Security Analysis of Common Terminals

Watch Dogs game perfectly describes the near future: around all kinds of devices, means for issuing and receiving cash, as well as various devices with Internet access, stuffed with vulnerabilities, the exploitation of which allows the hacker to extract certain benefits. For example, in a game, the protagonist with a smartphone can compromise the video surveillance system, thereby obtaining the ability to conduct surveillance and obtain additional information.
Watch Dogs fans disagreed: someone says it’s too “utopian” to get a smartphone and break everything. Others realize that “a fairy tale is a lie, but a hint in it” and the game world partly reflects the real one.
We will try to put forward some more arguments in favor of the fact that the devices around us, which we barely notice in parks and public places, can be vulnerable and carry danger - at least for our wallet.
')
Terminal terminators
The number of public devices that are waiting for their hero from a computer game goes off scale. Parks and streets are full of parking payment terminals of various means of transportation and cozy “booths” of fast recharging of a mobile device. Airports and train stations offer various devices for paying for tickets and receiving background information. The cinemas have terminals for buying and booking tickets for movie shows. In polyclinics and public institutions, visitors are greeted by electronic queuing devices and printing any receipts. Even toilets are equipped with payment terminals. True, hardly anyone will be able to handle the latest devices - the spirit is not enough :).


However, life teaches developers of such devices the fact that not all their users touch touchscreens with good intentions. If we type in a request of the form terminal hacked into Google, we get many relevant videos in which the main characters play solitaire on one or another terminal or paint any obscenities in Paint. The reason for this may be various bugs in the terminal applications, and they often carry a similar operating principle.

So, in one of the videos, the participant holds his finger on the screen for about ten seconds, and this leads to the result of “right-clicking”. On the other guys randomly poke in the lower left corner of the screen - and the full-screen application is minimized. Someone even thought of closing the terminal’s GSM antenna with his palm and thus provoking a connection error.
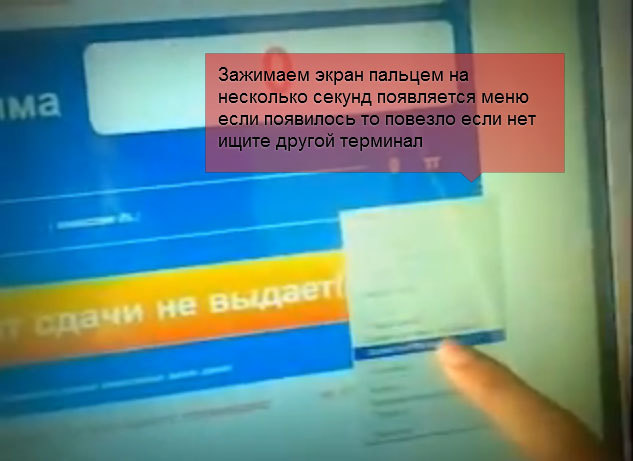
Of the cases of such devices being compromised, the incident with the payment terminals of one well-known electronic payment vendor is the most interesting. The attacker entered the line “last_page = StyleSheet.css” in the input field of the payment purpose using the virtual on-screen keyboard of the application, which is available in the interface of the payment system. As a processor for the file with this extension, notepad.exe was opened, which, through its help system, allowed the villain to move to the system control panel and launch the operating system's virtual keyboard.

Methods of security analysis of public terminals
Based on such videos and the sad experience of vendors, you can create a simple method of analyzing the security of devices of this type.

Our task: having a full-screen application in hand, which most likely functions on the basis of the Windows operating system, go beyond its limits into the system environment. For this you can use the so-called Tap-fuzzing. In other words - to work with your fingers. Click on different parts of the application in order to provoke its undocumented behavior. Or you can use Data-fuzzing and substitute various data in the input fields in order to provoke incorrect processing of incoming data.
As soon as you manage to call up an element of the standard interface of the operating system, the next step will be to get into the control panel, for example, through the help sections.
Entering the control panel will be the starting point for launching a virtual keyboard with corresponding consequences.
Traffic situation
Moscow residents are increasingly likely to find bicycle parking meters in the parks of their city. The essence of these devices is quite simple: there is a payment terminal for paying for a bicycle and a stand with bicycles. The output device in the payment terminal is a display, where the user can register to ride a bike and get background information.
The system interface is designed specifically for this type of device (if you have ever paid for something in the payment terminals, you can imagine what this is about), and it is difficult to get confused. In this interface, the user has the opportunity to get the current location of the parking machine, or rather, to see the mark on the Google map.
All such devices operate on the basis of classic operating systems (most often Windows-like) with all their vulnerabilities.
However, a specialized interface is a full-screen application with very limited functionality, which does not allow the user to get under the hood and deliberately or unintentionally mess things up nonsense. Accordingly, when analyzing the security of terminals, the main task is to go beyond the limits of this full-screen application. After that, you can play pranks: launch your applications, raise privileges, dump valuable information and so on.
In the considered systems of parking machines, an interesting feature was found. In the "Maps" section, the developers did not invent anything new and used maps from Google. And everything would be decent if only the widget from Google didn’t have a statusbar line, which among other information (current scale, copyrights, etc.) contains “Report an error”, “Privacy” and “Terms of Use” links, which open Internet Explorer Standard Window ...

And let's take a ride!
In addition to the described link, other links are imperceptibly scattered in this application (for example, when showing certain restaurants, you can click the Details button), by clicking on which you can open a browser.

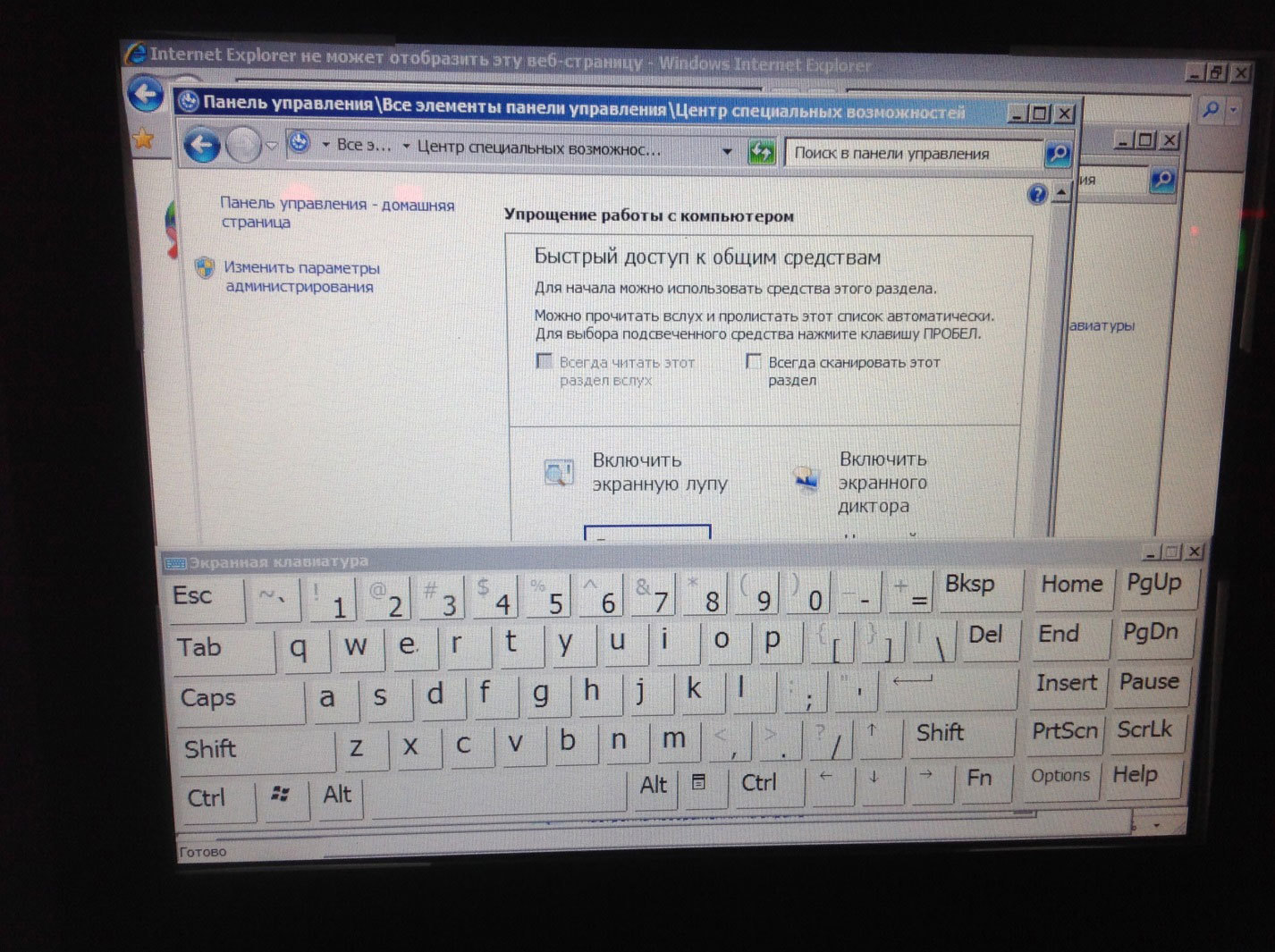
"So what? Well, I opened the browser - there are still no keyboards! ”Now it will be: the links on the pages with reference information allow you to go to the help section, which is called“ Special features ”, where the virtual keyboard is hidden (here’s another nasty minus Windows) .

Then everything depends on the imagination and the degree of arrogance of the attacker. Running cmd.exe demonstrates another configuration flaw: the current session of the operating system is running with administrator privileges, which means that we can potentially download and run any application completely free.
So, an attacker can get the NTLM hash of the administrator password. At the same time, it is likely that the password set on this device fits the other devices of this type - and this is the third lack of configuration.
On this adventure ends, so let's speculate that from all this an attacker can extract.
Terminals of public institutions
By state institutions, we mean those that are in buildings that have a coat of arms or a Russian flag. Without specifics and mention of manufacturers, but in fact :).
So, we have a full-screen application interface, which, based on the data we have entered, offers to print a receipt for payment.

After filling in all the fields and details, we press the “Create” button and observe the following picture: the terminal opens a standard print window for a few seconds, which contains all the print parameters of our document and automatically clicks the “Print” button.

As a result, if an attacker manages to click on the “Change” button, he gets an opportunity, through simple manipulations with print parameters, to go to the help section ...
Whitekheta fall asleep, blackheats wake up
Post-exploitation scenarios arise from the features of these devices:
- All of them are located in public places.
- Available 24/7.
- Have the same configuration.
- Have a higher degree of trust from the user.
- They are connected with each other and may have access to other “private” networks.
The main purpose of the attacker is direct or indirect financial gain as a result of the device being compromised. In this case, to achieve this goal, he can get not just an NTLM hash, which still needs to be brute-force to get a password, but immediately an administrator password. To do this, the attacker can extract passwords in clear text that are stored in memory. By the way, the latest version of the WCE utility can now not only dump passwords by inserting code into the lsass.exe process, but directly read the memory in the current session.
Add here support for Windows 7, on the basis of which work parking meters, and get the "key" immediately to all devices of this vendor.

In addition, an attacker can get a dump of the bicycle parking application, which kindly collects information about those who want to go: name, email address and telephone. It is possible that a database with important information is stored somewhere nearby. It is not necessary to explain that such a database will be of particular value in the market, because it contains verified phone and email addresses. In the event that there is no such database, the villain can install his keylogger, which intercepts all data entered by users and sends it to a remote server.
Considering one of the features of these devices - working 24/7, you can organize, for example, a pool for mining or use it for other hacking purposes that require an around-the-clock presence of an infected workstation on the network.
Particularly arrogant attackers can implement an attack scenario that will result in the receipt of user billing information: in the main window of the parking machine application, you can leave a field for entering plastic card details in an unobtrusive form, and with a high degree of probability, a misleading user will kindly leave them with his name, phone number and email ...
The abundance of scenarios that open up opportunities for access to personal data and the wallet of unsuspecting people is limited only by the imagination of intruders. The described situation with the protection of parking machines clearly demonstrates how several configuration flaws form a vulnerability.
In addition, a compromised terminal may be the starting point for further attacks on the corporate network. Very often, such devices access a terminal server or an entire subnet that is located in a trusted area of the company, which means that a small targeted attack using malware and / or social engineering can allow an attacker to be in the main office. Without knocking.

Recommendations
Our analysis of the protection of parking machines demonstrates how several configuration flaws make the device vulnerable. And the above attack scenarios - how it can open access to personal data and wallets for unsuspecting people to attackers.
In order to eliminate malicious activity on public devices, developers and administrators of bicycle parking terminals and other terminals located in public places, we recommend:
- Prevent the ability to open external links in a full-screen application.
- Do not allow any elements of the Windows interface to be called up (for example, with the right mouse button, using the print windows).
- Run the current operating system session with the limited privileges of a regular user.
- On each device, create a unique account with a unique password.
We recommend users of payment terminals not to enter full details of their payment cards. In no case can you enter the CVV2 / CVC2-card number, they are not required to make a payment. One should not neglect the possibility to pay the cash service in the terminal.

First published in the Hacker magazine dated 12/2014.
Subscribe to "Hacker"
Source: https://habr.com/ru/post/254003/
All Articles