and a half speeches on hacking drones.
I immediately promoted and made a selection of all available cases of hacks. Both military and civilian.
Some facts:
- To date, more than 70 countries produce unmanned aerial vehicles (drones) for the needs of the army, police, Emergency Situations Ministry, etc.
- From eBay from March 2014 to February 2015, sold 127,000 drones
- Do warriors now about 20.000 drones
')
10 real and 2 invented cases of hacking drones. (I will be grateful for additions)
2009
Place: Iraq, Afghanistan
Model: Predator unmanned aircraft (US $ 4.03 million, 2010)
Cracker: "Iraqi hackers"
Vulnerability: the data channel from the UAV to the ground control center

Wall street journal
For the first time, the US military in Iraq encountered a video interception in 2008, when a rebel was captured, on whose laptop were stored images obtained from American drones. In the summer of 2009, computers with several hours of UAV video recordings were also discovered.
As the newspaper notes, citing data from senior military officials and intelligence officials, the rebels used unprotected communication channels with UAVs for video interception. At the same time, they used software such as, for example, SkyGrabber, which can be bought over the Internet for as little as $ 25.95.
 SkyGrabber, according to the description of the Russian company SkySoftware, "receives and processes the traffic transmitted from the satellite, extracts files from it and saves them to your hard disk in accordance with the configured filters."
SkyGrabber, according to the description of the Russian company SkySoftware, "receives and processes the traffic transmitted from the satellite, extracts files from it and saves them to your hard disk in accordance with the configured filters."News on the tape .
2011
Location: Iran
Model: RQ-170 Sentinel
Burglar: Persian Specialists
Vulnerability: GPS spoofing
RQ-170 Sentinel

Who will plant him? He is a monument
Iran presented to the media a press release stating the successful interception of the American unmanned aerial vehicle type RQ-170 Sentinel. Among other versions of the interception of the device, there was also one that dealt with the use of special electronics, drowning out the signal of the GPS satellites and replacing it with its own. As a result of these actions, the UAV automatically, guided by the global navigation system, began returning home. Since the true signal of the satellites was drowned out by a false one, the RQ-170 took the Iranian airfield, taking it as its “home”. However, this is only a version, although it is fairly plausible. The first reports of this method of interception came shortly after the publication of the press release and were made with reference to an Iranian engineer who allegedly had a direct bearing on the interception operation.

Proof video

Iranians continuously troll the Americans. At first, they wanted to massively sell toy RQ-170 Sentinel on a scale of 1:80, and in 2014 they wrote down a full-size copy
Article on Habré with a discussion of the possibility of hacking the GPS system RQ-170
News on the tape .
2012
Location: Moscow, PHD
Model: AR.Drone
Burglar: Sergey Azovskov aka LAST_G
Vulnerability: Mobile Application Vulnerability

Under the terms of the competition, the organizers launched a miniature aircraft, controlled from a smartphone via a Wi-Fi network. Participants were asked to connect to the drone using their own programming knowledge, prevent the organizers from controlling the device and transfer control to their smartphone. According to Azovskov, the process of depriving the organizers of the rights to manage drones did not cause serious difficulties.
“Problems arose with the mobile application that is used to control the drone. I downloaded it, installed it, and then it turned out that it works with errors that had to be fixed, ”said Sergey Azovskov to RIA Novosti.

Location: Texas
Model: Helicopter for watering
Burglar: Todd Humphreys
Vulnerability: GPS spoofing
In 2012, American scientists from the University of Texas at Austin proved the practical possibility of hacking and intercepting the control of a UAV using GPS spoofing.
GPS spoofing can be performed only for those devices that use unencrypted civilian GPS signal.
(+ 1000 dollars to scientists)
Spoofing a GPS attack — an attack that attempts to fool a GPS receiver by broadcasting a slightly more powerful signal than that received from GPS satellites, such as to resemble a series of normal GPS signals. These simulated signals are modified in such a way as to force the recipient to incorrectly determine his location, considering him as the attacker will send. Since GPS systems work by measuring the time it takes for a signal to travel from satellite to receiver, successful spoofing requires the attacker to know exactly where his target is — so that the simulated signal can be structured with proper signal delays. The GPS spoofing attack begins by broadcasting a slightly more powerful signal that indicates the correct position, and then slowly deflects far to the position given by the attacker, because moving too quickly will result in a loss of signal blocking, and at this point the spoofer will only work as a transmitter interference. One of the versions of the capture of the American drone Lockheed RQ 170 in northeastern Iran in December 2011, is the result of such an attack.
Spoofing GPS was predicted and discussed in the GPS community earlier, but no known example of such a malicious spoofing attack has yet been confirmed.
University helicopter spoofing:
2013
Model: AR.Drone
Burglar: Samy Kamkar
Method: Aircrack-ng , Raspberry Pi is installed on the drone, WiFi transmitter and receiver:
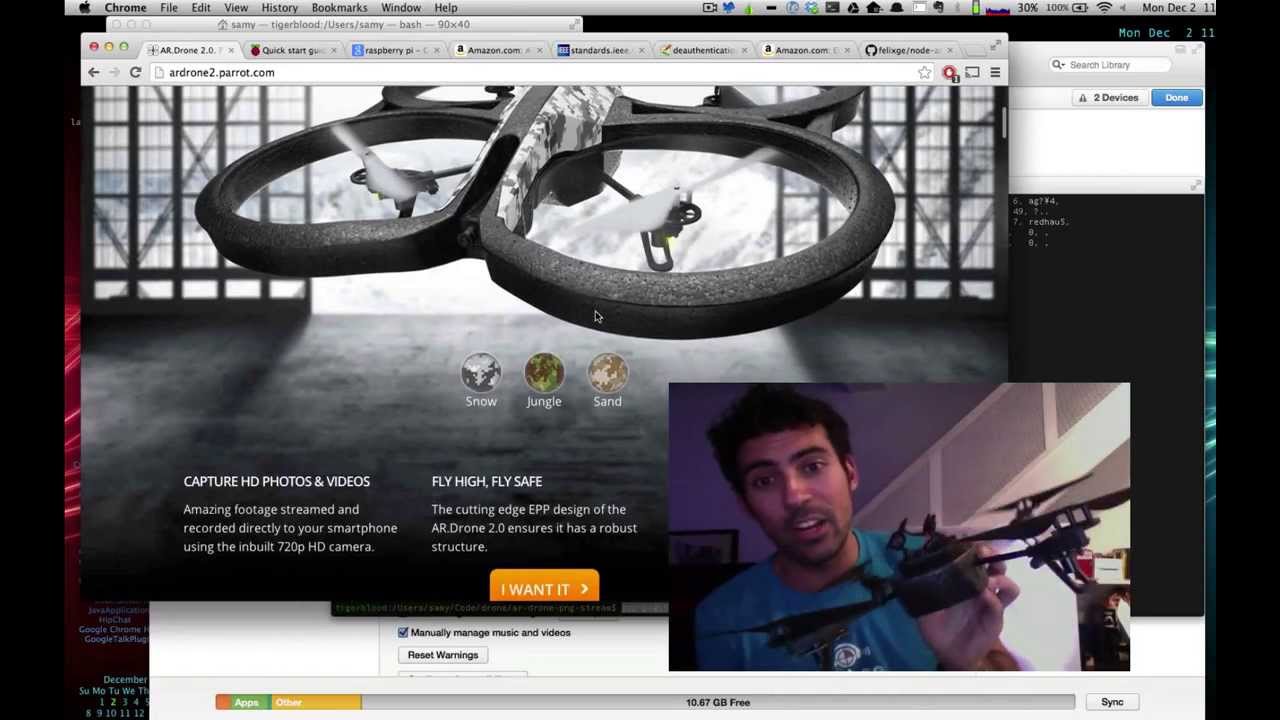
In his video, Kamkar said that he used the Aircrack-ng utility to hack a wireless network, and it was possible to detect quadcopters on the network thanks to the peculiarities of their MAC address. All quadcopters of this type have the same type of addresses, which allow us to distinguish them from other wireless devices.
Kamkar writes in his blog :
“How fun it would be to capture a drone that delivers parcels to Amazon, or any other drone, and make them your own zombie army. Sumptuously."
SkyJack monitors the MAC addresses of Wi-Fi networks in the signal coverage area, and then blocks them using its drone and disconnects from the iOS or Android device from which it was controlled. After that, the hacker can control the direction, speed and altitude of the drone, as well as receive an image from the cameras.
Defcon 21 - Phantom Network Surveillance UAV / Drone
Model: Phantom
Burglar: Ricky Hill
Method: Wispy spectrum analyzers and WiFi Pineapple:
2014
Location: USA
Drones: Parrot AR.Drone and DJI Phantom
Burglars: leading youtube channel Hack5
Method: WiFi Pineapple

WiFi Pineapple is a product of enterprising Americans who ordered a Wi-Fi router with two wireless interfaces and one wired from the Chinese, wrote OpenWRT-based firmware for it and stuffed it with utilities for hacking / intercepting and analyzing traffic.
The presenters screwed the WiFi Pineapple to the DJI Phantom copter and then chased the AR.Drone and cut it down.
Explains:
Anti-drone system

The failed project on Kickstarter
Personal Drone Detection System could protect you from neighbor spying with drones.
The equipment-locator detects an aircraft approaching you in a radius of 15 meters with a range of fixed operating frequencies from 1 MHz to 6.8 GHz. In appearance, the system most closely resembles a large Wi-Fi router (separate Personal Drone Detection System devices interact with each other using Wi-Fi technology) and several conventional “walkie-talkies”, each of which is the same sensor for detecting malicious buzzing devices. . The latter are detected by the system as moving in space sources of electromagnetic radiation.
The main control module is able to interact with “portable locators” at a distance of up to 61 m. All you need to do is to arrange two sensors around the perimeter of the house, use the command controller and synchronize with the control module of the anti-drone system. On the approach of the drone, you will be notified of the corresponding sound signal and the sent notification to your personal mobile device.
"Motor depot"
Russian "jammers". According to some reports, they lit up when intercepting UAVs.
In addition to PVC windows and luminaires, Kvant produces high-power noise interference stations, ground-based active interference stations and ground-based electronic radio intelligence systems AVTOBAZA.
2015
Burglar: Rahul Sasi
Purpose: Parrot AR.Drone 2.0 and DJI Phantom
Vulnerability: ARM Linux
Sacy applied reverse engineering to the proprietary program AR Drone program.elf
The researcher claims that a "combined" attack using Maldrone and Skyjack will allow you to intercept multiple targets and thus create a whole squadron of zombie drones. Given the growing interest in civilian UAVs from corporations such as DHL and Amazon, the picture is truly sinister. In addition, using Maldrone, the attacker has the opportunity not only to steal the drones themselves, but also to spy through the built-in cameras, intercepting video traffic from the attacked devices.
“After my malware attacks the controllers, the engines stop and the drone begins to fall brick down,” explains the researcher. “However, the backdoor instantly intercepts the control, and if the height is really high, there is enough time to avoid falling.”
Maldrone virus (abbr. From Malware Drone), developed by Sacy, is able to seize control of this program and move the drone in any direction, potentially hijacking it from the owner.
The disadvantage of Maldrone is that it takes a few moments for it to switch control of the device ports responsible for navigating to itself. During this "interception", the drone control is turned off, and it falls vertically down, so it can break if it is not high enough.
Create a backdoor:
Drone controller program.elf interacts with the navigation board using the ports:
/ dev / ttyO0 -> rotors and leds
/ dev / ttyO1 -> Nav board
/ dev / ttyPA1 -> Motor driver
/ dev / ttyPA2 -> accelerometer, gyrometer, and sonar sensors
/ dev / video0 ->
/ dev / video1 -> video4linux2 devices
/ dev / i2c-0
/ dev / i2c-1
/ dev / i2c-2
/ dev / usb-i2c

Maldrone Idea.
Step 1: Kills program.elf
Step 2: Setup a proxy serial port for navboard and others.
Step 3: Redirect serial interface ports to fake ports
Step 4: patch program.elf our proxy serial ports.
Step 5: Maldrone communicates to serial ports directly
Now all communication from the navigation board goes through Maldrone. The backdoor can intercept and change data on the fly and it communicates with the botserver.
Hindu invited everyone to the conference , where he promised to give details , but since then there has been no news. Presentation only.
2018
DARPA releases unbreakable drones .

Project Manager DARPA Ketlin Fisher talks about 2 cases of “theft” of military drones (2009 and 2011), and then the “hacker” presses the button and hacks the “Toffee”
2050
Little data, it is known that:
- a) drones fly
- b) they are completely cracking, despite the best efforts of DARPA
- c) hackers hunt for batteries
- d) the interface is a bit strange
- e) DELL laptops


Remember that in the glove compartment of a normal farmer (astronaut), near the spare wheel, there is always a directional antenna and a laptop stuffed with software. What if the drone?
Blackhat pda
Soon there will be similar gadgets, but for now we are training in the simulator.
This thing cracks quadcopters, drones and real helicopters equally easily.
Oh yeah, she still knows how to crack electronics (guns, mines, etc.) through walls. Dreaming is not bad.
PS
He addressed a question about hacking to his friends from CopterTime.ru , they are practically ahead of everyone of the novelties of quadrics to Moscow, and they have their own workshop, very similar to hackspace for drones.
They talked about how you can “hack” the Naza controller. Namely, how to disperse the older Naza Light ($ 170) to the newer Naza V2 ($ 300):

The fact is that dji blocked the bootloader from the Naza-m lite bootloader and just did not download the update. Here the craftsmen figured out what was happening, and launched the project naza-upgrade.com , where you can download software that allows you to upgrade the controller in a couple of clicks.
The upgrade includes optimized algorithms for GPS positioning and height retention, the ability to connect peripherals via Bluetooth, support for Octocopter, etc.
Upgrade video tutorial:
The flagship civilian drones DJI Inspire 1
There is such a drone in the US $ 3,000, it flies 18 minutes, but at the same time it can fly 13 km (6.5 km one way), this is a world record with a signal amplifier for the console. On a conventional transmitter, the control is kept 2 km. That is, it is quite possible to hijack such a copter, it flies at a speed of 22m / s, so the owner, even if he has a bit prepared for such cases, is unlikely to catch up with him.
(Read all the specifications of DJI Inspire 1 ).
I can imagine how in the future a minivan will go (not “Avtobaz”, of course), stuffed with equipment (pineapples, ubertusami, hackarafs, jammers, etc.), and steals not mopeds, but drones.

Video with a world record flight range of 13.357 meters:
Pps
Hacking targets (on click - big picture):

Source: https://habr.com/ru/post/254685/
All Articles