JavaScript and Reverse Engineering Contact Points

If you look at job descriptions for the Reverse Engineer position, you are unlikely to meet the requirement of knowledge of JavaScript there. And if you do, it is only in the context of its deobfuscation on various malicious pages commonly used by exploit packs.
And is it even possible to coexist JS (which some even call the web assembler) and the low level world with the Assembler at the head?
If web portals with:
- HEX editors
- assemblers
- disassemblers ( Cenigma , ODA , Radare2 Cloud )
- decompilers ( Retargetable Decompiler )
- emulators
- virtualizers
- etc.
In this article, I would like to present some really interesting and useful projects (I’ll just note that it is not a call for studying JS for reverse engineering tasks).
')
Node Capstone
Most recently, the framework for disassembling Capstone was born. The project immediately received community support and huge popularity. This is understandable: it is easy to use and immediately supports a large number of architectures: ARM, ARM64 (ARMv8), MIPS, PowerPC, SPARC, Windows OS and * nix (Mac OSX, iOS, Android, Linux, * BSD and Solaris). Over time, the framework has binded to different languages, and there are already: Python, Ruby, C #, Java, GO, C ++, OCaml, Vala and NodeJS. Yes, NodeJS!
Here is the binding itself: github.com/parasyte/node-capstone
And this is an example of code in which the 64-bit code for the x86 architecture is disassembled and then output to the console:
var capstone = require("capstone"); var code = new Buffer([ 0x55, 0x48, 0x8b, 0x05, 0xb8, 0x13, 0x00, 0x00 ]); var cs = new capstone.Cs(capstone.ARCH_X86, capstone.MODE_64); cs.detail = true; cs.disasm(code, 0x1000).forEach(function (insn) { console.log( "0x%s:\t%s\t%s\t%s", insn.address.toString(16), insn.mnemonic, insn.op_str, JSON.stringify(insn.detail) ); }); cs.close(); pe.js
github.com/mihailik/pe.js
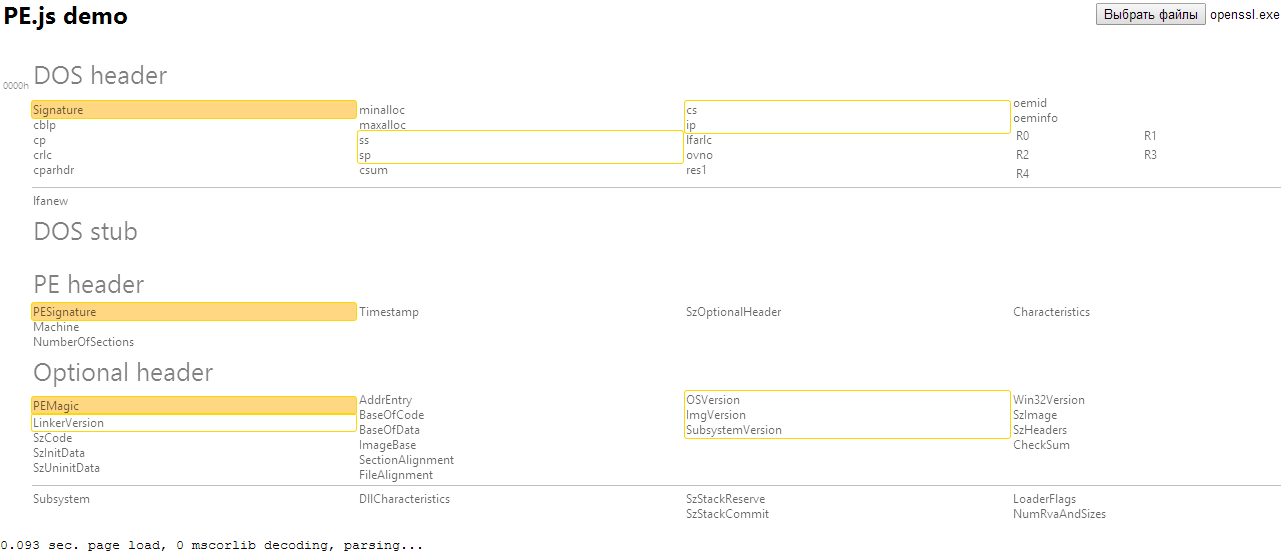
In the process of writing an exploit for the browser to bypass the ASLR, an address leak is often used, against which the ROP chain is then built. If you need to call some specific function, but it does not occur in the code, another maneuver is done. We calculate the beginning of the necessary DLL and pars it. For this, it would be nice to have JavaScript code that can parse the PE format and the import table in particular. This is where pe.js comes in.
Well, or as an infector of EXE files in pure JavaScript. Here's an example: alive-green.blogspot.ru/2014/03/js-javascript.html
cycript
www.cycript.org
cycript is a tool from the well-known Jay Freeman (saurik). It allows you to run and modify an application on Mac OS X or iOS in runtime. All this happens when interacting through the console (the launch of scripts is also present) in a hybrid language with the syntax Objective-C ++ and JavaScript.
There is also the ability to interact with Substrate - this is very convenient when implementing the function interception, logging, modifying parameters or results. Often used in the study of the program or its fuzzing.
Here is an example of working with cycript on iOS, where you are connecting to an application and viewing values in an object of a particular class.
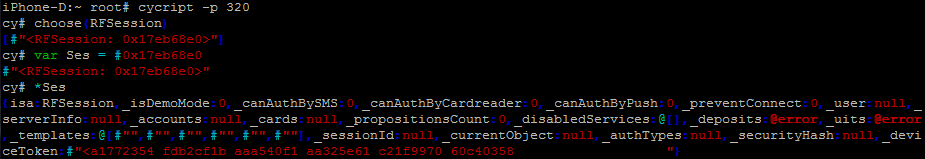
Or, probably, the most popular cycript function is the output of all the names of functions of a certain class with the address of their implementation:
function printMethods(className) { var count = new new Type("I"); var methods = class_copyMethodList(objc_getClass(className), count); var methodsArray = []; for(var i = 0; i < *count; i++) { var method = methods[i]; methodsArray.push({selector:method_getName(method), implementation:method_getImplementation(method)}); } free(methods); free(count); return methodsArray; } By using this library, you can find a lot of manuals on the Internet and even references to use on Habré.
On this tool, for example, a framework called iNalyzer is built , which is often used in blackbox testing of iOS applications.
Frida RE
www.frida.re

Frida allows you to inject JavaScript code into applications on Windows, Linux, Mac, Android and iOS platforms. As for architectures, of course, x86 / x64 / ARM / AArch64. The tool allows you to execute your own JS scripts inside the application: intercept functions, create wrappers around them, replace input / output parameters, or simply call a specific function from the application under study, and that’s not all. Thus, the same code can be used almost without changes on all the listed operating systems. As for Android, it has support for working with VM Dalvik, and you can work not only with native-functions, but also with those written in Java. The same can be said about Objective-C code for OS X and iOS.
The Frida core is written in C, and for its work it injects into the target process the V8 engine from Google, which executes our JS code with full access to the entire process memory and organizes a bi-directional interaction channel with the application.
Frida has such cool functions as send, resv, post_message, which allow you to communicate with our JS code, which is already running inside the target application, and thereby interactively change the behavior of the code inside. For example, we wrote a JS code that looks for a specific string in memory, and injected it into a mobile application. After that, we can first look for the login in the memory after authorization, and then the password or some other string, simply sending it to our JS script. And, of course, to get an answer, the necessary string was found or not.
This is, for example, the code for the enumerate_modules () built-in function, which is responsible for listing the libraries loaded into the process, in python binding:

Or here is the code for logging the work of the function with the int func prototype (int val, char * str):
script = process.session.create_script(""" Intercrptor.attach(ptr("%s"), { onEnter: function(args){ send({info:'onEnter', val:args[0].toInt32(), str:Memory.readUtf8String(args[1])}); }, onLeave: function(retval){ send({info:'onLeave', retval: retval.toInt32()}); } }); """ % addr The framework was first presented at the Hackito Ergo Sum 2013 conference and is now well maintained and updated. There is already support for iOS 8.1 and ARM64 architecture. And this is probably the most interesting project in this review.
Pinocchio
github.com/pablosole/pet
The project, which appeared even earlier than Frida, and implemented the idea of injecting the V8 engine into the program under study. Presented at the EkoParty 2012 conference, but, unlike Frida, has not received development and support from the community. But I think that it is worth mentioning it, since the source code is published and anyone can continue the development of the project, if he likes it.
Pinocchio allows you to realize all the features of PIN on JavaScript and is based on the V8 engine. I already wrote about DBI (Dynamic Binary Instrumentation) and the PIN framework. PIN itself does not stand still and develops. What Pinocchio can do is here .
Example code for handling events when a new module is loaded and a new thread is created in the program:
function newimage(img) { log(img.name + “ – “ + img.loadOffset.hex()); } function newthread(threadId, ctx, flags) { log(“New Thread “ + current.thread.tid); log(“Thread Stack:” + ctx.get(REG_ESP).hex()); } events.attach(“loadimage”, newimage); events.attach(“startthread”, newthread); This tool now supports only Windows and IA32.
More detailed presentation on the tool (in Spanish): www.ekoparty.org//archive/2012/Pin%20para%20Todos%20y%20Todas.pdf
IDA_JScript
github.com/dzzie/RE_Plugins/tree/master/IDA_JScript

If we are talking about reversing, then where is it without IDA Pro. Scripts for it with varying degrees of convenience can be written in a huge number of languages: C / C ++, IDC , Python ( IDAPython ), Ruby ( idarub ), Perl , Java ( idajava ), Ocaml ( idaocaml ). Some bindings, of course, are far from being up to date.
And JavaScript is no exception: IDA_JScript .
Of course, I doubt that many people actively use this, but the very fact of its existence is eloquent. You can use it, but you also have to maintain / update it.
Here is the code to get all the names specified by the user in the specified range:
s = 0x09A47A8 e = 0x09A5ACE if(s.length==0 || e.length == 0){ throw "invalid inputs" } s = parseInt(s); e = parseInt(e); ret = ''; com = 'comments:\r\n'; while(s < e) { n = ida.getname(s) c = ida.getcomment(s); if(n && n.length > 0){ ret += "MakeName(0X" + h(s) + ",\"" + n + "\");\r\n" } if(c && c.length > 0){ com += "0X" + h(s) + "\t= " + c + "\r\n"; } s = ida.nextea(s); if(s==-1) break; } ret = ret + "\r\n\r\n" + com t(ret) fso.setclipboard(ret); alert("Names and comments for range extracted"); bNarly
github.com/d0c-s4vage/bnarly

In order to understand what caused the browser to crash or how this or that page affects the internal structures of the browser, you need to look / follow what gets up JavaScript. This is still the debugger to this day. And the process in the debugger looks quite dreary and time consuming.
A friend with a nickname d0c_s4vage had the idea to instruct work in WinDbg via JS, that is, to execute WinDbg commands from JS. As a result, he created the bNarly project.
bNarly (browser Narly) is a tool for exploring and operating browsers. bNarly is a bridge between the WinDbg debugger and JavaScript.
This tool is written using the jQuery library.
Where can this tool come in handy in practice? The first thing that comes to mind is when analyzing crush, use-after-free operation or adjusting heap-spray.
Main functions:
- Memory dump
- Tracing free / alloc
- Execute javascript code
Work algorithm:
- Open browser
- Open WinDbg and attach to the desired tab.
- Put a breakpoint in WinDbg on the desired function
- In the bNarly window we write and execute the necessary code.
- WinDbg keeps track of everything, and then bNarly displays its information
- IE 8, 9, 10, 11
- Firefox> = 20
Chemhem dbg
github.com/hexgolems/schem

Recently, in the reverse engineering world, there has been active work in the direction of visualization of the studied data, displaying the process of program execution, in general, everything related to the convenience of perception in the study of a program.
One of the most commonly used tools with RE is the debugger. And the way it displays the process of the program is very important. Now there are plenty of debuggers, everything is different, including the UI, it is not always possible to configure it, but for someone it is either suffering or is completely absent.
The SchemDBG project tries to completely explode the debugger and the display so that it is possible to connect any debugger by simply supporting several basic operations.
SchemDBG aims to display / provide as much information as possible at any point of the program being debugged. Currently, GDB and PIN are supported as backends. Each of them is for 32-bit and 64-bit binary files running on a machine with Ubuntu as the host machine.
The debuggers are managed using a Ruby wrapper, and the web front-end is written in CoffeeScript. The frontend works correctly under Chromium (no other browser support is planned). At the same time, many clients can join one controller (debugger), which provides viewing in several screens (possible with different settings).
The project was developed in the framework of Google Summer of Code 2013.
Tessel
tessel.io
Well, for various games with iron with knowledge of JS this board is perfect. It turns out in the end this Arduino for JS-fans))

In detail this piece of iron has already been considered here .
For me, using web technologies to visualize data obtained in the RE process is now seen as the most promising and useful. For example, a plug-in for IDA Pro was written in internal development, which serves as a WebSocket server and helps to interact with the browser. And already in the browser with the help of the D3.js library , visualization of both static information and that obtained during the execution of the program under study occurs. Naturally, the interaction between IDA Pro and the browser is interactive. Such interaction can be viewed in the George Hotz QIRA project.
We can safely say that the distance between web technologies and RE tasks is gradually reduced ...
Source: https://habr.com/ru/post/253309/
All Articles