Evolution of web injects, part 1
Currently, web inject files have been adopted in many banking malware and are used as a means for financial fraud. This mechanism of malware operation was initially distributed in single copies and was dependent on one or another family of malicious programs. Over the past few years, web injections have been used as part of a whole cybercriminal ecosystem in which independent developers sell their products to botnet operators.

Such a market for the sale of such services can be observed in numerous underground forums, where we see an increasing number of offers from cybercriminals for the sale of sets of web injects. They include all the necessary opportunities to conduct bank fraud, including mechanisms to circumvent special security measures that banks use to ensure the security of user accounts.
')
Our study focuses on the very nature of web injecting and their growing market. We look back and see how web injects have evolved over time from the very beginning, when they looked like a regular phishing system and ending with automatic ATS systems that can be used to bypass two-factor 2FA authentication.
To date, the botnet operator, in order to earn money on fraudulent transactions, needs only a malicious program that can inject malicious HTML content into legitimate web pages of the browser. Thus, he, in fact, does not care how this malicious mechanism will be implemented, only its effectiveness is important to him. Therefore, to implement this algorithm and its mechanisms, it can resort to the services of other cybercriminals who know this area much better than him and who can offer the best services for conducting fraudulent schemes.
Introduction
In fact, web injections are one of the most advanced tools that use bank Trojans to conduct fraudulent transactions with users' bank accounts. Recently, banks have begun to use special security mechanisms that are designed to protect an account or user account from unauthorized access. Web injections are also not standing still, and their authors adapt their cybercrime tools to circumvent these security mechanisms. Selling kits of web injects in underground forums has been observed for several years now.
As we know, over the past few years, users are increasingly turning to Internet banking services for various banking operations. Cybercriminals also do not stand still and create special malicious tools to compromise users' computers and their mobile devices. At the very beginning of their evolution, the attackers relied on banking trojans, which contained functions for compromising several financial institutions and were well-known keyloggers (keyboard spies) and grabbers / hijackers of web forms. Both of these tools were used to steal confidential data from online banking accounts.
Keyloggers are less useful because they generate a general flow of characters typed by the user from the keyboard, from which you will still need to isolate the desired username and password to access your online banking account. This task fell on the shoulders of botnet operators. Grabber of forms became an obvious way out of this situation, since it could only receive data of interest to intruders that the user entered into a fake login form into an online banking account. Then, the captured data was sent to the remote server of the attackers.
From the point of view of today, form grabbers are a rather outdated way of capturing GET and POST HTTP protocol requests, with which form data is sent to a remote server. The well-known and already studied Zeus and SpyEye banking trojans were the first to use the form grabbing mechanism based on interceptions of API functions in the context of the web browser process. Some malware used forms grabbing based on tracking the network traffic flow generated by the browser. Using the API interception mechanism is more preferable for attackers, since this way the form data is intercepted before they are directly encrypted for subsequent transfer to a web server. This method is not without flaws, since it is dependent on a particular browser or its version.
Modern malware is increasingly using these outdated techniques; instead, they resort to web-injecting services that allow them to fine-tune and use a malicious scheme of web page compromise and theft of funds. In addition, the web injections themselves allow you to modify the content of the web pages of online banking sites, depending on the specific bank. Web injections allow attackers to perform a wide range of actions on a compromised web page that the user sees. There are several sets of web injects offered for sale in underground forums that use a jQuery JavaScript library.
Zeus and SpyEye, the popular banking trojans, were among the first to use web injections to compromise specific banking sites and modify their content. The content of the web page can be modified using the API call interception mechanism. This is the same method that malware uses to organize forms grabbing. A banking trojan can inspect the content received from the server and modify it on the fly before directly displaying this content in a browser. This technique is used to trick a user who trusts in the content that the web browser displays when they visit the online banking web page. This method is known as an attack on a user called Man-in-the-Browser (MitB). Below in Fig. Figure 1 shows an example of a real web injection that resulted in deletion of text with warnings about financial fraud.

Fig. 1. Malware using web-inject has deleted service information from the web page (online banking warning). At the top is a view of the original web page, at the bottom a compromised web page with the warning text removed.
The malicious content that will be added to the web page is located in the web injects configuration file. This file is usually downloaded by the infected computer from a remote C & C server. This method of transferring the configuration file is very convenient for attackers, since they can modify the contents of such a file once on the server and infected computers will receive an upgraded version of this file the next time. There are various formats of web injects configuration files, but one of them has gained the most popularity. It was used in the SpyEye banking Trojan and eventually became the de facto standard. In Fig. Figure 2 shows an example web injects configuration file.

Fig. 2. The standard format of the web injects configuration file.
As you can see above, the first parameter is the target URL where a specific web injection should work. The characters in the line after the URL indicate to the banking trojan what action it should take when the user opens this address in the browser. Table 1 shows the values of these service symbols, and Table 2 shows the various parameters (tags) of the configuration file. Some web injections are quite simple and contain functions similar to a simple phishing mechanism, i.e. they embed special fields into the body of the web page, in which the user is prompted to enter his personal and confidential data. An example of such a web inject is shown in Fig. 3

Table 1. The most common flags for the set_url parameter.

Table 2. The most common tags of the web injects configuration file.

Fig. 3. An example of malicious webpage content that specializes in collecting personal and confidential user information.
Automatic Transfer System (ATS)
Over time, web injecting has become increasingly specialized and multifunctional. Some of them contain special advanced features that help attackers to perform fraudulent operations with the user's account. Special scripts that implement such operations are designed to bypass the protective mechanisms of specified online banking websites. As web injecting developed, the security systems of banks' sites were also improved and all new features were added to detect malicious activity. In Fig. 4. You can see an example of a web injection in which the attackers have provided time intervals between malicious actions to simulate human behavior.

Fig. 4. A webinjection function that defines the logic for using time delays.
As soon as the fraudulent transfer from the user's account has been completed, a web injection hides the operation by using special mechanisms. Concealment is understood as an imperceptible adjustment of the cash balance of a bank account. Thus, the user remains ignorant of the fact that funds have been stolen from his account.
The popularity of ATS attacks has decreased recently, as the level of complexity to success ratio has decreased (success-rate-to-complexity ratio). We can still observe the use of ATS methods of in-the-wild attacks, but some cybercriminals have refused to use them in favor of those attacks that use "manual control". In this case, the attackers simply take the compromised computer under their control and perform fraudulent actions manually.
Bypassing the Transaction Authorization Number (TAN) mechanism
With the advent of banking malware, security experts at banks began to introduce special additional security features into banking resources. One of the most popular of these functions was two-factor authentication, which strengthened the security of transactions.
Two-factor authentication raises the security bar when conducting banking transactions through the use of special confirmation codes. Such codes can be obtained by the user in his bank simply in the form of a list, so-called. Transaction Authorization Numbers (TAN), or in the form of SMS-messages from the bank, the so-called Mobile codes (mTAN). If two-factor authentication is enabled, the user will use the received mTAN codes to confirm the ongoing transaction on the online banking website.
To bypass the mTAN mechanism, attackers can lure the user to install a special malicious program for a mobile device that will intercept SMS messages received from the bank. This can be accomplished through social engineering techniques. For example, as soon as a user logs into his online banking account via a compromised web browser, the malicious code will inject special malicious content onto a web page. Content is a text with a request to provide information about the mobile device used by the user (Fig. 5.).

Fig. 5. Malicious content on a web page that requests information about a mobile device.
After the user provides such information, he will receive an SMS message to his mobile device with a link to download the malicious application. He can also use the QR code to get the link. After its opening, the malware will be downloaded to the device, then the user will have to manually start its installation. This procedure can consist of several stages, for example, attackers can embed such content into the online banking web page that will act as a guide to installing malware, instructing the user step by step. As soon as the malware is installed on the mobile device, it will be able to redirect all received SMS messages to the attackers' phone, giving them the ability to bypass mTAN codes when conducting fraudulent actions with the user's account. Perkele and iBanking banking trojans are well-known malware representatives with such capabilities.
Since banks began to use two-factor authentication mechanisms, web injection developers were forced to adapt their malicious tools to circumvent them. As shown below, the attackers use one of the forms of social engineering to deceive the user and lure the necessary information from him, which will be used to circumvent these protective measures.
The information that became available to us after monitoring the activities of botnet malware provided us with a picture of the methods used by attackers to bypass the mTAN scheme. They all boil down to one general principle: displaying a special message to the user with a fictional story that will attract his attention. The attackers display it to the user at the very moment when he logs into his online banking account and believes that he is using a secure connection with the server and that all data displayed by the browser is reliable. One of these stories is based on the information that a certain amount of money was mistakenly transferred to the user and he should return it back. Such a scheme becomes possible because the malicious code of a web-injection can correct the cash balance displayed to the user, thus misleading it. Another story was based on the fact that the user was asked to "calibrate" his mobile device by performing a test cash transaction.
In Fig. 6. A fake malware message is shown asking to enter a TAN code from a list in the text field that was issued to a user in a bank. As we know, the codes in this list are numbered, so attackers ask for the code behind a certain number. The attackers ask the user to give them the TAN code in the event that they need to steal a certain amount of money from the user's account and confirm this operation with the 2FA mechanism. Phishing message is compiled as convincingly as possible for the corresponding impact on the user.

It should be noted that there are other web injections that are aimed not at compromising the websites of financial institutions and banks, but at compromising known services, for example, Facebook, Twitter, Google, Yahoo. Such web injections specialize in stealing users' confidential or private information, such as a credit card number or phone number. In Fig. 7 shows a web-inject, which is focused on a service known service Twitter.
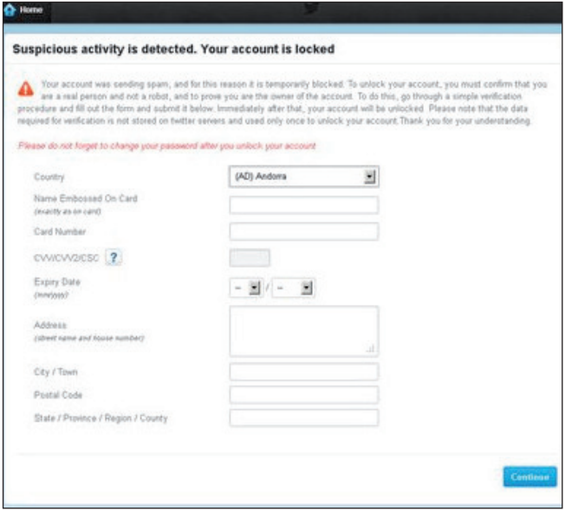
Fig. 7. Web inject for Twitter service.
Encryption of web injects configuration files
Since web injects configuration files contain key information for security researchers and CERT organizations around the world, attackers are directly interested in keeping the contents of these files out of their hands. For this purpose, encryption and obfuscation algorithms are applied to the files.
At the initial stage of the development of web inject files, the attackers did not use encryption and these files were transferred from the remote server to the bot in the open form. After the antivirus companies turned their attention to banker Trojans and began to track the appearance of these configuration files, the attackers began to use encryption, making the process of decrypting the content more difficult with each step. Banking Trojans such as Zeus and its modifications currently use several levels of encryption, and the decrypted file itself is stored in memory in parts, not in its entirety.
Compression or compression of JavaScript code can be performed by an attacker using the so-called. mechanism / packer /, but in this case, it can be quite quickly converted to the original look. The operation of obtaining original content can be performed using simple permutations of the “eval” function and the services of the JS beautifier service. This compression method is convenient because it reduces the size of the content of the web-inject, but its obvious disadvantage is the weak content security. In Fig. 8. A fragment of the script that was compressed using / packer / is shown.

Fig. 8. An example of a mechanism compressed / packer / script.
The algorithms used by hackers to obfuscate the content of web injections can significantly complicate their analysis, since deobfuscating the content can be a non-trivial task. In Fig. 9. An example of such obfuscated content is shown.

Fig.9. An example of obfuscated web injection.
The increase in the number of banking Trojans, as well as their complexity, will inevitably lead to a demand for high-quality web injections. Such demand has already been secured by corresponding proposals in underground cybercriminal forums.

Such a market for the sale of such services can be observed in numerous underground forums, where we see an increasing number of offers from cybercriminals for the sale of sets of web injects. They include all the necessary opportunities to conduct bank fraud, including mechanisms to circumvent special security measures that banks use to ensure the security of user accounts.
')
Our study focuses on the very nature of web injecting and their growing market. We look back and see how web injects have evolved over time from the very beginning, when they looked like a regular phishing system and ending with automatic ATS systems that can be used to bypass two-factor 2FA authentication.
To date, the botnet operator, in order to earn money on fraudulent transactions, needs only a malicious program that can inject malicious HTML content into legitimate web pages of the browser. Thus, he, in fact, does not care how this malicious mechanism will be implemented, only its effectiveness is important to him. Therefore, to implement this algorithm and its mechanisms, it can resort to the services of other cybercriminals who know this area much better than him and who can offer the best services for conducting fraudulent schemes.
Introduction
In fact, web injections are one of the most advanced tools that use bank Trojans to conduct fraudulent transactions with users' bank accounts. Recently, banks have begun to use special security mechanisms that are designed to protect an account or user account from unauthorized access. Web injections are also not standing still, and their authors adapt their cybercrime tools to circumvent these security mechanisms. Selling kits of web injects in underground forums has been observed for several years now.
As we know, over the past few years, users are increasingly turning to Internet banking services for various banking operations. Cybercriminals also do not stand still and create special malicious tools to compromise users' computers and their mobile devices. At the very beginning of their evolution, the attackers relied on banking trojans, which contained functions for compromising several financial institutions and were well-known keyloggers (keyboard spies) and grabbers / hijackers of web forms. Both of these tools were used to steal confidential data from online banking accounts.
Keyloggers are less useful because they generate a general flow of characters typed by the user from the keyboard, from which you will still need to isolate the desired username and password to access your online banking account. This task fell on the shoulders of botnet operators. Grabber of forms became an obvious way out of this situation, since it could only receive data of interest to intruders that the user entered into a fake login form into an online banking account. Then, the captured data was sent to the remote server of the attackers.
From the point of view of today, form grabbers are a rather outdated way of capturing GET and POST HTTP protocol requests, with which form data is sent to a remote server. The well-known and already studied Zeus and SpyEye banking trojans were the first to use the form grabbing mechanism based on interceptions of API functions in the context of the web browser process. Some malware used forms grabbing based on tracking the network traffic flow generated by the browser. Using the API interception mechanism is more preferable for attackers, since this way the form data is intercepted before they are directly encrypted for subsequent transfer to a web server. This method is not without flaws, since it is dependent on a particular browser or its version.
Modern malware is increasingly using these outdated techniques; instead, they resort to web-injecting services that allow them to fine-tune and use a malicious scheme of web page compromise and theft of funds. In addition, the web injections themselves allow you to modify the content of the web pages of online banking sites, depending on the specific bank. Web injections allow attackers to perform a wide range of actions on a compromised web page that the user sees. There are several sets of web injects offered for sale in underground forums that use a jQuery JavaScript library.
Zeus and SpyEye, the popular banking trojans, were among the first to use web injections to compromise specific banking sites and modify their content. The content of the web page can be modified using the API call interception mechanism. This is the same method that malware uses to organize forms grabbing. A banking trojan can inspect the content received from the server and modify it on the fly before directly displaying this content in a browser. This technique is used to trick a user who trusts in the content that the web browser displays when they visit the online banking web page. This method is known as an attack on a user called Man-in-the-Browser (MitB). Below in Fig. Figure 1 shows an example of a real web injection that resulted in deletion of text with warnings about financial fraud.

Fig. 1. Malware using web-inject has deleted service information from the web page (online banking warning). At the top is a view of the original web page, at the bottom a compromised web page with the warning text removed.
The malicious content that will be added to the web page is located in the web injects configuration file. This file is usually downloaded by the infected computer from a remote C & C server. This method of transferring the configuration file is very convenient for attackers, since they can modify the contents of such a file once on the server and infected computers will receive an upgraded version of this file the next time. There are various formats of web injects configuration files, but one of them has gained the most popularity. It was used in the SpyEye banking Trojan and eventually became the de facto standard. In Fig. Figure 2 shows an example web injects configuration file.

Fig. 2. The standard format of the web injects configuration file.
As you can see above, the first parameter is the target URL where a specific web injection should work. The characters in the line after the URL indicate to the banking trojan what action it should take when the user opens this address in the browser. Table 1 shows the values of these service symbols, and Table 2 shows the various parameters (tags) of the configuration file. Some web injections are quite simple and contain functions similar to a simple phishing mechanism, i.e. they embed special fields into the body of the web page, in which the user is prompted to enter his personal and confidential data. An example of such a web inject is shown in Fig. 3

Table 1. The most common flags for the set_url parameter.

Table 2. The most common tags of the web injects configuration file.

Fig. 3. An example of malicious webpage content that specializes in collecting personal and confidential user information.
Automatic Transfer System (ATS)
Over time, web injecting has become increasingly specialized and multifunctional. Some of them contain special advanced features that help attackers to perform fraudulent operations with the user's account. Special scripts that implement such operations are designed to bypass the protective mechanisms of specified online banking websites. As web injecting developed, the security systems of banks' sites were also improved and all new features were added to detect malicious activity. In Fig. 4. You can see an example of a web injection in which the attackers have provided time intervals between malicious actions to simulate human behavior.

Fig. 4. A webinjection function that defines the logic for using time delays.
As soon as the fraudulent transfer from the user's account has been completed, a web injection hides the operation by using special mechanisms. Concealment is understood as an imperceptible adjustment of the cash balance of a bank account. Thus, the user remains ignorant of the fact that funds have been stolen from his account.
The popularity of ATS attacks has decreased recently, as the level of complexity to success ratio has decreased (success-rate-to-complexity ratio). We can still observe the use of ATS methods of in-the-wild attacks, but some cybercriminals have refused to use them in favor of those attacks that use "manual control". In this case, the attackers simply take the compromised computer under their control and perform fraudulent actions manually.
Bypassing the Transaction Authorization Number (TAN) mechanism
With the advent of banking malware, security experts at banks began to introduce special additional security features into banking resources. One of the most popular of these functions was two-factor authentication, which strengthened the security of transactions.
Two-factor authentication raises the security bar when conducting banking transactions through the use of special confirmation codes. Such codes can be obtained by the user in his bank simply in the form of a list, so-called. Transaction Authorization Numbers (TAN), or in the form of SMS-messages from the bank, the so-called Mobile codes (mTAN). If two-factor authentication is enabled, the user will use the received mTAN codes to confirm the ongoing transaction on the online banking website.
To bypass the mTAN mechanism, attackers can lure the user to install a special malicious program for a mobile device that will intercept SMS messages received from the bank. This can be accomplished through social engineering techniques. For example, as soon as a user logs into his online banking account via a compromised web browser, the malicious code will inject special malicious content onto a web page. Content is a text with a request to provide information about the mobile device used by the user (Fig. 5.).

Fig. 5. Malicious content on a web page that requests information about a mobile device.
After the user provides such information, he will receive an SMS message to his mobile device with a link to download the malicious application. He can also use the QR code to get the link. After its opening, the malware will be downloaded to the device, then the user will have to manually start its installation. This procedure can consist of several stages, for example, attackers can embed such content into the online banking web page that will act as a guide to installing malware, instructing the user step by step. As soon as the malware is installed on the mobile device, it will be able to redirect all received SMS messages to the attackers' phone, giving them the ability to bypass mTAN codes when conducting fraudulent actions with the user's account. Perkele and iBanking banking trojans are well-known malware representatives with such capabilities.
Since banks began to use two-factor authentication mechanisms, web injection developers were forced to adapt their malicious tools to circumvent them. As shown below, the attackers use one of the forms of social engineering to deceive the user and lure the necessary information from him, which will be used to circumvent these protective measures.
The information that became available to us after monitoring the activities of botnet malware provided us with a picture of the methods used by attackers to bypass the mTAN scheme. They all boil down to one general principle: displaying a special message to the user with a fictional story that will attract his attention. The attackers display it to the user at the very moment when he logs into his online banking account and believes that he is using a secure connection with the server and that all data displayed by the browser is reliable. One of these stories is based on the information that a certain amount of money was mistakenly transferred to the user and he should return it back. Such a scheme becomes possible because the malicious code of a web-injection can correct the cash balance displayed to the user, thus misleading it. Another story was based on the fact that the user was asked to "calibrate" his mobile device by performing a test cash transaction.
In Fig. 6. A fake malware message is shown asking to enter a TAN code from a list in the text field that was issued to a user in a bank. As we know, the codes in this list are numbered, so attackers ask for the code behind a certain number. The attackers ask the user to give them the TAN code in the event that they need to steal a certain amount of money from the user's account and confirm this operation with the 2FA mechanism. Phishing message is compiled as convincingly as possible for the corresponding impact on the user.

It should be noted that there are other web injections that are aimed not at compromising the websites of financial institutions and banks, but at compromising known services, for example, Facebook, Twitter, Google, Yahoo. Such web injections specialize in stealing users' confidential or private information, such as a credit card number or phone number. In Fig. 7 shows a web-inject, which is focused on a service known service Twitter.

Fig. 7. Web inject for Twitter service.
Encryption of web injects configuration files
Since web injects configuration files contain key information for security researchers and CERT organizations around the world, attackers are directly interested in keeping the contents of these files out of their hands. For this purpose, encryption and obfuscation algorithms are applied to the files.
At the initial stage of the development of web inject files, the attackers did not use encryption and these files were transferred from the remote server to the bot in the open form. After the antivirus companies turned their attention to banker Trojans and began to track the appearance of these configuration files, the attackers began to use encryption, making the process of decrypting the content more difficult with each step. Banking Trojans such as Zeus and its modifications currently use several levels of encryption, and the decrypted file itself is stored in memory in parts, not in its entirety.
Compression or compression of JavaScript code can be performed by an attacker using the so-called. mechanism / packer /, but in this case, it can be quite quickly converted to the original look. The operation of obtaining original content can be performed using simple permutations of the “eval” function and the services of the JS beautifier service. This compression method is convenient because it reduces the size of the content of the web-inject, but its obvious disadvantage is the weak content security. In Fig. 8. A fragment of the script that was compressed using / packer / is shown.

Fig. 8. An example of a mechanism compressed / packer / script.
The algorithms used by hackers to obfuscate the content of web injections can significantly complicate their analysis, since deobfuscating the content can be a non-trivial task. In Fig. 9. An example of such obfuscated content is shown.

Fig.9. An example of obfuscated web injection.
The increase in the number of banking Trojans, as well as their complexity, will inevitably lead to a demand for high-quality web injections. Such demand has already been secured by corresponding proposals in underground cybercriminal forums.
Source: https://habr.com/ru/post/254267/
All Articles