Five obvious mistakes that for some reason continue to make
In this article I will tell you how from a single error message on the site I accidentally got access to the company's internal information (and even a bit more). I note that this can be done using only one browser.
Sites sometimes fall. That happens. But what is described in the article should not happen.
Recently I went to the site of one company and saw (once again, I note) instead of him the error message:
')
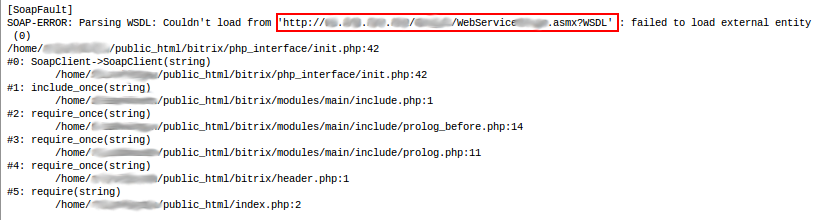
Why the site fell is a separate conversation. Let me just say that it is on the conscience of its developers.
The first error (too obvious, but ...) : display of error messages. Yes, everyone knows that you need to disable debugging in production. But damn it, why do I regularly see error messages in my browser ?!
So what can we learn from this message? Yes, no less than the public address of the SOAP-service. Well, well, it is unlikely that it is still available openly, but just in case, copy to the address bar and get ... a list of available methods. Many methods, most clearly for internal use. Each includes a description of the request and an example response. Many require authorization (transfer in the login request and password), but not all. We select one open method with the talking name and construct the query directly in the browser. Yes, many people criticize the Web Developer built in Firefox (and there is a reason for that), but it is quite suitable for simple tasks:
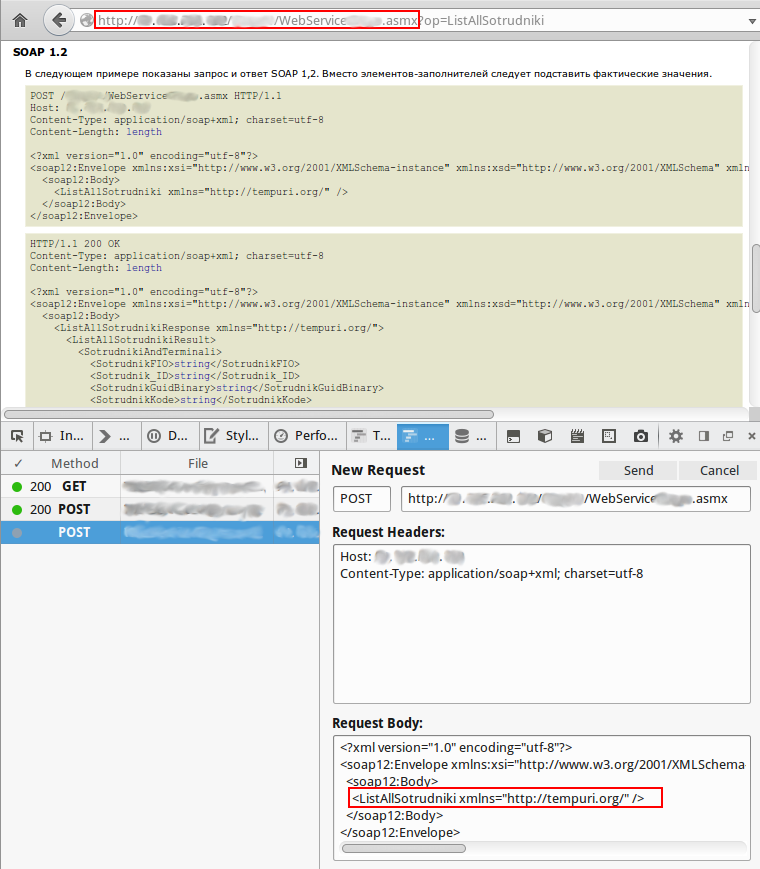
The second error : publicly available services. That's why this server looks to the world? Do any remote applications use it? Well, then close it by authorization. Or at least do not accompany the detailed instructions for action.
Let's see what the server told us. For the convenience of viewing, open the resulting XML in the same browser:

This is a list of company employees, a little less than two hundred items. Great, look for a guide. We find, to put it mildly, not the last person in the company (in the screenshot). Now we know his email and something suspiciously similar to Base64 in the element SotrudnikPassword. We decode the password in any of the many online decoders.
The third error : passwords in clear text. Even if the question of why to give passwords (hashes) to the outside is taken out of the brackets, it is still not clear why at least not the hashes. Or do developers believe that Base64 is suitable for this purpose?
Note : errors # 4 and # 5 refer not to security of services, but to personal security. Here the fault is not the developers, but the user, but I decided to leave them, since they are a) part of this story b) just as commonplace and obvious to everyone, but just as often committed.
Let's see what can be done with the information received. Let's try to get access to the specified mail. We check the domain in the first available DNS lookup service. Judging by the MX, this is GMail. Well, let's try to log in using the decoded password:
You are not surprised if I say that the password came up?
The fourth error : one password for different accounts. It will not matter how long it is and how many letters it has in a different register and numbers if it leaks because of yours or someone’s (as in this case) stupidity.
The password came up, but Google guards the user's security — sees that they’ve logged in from another IP, and requires additional confirmation:

That's just the last option offered to them looks too simple. Google, are you serious?

In this case, there was a rare enough surname, so it didn’t even take to indicate the name of the company. Let's try to enter the phone found:

Fit A corporate GMail opens (and, accordingly, Google Tasks, Google Drive and other services).
Fifth mistake : using easily recognizable information as an additional factor of authorization / control question (in this case known to others and the Internet phone number). Is it difficult to find out the mother's maiden name or the date of her birth? So why many services and banks still use them by default?
I wrote a letter to this person about the need to change the password. It is also customary to report vulnerabilities to developers and give time for correction. But. Re-read errors # 1— # 3. It is necessary to inform them that their reports of falls are shown to everyone, servers, excuse me, naked. look at the Internet and passwords are given to the first comer unless it is plain-text? Does it really need to be reminded of commercial developers applying for the corporate level? About things so simple and obvious, that without knowing them, you shouldn't take them to work? I hope that they will read it and recognize themselves. I want to tell them only one thing: “Guys, get out of the profession!”
About me : not a developer, not a security specialist, and generally no side IT. An advanced Internet user, let's say.
Prologue
Sites sometimes fall. That happens. But what is described in the article should not happen.
#one
Recently I went to the site of one company and saw (once again, I note) instead of him the error message:
')

Why the site fell is a separate conversation. Let me just say that it is on the conscience of its developers.
The first error (too obvious, but ...) : display of error messages. Yes, everyone knows that you need to disable debugging in production. But damn it, why do I regularly see error messages in my browser ?!
# 2
So what can we learn from this message? Yes, no less than the public address of the SOAP-service. Well, well, it is unlikely that it is still available openly, but just in case, copy to the address bar and get ... a list of available methods. Many methods, most clearly for internal use. Each includes a description of the request and an example response. Many require authorization (transfer in the login request and password), but not all. We select one open method with the talking name and construct the query directly in the browser. Yes, many people criticize the Web Developer built in Firefox (and there is a reason for that), but it is quite suitable for simple tasks:

The second error : publicly available services. That's why this server looks to the world? Do any remote applications use it? Well, then close it by authorization. Or at least do not accompany the detailed instructions for action.
# 3
Let's see what the server told us. For the convenience of viewing, open the resulting XML in the same browser:

This is a list of company employees, a little less than two hundred items. Great, look for a guide. We find, to put it mildly, not the last person in the company (in the screenshot). Now we know his email and something suspiciously similar to Base64 in the element SotrudnikPassword. We decode the password in any of the many online decoders.
The third error : passwords in clear text. Even if the question of why to give passwords (hashes) to the outside is taken out of the brackets, it is still not clear why at least not the hashes. Or do developers believe that Base64 is suitable for this purpose?
Note : errors # 4 and # 5 refer not to security of services, but to personal security. Here the fault is not the developers, but the user, but I decided to leave them, since they are a) part of this story b) just as commonplace and obvious to everyone, but just as often committed.
#four
Let's see what can be done with the information received. Let's try to get access to the specified mail. We check the domain in the first available DNS lookup service. Judging by the MX, this is GMail. Well, let's try to log in using the decoded password:

You are not surprised if I say that the password came up?
The fourth error : one password for different accounts. It will not matter how long it is and how many letters it has in a different register and numbers if it leaks because of yours or someone’s (as in this case) stupidity.
#five
The password came up, but Google guards the user's security — sees that they’ve logged in from another IP, and requires additional confirmation:

That's just the last option offered to them looks too simple. Google, are you serious?

In this case, there was a rare enough surname, so it didn’t even take to indicate the name of the company. Let's try to enter the phone found:

Fit A corporate GMail opens (and, accordingly, Google Tasks, Google Drive and other services).
Fifth mistake : using easily recognizable information as an additional factor of authorization / control question (in this case known to others and the Internet phone number). Is it difficult to find out the mother's maiden name or the date of her birth? So why many services and banks still use them by default?
Epilogue
I wrote a letter to this person about the need to change the password. It is also customary to report vulnerabilities to developers and give time for correction. But. Re-read errors # 1— # 3. It is necessary to inform them that their reports of falls are shown to everyone, servers, excuse me, naked. look at the Internet and passwords are given to the first comer unless it is plain-text? Does it really need to be reminded of commercial developers applying for the corporate level? About things so simple and obvious, that without knowing them, you shouldn't take them to work? I hope that they will read it and recognize themselves. I want to tell them only one thing: “Guys, get out of the profession!”
About me : not a developer, not a security specialist, and generally no side IT. An advanced Internet user, let's say.
Source: https://habr.com/ru/post/254597/
All Articles