How to easily decrypt TLS traffic from the browser in Wireshark
Many of you are familiar with Wireshark — a traffic analyzer that helps you understand network performance, diagnose problems, and generally knows a lot of things.
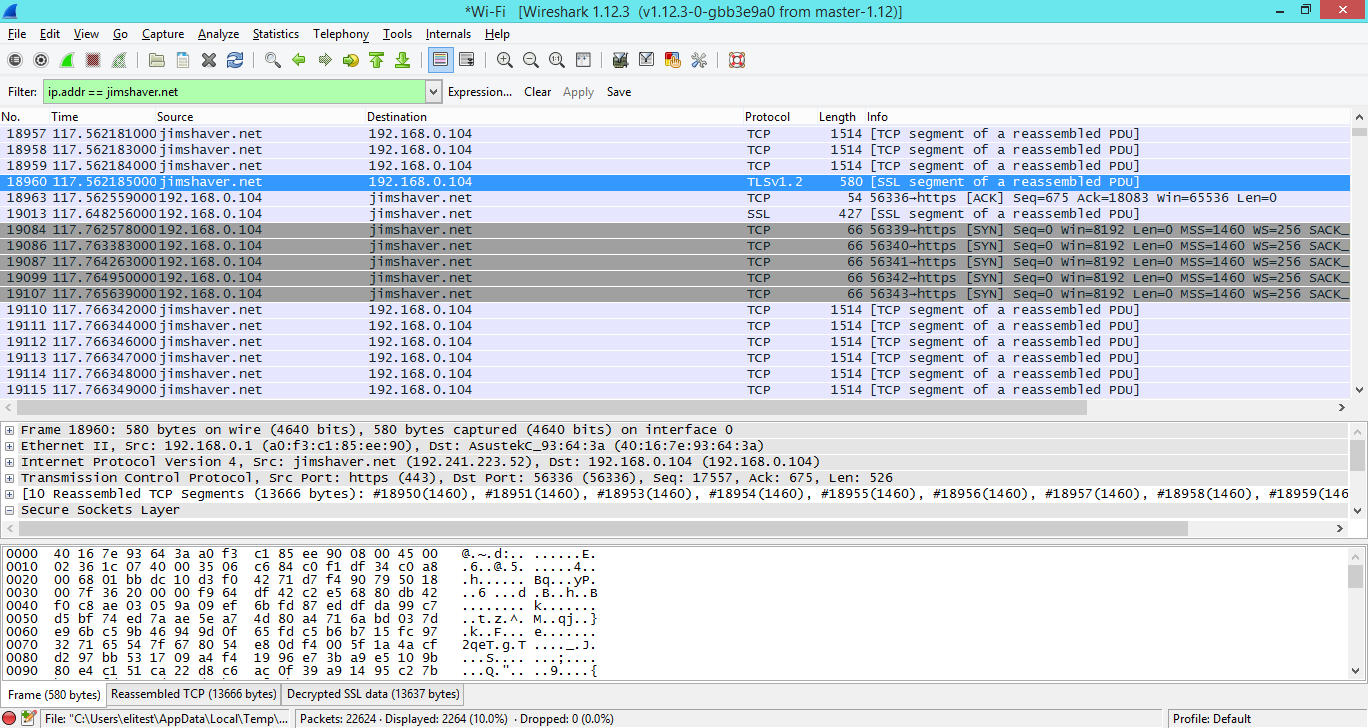
One of the problems with how Wireshark works is the inability to easily analyze encrypted traffic, such as TLS. Previously, you could specify Wireshark private keys, if you had them, and decrypt traffic on the fly, but this only worked if RSA was used exclusively. This functionality was broken because people started promoting Perfect Forward Secrecy, and the private key was not enough to get the session key that is used to decrypt the data. The second problem is that the private key should not or cannot be unloaded from the client, server, or HSM (Hardware Security Module) in which it is located. Because of this, I had to resort to dubious tricks with decoding traffic via man-in-the-middle (for example, via sslstrip ).
')
Well, friends, today I will tell you about the easier way! It turned out that Firefox and Development-version of Chrome support the logging of symmetric session keys, which are used to encrypt traffic, to a file. You can specify this file in Wireshark, and (voila!) Traffic is decrypted. Let's set this up.
We need to set the environment variable.
Open the properties of the computer, then "Advanced system settings", then "Environment variables ..."

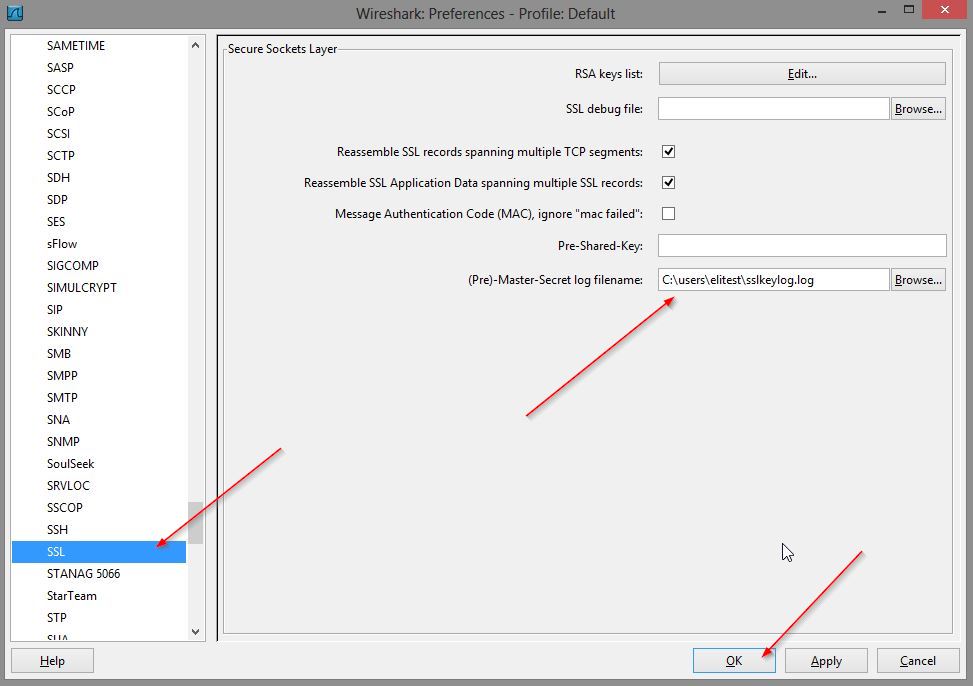
Add a new custom variable “SSLKEYLOGFILE”, and specify the path to the file where we want to save it.
You can also add this line to the end of your
The next time you launch Firefox or Chrome from the Dev channel, they will log TLS keys to this file.
UPD : If nothing works for you on OS X, take a look at the comments (original article). It seems that Apple has changed the work of the environment variables in the new version of OS X. Try running Firefox and Wireshark from the same terminal window:
Thank you Tomi for this remark.
You will need Wireshark version 1.6 and newer. Open the Wireshark settings:
Expand the Protocols section:
Specify the path to the file:
This is what we usually see when we inspect the TLS package:

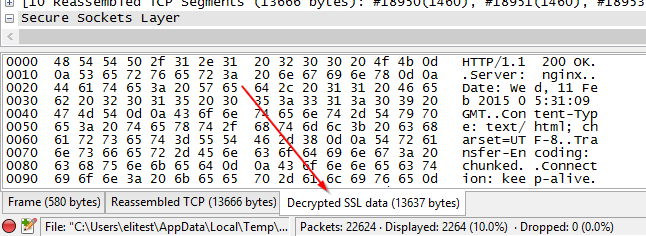
But what happens when we switch to the “Decrypted SSL Data” tab. Now we can see the request text. Victory!
Hopefully now it will be much easier for you to intercept TLS. One notable feature of this method is that you do not need to install Wireshark on a computer that generates TLS traffic, so you don’t have to install unnecessary program clients, you can save a dump to a file on a network drive, or just copy it from the machine, and use with traffic dump.
Thank you for reading!

One of the problems with how Wireshark works is the inability to easily analyze encrypted traffic, such as TLS. Previously, you could specify Wireshark private keys, if you had them, and decrypt traffic on the fly, but this only worked if RSA was used exclusively. This functionality was broken because people started promoting Perfect Forward Secrecy, and the private key was not enough to get the session key that is used to decrypt the data. The second problem is that the private key should not or cannot be unloaded from the client, server, or HSM (Hardware Security Module) in which it is located. Because of this, I had to resort to dubious tricks with decoding traffic via man-in-the-middle (for example, via sslstrip ).
')
Logging session keys to the rescue!
Well, friends, today I will tell you about the easier way! It turned out that Firefox and Development-version of Chrome support the logging of symmetric session keys, which are used to encrypt traffic, to a file. You can specify this file in Wireshark, and (voila!) Traffic is decrypted. Let's set this up.
We configure browsers
We need to set the environment variable.
Windows
Open the properties of the computer, then "Advanced system settings", then "Environment variables ..."

Add a new custom variable “SSLKEYLOGFILE”, and specify the path to the file where we want to save it.
Linux and Mac OS X
$ export SSLKEYLOGFILE=~/path/to/sslkeylog.log You can also add this line to the end of your
~/.bashrc on Linux or in ~/.MacOSX/environment on OS X, so you don’t have to install it every time after relogin.The next time you launch Firefox or Chrome from the Dev channel, they will log TLS keys to this file.
UPD : If nothing works for you on OS X, take a look at the comments (original article). It seems that Apple has changed the work of the environment variables in the new version of OS X. Try running Firefox and Wireshark from the same terminal window:
# export SSLKEYLOGFILE=/Users/username/sslkeylogs/output.log # open -a firefox # wireshark Thank you Tomi for this remark.
Hidden text
I do not know, as in MAC OS X, but in Linux, the method described by the author will not work. Environment variables always work within the same session (tty, pty), and you need to launch Firefox from the same window.
~ ValdikSS
~ ValdikSS
We configure Wireshark
You will need Wireshark version 1.6 and newer. Open the Wireshark settings:

Expand the Protocols section:

Specify the path to the file:

Result
This is what we usually see when we inspect the TLS package:

But what happens when we switch to the “Decrypted SSL Data” tab. Now we can see the request text. Victory!

Conclusion
Hopefully now it will be much easier for you to intercept TLS. One notable feature of this method is that you do not need to install Wireshark on a computer that generates TLS traffic, so you don’t have to install unnecessary program clients, you can save a dump to a file on a network drive, or just copy it from the machine, and use with traffic dump.
Thank you for reading!
Source: https://habr.com/ru/post/253521/
All Articles